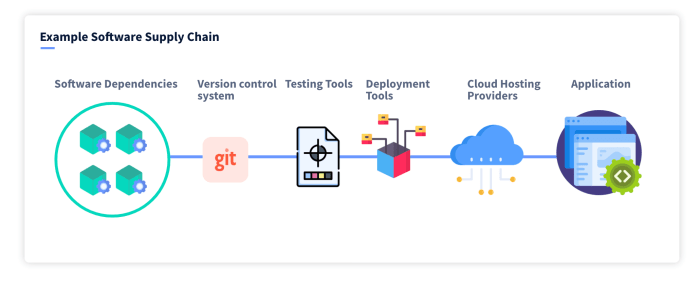
Should you worry about software supply chain attacks? The answer is likely a resounding yes. Malicious actors are increasingly targeting the software supply chain, inserting vulnerabilities into seemingly trustworthy components. This can lead to devastating consequences for businesses and users, impacting everything from financial stability to reputation. From compromised open-source libraries to vulnerable build systems, the potential for harm is substantial.
We’ll explore the various attack vectors, vulnerabilities, and ultimately, how to mitigate these risks.
Software supply chain attacks exploit the interconnected nature of software development. They often involve subtly altering seemingly innocuous components within a larger software system, potentially compromising many downstream users and organizations. Understanding these intricate attack pathways is crucial for protecting your systems and data.
Introduction to Software Supply Chain Attacks
Software supply chain attacks are a growing threat to organizations worldwide. These attacks exploit vulnerabilities in the intricate network of software development, distribution, and deployment. Instead of directly targeting a specific application, attackers insert malicious code into a widely used component or library, potentially impacting numerous downstream users. This insidious approach makes detection and remediation significantly more challenging.The ripple effect of a successful supply chain attack can be devastating, encompassing financial losses, reputational damage, and significant disruption to critical operations.
Understanding the various attack vectors and the potential consequences is crucial for proactive defense strategies.
Types of Software Supply Chain Attacks
Software supply chain attacks can manifest in several ways. Compromised build tools, malicious code embedded within libraries, and manipulated package repositories are just a few examples. These attacks can affect software at any stage, from development to deployment, making prevention and response a continuous challenge.
Attack Vectors in the Software Supply Chain
A multitude of attack vectors exist within the software supply chain. These points of vulnerability represent potential entry points for malicious actors. A comprehensive understanding of these vectors is essential for developing robust security measures.
| Attack Vector | Description | Impact | Mitigation |
|---|---|---|---|
| Compromised Build Tools | Attackers modify build tools to inject malicious code into legitimate software packages. | Potentially widespread infection of downstream users; difficult to detect. | Regularly update and scan build tools; employ secure code review practices. |
| Malicious Code in Libraries | Introducing malicious code into commonly used libraries or components. | Infection of applications that utilize the compromised library; wide-ranging impact depending on library usage. | Thorough vetting of open-source libraries; secure dependency management. |
| Tampered Package Repositories | Modifying legitimate package repositories to distribute malicious versions of software. | Installation of malicious software by users who rely on the compromised repository. | Employ multiple package repositories; utilize secure authentication and authorization protocols. |
| Compromised Developers | Attackers exploit vulnerabilities in the developer environment or gain unauthorized access to source code. | Malicious code integration into legitimate software; potentially undetected for extended periods. | Robust access controls; rigorous background checks; security awareness training for developers. |
| Supply Chain Compromises in Third-Party Dependencies | Malicious actors compromise the third-party dependencies used in software development. | Installation of malware or unintended functionality; wide-reaching effects depending on the nature of the compromise. | Thorough due diligence and vetting of third-party dependencies; implement secure dependency management tools. |
Examples of Recent Supply Chain Attacks
Numerous notable supply chain attacks have highlighted the severity of this threat. One example is the SolarWinds Orion attack, which compromised a widely used IT management tool. This attack showcased the potential for large-scale damage when a trusted component is compromised. Similarly, the attack on a widely used package repository demonstrates the need for secure and robust dependency management.
Such events underscore the need for continuous vigilance and proactive security measures.
Understanding the Risks and Vulnerabilities
Software supply chain attacks exploit vulnerabilities within the intricate web of dependencies that underpin modern software development. These attacks can have devastating consequences, impacting everything from critical infrastructure to everyday applications. Understanding the specific risks and vulnerabilities within the software development lifecycle (SDLC) is crucial to mitigating these threats.Identifying and addressing these vulnerabilities requires a multifaceted approach, encompassing meticulous code reviews, robust security testing, and vigilant monitoring of dependencies.
A deeper understanding of the risks associated with various components and stages in the SDLC empowers developers and organizations to build more secure and resilient software.
Key Vulnerabilities in the Software Development Lifecycle (SDLC)
The software development lifecycle (SDLC) presents several entry points for malicious actors seeking to compromise software. These vulnerabilities often stem from inadequate security practices at various stages of the process.
- Inadequate Security Testing: A lack of comprehensive security testing throughout the SDLC can leave vulnerabilities unaddressed. This includes insufficient penetration testing, static and dynamic analysis, and insufficient vulnerability scanning of dependencies. The absence of security testing during development and deployment phases significantly increases the likelihood of undetected flaws that attackers can exploit.
- Poorly Managed Dependencies: Modern software relies heavily on external libraries and components. Maintaining these dependencies and keeping track of potential vulnerabilities within them is a significant challenge. The lack of a comprehensive dependency management strategy and insufficient validation of dependencies exposes the software to potential vulnerabilities in the open-source components and third-party libraries.
- Insufficient Code Reviews: Manual code reviews, often crucial for identifying vulnerabilities and security flaws, are frequently insufficient or performed haphazardly. Automated tools and techniques can augment human review processes and help identify more complex vulnerabilities. Manual reviews are often insufficient, lacking in scope, and potentially influenced by cognitive biases. Thorough and consistent code reviews are essential for detecting vulnerabilities.
- Lack of Secure Coding Practices: The absence of established security guidelines and best practices within development teams can lead to vulnerabilities in the final product. Developers often lack the training or awareness necessary to implement secure coding techniques. The lack of awareness or training in secure coding practices is a critical vulnerability that exposes the software to attacks.
Risks Associated with Open-Source Components
Open-source software, while offering significant benefits, introduces inherent risks due to its collaborative nature. Malicious actors can exploit this collaborative nature to introduce vulnerabilities into seemingly benign open-source projects.
- Malicious Code Injection: Attackers can subtly introduce malicious code into open-source projects, often going unnoticed until it is incorporated into downstream applications. The nature of collaborative development makes it difficult to identify malicious code. The vast and often unvetted nature of open-source projects makes it a fertile ground for malicious code injection. Malicious code can be difficult to identify, even for experienced developers.
- Hidden Backdoors: The complexity of open-source codebases can obscure the presence of backdoors, allowing attackers remote access. These hidden backdoors can remain undetected for extended periods, creating persistent vulnerabilities in the software. The complexity of open-source codebases makes it difficult to detect hidden backdoors.
- Dependency Chain Vulnerabilities: Attackers can exploit vulnerabilities in the dependencies of open-source projects, leading to vulnerabilities in downstream applications that rely on them. This domino effect can compromise multiple applications. Dependency chains can be extensive, creating complex and hard-to-manage vulnerabilities.
Risks Posed by Third-Party Libraries and Dependencies
Third-party libraries and dependencies play a crucial role in software development, but their use can introduce substantial risks. A single vulnerable library can compromise the entire application.
- Vulnerable Dependencies: Using vulnerable third-party libraries introduces vulnerabilities into the software. Attackers can exploit these vulnerabilities to gain unauthorized access or control. Libraries with known vulnerabilities pose a significant risk if not updated or replaced.
- Lack of Visibility: The sheer volume and complexity of third-party libraries can make it challenging to identify and assess potential vulnerabilities. This lack of visibility can impede effective security management. The vast number of libraries and the rapid pace of updates make it difficult to track and assess vulnerabilities.
- Lack of Security Audits: Without proper security audits of third-party libraries, organizations cannot assess the level of risk. This lack of visibility into the security posture of third-party libraries is a critical vulnerability.
Risks from Compromised Build Systems, Should you worry about software supply chain attacks
Build systems are integral to software development, but a compromised build system can lead to severe security breaches.
- Tampered Build Scripts: Malicious actors can tamper with build scripts to inject malicious code or alter the software’s functionality. This manipulation often goes undetected until the compromised software is deployed. Tampering with build scripts can result in malicious code being integrated into the software.
- Unauthorized Access: If the build system is vulnerable to unauthorized access, attackers can potentially modify the source code, insert malicious components, or even gain access to sensitive project data. Unauthorized access to build systems can lead to the compromise of critical project data and the manipulation of the software’s functionality.
Comparative Analysis of Attack Vectors
| Attack Vector | Risk Level | Impact | Mitigation Strategy |
|---|---|---|---|
| Inadequate Security Testing | High | Unidentified vulnerabilities leading to exploitation | Comprehensive security testing throughout the SDLC |
| Poorly Managed Dependencies | High | Exploitation of vulnerabilities in dependencies | Robust dependency management and validation |
| Malicious Code Injection (Open Source) | High | Malicious code execution | Scrutiny of open-source components, regular updates |
| Vulnerable Third-Party Libraries | High | Compromised software functionality | Regular updates and vulnerability assessments |
| Compromised Build Systems | Critical | Malicious code insertion | Strong access controls, regular security audits |
Assessing the Impact of Attacks
Software supply chain attacks, while often subtle, can inflict devastating damage across various fronts. Beyond the technical vulnerabilities exploited, the repercussions extend into financial instability, reputational harm, and a erosion of user trust. Understanding the multifaceted impact is crucial for effective mitigation strategies.
Financial and Reputational Damage
The financial consequences of a successful software supply chain attack can be substantial. Companies impacted often face significant costs associated with incident response, remediation, and legal battles. The disruption to operations, lost productivity, and potential fines or penalties further amplify the financial burden. Furthermore, damaged brand reputation can lead to decreased customer loyalty and lost revenue streams.
A tarnished image can take years to rebuild.
Examples of Impacted Companies
Numerous companies have experienced firsthand the destructive power of supply chain attacks. While specific details are often kept confidential for security reasons, reports of significant financial losses and operational disruptions following such attacks are common. One example could be a major software vendor whose product, integrated into many other companies’ systems, was compromised. This compromise led to widespread system outages and significant financial losses for downstream clients, impacting their own operations and financial statements.
Another example could be a company that suffered reputational damage when a security flaw, introduced through a compromised library in their software supply chain, was exposed, impacting user trust.
Impact on User Trust and Security
A successful software supply chain attack can severely undermine user trust in software products. Users may lose confidence in the security and reliability of the affected software, leading to reluctance to use it. This impact transcends the direct victims, as a general erosion of trust in software security can have wider consequences across the industry. When users perceive a systemic vulnerability, their trust in the entire software ecosystem is shaken.
Honestly, should you worry about software supply chain attacks? Probably. It’s like wondering if you’ll get a missing one of your child tax credit payments. Figuring out why you’re missing a payment, as detailed in this helpful guide, missing one of your child tax credit payments heres what the problem could be , takes some digging.
Similarly, identifying vulnerabilities in the software you use requires vigilance. So, yeah, probably worth keeping an eye on these supply chain risks.
The long-term impact on user trust can be measured in lost sales and brand loyalty, with long-term consequences for the software industry.
Potential Consequences of a Successful Attack
| Impact Area | Description | Severity | Example |
|---|---|---|---|
| Financial | Direct costs of remediation, legal fees, lost revenue, and potential penalties. | High | A major e-commerce platform losing millions due to a payment processing vulnerability introduced through a third-party library. |
| Reputational | Damage to brand image, loss of customer trust, and decreased market share. | High | A major software company experiencing a decline in user trust after a critical vulnerability was discovered in their software, impacting their future sales. |
| Operational | System outages, data breaches, and disruption of business processes. | High | A healthcare provider facing major disruptions to their electronic health records system due to a supply chain compromise. |
| Legal | Potential lawsuits, regulatory fines, and damage to company’s legal standing. | High | A company facing a class-action lawsuit due to a privacy violation resulting from a software supply chain compromise. |
| User Trust | Loss of customer confidence in the security and reliability of software. | High | Significant drop in user downloads and registrations for a software application after a supply chain vulnerability was exposed. |
Mitigation Strategies and Security Best Practices
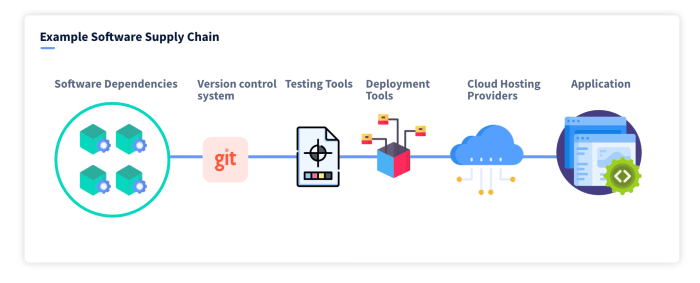
Software supply chain attacks are a serious threat, but proactive measures can significantly reduce the risk. Implementing robust security practices throughout the development lifecycle, from code creation to deployment, is crucial. This involves a multifaceted approach, addressing vulnerabilities in open-source components, securing development environments, and establishing rigorous verification processes. By prioritizing security at every stage, organizations can build more resilient and trustworthy software ecosystems.Effective mitigation strategies involve a combination of technical controls and procedural best practices.
These strategies aim to detect and prevent malicious actors from compromising software components or introducing vulnerabilities during development, testing, and deployment. Proactive measures are key to safeguarding software from supply chain attacks.
Secure Coding Practices
Secure coding practices are fundamental to mitigating the risk of vulnerabilities that attackers can exploit. These practices involve writing code that is resistant to common attack vectors. Developers should be trained to identify and avoid potential vulnerabilities, such as buffer overflows, SQL injection, and cross-site scripting. Implementing these practices early in the development process can significantly reduce the likelihood of vulnerabilities being introduced into the software supply chain.
- Input Validation: Thoroughly validating all user inputs is essential. This prevents attackers from injecting malicious code or manipulating data to compromise the application. Input validation should be performed at multiple stages to catch potential errors. For example, data should be validated for type, length, and format to ensure it conforms to expected parameters.
- Authentication and Authorization: Robust authentication and authorization mechanisms are crucial to limit access to sensitive data and functionality. These mechanisms should verify the identity of users and ensure that only authorized users can access specific resources. This helps prevent unauthorized access and data breaches.
- Least Privilege Principle: Granting users only the necessary permissions to perform their tasks reduces the impact of a security breach. Limiting access to sensitive data and resources can significantly reduce the potential for damage if a vulnerability is exploited.
Securing Open-Source Components
Open-source components are widely used in software development, but they can introduce vulnerabilities if not carefully managed. Organizations must establish processes to identify, assess, and mitigate potential risks associated with these components. This includes regularly updating open-source libraries to patch known vulnerabilities and employing security tools to scan for potential issues.
- Regular Updates: Regularly updating open-source components to patch known vulnerabilities is crucial. This proactive approach helps minimize the attack surface and reduces the risk of exploitation.
- Vulnerability Scanning: Employing automated vulnerability scanners to identify potential issues in open-source components is vital. These scanners can automatically detect vulnerabilities, providing insights into potential risks and enabling timely mitigation.
- Dependency Management Tools: Utilizing dependency management tools can streamline the process of managing and updating open-source components. These tools can automate the process of identifying dependencies and applying updates.
Verifying Software Component Integrity
Ensuring the integrity of software components is critical to prevent malicious actors from substituting or modifying components. This involves verifying the source and authenticity of software packages to ensure that they haven’t been tampered with. Digital signatures and checksums are common techniques used to verify the integrity of components.
- Digital Signatures: Employing digital signatures to verify the authenticity of software components is essential. These signatures validate the source of the component and confirm that it hasn’t been altered.
- Checksum Verification: Using checksums to verify the integrity of downloaded software packages is crucial. This technique ensures that the downloaded package matches the original, preventing unauthorized modifications.
Security Tools for Supply Chain Attacks
Several tools aid in identifying and preventing software supply chain attacks. These tools can automate the process of vulnerability scanning, dependency analysis, and integrity verification. Organizations can leverage these tools to proactively identify potential threats and mitigate risks.
- Dependency Track: This tool is used to analyze project dependencies to identify vulnerabilities in open-source components.
- Snyk: This platform automates the process of identifying and addressing vulnerabilities in dependencies. It helps identify vulnerabilities and provides remediation guidance.
- OWASP Dependency-Check: This tool can scan projects to identify open-source dependencies with known vulnerabilities.
The Role of Security Teams and Governance
Protecting the software supply chain is a multifaceted challenge that requires a coordinated effort between security teams and robust governance frameworks. Security teams are the front line in identifying and mitigating vulnerabilities, while governance sets the stage for consistent security practices across the entire organization. Effective policies and procedures are crucial for building a strong defense against increasingly sophisticated attacks.
Responsibilities of Security Teams
Security teams play a vital role in proactively identifying and responding to potential threats in the software supply chain. This involves a combination of technical expertise and a deep understanding of the organization’s unique software development lifecycle. Their responsibilities extend beyond simply reacting to incidents; they must also be involved in the design, development, and deployment phases.
While worrying about software supply chain attacks might seem like a constant uphill battle, recent developments like the leaked Xbox handheld photos and details on the Microsoft Asus ROG Ally 2, as seen in the FCC listing here , highlight the importance of vigilance. Ultimately, understanding these potential vulnerabilities is key to ensuring a secure digital environment, regardless of the latest gaming hardware.
- Threat Modeling and Vulnerability Assessment: Security teams must proactively identify potential vulnerabilities in software components and dependencies. This includes analyzing open-source libraries, third-party components, and internal codebases for known weaknesses. Thorough threat modeling should be performed throughout the software development lifecycle.
- Security Training and Awareness: Educating development teams on secure coding practices, the importance of software supply chain security, and how to identify and report potential vulnerabilities is critical. Regular training sessions and readily accessible resources can significantly improve the security posture of the organization.
- Incident Response Planning and Execution: A well-defined incident response plan is essential to handle potential supply chain attacks. Security teams must be prepared to detect, contain, and remediate attacks swiftly and effectively. This includes clear communication protocols and established procedures.
- Continuous Monitoring and Improvement: Security teams need to constantly monitor the software supply chain for suspicious activity and adapt their strategies to evolving threats. Regular security audits and vulnerability scans are crucial to maintaining a proactive approach.
Role of Governance in Establishing Security Protocols
Governance plays a critical role in establishing and enforcing security protocols for the software supply chain. It defines the overall security strategy, establishes clear roles and responsibilities, and enforces compliance across the organization.
- Defining Security Policies and Standards: Governance bodies must establish clear security policies and standards that apply to all software development projects. These policies should cover everything from secure coding practices to vulnerability management processes.
- Implementing Security Controls: Governance teams need to put in place and enforce the necessary security controls, such as automated security scans, code reviews, and dependency checks, throughout the entire software development lifecycle.
- Establishing Secure Development Lifecycle (SDL) Practices: A robust SDL is essential to integrating security into every stage of software development. Governance should mandate the use of secure coding practices and security testing throughout the lifecycle.
- Enforcing Compliance: Governance bodies must enforce compliance with established security policies and standards. This ensures consistency and minimizes the risk of vulnerabilities in the supply chain.
How Strong Security Policies Prevent Attacks
Strong security policies and their consistent enforcement create a layered defense against attacks on the software supply chain. These policies are essential for preventing attackers from exploiting vulnerabilities in the supply chain.
- Mitigation of Known Vulnerabilities: Implementing robust security policies allows organizations to proactively identify and address known vulnerabilities in software components. This reduces the attack surface and makes the system less susceptible to exploitation.
- Reduced Attack Surface: By following secure coding practices and rigorously evaluating dependencies, organizations significantly reduce the attack surface for potential attackers.
- Improved Incident Response: A well-defined policy framework provides a structured approach for detecting, responding to, and recovering from security incidents related to the software supply chain. A documented incident response plan, approved by governance, is critical.
Steps to Implement a Robust Program
A robust software supply chain security program requires a multi-pronged approach. Implementing these steps builds a resilient defense against attacks.
- Establish a Centralized Security Team: Create a dedicated security team responsible for overseeing and managing software supply chain security. This team will be responsible for identifying vulnerabilities and responding to incidents.
- Implement Secure Development Practices: Integrate security into the software development lifecycle through training, code reviews, and security testing. Security awareness is critical at all levels of the organization.
- Implement Automated Security Tools: Use automated tools for vulnerability scanning, dependency analysis, and other security tasks. This helps automate the process of identifying potential vulnerabilities.
- Regularly Review and Update Policies: Security threats and vulnerabilities evolve constantly. Security policies and procedures should be regularly reviewed and updated to stay ahead of these threats.
- Establish Strong Governance Framework: Create a framework that clearly defines roles and responsibilities for supply chain security. This will ensure accountability and consistency.
Staying Informed and Adapting to Threats: Should You Worry About Software Supply Chain Attacks
Staying ahead of evolving software supply chain threats requires constant vigilance and a proactive approach. The landscape of vulnerabilities is dynamic, with attackers constantly developing new techniques and exploiting emerging weaknesses. Therefore, continuous learning and adaptation are crucial to effectively mitigate risks.Staying informed about emerging threats and vulnerabilities is not a passive exercise. It demands actively seeking out information from reputable sources, understanding the tactics and motivations of threat actors, and adapting security strategies accordingly.
This proactive approach is critical for maintaining a robust defense against sophisticated attacks.
Key Resources for Staying Updated
Understanding the constantly shifting threat landscape requires access to reliable information sources. Staying updated on emerging vulnerabilities, attack vectors, and attacker tactics is paramount to protecting software supply chains.
Honestly, should you worry about software supply chain attacks? Probably. It’s a growing concern, especially when you consider how much software we use daily. But, let’s be honest, sometimes I just want to rant about how much I miss swappable laptop batteries! Please bring back swappable laptop batteries would make a huge difference in how we approach tech frustrations.
So, while software supply chain attacks are a valid concern, maybe we should also focus on the small, but important, things, like the freedom of choice in portable tech, which is why I think you should worry about software supply chain attacks.
- Security Newsletters and Blogs: Numerous cybersecurity companies and organizations publish regular newsletters, blogs, and articles focusing on the latest threat intelligence. These resources often provide detailed analyses of recent attacks, highlighting the vulnerabilities exploited and the methods used. Subscribing to these publications ensures you receive updates on emerging trends and threats.
- Industry Publications: Publications such as Dark Reading, Threatpost, and Infosecurity Magazine often provide in-depth articles and analysis on security issues, including supply chain attacks. These publications offer valuable insights into emerging threats, providing a broader context for understanding the risks.
- Open-Source Intelligence (OSINT): Utilizing OSINT techniques, such as monitoring online forums and social media, can provide valuable insights into the activities of threat actors. Observing the conversations and discussions within these communities can reveal new tactics and techniques that attackers are using.
- Vulnerability Databases: Databases like the National Vulnerability Database (NVD) are essential for tracking known vulnerabilities. This information helps security teams prioritize patching and address potential weaknesses before they are exploited.
Monitoring and Responding to Potential Attacks
Proactive monitoring of software supply chains is essential to detect and respond to potential attacks in a timely manner. A well-defined monitoring strategy should incorporate multiple layers of defense.
- Automated Security Tools: Implementing automated security tools, such as vulnerability scanners and intrusion detection systems, can significantly enhance your ability to detect suspicious activities. These tools can automatically scan software components for known vulnerabilities and raise alerts for anomalies in system behavior.
- Security Information and Event Management (SIEM): Employing SIEM solutions provides a centralized platform for collecting and analyzing security logs from various sources. This comprehensive view allows for correlation of events and detection of patterns that may indicate malicious activity.
- Incident Response Plan: A well-defined incident response plan is crucial for handling security incidents promptly and effectively. This plan should Artikel the steps to be taken in case of a suspected or confirmed attack, including containment, eradication, recovery, and lessons learned.
Continuous Learning and Adaptation
Staying informed is not enough; continuous learning and adaptation are critical for success in mitigating supply chain risks. Regular training for security teams is paramount to ensure they have the skills and knowledge to handle emerging threats.
- Security Training Programs: Investing in regular security training programs for personnel across the organization ensures that everyone understands the importance of software supply chain security and how to identify and report potential risks.
- Security Awareness Campaigns: These campaigns help raise awareness of security risks and promote good security practices among employees, which can help prevent human error that can lead to successful attacks.
- Stay Updated with New Research: Staying abreast of new research and developments in the field of supply chain security is essential for understanding the latest techniques and countermeasures.
Recommended Industry Publications and News Sources
- Dark Reading: A leading publication for IT security professionals covering a wide range of topics, including supply chain security.
- Threatpost: Provides news and analysis on emerging cyber threats, including those targeting software supply chains.
- Infosecurity Magazine: Offers comprehensive coverage of cybersecurity issues, including articles on software supply chain vulnerabilities.
- The Hacker News: Provides news and analysis on security incidents, vulnerabilities, and threat actors.
Case Study: The “Malicious Maven” Attack
The software supply chain is a complex network of dependencies. Malicious actors can exploit these vulnerabilities to introduce malicious code into seemingly benign software packages, wreaking havoc on unsuspecting users and organizations. This case study explores a fictional but realistic example of such an attack, focusing on the “Malicious Maven” incident.This scenario illustrates the potential devastation of a well-orchestrated supply chain attack, highlighting the need for robust security measures and continuous vigilance across the entire software development lifecycle.
Attack Methodology
The “Malicious Maven” attack leveraged a popular open-source library, “DataFlow,” widely used by many applications. Attackers infiltrated the official repository, replacing a legitimate version of DataFlow with a compromised version containing malicious code. This code, subtly disguised, collected sensitive data from affected applications and relayed it to a remote server controlled by the attackers. The attack exploited a common vulnerability in the library’s handling of user-provided input, allowing for the execution of arbitrary code.
Impact of the Attack
The impact of the “Malicious Maven” attack was significant. Hundreds of applications, unknowingly reliant on the compromised DataFlow library, were compromised. Sensitive data, including user credentials, financial information, and intellectual property, was exfiltrated. The attackers gained unauthorized access to internal systems of numerous organizations, potentially leading to substantial financial losses, reputational damage, and legal repercussions. The attack highlighted the ripple effect of a compromised dependency, affecting many downstream users without their direct involvement.
Mitigation Strategies and Response
A comprehensive response to the “Malicious Maven” attack involved several key steps. Firstly, affected organizations immediately identified and removed the compromised DataFlow library from their applications. Secondly, they implemented stricter security protocols for software updates and dependencies. This included enhanced vulnerability scanning and code review processes. Thirdly, incident response teams investigated the attack to understand the scope of the breach and identify any further compromised systems.
Fourthly, the open-source community, alerted to the attack, swiftly patched the vulnerable DataFlow library.
Lessons Learned
The “Malicious Maven” attack underscored the importance of proactive security measures. It highlighted the need for a robust security posture throughout the entire software supply chain, encompassing not only the development process but also the deployment and maintenance phases. Open-source projects need enhanced security monitoring and review mechanisms to prevent similar intrusions. The attack also emphasized the critical role of communication and collaboration between developers, security teams, and users.
Attack Timeline and Response
| Stage | Description | Impact | Mitigation |
|---|---|---|---|
| Pre-attack | Attackers identify vulnerability in DataFlow, create malicious code. | Vulnerable open-source library in circulation. | Enhanced vulnerability scanning and code review for open-source libraries. |
| Attack | Attackers replace legitimate DataFlow library version with malicious one in the repository. | Compromised applications collect and send data to attackers. | Regular updates and security patches for dependencies. |
| Discovery | Users and organizations notice unusual activity in affected applications. | Data breaches, financial losses, reputational damage. | Incident response plan and robust monitoring of application behavior. |
| Containment | Affected organizations isolate compromised systems, remove malicious library. | Limited data exposure and system damage. | Establish clear communication channels for incident response. |
| Recovery | Organizations restore systems, implement security upgrades, and notify affected users. | System restoration, user notification, and financial recovery. | Collaboration with security researchers, developers, and users. |
End of Discussion
In conclusion, the risks posed by software supply chain attacks are undeniable. The potential for widespread damage, financial loss, and reputational harm is significant. By understanding the vulnerabilities, implementing robust mitigation strategies, and maintaining vigilance, organizations can significantly reduce their exposure to these attacks. Continuous learning, adaptation, and a proactive approach to security are paramount in the ever-evolving landscape of software supply chain threats.