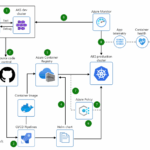
Securing containers with nist sp 800 190 – Securing containers with NIST SP 800-190 is crucial in today’s cloud-native world. This comprehensive guide dives deep into the practical application of NIST Special Publication 800-190’s guidelines for container security. We’ll explore best practices, implementation strategies, and essential monitoring techniques to ensure your containerized applications are robust and secure.
The document Artikels a systematic approach to securing container environments, addressing critical aspects like image scanning, secure deployment, access controls, and incident response. We’ll also look at the relationship between NIST SP 800-190 and other industry standards, providing a clear comparison to help you understand its unique position in the container security landscape.
Introduction to NIST SP 800-190
NIST Special Publication 800-190, “Security and Privacy Considerations for Containerized Applications,” provides a comprehensive framework for securing containerized applications. It’s a valuable resource for organizations looking to adopt container technology while mitigating the inherent security risks. The document addresses the unique challenges of containerization, such as shared kernel environments and rapid deployment cycles, by offering practical guidelines and best practices.This document’s scope encompasses a wide range of security considerations, including image integrity, access control, and network security.
It helps organizations understand and implement robust security measures across the entire container lifecycle, from image creation to runtime execution. The guidelines within SP 800-190 are designed to be adaptable and applicable to various container orchestration platforms and environments.
Key Principles and Guidelines
NIST SP 800-190 emphasizes several key principles for securing containerized applications. These include establishing secure development practices for container images, ensuring the integrity and authenticity of images, and implementing robust access controls to manage user permissions and privileges within the containerized environment. The document also provides guidelines for secure container runtime environments and secure network configurations. A critical aspect is the emphasis on the entire container lifecycle, from build to deployment, addressing potential vulnerabilities at each stage.
Relationship to Other Standards
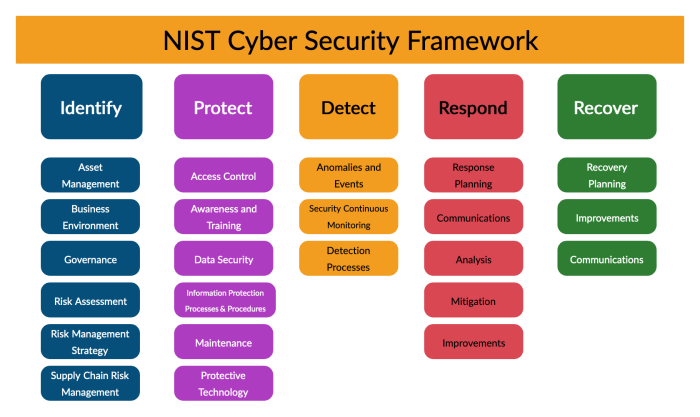
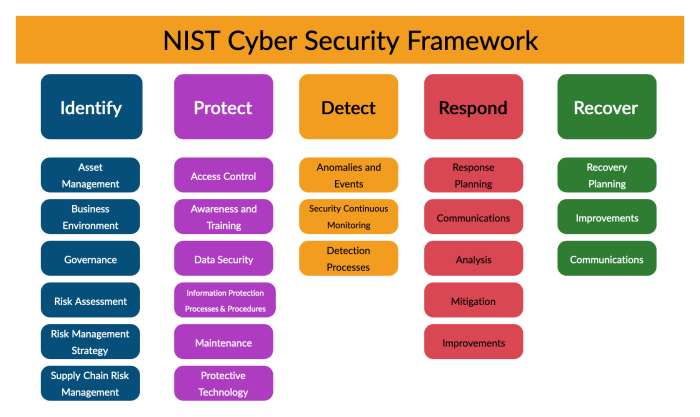
NIST SP 800-190 aligns with and complements other security standards and frameworks. It resonates strongly with the principles of the NIST Cybersecurity Framework, focusing on risk management and continuous improvement. The document also draws upon and expands upon concepts Artikeld in other container-specific security guidance, such as Docker’s security best practices. It is important to consider these interrelationships to create a comprehensive and layered security posture for containerized applications.
Comparison to Other Container Security Standards
| Standard | Focus | Key Features | Strengths | Weaknesses |
|---|---|---|---|---|
| NIST SP 800-190 | Comprehensive security for containerized applications, encompassing the entire lifecycle | Image integrity, access control, runtime security, network security, secure development | Provides a high-level framework applicable to various container orchestration platforms. Emphasizes a risk-based approach. | May require tailoring for specific container orchestration platforms. Can be perceived as a high-level overview. |
| Docker Security Best Practices | Specific guidance for Docker containers | Image scanning, vulnerability management, secure configuration, runtime controls | Provides concrete steps for Docker environments, offering detailed implementation guidance. | Limited scope compared to NIST SP 800-190. May not cover all container orchestration platforms. |
| OWASP Container Security | Focuses on identifying and mitigating vulnerabilities in container images | Vulnerability scanning, penetration testing, secure coding practices | Highlights specific vulnerabilities and potential attack vectors. | May not encompass the full spectrum of security considerations. |
Container Security Practices Aligned with NIST SP 800-190

Containerization, while offering significant advantages in software development and deployment, introduces unique security considerations. This necessitates a robust security framework to ensure the integrity and confidentiality of applications and data housed within these containers. NIST SP 800-190 provides a valuable guideline for establishing secure container practices. This discussion explores critical container security best practices, aligning them with the NIST framework.Implementing a comprehensive security strategy for containerized applications requires careful consideration of various factors.
This includes understanding vulnerabilities within container images, establishing secure deployment pipelines, and continuously monitoring containerized environments. The NIST SP 800-190 framework provides a structured approach to address these aspects, ensuring alignment with industry best practices.
Container Image Scanning
Container images are often downloaded from public repositories, posing a potential security risk. A critical step in securing containerized environments is comprehensive container image scanning. This involves automatically identifying vulnerabilities within the container image layer.Automated tools and platforms can scan container images for known vulnerabilities. These tools compare the container image’s contents against a database of known vulnerabilities and potential security flaws.
Securing containers with NIST SP 800-190 is crucial for data protection, especially in the cloud. While the recent news about the mixer shut down twitch facebook gaming partnership mixer shut down twitch facebook gaming partnership highlights a different kind of vulnerability, robust container security practices, like those outlined in NIST SP 800-190, are still essential for maintaining data integrity and avoiding similar disruptions in the future.
The principles of least privilege and secure configurations are key components of a strong security posture for containerized applications.
This proactive approach minimizes the risk of deploying compromised images. By implementing a consistent image scanning policy, organizations can ensure that only secure images are deployed into production environments.
Secure Container Deployment Strategies
Secure deployment strategies are paramount for mitigating risks associated with containerized applications. These strategies encompass various aspects of the container lifecycle, from building images to deploying them into production environments.Properly configured container orchestration platforms, such as Kubernetes, are crucial for secure deployments. Using role-based access control (RBAC) for managing container resources and implementing network segmentation to restrict container access to only necessary resources are crucial elements.
Using least privilege principles when configuring container processes and enforcing strict security policies throughout the container deployment pipeline is essential. This comprehensive approach ensures that containers operate with minimal access to sensitive data and resources.
Common Vulnerabilities and Mitigation Strategies
Containerized environments are susceptible to a range of vulnerabilities, from vulnerabilities within the container image to misconfigurations in the deployment pipeline.Insecure container images represent a significant vulnerability. Using compromised or unpatched base images, or including unintended packages, can introduce security flaws. Employing automated scanning, and using trusted repositories, mitigates this risk. Improperly configured networking within the container environment, such as allowing excessive access or exposing unnecessary ports, can be exploited.
Network segmentation and enforcing strict access control policies prevent unauthorized access. Also, improper configuration of the container runtime environment can expose sensitive data or configuration files, creating opportunities for malicious actors. Utilizing hardening guidelines and employing secure configuration management tools reduces the likelihood of such vulnerabilities.
Container Security Tools and NIST SP 800-190 Alignment
| Tool | NIST SP 800-190 Alignment | Description |
|---|---|---|
| Clair | Image Scanning | Clair is a container image vulnerability scanner that helps identify vulnerabilities in container images. |
| Anchore Engine | Image Scanning, Deployment | Anchore Engine is a platform for securing container images, providing scanning, analysis, and compliance validation. |
| Kubernetes | Deployment, Security Policies | Kubernetes is a container orchestration platform that facilitates secure deployments and enforcement of security policies. |
| Sysdig Secure | Monitoring, Detection | Sysdig Secure provides container security monitoring and detection capabilities. |
Implementing Security Controls for Container Environments
Containerization has revolutionized software development, offering agility and efficiency. However, this very agility necessitates robust security measures to prevent vulnerabilities. Implementing security controls in container environments is crucial to protect sensitive data and maintain the integrity of applications. This involves a layered approach, encompassing access control, registry security, authentication, authorization, and cryptographic techniques.
Access Control Mechanisms in Containerized Systems
Implementing robust access control is paramount in securing containerized systems. This involves defining granular permissions for users and processes operating within the containers and the host infrastructure. Role-Based Access Control (RBAC) is a common approach, allowing administrators to define specific roles with corresponding privileges. This method ensures that only authorized users can access and modify containerized applications and data.
Properly configured access control lists (ACLs) on container orchestrators like Kubernetes further restrict access at the infrastructure level. By implementing least privilege, minimizing the potential impact of compromised accounts is a key element.
Securing Container Registries
Container registries are crucial repositories for container images. Securing them is a fundamental aspect of overall container security. Implementing strong authentication mechanisms, such as multi-factor authentication (MFA), is essential. Regular vulnerability assessments and patching are necessary to address potential security flaws. Network segmentation and firewalls are crucial for limiting unauthorized access to the registry.
Securing containers with NIST SP 800-190 is crucial, especially when considering the recent news about Amazon France closing fulfillment centers due to health concerns at Amazon France warehouse closing fulfillment centers health ruling. This highlights the importance of robust security measures in any logistics environment, including containerization, to ensure safety and efficiency. Ultimately, following guidelines like NIST SP 800-190 is key to protecting sensitive data and preventing potential disruptions, even in large-scale operations like those of Amazon.
Employing encryption throughout the image lifecycle, from upload to download, further enhances security. Using private registries is a strong security practice, as it limits exposure to public networks.
Strong Authentication and Authorization Mechanisms within Containers
Implementing strong authentication and authorization is crucial to restrict access to containerized applications and data. Employing industry-standard authentication methods, such as those based on certificates, is important for verifying the identity of users and processes. These methods ensure that only authorized entities can interact with the containers. Within the container itself, secure user accounts and permissions are needed.
These should adhere to the principle of least privilege, granting only the necessary access for specific tasks.
Cryptographic Techniques for Securing Container Images and Data, Securing containers with nist sp 800 190
Cryptographic techniques are vital for securing container images and data. This includes using cryptographic hashes to verify the integrity of images during the build and deployment processes. Using encryption at rest and in transit safeguards sensitive data stored within containers and during transmission. Implementing secure boot processes for container images prevents malicious code from being loaded into the containers.
Using digital signatures for image verification allows for validating the authenticity and integrity of container images from trusted sources.
Securing containers with NIST SP 800-190 is crucial for robust systems. It’s all about best practices for building secure applications. While we’re on the topic of security, have you checked out the latest podcast discussion on ctrl walt delete podcast online ads ? It’s fascinating how these topics relate, and it’s a good reminder that even seemingly separate areas like podcast advertising and container security share underlying principles of protection and control.
Ultimately, applying these security principles in any context, whether for applications or podcast ad strategies, is key to robust digital ecosystems.
Security Controls and NIST SP 800-190 Guidelines
| Security Control | NIST SP 800-190 Guideline(s) |
|---|---|
| Role-Based Access Control (RBAC) | Guidelines related to access control and authorization (e.g., 800-190). |
| Multi-Factor Authentication (MFA) | Guidelines related to authentication mechanisms (e.g., 800-190). |
| Network Segmentation | Guidelines related to network security and isolation (e.g., 800-190). |
| Regular Vulnerability Assessments | Guidelines related to risk management and vulnerability identification (e.g., 800-190). |
| Image Signing and Verification | Guidelines related to digital signatures and image integrity (e.g., 800-190). |
Monitoring and Auditing Container Environments
Continuous monitoring is paramount in container security. Ignoring potential vulnerabilities or threats can lead to significant damage, from data breaches to system outages. A proactive approach, coupled with robust auditing, allows for swift detection and mitigation of threats. Effective monitoring enables the identification of suspicious activity and the quick response to emerging security incidents, minimizing the impact of potential breaches.
Importance of Continuous Monitoring
Container environments are dynamic and complex. Changes in application code, dependencies, and deployment configurations happen frequently. This inherent dynamism necessitates constant monitoring to detect anomalies and unauthorized activities. Without continuous monitoring, potential threats might remain undetected, leading to compromised systems and data loss. This constant vigilance allows for prompt identification of suspicious activity, preventing escalation and enabling rapid containment.
Methods for Detecting and Responding to Security Incidents
Various methods are available for detecting and responding to security incidents within containerized environments. These include intrusion detection systems (IDS), security information and event management (SIEM) tools, and log analysis techniques. Implementing these methods allows for the detection of malicious activities and the rapid response to security incidents, minimizing the impact of potential breaches.
- Network traffic analysis tools can identify unusual patterns or high-volume traffic, which might indicate malicious activity or unauthorized access attempts.
- Real-time monitoring of container logs provides insights into container behavior and can detect anomalies, such as unexpected resource consumption or unauthorized API calls.
- Security information and event management (SIEM) systems collect and analyze logs from various sources, enabling correlation of events and the detection of potential threats.
Log Management and Analysis Practices
Effective log management and analysis are crucial for identifying and understanding security events in container environments. This involves collecting, storing, and analyzing logs from various sources, including containers, orchestrators (like Kubernetes), and supporting infrastructure. This practice enables a comprehensive understanding of system activity and allows for the identification of anomalies and potential security breaches.
- Centralized log aggregation is essential for collecting logs from diverse sources, such as container logs, network traffic logs, and security tools.
- Implementing robust log retention policies ensures that valuable historical data is available for investigation, enabling forensic analysis in case of incidents.
- Advanced log analysis tools can identify patterns, correlations, and anomalies that might indicate malicious activity, allowing for proactive security measures.
Incident Response Procedures
A well-defined incident response plan is critical for effectively managing and mitigating security incidents in container environments. This plan should Artikel roles and responsibilities, communication protocols, and procedures for containment, eradication, and recovery. A detailed and well-rehearsed incident response plan enables swift and coordinated action to minimize the impact of security breaches.
- Establish clear communication channels between security teams and other stakeholders, enabling rapid dissemination of information and coordinated action.
- Define specific roles and responsibilities for each team member, ensuring a structured and efficient response to security incidents.
- Develop a comprehensive plan for containment, eradication, and recovery to minimize the impact of a security incident.
Key Monitoring Tools and NIST SP 800-190 Alignment
The following table Artikels key monitoring tools and their alignment with NIST SP 800-190, focusing on specific security controls and best practices.
| Monitoring Tool | NIST SP 800-190 Alignment |
|---|---|
| Elasticsearch, Logstash, Kibana (ELK Stack) | Log management, data analysis, and security information and event management (SIEM) capabilities. |
| Prometheus | Monitoring container metrics, resource utilization, and performance. Supports alerting on critical thresholds. |
| Grafana | Visualizing metrics and logs, aiding in trend analysis and identification of anomalies. |
| Security Information and Event Management (SIEM) systems | Centralized log aggregation, correlation, and threat detection. |
| Intrusion Detection Systems (IDS) | Detection of malicious network traffic and activities. |
Case Studies and Real-World Examples: Securing Containers With Nist Sp 800 190
Container security is paramount in today’s cloud-native world. Breaches can lead to significant data loss, reputational damage, and financial penalties. Understanding real-world examples of both vulnerabilities and successful implementations is crucial for effective container security practices. This section delves into case studies, hypothetical scenarios, and security audit strategies.
Real-World Container Security Breaches
Numerous container security breaches have highlighted the importance of robust security measures. A notable example involves a company using Docker containers for their web application. A compromised image repository led to malicious code being deployed in production, resulting in unauthorized access to sensitive customer data. Had the company adhered to NIST SP 800-190, specifically the secure image scanning and vulnerability management practices, this breach could have been mitigated.
Another example involved a containerized database service where insufficient access controls allowed unauthorized access to sensitive data.
Successful Implementations of Container Security Best Practices
Several organizations have successfully implemented container security best practices, aligning with NIST SP 800-190. One such example is a financial institution that leverages a multi-layered security approach. They utilize a combination of container orchestration platform security features, automated vulnerability scanning, and rigorous image scanning procedures, enabling early detection and remediation of vulnerabilities. This multi-layered strategy ensures compliance with NIST SP 800-190 standards and safeguards sensitive data.
Hypothetical Security Incident in a Containerized Environment
Imagine a company using Kubernetes for their microservices architecture. A malicious actor gains unauthorized access to a container registry. They then inject malicious code into a critical application container image, leading to the compromise of sensitive customer data. This scenario highlights the importance of secure image repositories, strong access controls, and regular security audits. The attacker’s access may have been facilitated by weak authentication mechanisms within the registry.
Hypothetical Security Audit Plan for a Containerized System
A comprehensive security audit plan should cover various aspects of the containerized system. The plan should include a detailed assessment of the container images, the container orchestration platform, and the network configurations. A crucial aspect is to ensure compliance with NIST SP 800-190.
- Phase 1: Planning and Scoping. The plan Artikels the scope of the audit, defining the specific systems and technologies to be evaluated. It also identifies the resources required, including personnel and tools.
- Phase 2: Image Analysis. Thorough examination of container images for vulnerabilities, using automated scanning tools. Compliance with NIST SP 800-190’s secure image practices is a key aspect of this phase.
- Phase 3: Orchestration Platform Assessment. The security audit analyzes the container orchestration platform (e.g., Kubernetes) for security configurations, access controls, and monitoring mechanisms.
- Phase 4: Network Security Evaluation. This stage assesses the network configurations and security controls related to container communication. It evaluates network segmentation, firewalls, and intrusion detection systems.
- Phase 5: Reporting and Remediation. The audit generates a comprehensive report detailing identified vulnerabilities and their severity. Specific remediation steps are provided for each identified issue, allowing for prioritized action.
Remediation Steps for Security Vulnerabilities
Once vulnerabilities are identified during the audit, remediation steps need to be meticulously followed. These steps include patching the vulnerable images, upgrading the container orchestration platform, and strengthening access controls. Prioritization of remediation is critical based on the severity and potential impact of the identified vulnerabilities. Remediation is a crucial part of maintaining security in a containerized environment.
- Vulnerability Patching. Immediately apply security patches to affected container images, ensuring compliance with NIST SP 800-190.
- Configuration Updates. Update configurations for container orchestration platforms and other supporting systems to enhance security and align with NIST SP 800-190 guidelines.
- Access Control Enhancements. Implement stronger access controls, limiting access to container registries and other sensitive resources.
- Monitoring and Logging. Implement comprehensive monitoring and logging mechanisms to detect and respond to potential threats, providing compliance with NIST SP 800-190 standards.
Future Trends and Considerations
Container security is an ever-evolving landscape, demanding continuous adaptation to emerging threats and vulnerabilities. Staying ahead of the curve requires a proactive approach, understanding the future directions of container security practices and the technologies underpinning them. This section explores potential future trends and considerations, providing insights into the evolving challenges and opportunities in this dynamic field.The increasing adoption of containers across various industries is driving the need for robust and adaptable security measures.
The complex interplay of container orchestration platforms, microservices architectures, and the inherent dynamism of containerized environments necessitates a forward-thinking approach to security. This involves not only understanding existing vulnerabilities but also anticipating and mitigating future threats.
Emerging Threats and Vulnerabilities
Container environments are susceptible to a variety of threats, including vulnerabilities in the underlying operating system, image manipulation attacks, and vulnerabilities in the container runtime. Sophisticated attackers often leverage these weaknesses, targeting misconfigurations, weak authentication mechanisms, and inadequate access controls. Moreover, the dynamic nature of containerized applications can make it difficult to detect and respond to emerging threats.
The rise of sophisticated attacks, such as supply chain attacks targeting container images, necessitates proactive security measures.
Future Directions in Container Security Practices
Future container security practices will likely emphasize proactive security measures, including secure image scanning and vulnerability management throughout the entire software development lifecycle (SDLC). Automated security testing and continuous monitoring will become increasingly important to identify and address security issues early on. Additionally, zero-trust security models will gain prominence, restricting access to containerized applications and resources based on strict identity and authorization policies.
Latest Advancements in Container Security Technologies
Recent advancements in container security technologies focus on improving image scanning and analysis, hardening container runtimes, and enhancing security monitoring and auditing capabilities. The use of machine learning and AI-powered tools for threat detection and response is becoming more prevalent, enabling automated threat identification and remediation. For example, tools are now available that can detect anomalies in container behavior and flag potential security breaches in real-time.
Examples of Emerging Container Security Tools
Several emerging container security tools are addressing the growing need for robust security in container environments. These tools include:
- Automated container image scanning tools that identify vulnerabilities and misconfigurations in container images.
- Security tools for container orchestration platforms that enhance security controls and monitoring.
- Runtime security tools that monitor container behavior for suspicious activities and prevent attacks.
These tools offer the potential for automating security tasks and significantly reducing the risk of breaches.
Potential Future Trends and Impact on Container Security
The following table summarizes potential future trends and their potential impact on container security.
| Potential Future Trend | Potential Impact on Container Security |
|---|---|
| Increased use of serverless container technologies | Requires new security considerations for the serverless environment, including improved authorization and access control mechanisms. |
| Adoption of advanced threat detection and response tools | Leads to faster detection and mitigation of attacks, reducing the impact of security breaches. |
| Greater emphasis on secure development practices | Reduces the risk of vulnerabilities introduced during the development process. |
| Integration of container security with DevOps pipelines | Enhances security automation and allows for continuous security validation. |
| Focus on zero-trust security principles | Reduces the attack surface by restricting access based on identity and authorization. |
Last Word
In conclusion, securing containers with NIST SP 800-190 provides a robust framework for building secure containerized applications. By understanding and implementing the guidelines, you can mitigate vulnerabilities, enhance security posture, and safeguard sensitive data. This guide offers practical insights, enabling you to proactively address potential risks and maintain a secure container ecosystem.