VM series technology and virtual firewall ROI are critical for modern businesses seeking enhanced security and efficiency. This in-depth exploration delves into the core functionalities of VM series technology, examining its evolution and various use cases. We’ll analyze different virtual firewall mechanisms, comparing their performance, scalability, and security features. Crucially, we’ll demonstrate a structured method for assessing the return on investment (ROI) of implementing VM series technology, considering factors like hardware, software, and personnel costs.
We’ll also discuss the integration process and present practical examples and case studies, ultimately helping you understand the potential benefits and challenges of this technology.
Introduction to VM Series Technology
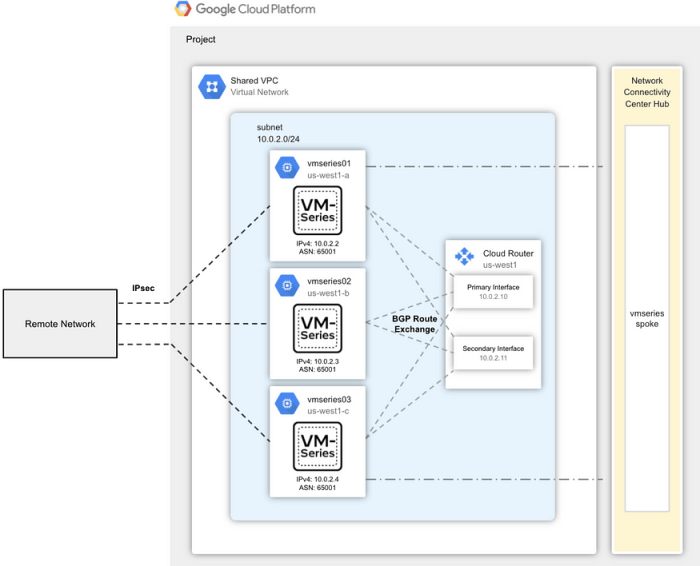
Virtual Machine (VM) series technology has revolutionized the way businesses and individuals deploy and manage computing resources. It allows for the creation of multiple virtual machines (VMs) on a single physical server, significantly increasing resource utilization and flexibility. This approach dramatically reduces hardware costs and simplifies management, leading to substantial operational efficiencies.VM series technology is a cornerstone of cloud computing and modern data centers.
It enables organizations to easily scale resources up or down based on demand, making it an invaluable tool for dynamic workloads and fluctuating resource needs. The ability to quickly provision and deploy VMs is a key advantage in today’s fast-paced IT landscape.
Core Functionalities and Key Features
VM series technology provides a suite of functionalities for virtualizing and managing computing resources. These functionalities include the creation, deployment, and management of VMs. Key features include hardware virtualization, enabling multiple operating systems to run concurrently on a single physical server, and resource isolation to prevent interference between VMs. Security features like access control and encryption are essential for protecting sensitive data.
VM series technology and virtual firewall ROI are crucial for modern security. Understanding the potential attack vectors, like those highlighted in the Unit42 attack surface threat report , is key to maximizing ROI. This report underscores the need for robust defenses, which is exactly what VM series technology and virtual firewalls provide.
Efficient resource allocation and management are key to maintaining optimal performance.
Evolution and Advancements
The evolution of VM series technology has been marked by continuous advancements in virtualization technologies. Early VM implementations were often limited in terms of performance and scalability. Over time, advancements in hypervisor technology and hardware support have significantly improved VM performance, stability, and resource utilization. Improvements in networking capabilities and storage integration have enabled more complex and sophisticated applications to run within VMs.
Use Cases and Applications
VM series technology finds diverse applications across various industries. It’s widely used for web hosting, providing scalable and cost-effective solutions for hosting websites and web applications. In data centers, VMs enable efficient resource utilization, improving performance and reducing hardware costs. VM series technology is also crucial for software development and testing, allowing developers to quickly create and deploy test environments.
Furthermore, disaster recovery and business continuity plans rely on VM technology to replicate and recover systems quickly and efficiently.
Architecture and Components of a Typical VM Series System, Vm series technology and virtual firewall roi
A typical VM series system comprises several key components. The hypervisor is the core component, acting as a layer between the physical hardware and the virtual machines. The hypervisor manages the allocation of resources to each VM, ensuring smooth operation and preventing interference. Virtualized storage solutions are integral to storing VM data and configurations. Networking components allow VMs to communicate with each other and the external network.
Management tools provide the interface for monitoring and managing the entire VM environment.
Illustrative Diagram
+-----------------+ +-----------------+ +-----------------+
| Physical Server |---->| Hypervisor |---->| Virtual Machine 1|
+-----------------+ +-----------------+ +-----------------+
| (Hardware) | | (Virtualization) | | (OS & Apps) |
+-----------------+ +-----------------+ +-----------------+
|
|
|--------> Virtual Machine 2
|
|
|--------> Virtual Machine n
|
|
|
+-----------------+ +-----------------+ +-----------------+
| Network |-----| Storage |-----| Management Tools|
+-----------------+ +-----------------+ +-----------------+
This diagram illustrates the core components of a VM series system.
The physical server houses the hypervisor, which in turn manages multiple virtual machines. These VMs run their own operating systems and applications, effectively sharing the underlying physical hardware resources. The network, storage, and management tools are crucial components for communication, data storage, and system oversight.
Virtual Firewall Mechanisms
Virtual firewalls are a crucial component of modern VM series technology, providing a critical layer of security for virtualized environments. They act as gatekeepers, controlling network traffic and preventing unauthorized access to virtual machines. Understanding the different mechanisms employed within these virtual firewalls is essential for effective security implementation and optimization. Their function is to enforce security policies, filter traffic, and protect the integrity of virtualized resources.
Different Virtual Firewall Mechanisms
VM series technology utilizes various virtual firewall mechanisms to achieve robust security. These mechanisms can be categorized based on their functionality and implementation. Different mechanisms offer varying levels of performance, scalability, and security, impacting the overall effectiveness of the virtual firewall solution. A well-chosen mechanism aligns with the specific needs and requirements of the virtualized environment.
Firewall Technologies and Their Strengths/Weaknesses
Several firewall technologies are employed in virtualized environments, each with unique strengths and weaknesses. Packet filtering firewalls, for example, examine network packets based on predefined rules. They are relatively simple to configure and offer fast performance but can be susceptible to attacks if the rules are not carefully crafted. Stateful inspection firewalls, on the other hand, track the context of network connections, providing enhanced security by detecting malicious activity.
However, this increased scrutiny can sometimes lead to decreased performance. Application firewalls go a step further, inspecting application-layer traffic for malicious intent. This detailed examination offers high security but can significantly impact performance, especially for complex applications. The choice of firewall technology depends on the specific security needs and performance constraints of the virtualized environment.
Security Protocols Supported by VM Series Virtual Firewalls
VM series virtual firewalls support a range of security protocols. These protocols, like TCP/IP, UDP, and ICMP, are fundamental to network communication and must be managed securely within the virtual environment. More advanced protocols, such as SSL/TLS for secure communication, and SSH for remote access, are often supported as well. Supporting these protocols ensures that virtual machines can communicate securely while being protected from unauthorized access.
Furthermore, the virtual firewalls often support specific protocols related to virtualized network traffic, such as VXLAN and other overlay networking protocols.
Comparison of Virtual Firewall Solutions
| Firewall Feature | Solution A (Packet Filtering) | Solution B (Stateful Inspection) | Solution C (Application Layer) |
|---|---|---|---|
| Performance | High | Medium | Low |
| Scalability | Good | Excellent | Moderate |
| Security | Low | High | Very High |
Benefits and Drawbacks of Each Firewall Mechanism
Different firewall mechanisms present unique advantages and disadvantages. Packet filtering firewalls, while fast, lack the sophisticated security features of stateful inspection or application-layer firewalls. Stateful inspection firewalls, with their superior security, may come at the cost of reduced performance. Application-layer firewalls offer the highest security level but may struggle to handle high volumes of traffic. The selection of the right mechanism is crucial for optimal security and performance within a virtualized environment.
It is important to carefully consider the specific security needs and performance constraints before selecting a particular virtual firewall mechanism.
ROI Assessment for VM Series Technology
Virtual machine (VM) series technology offers compelling advantages, but its true value hinges on a thorough ROI assessment. Understanding the potential financial benefits and costs is crucial for making informed decisions about adoption. This section delves into the structured methodology for evaluating the return on investment of VM series technology, providing key metrics, influential factors, and a practical example to illustrate the calculation.
Structured ROI Assessment Methodology
A robust ROI assessment begins with clearly defined objectives. These objectives should encompass quantifiable goals, such as increased efficiency, reduced operational costs, or enhanced security. Next, a baseline assessment of existing infrastructure is necessary. This includes current hardware, software, and personnel costs, as well as operational processes. A detailed analysis of the potential benefits and costs of implementing VM series technology is then required.
This phase should encompass the predicted performance improvements, the cost of implementing and maintaining the new system, and the anticipated return on investment. Finally, the assessment should include a realistic timeline for the implementation and anticipated payback period. By employing this structured methodology, organizations can effectively measure the ROI of VM series technology.
Key Metrics for Measuring ROI
Several key metrics are essential for accurately measuring the ROI of VM series technology. These metrics provide a comprehensive picture of the financial impact. The most significant include:
- Cost Savings: Quantify the reduction in hardware, software, and operational costs associated with the new VM series system. This includes the cost of licenses, maintenance, and power consumption.
- Increased Efficiency: Measure the improved performance metrics, such as processing speed, response times, and throughput. This can be translated into cost savings through reduced processing time or increased productivity.
- Improved Scalability: Evaluate the flexibility and adaptability of the VM series technology to accommodate future growth and changing business needs. This translates into reduced costs associated with upgrading or expanding existing infrastructure.
- Enhanced Security: Assess the enhanced security posture provided by the VM series technology. This includes the reduction in vulnerabilities, improved data protection, and reduced security incidents. This is a difficult metric to quantify but can be demonstrated through reduced incident response costs and improved compliance with security regulations.
- Reduced Downtime: Quantify the reduction in system downtime and disruptions. This metric translates to avoiding lost productivity and revenue.
Factors Influencing ROI
Several factors influence the ROI of VM series technology implementations. These factors need to be considered in a holistic assessment:
- Complexity of the Implementation: The more complex the migration to a VM series environment, the longer the implementation time and the higher the associated costs. Thorough planning and preparation can mitigate these costs.
- Skill Set of the Personnel: The level of expertise of the IT staff responsible for managing the VM series environment significantly affects the efficiency of the implementation and its long-term success. Training and upskilling are vital.
- Hardware Requirements: The specific hardware requirements for the VM series technology, including storage and processing capabilities, will affect the overall cost of implementation and maintenance.
- Software Compatibility: The compatibility of the existing applications with the VM series platform is a critical factor. Migrating applications to a VM series environment may require significant adjustments or modifications.
- Security Considerations: Proper security measures are crucial in VM series environments. The cost of security solutions, including firewalls and intrusion detection systems, needs to be factored in.
Calculating Potential ROI for a Specific Use Case
Consider a company migrating its 10 servers to a VM series solution. The current annual cost of server maintenance is $20,
000. The VM series solution requires a one-time investment of $10,000 for software licenses and $5,000 for initial setup. Assuming a 5-year payback period and a 10% annual savings in operational costs, the potential ROI is calculated as follows:
Annual Savings = Current Annual Cost x Savings Percentage = $20,000 x 0.10 = $2,000
Total Savings over 5 Years = Annual Savings x Number of Years = $2,000 x 5 = $10,000
Total Investment = Software Cost + Setup Cost = $10,000 + $5,000 = $15,000
Potential ROI = Total Savings over 5 Years – Total Investment = $10,000 – $15,000 = -$5,000
This example demonstrates that in this particular use case, the implementation of VM series technology does not result in a positive return on investment. Further analysis is needed to determine whether the expected benefits can offset the higher initial costs.
Comparing ROI of VM Series Against Traditional Solutions
Traditional on-premise solutions often have higher upfront costs for hardware but lower recurring costs for software and maintenance. VM series technology usually involves lower hardware costs in the long term but higher initial software and setup costs. The choice between the two depends on specific needs and circumstances. A thorough analysis of costs and benefits is essential to determine the optimal solution.
Potential Costs and Benefits of Adopting VM Series Technology
| Category | Cost | Benefit |
|---|---|---|
| Hardware | Lower initial investment for servers (virtualized). | Reduced long-term hardware maintenance and upgrades. |
| Software | Higher initial software licensing costs. | Increased flexibility and scalability. |
| Personnel | Potential need for additional training for staff to manage the virtualized environment. | Increased efficiency and potential for reduced staffing costs over time through automation. |
VM Series Technology and Virtual Firewall Integration
Integrating VM Series technology with virtual firewalls is crucial for modern network security. This seamless integration allows for enhanced control and visibility across virtualized environments. It significantly improves security posture by enabling centralized management and policy enforcement. The process requires careful planning and configuration to ensure optimal performance and prevent potential conflicts.
The integration process typically involves several key steps. First, the virtual firewall must be configured to recognize and interact with the VM Series environment. This usually entails defining the network segments and rules that govern traffic flow between virtual machines and the external network. Second, the VM Series platform must be configured to support the virtual firewall’s policies.
This involves setting up communication channels and integrating security policies. The result is a unified security approach that protects virtualized resources effectively.
Integration Process Overview
The integration process involves several key stages, starting with the assessment of the current network infrastructure and the desired security posture. This crucial initial step informs the configuration choices that follow.
Step-by-Step Integration Guide
- Assessment of Existing Infrastructure: Evaluate the current network topology, including virtualized environments and existing security measures. Identify potential integration points and limitations. This initial assessment is essential for planning and ensuring compatibility between the VM Series and virtual firewall.
- Virtual Firewall Configuration: Configure the virtual firewall to recognize and interact with the VM Series environment. This involves defining network segments, rules, and policies for virtual machines. These policies should align with the overall security strategy for the organization. Examples include allowing specific ports for application traffic or blocking certain IP addresses.
- VM Series Configuration: Configure the VM Series platform to support the virtual firewall’s policies. This involves setting up communication channels between the VM Series and the virtual firewall. Configure the necessary network interfaces and virtual network connections. This ensures that the virtual firewall can effectively manage traffic between virtual machines.
- Testing and Validation: Thoroughly test the integration to ensure that the virtual firewall and VM Series platform are functioning correctly. This step includes testing traffic flow, verifying policy enforcement, and identifying any potential issues. This critical step helps identify any problems before deployment.
- Deployment and Monitoring: Deploy the integrated solution and establish monitoring procedures to track performance and identify any potential problems. Regular monitoring ensures that the system remains secure and efficient.
Configuration Options
Various configuration options are available to tailor the integration to specific needs. These include:
- Network Segmentation: Define specific network segments for virtual machines, enabling granular control over traffic flow and enhancing security.
- Firewall Rules: Configure rules to allow or block specific traffic based on source/destination IP addresses, ports, and protocols. These rules are crucial for controlling access to and from virtual machines.
- Security Policies: Implement security policies to define access control, authentication, and logging mechanisms. These policies ensure consistent security practices across the entire virtualized environment.
- Monitoring Tools: Leverage monitoring tools to track traffic patterns, identify potential security breaches, and ensure optimal performance. These tools are vital for continuous oversight of the integrated system.
Flowchart of Integration Process

The flowchart illustrates the steps involved in integrating VM Series technology with virtual firewalls, highlighting the iterative nature of the process. The process emphasizes testing and validation to prevent unexpected issues after deployment.
Practical Examples and Case Studies
VM series technology and virtual firewalls are rapidly transforming network security and management. Understanding how these technologies have been implemented in real-world scenarios is crucial for evaluating their potential impact. This section presents case studies showcasing successful deployments, highlighting challenges overcome, and the resulting benefits.
VM series technology and virtual firewall ROI are crucial for businesses looking to streamline security. While exploring these solutions, I stumbled upon a helpful fix for a screen tinting issue on the OnePlus Nord, detailed in this excellent guide: oneplus nord has screen tinting issue fix way. This highlights the importance of reliable technical solutions, which ultimately ties back into the effective use of VM series technology and the return on investment from virtual firewalls.
Real-World Examples of VM Series Technology Implementation
Numerous organizations across various industries have successfully deployed VM series technology, achieving significant improvements in efficiency, security, and cost savings. These implementations often involve migrating existing physical servers to virtual machines, enabling greater flexibility and resource utilization. For example, a financial institution might leverage VM series to consolidate multiple data centers into a single, centralized virtual environment.
Case Studies of Successful Deployments
One notable case study involves a medium-sized e-commerce company that transitioned from a traditional physical server infrastructure to a virtualized environment using VM series technology. This migration enabled the company to reduce hardware costs by 30% while simultaneously improving operational efficiency. The company also implemented a virtual firewall solution, enhancing security and reducing vulnerabilities. By automating routine tasks, the company reduced the workload on its IT staff and freed them up to focus on strategic initiatives.
Challenges Encountered and How They Were Overcome
Implementing VM series technology and virtual firewalls isn’t always straightforward. One common challenge is ensuring compatibility between existing applications and the new virtualized environment. Thorough planning, testing, and careful migration strategies can mitigate this risk. Another challenge involves managing the increased complexity of a virtualized infrastructure. Implementing robust monitoring tools and establishing clear procedures for troubleshooting can address this concern.
VM series technology and virtual firewall ROI are crucial for businesses, but sometimes you need a little extra juice for your mobile devices. Finding the best battery packs for your Galaxy S6, like those detailed in this helpful guide, best battery packs your galaxy s6 , can be a game-changer for productivity. Ultimately, optimizing your tech, from mobile to server-level solutions, is key to efficiency and return on investment.
The e-commerce company, for instance, addressed compatibility issues through rigorous testing and application re-configuration. They overcame the complexity challenge by implementing a dedicated team to manage the virtual environment and provide support.
Impact on Efficiency, Security, and Cost Savings
VM series technology and virtual firewalls often lead to significant improvements in efficiency, security, and cost savings. By centralizing resources and automating processes, these technologies can streamline operations and reduce manual intervention. Enhanced security features within virtual firewalls often lead to a reduced attack surface and improved overall security posture. The e-commerce company, for example, experienced a 20% reduction in IT operational costs and a 15% improvement in security posture following the implementation.
Summary of Key Takeaways from Case Studies
| Case Study | Description | Impact |
|---|---|---|
| E-commerce Company | Migrated from physical to virtual infrastructure, implemented virtual firewalls. | 30% reduction in hardware costs, 20% reduction in IT operational costs, 15% improvement in security posture, improved operational efficiency. |
| Financial Institution (Hypothetical) | Consolidated multiple data centers into a centralized virtual environment using VM series technology. | Potential for increased scalability, reduced operational costs, and enhanced security. |
Future Trends and Considerations: Vm Series Technology And Virtual Firewall Roi
The landscape of virtual machine (VM) series technology and virtual firewalls is constantly evolving. Understanding emerging trends, potential challenges, and the role of cloud computing and automation is crucial for organizations seeking to leverage these technologies effectively. This section explores the future trajectory of these critical security components.
The adoption of virtualization has led to a significant increase in the complexity of network security. Virtual firewalls are now essential for isolating and securing virtualized environments, but the future demands even more sophisticated solutions. This evolution necessitates a forward-looking approach that anticipates the needs of tomorrow’s data centers and cloud deployments.
Emerging Trends in VM Series Technology
VM series technology is rapidly evolving, driven by advancements in cloud computing, containerization, and the increasing need for security. Key trends include the integration of AI and machine learning for automated threat detection and response, and the rise of serverless computing, which will demand new approaches to security management. These developments highlight the need for dynamic and adaptive security solutions.
Future Direction of Virtual Firewall Technology
Virtual firewall technology is progressing toward greater automation and integration with other security tools. Expect to see an increase in the use of software-defined networking (SDN) and network function virtualization (NFV) to enhance flexibility and scalability. This will allow for more granular control over network traffic and faster response times to security threats.
Potential Future Challenges and Opportunities Related to VM Series Technology
The increasing complexity of virtualized environments presents both challenges and opportunities. Challenges include the need for robust security policies and tools that can adapt to dynamic environments. Opportunities include the potential for enhanced security and efficiency through automation, and the ability to quickly scale resources to meet changing demands.
Role of Cloud Computing and Automation in VM Series Deployments
Cloud computing and automation are crucial for streamlining VM series deployments and managing the associated complexity. Cloud platforms provide a scalable infrastructure that can accommodate fluctuating demands. Automation tools will be critical for tasks such as provisioning, patching, and monitoring, allowing for faster deployment and more efficient management. The combination of these two technologies will lead to increased agility and reduced operational overhead.
Final Thoughts
In conclusion, VM series technology and virtual firewall ROI offer significant advantages, but careful consideration of implementation details is essential. By understanding the various virtual firewall mechanisms, assessing ROI, and integrating them seamlessly, organizations can unlock substantial efficiency gains and enhanced security. Future trends and considerations are also important to navigate the evolving landscape of cloud-based solutions. The provided examples and case studies offer practical insights, empowering you to make informed decisions about adopting this powerful technology.