Sd quickstart service for software ngfw terraform add on – SD quickstart service for software NGFW Terraform add-on provides a streamlined path to integrating secure network gateways into your infrastructure. This comprehensive guide walks you through installation, configuration, and integration with existing systems, ensuring a smooth and secure deployment. We’ll cover everything from basic setup to advanced use cases, complete with practical examples and troubleshooting tips.
The add-on streamlines the process of setting up and configuring Software Defined Networking (SDN) based firewalls (NGFWs) using Terraform. It offers a convenient method to automate the entire process, ensuring consistency and reducing manual errors. The add-on is designed to be flexible, allowing customization to fit specific needs and integrate seamlessly with existing infrastructure.
Introduction to SD Quickstart Service for Software NGFW Terraform Add-on
This service streamlines the deployment of software-defined firewalls (NGFWs) using Terraform. It provides a pre-configured, quick-start solution for organizations looking to rapidly deploy and manage their NGFW infrastructure. The add-on automates the crucial tasks of infrastructure provisioning, configuration, and integration, enabling faster time to value.The Terraform add-on significantly reduces the complexity and time associated with manual NGFW setup, freeing up IT teams to focus on higher-level tasks and strategic initiatives.
Just finished setting up the SD quickstart service for software NGFW Terraform add-on, and wow, it’s pretty slick. While I was waiting for the deployment to complete, I stumbled across some interesting news about the Sony Xperia 1 IV and 5 IV getting Android 13, a major update that should make them even more powerful. Now that the Terraform deployment is done, I’m excited to start testing the new quickstart service and see how it performs.
This automated approach to NGFW deployment allows for consistent and reliable deployments, minimizing errors and ensuring security best practices are adhered to.
Target Audience and Use Cases
This add-on is designed for IT administrators, security engineers, and DevOps teams responsible for deploying and managing software NGFWs. Use cases include:
- New deployment of NGFWs: The service is ideal for rapidly deploying NGFWs in new environments, such as cloud-based infrastructures or on-premises data centers.
- Scaling existing NGFW deployments: Organizations looking to scale their NGFW infrastructure can leverage the add-on to automate the deployment of additional instances, maintaining consistency across the environment.
- Disaster recovery and failover: The automated deployment approach enables rapid deployment of NGFWs during disaster recovery scenarios, ensuring business continuity.
- Multi-cloud deployments: This service facilitates seamless deployment of NGFWs across multiple cloud platforms, simplifying management and ensuring consistency.
Benefits Compared to Alternative Solutions
The SD Quickstart service offers several advantages over manual deployments or other solutions:
- Reduced Deployment Time: Automation drastically reduces the time required to deploy and configure NGFWs, enabling faster time to value.
- Increased Consistency: Automated deployments ensure consistent configurations across all instances, minimizing human error and improving security posture.
- Simplified Management: Centralized management through Terraform allows for easier monitoring and management of the NGFW infrastructure.
- Improved Security Posture: The add-on helps ensure security best practices are followed throughout the deployment process, reducing the risk of security vulnerabilities.
- Cost Optimization: Automation leads to reduced labor costs associated with manual deployments and configuration.
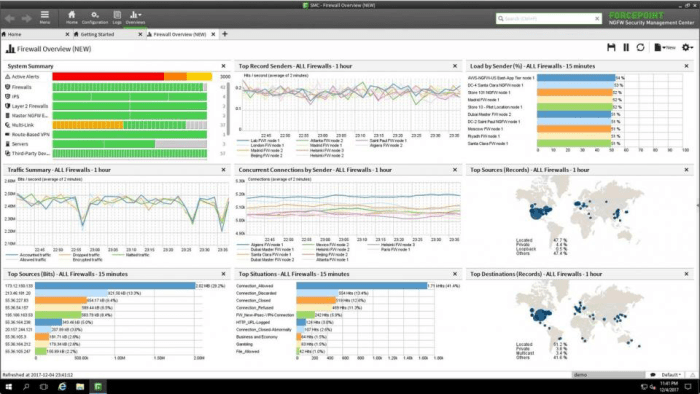
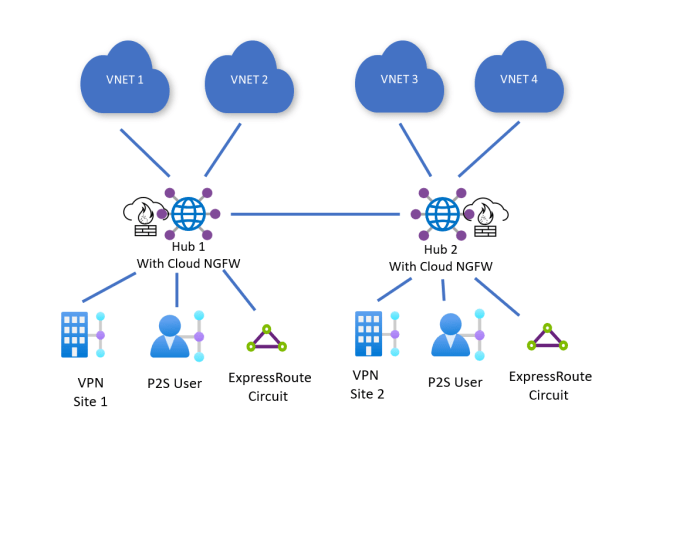
High-Level Architecture
The add-on’s architecture leverages a modular design, promoting flexibility and scalability.
| Component | Description |
|---|---|
| Terraform Provider | Provides the interface for interacting with the NGFW vendor’s infrastructure. |
| NGFW Instance | The core software-defined firewall instance. |
| Configuration Scripts | Terraform scripts defining the NGFW instance’s configuration (e.g., security policies, network connectivity). |
| Infrastructure as Code (IaC) | The core mechanism enabling automated deployment and management of the NGFW infrastructure. |
| Centralized Management Console | Facilitates centralized monitoring and management of the NGFW instances. |
This modular architecture enables easier customization and integration with existing infrastructure.
The service’s architecture is designed to be highly scalable and adaptable to various environments and use cases. This modularity allows for straightforward customization to match specific organizational needs and ensures efficient maintenance.
Installation and Setup Procedures
This section details the step-by-step process for installing the Terraform add-on for Software NGFW, along with necessary prerequisites, configuration options, and various installation methods. Understanding these procedures is crucial for seamless integration and efficient management of your network security infrastructure.Setting up the Terraform add-on requires careful attention to prerequisites and configurations. Proper setup ensures the add-on functions correctly and integrates seamlessly with your existing infrastructure.
This document provides a comprehensive guide to simplify the process.
Prerequisites
Before installing the Terraform add-on, ensure the following prerequisites are met:
- A valid account with necessary permissions on the target cloud platform (e.g., AWS, Azure, GCP).
- A properly configured Terraform environment with the required providers (e.g., aws, azurerm, google). Verify the versions are compatible with the add-on.
- The latest version of Terraform installed on your local machine.
- A well-defined network topology and desired configuration for the Software NGFW instances.
Installation Methods, Sd quickstart service for software ngfw terraform add on
This section Artikels the available methods for installing the Terraform add-on, including manual and automated approaches. Each method provides distinct advantages depending on your technical expertise and infrastructure setup.
| Method | Steps |
|---|---|
| Manual Installation |
|
| Automated Installation |
|
Configuration Options
The Terraform add-on offers various configuration options for customizing the Software NGFW instances. These options enable tailored security policies and configurations to meet specific needs.
- Network Configuration: Define the network settings for the Software NGFW instances, including subnets, IP addresses, and routing tables.
- Security Policies: Configure detailed security policies for inbound and outbound traffic, including firewall rules and access controls. This allows for precise control over network access.
- Authentication Methods: Specify authentication methods, such as username/password or API keys, for secure access to the Software NGFW instances.
- Monitoring and Logging: Configure logging and monitoring options for the Software NGFW instances, enabling real-time insights into network activity and potential security breaches.
Configuration Options and Customization
This section dives into the configurable parameters of the SD Quickstart Service for Software NGFW Terraform Add-on, enabling you to tailor the service to specific network security needs. Understanding these options allows for optimized performance and enhanced security posture. Customization is crucial for adapting the service to various environments and use cases.By modifying default settings, administrators can fine-tune the service to better suit their specific requirements, whether it’s prioritizing throughput, enhancing security policies, or adjusting logging levels.
Proper configuration is paramount for achieving optimal performance and preventing potential issues.
Configuration Parameters
The Terraform add-on provides a comprehensive set of configuration parameters, enabling granular control over the service’s behavior. This allows administrators to adjust the service to specific network topologies and security policies.
- `firewall_rules`: This parameter defines the security rules enforced by the Software NGFW. The rules dictate which traffic is allowed or blocked, forming the core of the firewall’s functionality. Examples include allowing SSH traffic on port 22, blocking malicious IP ranges, and permitting internal network communication.
- `logging_level`: This setting controls the verbosity of logs generated by the service. Adjusting this parameter allows administrators to prioritize different levels of detail in their monitoring. For example, setting it to “DEBUG” captures extensive data for troubleshooting, while “INFO” provides sufficient information for routine monitoring.
- `performance_tuning`: This parameter enables specific optimizations to enhance service performance. For instance, these optimizations could involve adjusting packet processing rates, prioritizing critical traffic, or enabling advanced caching mechanisms. Adjustments can be crucial for handling high-traffic environments.
- `security_policy_enforcement`: This parameter governs the rigor of security policy enforcement. Higher levels of enforcement can block more potentially malicious traffic, but might also impact legitimate traffic in certain circumstances. It’s vital to balance security with application performance. For example, selecting “high” enforcement could reduce the risk of denial-of-service attacks but may slightly slow down legitimate connections.
Impact of Configuration Choices
The chosen configuration settings directly impact the service’s performance and security. Careful consideration of these choices is crucial to prevent unintended consequences.
I’ve been diving deep into the SD Quickstart service for Software NGFW Terraform add-on lately, and it’s been a real eye-opener. While fascinating advancements in space exploration, like the recent delay of the NASA Ingenuity Mars helicopter flight ( nasa ingenuity mars helicopter flight delayed wednesday ), capture our attention, I’m still focused on the practical applications of this service for efficient network security automation.
It’s amazing how quickly you can deploy and configure everything with Terraform, making it a huge time saver for network engineers.
- `firewall_rules`: Stricter rules can improve security but may hinder legitimate traffic flow, potentially leading to application downtime. Conversely, lax rules increase the risk of security breaches.
- `logging_level`: High logging levels generate significant data, increasing storage requirements and potentially impacting system performance. Lower levels reduce the amount of data but may reduce troubleshooting capabilities.
- `performance_tuning`: Aggressive tuning can significantly improve throughput but may introduce latency in certain situations. Proper tuning is essential to ensure both speed and stability.
- `security_policy_enforcement`: High enforcement levels enhance security but can impact legitimate application access. Careful consideration of the balance between security and application performance is critical.
Configuration Options Summary
This table summarizes the available configuration parameters, their descriptions, and default values. These values provide a starting point for customizing the service to your specific environment.
| Parameter | Description | Default Value |
|---|---|---|
| `firewall_rules` | Defines security rules for traffic filtering. | Default ruleset (allowing SSH, HTTPS, etc.) |
| `logging_level` | Sets the level of detail for generated logs. | INFO |
| `performance_tuning` | Enables optimizations to improve service performance. | Balanced |
| `security_policy_enforcement` | Controls the rigor of security policy enforcement. | Medium |
Integration with Existing Systems
This Terraform add-on for software NGFWs is designed with seamless integration in mind. Understanding how to connect it to your existing infrastructure is crucial for a smooth transition and maximizing the benefits of the new security solution. This section details the integration points and configuration procedures, providing a practical guide for bridging the gap between your current systems and the new add-on.The add-on utilizes standard APIs and protocols, facilitating integration with a wide array of systems.
Careful configuration is key to ensuring data flows correctly between the add-on and your existing infrastructure. This approach reduces potential conflicts and maximizes compatibility.
Integration Points and Required Steps
The add-on offers various integration points, allowing flexible connections to different parts of your existing infrastructure. Each integration point requires specific configuration steps to establish a reliable connection.
The SD Quickstart service for Software NGFW Terraform add-on is a game-changer, streamlining deployment. However, recent developments in the funding world, like the Founders Fund’s involvement with Peter Thiel, SVB, and Silicon Valley Bank’s ESG initiatives, demonstrate the complex financial ecosystems that can impact even seemingly straightforward tech solutions. Ultimately, understanding these interconnected factors is crucial for navigating the complexities of modern software deployments like the SD Quickstart service.
- Network Management Systems (NMS): The add-on supports integration with popular network management systems through a standardized API. Configuration involves specifying the API endpoint, authentication credentials, and the data fields to be exchanged. This ensures the NGFW configuration is reflected in the NMS, providing a unified view of your network security posture.
- Security Information and Event Management (SIEM) Systems: Integrating with SIEM systems allows for real-time threat detection and analysis. The add-on can push security events, such as alerts and logs, to the SIEM for correlation and analysis. Specific configuration involves defining the SIEM endpoint, authentication method, and the desired log format.
- Configuration Management Systems (CMS): For organizations using CMS tools, the add-on can be integrated to automate the deployment and configuration of the NGFW. This involves creating a predefined configuration file or schema, which the CMS can use to update the add-on in the desired state.
- Vulnerability Scanning Tools: Integration with vulnerability scanning tools allows the add-on to automatically update its security rules based on identified vulnerabilities. This ensures the NGFW is always protected against the latest threats. The integration process involves specifying the tool’s API and the vulnerability data format.
Comparison with Other Similar Add-ons
The integration process with this add-on leverages industry-standard protocols and APIs, which makes it compatible with a wider range of existing systems compared to some competitors. Its modular design and clear documentation facilitate the integration process. Other add-ons might require custom scripting or specific configurations, whereas this add-on prioritizes a more streamlined and standardized approach.
Integration Scenarios and Configuration Details
The table below illustrates different integration scenarios and the required configuration details.
| System | Integration Points | Configuration |
|---|---|---|
| System A (NMS) | API integration for real-time configuration updates and status monitoring | Specify API endpoint, authentication credentials (API key or token), data fields for synchronization. |
| System B (SIEM) | Log forwarding and alert notification | Define SIEM endpoint, authentication details (username/password or API key), desired log format (e.g., JSON, Syslog). |
| System C (CMS) | Automated configuration deployment | Create a configuration template, define the connection to the CMS, specify variables to be passed to the add-on. |
| System D (Vulnerability Scanner) | Automatic rule updates based on identified vulnerabilities | Specify the vulnerability scanner’s API, the vulnerability data format (e.g., CVE IDs, CVSS scores), and any required authentication. |
Security Considerations: Sd Quickstart Service For Software Ngfw Terraform Add On
Deploying a Software-Defined Firewall (SD-Firewall) add-on requires careful attention to security to prevent vulnerabilities and ensure the integrity of the network. Proper configuration and management practices are crucial to mitigating risks associated with the add-on. This section details potential security risks, best practices for securing the add-on, and recommended security measures.Implementing robust security measures for the SD-Firewall add-on is paramount to maintaining network integrity and protecting sensitive data.
By proactively addressing potential vulnerabilities and following best practices, organizations can minimize the risk of breaches and ensure the reliable operation of their SD-Firewall.
Potential Security Risks
The SD-Firewall add-on, like any software component, presents potential security risks if not implemented and managed securely. These risks can arise from misconfigurations, vulnerabilities in the add-on itself, or inadequate access controls. Poorly configured rules can allow unauthorized access or malicious traffic to bypass the firewall. Outdated versions of the add-on might contain known vulnerabilities that attackers could exploit.
Furthermore, inadequate access control to the add-on’s configuration and management interface can expose the system to unauthorized modifications or malicious attacks.
Best Practices for Securing the Add-on’s Configuration
Implementing strong security practices during the add-on configuration is vital to minimize vulnerabilities. This includes restricting access to the configuration interface, employing strong passwords, and adhering to a principle of least privilege. Regularly reviewing and auditing configurations helps identify and address potential misconfigurations.
- Access Control: Implement role-based access control (RBAC) to restrict access to the add-on’s configuration interface. Only authorized personnel should be granted the necessary privileges for configuration and management. Employ multi-factor authentication (MFA) for all administrative accounts to enhance security further.
- Strong Passwords: Use strong, unique passwords for all accounts accessing the add-on. Utilize a password manager to generate and securely store these passwords. Avoid using easily guessable passwords or passwords that are reused across multiple systems.
- Principle of Least Privilege: Grant users only the necessary permissions to perform their tasks. Limit administrative privileges to authorized personnel to prevent unauthorized modifications to the add-on’s configuration.
- Regular Audits: Regularly review and audit the add-on’s configuration to identify and address potential misconfigurations. Implement automated tools to detect and report unusual or potentially harmful changes in the configuration.
Recommended Security Measures for Managing the Add-on
Proactive management of the SD-Firewall add-on is essential for maintaining security. This includes regular updates, vulnerability scanning, and incident response planning. Monitoring network traffic for suspicious activity and promptly addressing security incidents is also vital.
- Regular Updates: Keep the add-on’s software and dependencies updated to patch known vulnerabilities. Utilize automated update mechanisms to ensure timely updates are applied to prevent known exploits. Following a structured update schedule ensures timely security patches are deployed.
- Vulnerability Scanning: Conduct regular vulnerability scans of the add-on and the underlying infrastructure. Use automated tools to identify potential vulnerabilities and promptly address any found issues. This proactive approach reduces the risk of known exploits being leveraged against the system.
- Incident Response Plan: Develop and regularly test an incident response plan for security incidents related to the add-on. Establish clear procedures for detecting, containing, and recovering from security breaches. A well-defined plan helps minimize the impact of potential incidents.
- Monitoring: Continuously monitor network traffic for suspicious activity. Use intrusion detection systems (IDS) and security information and event management (SIEM) tools to detect and respond to potential threats. Implement real-time alerts for unusual network activity to quickly identify potential attacks.
Security Considerations List
To ensure secure deployment of the SD-Firewall service, consider these critical points:
- Implement strong access controls and authentication mechanisms for all administrative accounts.
- Regularly update the add-on’s software and dependencies to address known vulnerabilities.
- Conduct regular vulnerability scans to identify and mitigate potential weaknesses.
- Establish a comprehensive incident response plan to address security incidents promptly.
- Monitor network traffic for suspicious activity and promptly investigate any anomalies.
- Maintain detailed logs of all configurations and changes to the add-on.
- Comply with relevant industry standards and regulations for security practices.
Troubleshooting and Support
Navigating potential snags in your Software NGFW Terraform add-on deployment is crucial. This section details common issues, support avenues, and debugging techniques to ensure a smooth experience. A proactive approach to troubleshooting minimizes downtime and maximizes your deployment’s efficiency.Effective troubleshooting hinges on understanding potential pitfalls and having access to robust support channels. This section equips you with the knowledge to identify and resolve common problems, and guides you on how to gather necessary information for support requests.
Common Issues and Solutions
Troubleshooting involves identifying and resolving issues. The following table Artikels common problems encountered during deployment and provides corresponding solutions.
| Issue | Solution |
|---|---|
| Terraform configuration errors | Verify syntax in Terraform configuration files, especially variable definitions and resource configurations. Use Terraform’s built-in validation tools to pinpoint errors and refer to the add-on’s documentation for correct configuration parameters. |
| Connection failures to the cloud provider | Check network connectivity to the cloud provider. Ensure appropriate firewall rules are configured and that the cloud provider’s authentication credentials are valid and properly configured in Terraform. Test connectivity using the cloud provider’s command-line tools. |
| Unexpected add-on behavior | Review logs from the Software NGFW deployment and cloud provider resources. Verify the add-on’s configuration aligns with intended behavior and expected outputs. Compare actual outputs with expected outputs from the documentation. |
| Resource provisioning failures | Thoroughly review Terraform state files to pinpoint any inconsistencies or missing resources. Ensure dependencies between resources are correctly established. Double-check the configuration of the Software NGFW resources. |
Accessing Support Resources
Access to timely and effective support is critical. The add-on provides several avenues for assistance, including detailed documentation, a dedicated support forum, and direct email support channels. Explore these resources to get answers to your questions.
- Documentation: Comprehensive documentation, readily available online, details installation procedures, configuration options, and troubleshooting steps. Thorough examination of this resource can resolve many issues independently.
- Support Forum: Engage with a community of users and experts in the dedicated support forum. This platform facilitates the exchange of insights, solutions to common problems, and collaborative problem-solving.
- Email Support: For complex issues or unique situations, direct email support provides a dedicated channel for assistance from the add-on developers. Submit detailed reports, including the error messages, configuration, and steps taken.
Collecting Debugging Information
Collecting relevant information is paramount for accurate diagnosis and efficient resolution of issues. This information will aid support personnel in understanding the problem and its context.
- Terraform State File: Provide the Terraform state file to illustrate the current state of the deployment. This file details the resources provisioned and their attributes.
- Add-on Logs: Capture and provide logs generated by the Software NGFW add-on during the process. Logs often contain crucial information about the steps taken and encountered errors.
- Cloud Provider Logs: Gather logs from the cloud provider’s services involved in the deployment. These logs can highlight network issues, authentication problems, or resource allocation failures.
- Configuration Files: Include the configuration files used in the Terraform deployment, including the add-on-specific configuration. This aids in understanding the parameters applied to the Software NGFW deployment.
Troubleshooting Guide
This guide offers a systematic approach to resolving common issues with the Software NGFW Terraform add-on. Follow these steps to identify and rectify problems.
- Verify Configuration: Double-check all configuration settings for accuracy. Ensure correct parameter values and adherence to the documentation.
- Check Logs: Examine logs from Terraform, the cloud provider, and the add-on for error messages and relevant information. Understand the sequence of events leading to the problem.
- Isolate the Issue: Narrow down the problem by progressively testing different configurations and eliminating potential causes.
- Test Solutions: Implement potential solutions and verify that they resolve the issue. Implement solutions gradually, and test them before fully deploying changes.
- Contact Support: If the issue persists, contact support with the collected debugging information.
Advanced Use Cases and Examples
This section delves into sophisticated applications of the SD Quickstart Service for Software NGFW Terraform Add-on. We’ll explore how to customize the add-on for specific needs, demonstrate complex deployments, and highlight the benefits and challenges associated with each example.Advanced use cases often require tailoring the add-on’s configuration beyond the basic setup. This section will demonstrate how to adapt the add-on to handle these more intricate scenarios.
Examples will focus on leveraging the add-on’s flexibility to achieve specific security goals in diverse network topologies.
Multi-Site Deployment with Centralized Management
This use case focuses on deploying the Software NGFW across multiple geographically dispersed sites while maintaining centralized management. Centralized management streamlines configuration updates and security policies across all locations, ensuring consistency and reducing administrative overhead. The add-on enables this by allowing for the creation of a central management console that controls the NGFW instances at each site. This architecture is vital for organizations with distributed operations.
- The add-on facilitates the creation of a unified policy engine. This engine can be used to enforce security policies across all sites, ensuring a consistent security posture regardless of the location.
- Implementing a central logging and monitoring system is crucial for tracking and analyzing security events across all sites. This helps to detect and respond to threats more effectively.
- Using a central configuration management system allows for automated updates and configurations of the NGFW instances at each site, reducing manual effort and minimizing potential errors.
High Availability and Failover
This use case demonstrates how to implement high availability for the Software NGFW using the add-on. By deploying multiple instances of the NGFW in a high-availability configuration, the service ensures continuous operation even if one instance fails. This is crucial for maintaining uninterrupted network access and security.
- The add-on supports configuring redundant NGFW instances, enabling automatic failover to a standby instance if the primary instance encounters issues.
- The add-on facilitates seamless failover, ensuring minimal disruption to network traffic and maintaining security policies during the transition.
- Monitoring the health of both instances and facilitating automatic failover are key components of this configuration.
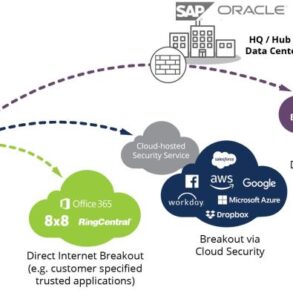
Integration with Cloud-Based Security Tools
This use case focuses on integrating the Software NGFW with cloud-based security tools, such as cloud access security brokers (CASBs) or security information and event management (SIEM) systems. This integration provides comprehensive visibility into network traffic and enhances security analysis.
- The add-on allows for the seamless exchange of security events and alerts between the Software NGFW and cloud-based security tools. This allows for more comprehensive threat detection and response.
- Data exchange between the NGFW and cloud-based security tools provides a richer picture of network activity, enabling faster identification of malicious activity and security breaches.
- Integrating with SIEM systems facilitates detailed analysis of security events, allowing for trend identification and proactive security measures.
Customizing Policies for Specific Applications
This use case describes the ability to customize security policies based on specific application types or user groups. This approach enables targeted protection for sensitive data and applications, preventing unauthorized access while allowing authorized access.
- The add-on supports defining security policies that apply to specific applications or user groups, allowing for fine-grained control over network access.
- Defining granular policies for various applications ensures only authorized users or systems can access specific applications.
- This customization allows the Software NGFW to be tailored to the unique security requirements of each application or user group.
Final Wrap-Up
In conclusion, the SD quickstart service for software NGFW Terraform add-on simplifies the deployment and management of secure network gateways. By automating the installation, configuration, and integration processes, this add-on enhances efficiency and security. This comprehensive guide provides the necessary knowledge to confidently utilize this tool, ensuring a secure and efficient infrastructure. Whether you’re a seasoned DevOps engineer or just starting your journey, this guide will empower you to leverage the power of Terraform for SDN deployments.