Top security orchestration use cases are rapidly transforming how organizations approach cybersecurity. From automating incident responses to streamlining compliance, these powerful tools offer a wide range of benefits. This exploration dives deep into the practical applications of security orchestration, highlighting its crucial role in modern threat landscapes.
Security orchestration platforms aren’t just about automating tasks; they’re about proactively addressing security vulnerabilities. By connecting various security tools and processes, orchestration creates a unified approach to threat detection, response, and management. This allows organizations to not only react faster but also to anticipate and mitigate potential risks more effectively.
Introduction to Security Orchestration
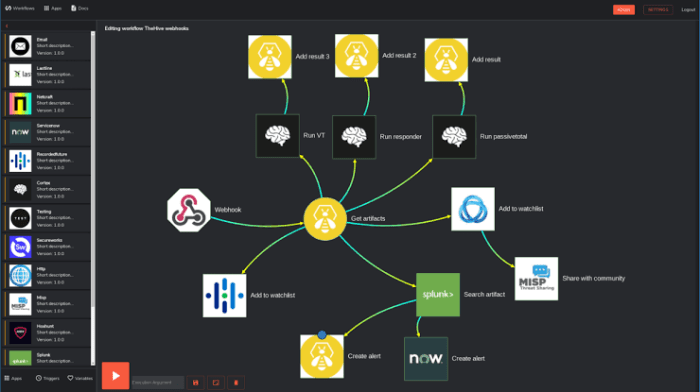
Security orchestration is a crucial component in modern cybersecurity. It automates the response to security incidents by integrating various security tools and platforms. This approach streamlines incident response processes, improves threat detection, and reduces the time it takes to remediate vulnerabilities. Effectively orchestrating security operations enhances overall security posture, leading to faster incident resolution and reduced business impact.The core concepts behind security orchestration revolve around automating security tasks and streamlining workflows.
This involves defining predefined sequences of actions to be performed in response to specific security events. Security orchestration platforms facilitate communication and collaboration between various security tools and systems, enabling a more unified and efficient approach to incident management. The goal is to automate responses to known threats and reduce manual intervention, which can significantly enhance security posture.
Top security orchestration use cases often involve streamlining complex processes. For instance, imagine a scenario where a bookstore like bookshop.org, with its focus on independent authors, faces a surge in online sales, and needs to quickly scale security measures. This might involve analyzing customer data, identifying potential threats, and proactively implementing new security protocols. This is similar to the challenges faced by independent authors like Andy Hunter and how they navigate the Amazon ebook monopoly, discussed in this great article on bookshop org andy hunter amazon ebooks monopoly books.
Ultimately, these use cases highlight the critical need for robust security orchestration tools to manage and adapt to ever-changing digital landscapes.
Core Concepts and Principles
Security orchestration is built upon the principles of automation, integration, and collaboration. Automation streamlines the response to security incidents by defining predefined workflows and actions. Integration ensures seamless communication and data sharing between different security tools. Collaboration facilitates coordinated responses by multiple security teams. These principles are crucial for effective incident management and response.
Types of Security Orchestration Platforms
Security orchestration platforms come in various forms, each with its own strengths and weaknesses. There are platform-as-a-service (PaaS) offerings, where users leverage a cloud-based solution. On-premise solutions provide greater control over infrastructure, while hybrid solutions combine elements of both. Choosing the right platform depends on the organization’s specific needs, budget, and technical expertise.
Benefits of Employing Security Orchestration
Implementing security orchestration offers numerous benefits. It improves efficiency by automating tasks, reduces response time to security incidents, and enhances the overall security posture. Automation of repetitive tasks frees up security analysts to focus on more strategic initiatives. Moreover, better collaboration and communication among security teams lead to more coordinated and effective responses to threats. This approach enhances visibility into security events, facilitating quicker threat detection and response.
Comparison of Security Orchestration Platforms
| Feature | Platform A | Platform B | Platform C |
|---|---|---|---|
| Detection capabilities | Supports various detection mechanisms, including SIEM and network analysis | Specialized in threat intelligence and advanced malware detection | Focuses on cloud security threats and anomalies |
| Pricing | Subscription-based model with tiered pricing | Pay-as-you-go pricing with variable costs | Per-user pricing with additional charges for advanced features |
| Deployment Options | Cloud-based deployment | On-premise and cloud-based deployment options | Hybrid deployment supported |
This table provides a high-level comparison of three hypothetical security orchestration platforms. The specific features, pricing, and deployment options of each platform may vary depending on the vendor and their product offerings. Organizations should carefully evaluate the specific needs and requirements of their environment when choosing a platform.
Top security orchestration use cases are all about streamlining security processes, and a big part of that is making sure everything works together seamlessly. However, issues like the incompatibility between iOS 16 iMessage’s edit message feature and previous iOS versions highlight the complexities of maintaining interoperability across different software versions, which is a similar challenge in security orchestration.
Security orchestration tools need to account for these evolving standards to ensure a consistent security posture across the board. iOS 16 iMessage edit messages incompatible previous versions of iOS is a good example of this kind of interoperability problem. Ultimately, effective security orchestration relies on robust solutions that adapt to these dynamic changes.
Common Use Cases for Security Orchestration: Top Security Orchestration Use Cases

Security orchestration platforms are rapidly becoming crucial for organizations seeking to enhance their security posture. These platforms go beyond simple security tools by automating and coordinating responses to security incidents. This automation not only saves valuable time and resources but also improves the effectiveness of security teams in reacting to threats. The power of orchestration lies in its ability to connect various security tools and processes, streamlining incident management and enhancing overall security.Security orchestration platforms are no longer a futuristic concept but a practical necessity for modern organizations.
Their ability to integrate disparate security tools, automate responses, and provide centralized visibility into security events is transforming how security teams operate. Real-world use cases demonstrate the significant advantages of this approach, including faster incident resolution, reduced risk, and enhanced threat detection capabilities.
Threat Hunting and Incident Response Automation
Security orchestration significantly enhances threat hunting and incident response by automating repetitive tasks and enabling faster identification and containment of threats. This automation is critical for keeping pace with the ever-evolving threat landscape. By automating tasks such as data collection, analysis, and response, security teams can focus on higher-level strategic activities.
Vulnerability Management Automation
Security orchestration platforms enable automated vulnerability management processes. This automation streamlines the identification, assessment, and remediation of vulnerabilities across an organization’s IT infrastructure. The ability to automate these tasks significantly improves the efficiency of vulnerability management programs, enabling quicker remediation and minimizing potential security breaches. This automation allows for proactive identification and mitigation of vulnerabilities, preventing potential exploitation.
Top security orchestration use cases are all about streamlining security operations. From automating incident response to proactively identifying vulnerabilities, these tools are game-changers. Think of it like upgrading your security infrastructure to a fully automated blacksmith, much like the cool Shovel Knight Blacksmith Man at Arms Watch here. This intricate timepiece, while a bit fantastical, highlights the precision and efficiency that these security orchestration tools can bring to bear, allowing for more focused and proactive security measures.
Security Information and Event Management (SIEM) Integration
Security orchestration platforms effectively integrate with SIEM systems. This integration facilitates a comprehensive view of security events, enabling a unified security operations center (SOC). The automation of threat detection and response tasks allows for proactive identification and mitigation of security risks. By centralizing security data and automating incident response processes, orchestration significantly enhances threat detection capabilities.
Compliance and Audit Automation
Security orchestration platforms facilitate the automation of compliance and audit processes. This automation ensures that security controls are consistently implemented and maintained, reducing the risk of non-compliance. The ability to automate these tasks significantly improves efficiency and reduces the time and resources needed for compliance and audit activities. By automating compliance-related tasks, organizations can proactively ensure their adherence to regulatory standards.
Table Comparing and Contrasting Use Cases
| Use Case | Specific Security Needs | How Orchestration Addresses Needs |
|---|---|---|
| Threat Hunting and Incident Response | Rapid threat detection, efficient incident response, automation of repetitive tasks. | Automates data collection, analysis, and response procedures, enabling faster containment and resolution. |
| Vulnerability Management | Proactive identification and remediation of vulnerabilities, efficient tracking of vulnerabilities, consistent remediation process. | Automates vulnerability scanning, assessment, and remediation tasks, leading to faster resolution and reduced risk. |
| SIEM Integration | Unified view of security events, automated threat detection, centralized security operations. | Connects various security tools and processes to provide a centralized security operations center (SOC), improving threat detection and response. |
| Compliance and Audit | Ensuring consistent implementation of security controls, timely completion of audits, reduced compliance risks. | Automates compliance-related tasks and processes, ensuring adherence to regulatory standards and improving audit efficiency. |
Threat Detection and Response
Security orchestration significantly enhances threat detection and response capabilities by automating and streamlining the entire process. This approach transforms reactive security postures into proactive ones, enabling faster incident resolution and reduced attack impact. By connecting disparate security tools and automating workflows, orchestration empowers organizations to identify threats more effectively and respond to them with precision and speed.
Improving Threat Detection Capabilities
Security orchestration platforms consolidate data from various security tools, such as firewalls, intrusion detection systems (IDS), and security information and event management (SIEM) systems. This centralized view provides a comprehensive picture of security events, enabling the identification of subtle patterns and anomalies that might be missed by individual tools. Sophisticated correlation and analysis capabilities within orchestration platforms help to identify potential threats earlier and with greater accuracy.
For example, if an IDS detects a suspicious login attempt from an unusual IP address, and a SIEM identifies a corresponding increase in network traffic from the same IP, orchestration can immediately flag this as a potential malicious activity.
Automating Threat Responses
Orchestration automates the response to detected threats. Once a threat is identified, the orchestration platform can trigger predefined actions, such as blocking malicious IPs, quarantining infected systems, or initiating incident response procedures. This automation dramatically reduces the time it takes to respond to security incidents, minimizing the window of vulnerability and the potential for damage. For example, if a malware sample is identified, the orchestration platform can automatically quarantine the affected systems and notify the relevant personnel.
Incident Response Workflows
Security orchestration plays a vital role in streamlining incident response workflows. Orchestration platforms can automate the entire incident response lifecycle, from detection and analysis to containment and remediation. This automation ensures that incident response procedures are consistently followed and that critical tasks are completed efficiently. The platform can trigger predefined tasks based on predefined rules and criteria, enabling faster response times and minimizing human error.
For instance, a malicious email campaign could trigger an automated workflow that quarantines infected user accounts, notifies affected users, and automatically updates security protocols.
Improving Security Posture and Reducing Response Time
By automating tasks, security orchestration dramatically reduces response time to security incidents. This translates to a significant improvement in security posture, minimizing the time a system remains vulnerable and the potential for damage. The speed and precision of automated responses, guided by predefined rules and procedures, minimize the risk of human error and ensure a more effective and efficient response to threats.
Reduced response time also contributes to faster remediation and minimizes the attack surface. Organizations can maintain a proactive security posture and mitigate risks.
Threat Detection Methods and Orchestration
| Threat Detection Method | Orchestration Tools/Techniques | Description |
|---|---|---|
| Network Intrusion Detection | SIEM integration, Network traffic analysis, Anomaly detection | Orchestration tools can correlate network traffic patterns with known attack signatures to identify malicious activity. |
| Endpoint Detection and Response (EDR) | EDR integration, File integrity monitoring, User behavior analysis | Orchestration platforms can aggregate data from multiple EDR sources to identify and respond to malicious activities on endpoints. |
| Vulnerability Management | Vulnerability scanning integration, Patch management automation | Orchestration tools can automate the process of identifying vulnerabilities, prioritizing remediation efforts, and deploying patches. |
| Security Information and Event Management (SIEM) | Correlation analysis, Alert prioritization, Automated incident response | Orchestration can integrate with SIEM to correlate security events and automate incident response procedures based on predefined rules. |
Security Information and Event Management (SIEM) Integration
Security orchestration platforms, while powerful in their own right, gain significantly from integration with Security Information and Event Management (SIEM) systems. This combination creates a more comprehensive and effective security posture by leveraging the strengths of both technologies. SIEMs excel at collecting and correlating security events, while orchestration platforms excel at automating responses to these events. The synergy between these two systems allows for a more proactive and automated approach to security.Integrating security orchestration with SIEM systems allows for a unified view of security events, enabling quicker identification and response to threats.
By correlating data from various sources, including SIEM logs, the orchestration platform can create a more holistic picture of the security landscape. This integrated approach empowers security teams to move beyond reactive measures and implement proactive threat detection and response strategies.
Significance of SIEM Integration
SIEM systems are foundational for security information gathering. They collect logs from various security devices, such as firewalls, intrusion detection systems, and endpoint security tools. These logs, when correlated and analyzed, reveal patterns that can indicate potential threats or vulnerabilities. By integrating with orchestration platforms, SIEMs provide a wealth of data for automated responses, dramatically improving threat detection and response times.
Connecting and Leveraging SIEM Data
The process of connecting and leveraging data from SIEM systems involves several key steps. First, the orchestration platform establishes a connection with the SIEM. This connection allows the platform to pull data in real-time or at scheduled intervals. Second, the orchestration platform identifies relevant security events based on predefined rules and thresholds from the SIEM. Third, the orchestration platform automatically triggers pre-configured response actions based on these events.
For example, if a suspicious login attempt is detected, the orchestration platform can automatically block the IP address, alert the security team, and even initiate a forensic investigation.
Enhancing Security Event Analysis
Security orchestration enhances the analysis of security events by providing a centralized platform for correlating events from multiple sources. Instead of manually analyzing logs from various systems, the orchestration platform correlates events from the SIEM with other security data, creating a more complete picture of the threat. This consolidated view allows security teams to quickly identify and prioritize threats, enabling faster and more effective responses.
For instance, the orchestration platform can identify a series of failed login attempts from the same IP address, correlated with unusual network traffic patterns, and flag this as a potential brute-force attack.
Benefits of a Unified Security Platform
A unified security platform, combining orchestration and SIEM, provides numerous benefits. It automates security tasks, such as incident response and threat hunting, resulting in reduced response times. It provides a centralized view of the security posture, improving threat visibility. It enhances collaboration between security teams, fostering a more efficient and coordinated approach to security. Furthermore, a unified platform can improve compliance by providing a comprehensive audit trail and detailed reporting capabilities.
Integration Flowchart
(Example Flowchart depicting the integration of Security Orchestration and SIEM. The flowchart would illustrate the process of data collection from the SIEM, event filtering, trigger actions based on defined rules, and notification/response mechanisms.)
Compliance and Audit Management
Security orchestration platforms are rapidly becoming essential tools for organizations seeking to navigate the complex landscape of compliance regulations. These platforms provide a centralized and automated approach to managing and monitoring security posture, which directly supports compliance efforts. This streamlined process not only reduces manual effort but also minimizes the risk of human error, leading to a more robust and reliable compliance framework.Security orchestration goes beyond simply logging events; it empowers organizations to proactively identify and address potential compliance violations.
This proactive approach fosters a culture of compliance and reduces the likelihood of costly penalties and reputational damage. By automating key compliance-related tasks, security orchestration ensures that organizations maintain a consistent and reliable compliance posture.
Facilitating Compliance with Industry Regulations
Security orchestration platforms provide a comprehensive framework for meeting various industry regulations. By automating the collection, analysis, and reporting of security data, these platforms enable organizations to demonstrate compliance with regulations like HIPAA, GDPR, PCI DSS, and others. The automated workflows ensure consistent data collection and reporting, crucial for demonstrating compliance. These automated processes allow organizations to meet regulatory requirements more efficiently and effectively.
Automating Audit Processes
Security orchestration platforms significantly enhance the efficiency of audit processes. Instead of manually collecting and reviewing logs, organizations can leverage the platform’s automated workflows to generate audit reports and identify potential compliance gaps. This automation not only saves time and resources but also reduces the risk of human error, enhancing the accuracy and reliability of audit findings. Automating audit processes ensures that all necessary data is gathered and analyzed, minimizing the potential for missing critical information.
Maintaining Compliance Records
Security orchestration platforms play a critical role in maintaining detailed and accurate compliance records. These platforms store and organize audit logs, security events, and other relevant information in a centralized repository. This centralized repository ensures that all necessary information is readily accessible for audits and regulatory reviews. This streamlined approach to record-keeping simplifies the process of demonstrating compliance, ensuring that all necessary information is readily available.
Streamlining Compliance Procedures
Security orchestration platforms streamline compliance procedures by automating various tasks, reducing manual effort, and improving efficiency. This automated workflow not only reduces the workload of security teams but also ensures consistency and accuracy in compliance-related activities. The automated procedures ensure consistent application of compliance policies and procedures across the organization. These efficiencies free up security personnel to focus on more strategic initiatives.
Common Compliance Regulations and Security Orchestration Support
| Compliance Regulation | How Security Orchestration Aids Compliance |
|---|---|
| HIPAA | Automates the collection and analysis of protected health information (PHI) related events, ensuring compliance with access controls and data security protocols. |
| GDPR | Streamlines data subject access requests, enabling automated processing and response to data subject requests. |
| PCI DSS | Monitors payment card data handling and security protocols, automatically identifying and alerting on potential vulnerabilities and misconfigurations. |
| SOX | Automates financial record management and audits, ensuring the accuracy and completeness of financial data for compliance reporting. |
| NIST Cybersecurity Framework | Enables organizations to automate the implementation and monitoring of security controls Artikeld in the framework, providing evidence of compliance and identifying gaps in security posture. |
Incident Response Automation
Security orchestration platforms dramatically streamline incident response, shifting from reactive to proactive handling. By automating crucial tasks, these platforms free up security teams to focus on more strategic initiatives, significantly reducing response times and improving overall incident management effectiveness. This empowers organizations to quickly contain and remediate threats, minimizing potential damage.
Automating Incident Response Workflows
Security orchestration platforms automate incident response workflows by creating pre-defined playbooks. These playbooks detail the specific actions required to handle different types of security incidents. When a security alert triggers, the orchestration platform automatically executes the corresponding playbook, initiating a series of pre-programmed actions. This automated approach minimizes manual intervention, accelerating the response process.
Examples of Automating Actions During a Security Incident
Security orchestration platforms can automate a wide range of actions during a security incident. For example, upon detecting a malicious file, the orchestration platform can automatically quarantine the affected systems, block the malicious IP address, and notify relevant personnel. Furthermore, the platform can automatically generate reports detailing the incident’s scope and impact. These actions are typically configured in pre-defined playbooks.
Demonstrating the Use of Orchestration for Faster and More Efficient Incident Handling
Security orchestration dramatically speeds up incident handling. Consider a scenario where a malware infection is detected. A traditional approach might involve multiple steps and teams, leading to significant delays. With orchestration, the platform can automatically isolate the infected systems, block malicious communications, and notify affected users, all within minutes. This streamlined process significantly reduces the time to containment and eradication, preventing further damage.
This contrasts sharply with manual processes, where response times are often measured in hours or even days.
Reducing Human Intervention During an Incident, Top security orchestration use cases
Orchestration significantly reduces human intervention during an incident. By automating tasks like isolating infected systems, blocking malicious traffic, and initiating remediation steps, the platform minimizes the need for manual intervention. This reduces the potential for human error and ensures a more consistent and reliable response. This automated approach also allows security teams to concentrate on higher-level tasks, such as incident analysis and prevention strategies.
Automated Incident Response Process Diagram
This diagram illustrates a simplified representation of the automated incident response process using security orchestration. The process begins with a security alert triggering an incident. The orchestration platform then executes the pre-defined playbook, which includes actions like quarantining affected systems, blocking malicious traffic, notifying relevant personnel, and initiating remediation steps. This diagram emphasizes the automated flow of actions, minimizing manual intervention and accelerating the response.
Cloud Security Orchestration
Cloud security orchestration is rapidly becoming a critical component of modern security strategies. The inherent complexity of cloud environments, with their dynamic nature and diverse services, demands a unified approach to security management. This approach needs to go beyond traditional security tools and incorporate automation to effectively address the unique challenges presented by cloud deployments.
Unique Challenges of Cloud Security Orchestration
Cloud environments introduce several complexities that make traditional security approaches inadequate. These include the sheer scale and dynamism of cloud deployments, the proliferation of cloud services with varying security features, and the difficulty in centralizing visibility across diverse cloud platforms (e.g., AWS, Azure, GCP). Security teams need a robust orchestration platform to manage the complexity, ensuring consistency and efficiency in security policies and processes across these environments.
The distributed nature of cloud infrastructure also presents a challenge in terms of security monitoring and response.
Use Cases for Security Orchestration in Cloud Environments
Security orchestration in cloud environments is crucial for several key use cases. These include automating security tasks such as vulnerability scanning, compliance checks, and incident response, enabling proactive threat detection and response in real time. It also empowers security teams to streamline and automate routine security tasks, freeing up resources for more strategic initiatives. Furthermore, it enhances the effectiveness of incident response by automatically correlating and analyzing security events across various cloud services.
Implementing a security orchestration platform can greatly reduce manual intervention, thus accelerating the process of threat containment.
Need for Security Orchestration to Manage Complex Cloud Deployments
Managing complex cloud deployments necessitates a robust security orchestration platform. This platform facilitates centralized control and visibility across multiple cloud environments, enabling a unified approach to security management. The platform provides a single pane of glass for monitoring security events, managing security policies, and automating security tasks, streamlining the security process and improving operational efficiency. Without orchestration, security teams face the daunting task of managing disparate tools and processes across various cloud services, leading to potential blind spots and inefficiencies.
Benefits of Automated Security Tasks in Cloud Environments
Automation of security tasks in cloud environments yields significant benefits. Automating tasks such as vulnerability scanning, patch management, and compliance checks frees up security personnel to focus on higher-level strategic initiatives. This automation significantly reduces the time spent on repetitive tasks, enhancing operational efficiency and allowing security teams to respond more quickly to threats. Automated security tasks contribute to a more proactive security posture by identifying and mitigating potential vulnerabilities before they are exploited.
This leads to a significant reduction in the risk of breaches and data loss.
Key Considerations for Implementing Security Orchestration in a Cloud Environment
A successful security orchestration implementation in a cloud environment requires careful planning and consideration of various factors, including the integration of existing security tools, the need for centralized visibility across different cloud platforms, the definition of clear security policies and procedures, and the selection of a robust orchestration platform capable of handling the scale and dynamism of the cloud environment. Careful evaluation of the integration process is crucial to avoid potential conflicts or compatibility issues between the orchestration platform and existing security tools.
Software Defined Security Orchestration
Software-defined security orchestration (SDSO) represents a paradigm shift in how security teams manage and respond to threats. It moves away from static, device-centric security solutions to a more dynamic, policy-driven approach. This approach allows for greater flexibility and scalability, enabling organizations to adapt quickly to evolving threats and compliance requirements. SDSO abstracts the underlying security infrastructure, enabling a more streamlined and automated security operations process.SDSO decouples security functions from the physical infrastructure, allowing for greater agility and scalability.
This decoupling empowers security teams to deploy and manage security tools in a more efficient and adaptable manner, optimizing resource allocation and response times. This approach also enables security teams to leverage the full potential of their existing security tools, even those from different vendors.
Concept of Software-Defined Security Orchestration
Software-defined security orchestration is a framework that allows security operations to be managed and automated through software. It uses a central control plane to orchestrate security tools and policies across different security domains, whether on-premises, in the cloud, or hybrid environments. This central control plane allows for consistent and automated responses to security events, regardless of the location of the event or the security tool used to address it.
Essentially, it acts as a conductor for a complex orchestra of security tools, ensuring they work together seamlessly.
Examples of Software-Defined Security Orchestration in Action
SDSO can be implemented in various scenarios to improve security posture. For instance, a security team can use SDSO to automate incident response procedures. When a security alert is triggered, the SDSO platform can automatically investigate the threat, contain the incident, and remediate the affected systems. Another example involves automating compliance tasks. SDSO can monitor compliance posture in real-time and automatically remediate any violations to ensure continuous compliance.
For instance, it can automatically reconfigure firewall rules to meet compliance requirements.
Benefits of Software-Defined Security Orchestration
SDSO offers several benefits, including improved efficiency, reduced response time, and enhanced security posture. Security teams can automate tasks such as incident response, threat hunting, and compliance monitoring. This automation leads to faster identification and resolution of security incidents, resulting in reduced downtime and minimized impact on business operations. Additionally, SDSO promotes consistent security policies and procedures across different environments.
Flexibility and Scalability of Software-Defined Security Orchestration
SDSO offers significant flexibility and scalability, enabling organizations to adapt quickly to changing security needs. The centralized control plane allows for dynamic policy adjustments, providing an adaptable framework for handling a wide range of threats. Security teams can easily scale their security operations by adding or removing security tools without significant infrastructure changes. This adaptability is crucial in today’s rapidly evolving threat landscape.
Comparison of Software-Defined Security Orchestration Tools
| Tool | Features | Pricing | Ease of Use |
|---|---|---|---|
| Example Tool 1 | Comprehensive security orchestration, integration with various security tools, automation capabilities, centralized management, real-time monitoring | Starts at $XX,000 per year, dependent on the number of users and features required | Medium, requires technical expertise for configuration and customization |
| Example Tool 2 | Cloud-native security orchestration, API-driven integrations, strong automation capabilities, scalable architecture | Subscription-based, starting from $XX per user per month | High, intuitive interface, well-documented resources |
| Example Tool 3 | On-premises security orchestration, high level of customization, granular control over security processes, robust reporting | Variable, based on the number of agents and features | Low, simple setup and straightforward configuration |
Note: Pricing and ease of use are approximate and may vary based on specific implementation details. “Example Tool 1”, “Example Tool 2”, and “Example Tool 3” are placeholders. Actual tools would have different feature sets and pricing models.
Last Word
In conclusion, top security orchestration use cases demonstrate a powerful shift towards proactive and automated security. By understanding and implementing these use cases effectively, organizations can dramatically enhance their security posture, reduce response times, and ultimately mitigate the impact of cyber threats. The key takeaway is that security orchestration is no longer a luxury, but a necessity in today’s complex digital environment.











