WhatsApp biometric authentication fingerprint face unlock desktop browser app is poised to revolutionize how we secure our messaging accounts. This innovative approach promises enhanced security by integrating biometric features like fingerprint and facial recognition into the desktop browser version of WhatsApp. It explores the technical, security, and user experience considerations, including the challenges of implementing biometrics in a browser environment and the potential impact on user privacy.
The article delves into the evolution of authentication methods in messaging apps and compares various biometric methods, highlighting their strengths and weaknesses.
The integration of biometrics promises a more convenient and secure way to access WhatsApp on desktop. The article explores how this integration can be seamless, while considering potential usability issues and accessibility concerns. It also addresses the critical aspect of maintaining user familiarity with the existing WhatsApp interface while incorporating these new security measures.
Introduction to Biometric Authentication on WhatsApp
WhatsApp, a ubiquitous messaging platform, is constantly evolving to enhance user experience and security. A significant step in this evolution is the integration of biometric authentication, a method that leverages unique physical characteristics to verify user identity. This approach promises to significantly bolster security against unauthorized access and enhance user convenience.Biometric authentication, relying on unique biological traits like fingerprints and facial features, is becoming increasingly prevalent across various applications.
This shift reflects a growing need for robust security measures in the digital age. The integration of biometrics into WhatsApp represents a proactive approach to protect user data and accounts, mirroring the trend seen in other mobile applications.
Biometric Authentication Methods
Biometric authentication methods utilize unique physical characteristics for user identification. Fingerprint scanning and facial recognition are two prominent examples. Fingerprint scanners utilize the unique patterns of ridges and valleys on a fingertip, while facial recognition systems analyze facial features to identify individuals. These methods offer a high degree of security compared to traditional password-based systems.
Evolution of Authentication Methods in Messaging Apps
Messaging apps have progressively advanced their security measures. Early iterations often relied on simple passwords, which, while functional, presented vulnerabilities to unauthorized access. The evolution towards multi-factor authentication and now biometrics represents a significant stride in user protection.
Potential Benefits of Biometric Authentication in WhatsApp
Integrating biometrics into WhatsApp offers several advantages. Firstly, it enhances security by adding an extra layer of protection against unauthorized access. Secondly, it simplifies user authentication, offering a convenient alternative to complex passwords. Thirdly, it can potentially reduce fraudulent activities by verifying the identity of the user more accurately.
Examples of Biometric Use in Other Apps
Many applications already leverage biometric authentication for security. For instance, mobile banking apps often use fingerprint or facial recognition to verify user identity before accessing sensitive financial information. Similarly, some e-commerce platforms utilize biometrics for secure logins.
Comparison of Biometric Authentication Methods
| Authentication Method | Pros | Cons |
|---|---|---|
| Fingerprint Scanning | High accuracy, convenient, relatively secure | Requires a physical device, potential for damage or spoofing |
| Facial Recognition | Non-intrusive, user-friendly, can be contactless | Susceptible to spoofing with images, potentially affected by lighting conditions |
Implementing Biometric Authentication in WhatsApp Desktop Browser App
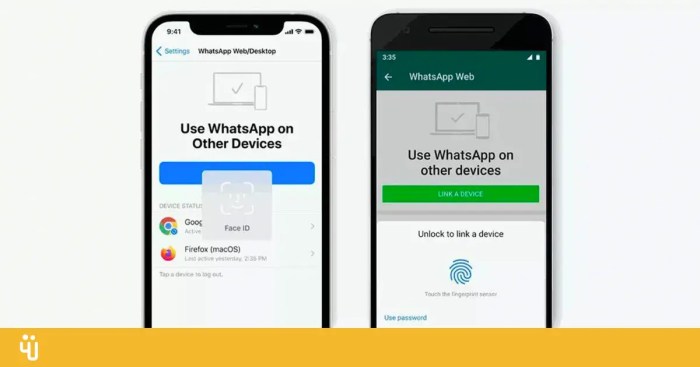
Adding biometric authentication to the WhatsApp desktop browser app presents a unique set of challenges compared to native desktop applications. The primary hurdle lies in the inherent limitations of browser-based environments, which often lack direct access to the hardware necessary for secure biometric capture. However, with careful consideration of security and user experience, robust biometric authentication can be integrated, enhancing the overall security posture of the app.Implementing biometric authentication on a desktop browser application introduces a number of technical considerations.
A key aspect is bridging the gap between the browser’s sandboxed environment and the underlying hardware. This often requires the use of browser extensions or plugins, which themselves have security implications that must be addressed.
Ever wondered about WhatsApp’s biometric authentication? Fingerprint and face unlock on a desktop browser app is a fascinating development. While this technology is promising, it’s important to consider the broader implications for security, like the recent advancements in self-driving cars, particularly with the US Congress’s first self-driving car bill, the AV Start Act av start act congress us first self driving car bill tesla gm.
Ultimately, biometric authentication on WhatsApp’s desktop browser will need robust security measures to protect user data, just as the automotive industry is striving for safety and reliability in autonomous vehicles.
Technical Challenges of Implementing Biometrics in a Desktop Browser App
Browser security models, designed for web applications, often restrict direct interaction with hardware. This limits the ability to access biometric sensors directly. To overcome this, solutions frequently involve using browser extensions or plugins, which can introduce potential security vulnerabilities if not carefully designed and implemented. Careful consideration of permissions and sandboxed environments is paramount.
Security Considerations for Handling Biometric Data
Protecting biometric data is critical. The data, particularly fingerprint or facial templates, must be encrypted both in transit and at rest. Storing these templates securely within the browser environment, complying with data privacy regulations (like GDPR), and implementing robust access controls are essential. Data breaches could lead to significant security issues and reputational damage.
User Experience Implications of Adding Biometric Authentication
User experience is paramount. The process of biometric authentication should be seamless and intuitive, minimizing friction. Clear instructions, visual cues, and feedback mechanisms are vital for a positive user experience. A user should not be overwhelmed by the complexity of the authentication procedure. The system must be resistant to false positives and negatives to prevent unwanted account lockouts.
Comparison of Biometric Methods on Desktop Browsers
Different biometric methods offer varying degrees of security and usability on desktop browsers. Fingerprint authentication often involves more complex integration with browser extensions or plugins, while facial recognition can be more user-friendly, relying on the webcam. The choice of method should be informed by security requirements, user expectations, and technical feasibility. Factors such as the prevalence of biometric hardware on user devices and the specific security needs of the app must be considered.
Steps to Implement a Fingerprint Authentication System on a Desktop Browser
To ensure a smooth and secure fingerprint authentication system on a desktop browser, a structured approach is essential. The following steps Artikel the general procedure:
| Step | Description |
|---|---|
| 1. | Security Assessment: Evaluate the security risks associated with the specific biometric method, considering potential vulnerabilities related to browser extensions and data handling. |
| 2. | Integration with a Secure Plugin: Develop a secure browser plugin that interacts with the operating system’s fingerprint sensor. This plugin needs rigorous testing to ensure its security. |
| 3. | Fingerprint Template Generation: Develop a method to securely generate a fingerprint template. The template must be encrypted and stored in a secure manner. |
| 4. | Authentication Process: Implement the authentication process, which includes capturing the user’s fingerprint and comparing it with the stored template. |
| 5. | Error Handling: Develop comprehensive error handling mechanisms to address potential issues like incorrect fingerprints or failed authentication attempts. |
| 6. | User Feedback: Design appropriate user feedback mechanisms to inform the user about the status of the authentication process. |
| 7. | Testing and Refinement: Rigorously test the entire system under various conditions and user scenarios to ensure its reliability and robustness. |
Security and Privacy Aspects

Biometric authentication, while offering a convenient and secure login method, necessitates a robust security framework to protect user data. The sensitive nature of biometric information, like fingerprints and facial features, demands meticulous attention to data encryption and protection against breaches. This section delves into the critical security and privacy considerations surrounding biometric authentication in WhatsApp’s desktop browser app.
Importance of Data Encryption
Protecting biometric data from unauthorized access is paramount. Encryption plays a crucial role in ensuring the confidentiality and integrity of this sensitive information. By converting data into an unreadable format, encryption renders it useless to attackers. This is essential for preventing data breaches and maintaining user trust. The process of encryption involves transforming readable data into an encoded form, requiring a unique decryption key to restore the original information.
Potential Risks of Biometric Data Breaches
Compromised biometric data can lead to significant risks. Unauthorized access to fingerprint or facial recognition templates can grant malicious actors access to user accounts and potentially sensitive personal information. A successful breach could allow attackers to impersonate users, gain access to messages, or even control WhatsApp accounts. The potential for identity theft and financial fraud is substantial.
Security Measures to Protect Biometric Data
Robust security measures are vital to safeguard biometric data. These measures include strong access controls, regular security audits, and robust encryption protocols. Implementing multi-factor authentication alongside biometric authentication significantly enhances security. Employing secure hardware security modules (HSMs) can further protect the encryption keys, adding an extra layer of protection against sophisticated attacks. Regularly updating security protocols and software is critical to address emerging threats.
Comparison of Encryption Methods for Biometric Data
Different encryption methods offer varying levels of security and performance. Symmetric-key encryption, such as AES, uses the same key for encryption and decryption, which is relatively fast. Asymmetric-key encryption, such as RSA, uses separate keys for encryption and decryption, offering enhanced security but can be slower. Hybrid approaches combining both methods can balance speed and security effectively.
The choice of encryption method depends on the specific needs and constraints of the application.
Security Protocols for User Data Protection
Implementing robust security protocols is critical to protecting user data. These protocols should address various security concerns, including unauthorized access, data breaches, and unauthorized modifications.
| Security Protocol | Description | Strengths | Weaknesses |
|---|---|---|---|
| HTTPS | Secure protocol for transmitting data over the internet. | Widely adopted, secure connection. | Vulnerable to man-in-the-middle attacks if not properly implemented. |
| TLS/SSL | Protocols that encrypt communication between a web server and a client. | Provides strong encryption, widely supported. | Requires proper configuration and key management. |
| Biometric Authentication | Uses unique biological traits to verify user identity. | Highly secure, prevents unauthorized access. | Requires secure storage and handling of biometric data. |
User Experience and Interface Design
Crafting a biometric authentication interface for a desktop browser app demands careful consideration of the user experience. A seamless and intuitive process is paramount, ensuring users feel secure and confident in the system’s ability to protect their accounts. The design must be mindful of the specific characteristics of desktop environments, differing from mobile interfaces. This involves understanding user expectations, accommodating various scenarios, and addressing potential challenges.The authentication process should be presented in a clear, consistent, and visually appealing manner.
Employing visual cues and feedback mechanisms helps users understand the system’s progress and status during authentication. Clear instructions and prompts are essential to guide users through the process, ensuring minimal friction and confusion.
WhatsApp’s new biometric authentication, including fingerprint and face unlock for its desktop browser app, is a fascinating development. It’s interesting to consider how this security enhancement might impact user experience, particularly in comparison to the recent Spotify redesign, spearheaded by Gustav Söderström, that’s influenced by TikTok streaming and podcasts, enhancing music discovery here. Ultimately, these advancements in both platforms show a growing trend towards secure and intuitive user interfaces in mobile and desktop applications.
Designing the Authentication Process for Different User Scenarios
Different user scenarios require nuanced approaches to biometric authentication. For instance, frequent users may benefit from a streamlined process, whereas infrequent users might require more explicit guidance. This section details the user experience considerations for various user types. A user with a well-established authentication history may prefer a quicker, more automated experience. In contrast, a new user will likely require a more structured process with clear instructions and visual cues.
This adaptability is crucial to maintaining a positive user experience across diverse usage patterns.
User Experience Challenges of Implementing Biometrics on Desktop Browsers
Implementing biometric authentication on desktop browsers presents unique challenges. One primary challenge is the diversity of hardware and software configurations across user devices. Varying screen resolutions, operating systems, and browser versions can affect the display and performance of biometric authentication components. Ensuring compatibility across these diverse environments is essential to maintain a consistent user experience. Another challenge is the potential for user frustration due to hardware limitations.
For example, if a user’s fingerprint reader is not functioning optimally, the authentication process might fail, leading to user dissatisfaction. Furthermore, desktop environments often involve concurrent tasks and complex workflows, necessitating robust error handling and fallback mechanisms to minimize disruptions to user activity.
Examples of Successful Biometric Authentication Interfaces
Several applications have successfully integrated biometric authentication into their desktop interfaces. Examples include financial institutions and enterprise software, where robust security and user convenience are paramount. A key aspect of these successful implementations is the clear and intuitive presentation of biometric prompts. These interfaces provide clear instructions and visual feedback, ensuring users understand the authentication process. The successful interfaces often employ visual cues, such as loading indicators or progress bars, to enhance the user experience during the authentication process.
Table of User Interface Design Elements for Biometric Authentication
| Design Element | Description | Example |
|---|---|---|
| Clear Instructions | Provide concise and easily understandable prompts for each step. | “Place your finger on the sensor.” |
| Visual Feedback | Display visual cues to indicate the authentication process status. | A loading animation while processing the biometric data. |
| Error Handling | Provide clear and actionable error messages for failed authentication attempts. | “Authentication failed. Please try again.” |
| Accessibility Options | Offer alternative authentication methods for users with disabilities. | A password-based fallback option. |
| Security Indicators | Visually communicate the level of security in use. | A lock icon to indicate the secured authentication. |
Integration with Existing WhatsApp Features: Whatsapp Biometric Authentication Fingerprint Face Unlock Desktop Browser App
Seamless integration of biometric authentication into WhatsApp’s existing ecosystem is crucial for user adoption and a positive user experience. Maintaining familiarity with the app’s interface is paramount to avoiding friction and confusion. This involves thoughtful design choices that minimize disruptions to the user flow.A well-designed integration should not require significant changes to the existing user experience. The goal is to make the biometric authentication process as unobtrusive as possible, ensuring users can continue using WhatsApp without needing to learn a new set of procedures.
Maintaining User Familiarity
The core principle in integrating biometric authentication is to minimize disruption to the current WhatsApp workflow. Users should not have to learn entirely new interactions. The transition should be intuitive and logical, aligning with existing patterns of use. This includes maintaining the same visual cues and interactions associated with existing features.
Ever wished WhatsApp had biometric authentication? A fingerprint or face unlock feature for the desktop browser app would be seriously cool. While you’re waiting for that, check out some amazing deals on Amazfit watches during Amazon’s Prime Early Access event. Save up to 50 on Amazfit watches during Amazon’s Prime early access event – a great way to treat yourself while you anticipate the WhatsApp biometric update.
Hopefully, that feature will be here soon, so you can secure your chats with a personal touch!
Integrating Biometric Authentication with WhatsApp’s Messaging System
Biometric authentication can be integrated into WhatsApp’s messaging system in several ways. One approach is to use biometric authentication for unlocking the app itself, allowing access to the entire messaging system. Alternatively, biometric authentication could be applied to specific actions within the messaging system, such as initiating a call or sending a sensitive message.
Integrating Authentication with Other Existing Features
Biometric authentication can be integrated with other WhatsApp features such as the call system, voice notes, media sharing, and account settings. For example, a user might need biometric verification before initiating a voice call to enhance security. Similarly, access to sensitive media or account settings could require biometric verification for enhanced privacy.
Interaction Table: Biometric Authentication and Existing WhatsApp Features
| WhatsApp Feature | Biometric Authentication Integration Points |
|---|---|
| App Launch | Primary authentication point, ensuring secure access to all features. |
| Messaging System | Verification for sensitive messages or to confirm user identity. |
| Calls | Authentication before initiating calls, especially for secure or confidential calls. |
| Voice Notes | Optional verification for voice notes to prevent unauthorized access or recording. |
| Media Sharing | Optional verification for sharing sensitive media to control access. |
| Account Settings | Verification for sensitive account changes or modifications, enhancing security. |
Accessibility and Inclusivity Considerations
Ensuring a seamless and equitable user experience is paramount in the design of biometric authentication systems. Ignoring accessibility considerations can exclude a significant portion of the user base, leading to frustration and ultimately hindering the adoption of the technology. A well-designed biometric system should be usable by everyone, regardless of physical abilities or personal circumstances.
Importance of Accessibility for All Users
Accessibility and inclusivity are not just ethical considerations; they are essential for the success of any product. A diverse user base brings a wide range of needs and abilities, and a product that caters to those diverse needs will ultimately have a wider reach and greater impact. By considering accessibility early in the design process, developers can create a system that is usable and enjoyable for everyone.
Designing for Users with Disabilities
Designing biometric authentication for users with disabilities requires careful consideration of various impairments. For users with visual impairments, alternative authentication methods like voice commands or haptic feedback should be available. Users with motor impairments might benefit from larger touch targets, adjustable sensitivity settings, and alternative input methods like head tracking or voice commands. For users with cognitive impairments, clear instructions, simple interface design, and reduced complexity in the authentication process are critical.
Consideration should also be given to users with hearing impairments.
Creating a Usable System for a Diverse User Base
A diverse user base requires a system that caters to varying levels of technical proficiency and familiarity with biometric technology. A multi-faceted approach is crucial, combining intuitive interfaces with clear and concise instructions. The system should provide alternative authentication methods for users who may struggle with the primary biometric method. The interface should also be adaptable to various screen sizes and resolutions, ensuring usability on different devices and operating systems.
Examples include providing text-based alternatives for visual instructions and incorporating keyboard shortcuts for users who prefer using a keyboard over a mouse or touch screen.
Examples of Successful Inclusive Design in Other Applications, Whatsapp biometric authentication fingerprint face unlock desktop browser app
Many applications have successfully incorporated inclusive design principles in their authentication processes. For instance, banking apps often provide alternative authentication methods for visually impaired users. These may include text-to-speech features for reading prompts and instructions or alternative input methods that are easier to use. Similarly, social media platforms have made significant strides in creating more accessible interfaces, offering options for users with various needs and preferences.
These examples demonstrate that inclusive design is achievable and can enhance the user experience for a broader range of individuals.
Accessibility Features for Biometric Authentication
| Accessibility Feature | Description | Example Implementation |
|---|---|---|
| Alternative Authentication Methods | Providing alternative ways to authenticate, such as voice commands or passcodes. | Allow users to authenticate with a PIN code or voice recognition in addition to fingerprint or facial recognition. |
| Adjustable Sensitivity | Giving users the ability to adjust the sensitivity of the biometric sensor. | Enabling users to increase or decrease the sensitivity of fingerprint recognition to accommodate different finger pressures or skin conditions. |
| Large Touch Targets | Using larger touch targets for biometric input to make them easier for users with limited dexterity to interact with. | Increasing the size of the fingerprint sensor or facial recognition area for users with motor impairments. |
| Haptic Feedback | Providing tactile feedback to indicate success or failure in the authentication process. | Using vibrations or subtle bumps on a device to signal successful or unsuccessful authentication. |
| Clear Instructions | Providing clear and concise instructions and prompts for the biometric authentication process. | Using simple, easy-to-understand language and visual cues to guide users through the authentication process. |
Future Trends and Predictions
Biometric authentication is rapidly evolving, and its integration into messaging apps like WhatsApp is poised to reshape the future of digital security and user experience. The potential for enhanced security and user convenience is significant, but careful consideration of privacy implications is crucial. Emerging technologies and the integration of AI are factors that will drive the evolution of this field.
Potential of Biometric Authentication in Messaging Apps
The future of biometric authentication in messaging apps extends beyond the current fingerprint and face recognition methods. WhatsApp, like other platforms, will likely explore more advanced biometric technologies to further enhance security and streamline user experience. This evolution is expected to encompass a broader range of user needs and preferences, resulting in a more personalized and secure platform. Improved user trust in digital communication and seamless access to accounts are significant benefits.
Emerging Biometric Technologies for WhatsApp
Several emerging biometric technologies could be integrated into WhatsApp, each with its unique strengths and weaknesses. These include liveness detection techniques that verify the biometric sample is from a live user, and potentially even behavioral biometrics, which analyzes typing patterns or voice recognition. These advancements aim to prevent spoofing attempts and strengthen security. Liveness detection is particularly important in countering sophisticated attacks and safeguarding user accounts.
Behavioral biometrics can provide another layer of security, particularly in situations where visual biometrics might be compromised.
AI Integration for Enhanced Biometric Security
AI plays a crucial role in enhancing biometric security. AI algorithms can analyze biometric data in real-time, adapting to user variations in posture, lighting conditions, or device positioning. This dynamic adaptation significantly improves accuracy and reduces false rejections. AI can also analyze patterns in user behavior to detect anomalies, potentially alerting users to suspicious activity. The ability to continuously learn and adapt to user patterns is key to the success of this integration.
Impact on User Privacy in the Future
The integration of advanced biometric technologies raises important privacy concerns. Transparency in data collection and usage, alongside robust data encryption protocols, are crucial for building user trust. Detailed privacy policies explaining how data is collected, used, and protected are necessary to maintain user confidence. Strict adherence to data protection regulations and user consent mechanisms is paramount to maintaining user trust.
Potential Future Integration of Emerging Biometric Technologies
| Technology | Potential Integration in WhatsApp | Security Advantages | Privacy Considerations |
|---|---|---|---|
| Liveness Detection (e.g., thermal imaging) | Verification of user’s presence during authentication | Reduced risk of spoofing attempts | Potential for data collection and privacy concerns if not handled responsibly |
| Behavioral Biometrics (e.g., typing patterns) | Additional layer of security, especially for compromised visual biometrics | Increased security against impersonation | Privacy implications of tracking and storing typing patterns |
| Voice Recognition | Authentication and authorization in specific contexts | Enhanced security in scenarios where visual biometrics may be unavailable or difficult | Potential for privacy concerns related to voice data collection and storage |
| Multi-Factor Authentication (MFA) | Integration with existing authentication protocols | Strengthened security through combination of biometric and traditional methods | Additional steps for user experience may be required, so ease of use should be considered |
Wrap-Up
In conclusion, the introduction of WhatsApp biometric authentication for desktop browsers represents a significant step forward in digital security. While challenges remain, the potential benefits of enhanced security and convenience are substantial. This exploration highlights the complexities and considerations surrounding the implementation of biometrics, ensuring a robust and user-friendly experience. The future of messaging app security may very well hinge on the success of this innovative approach.