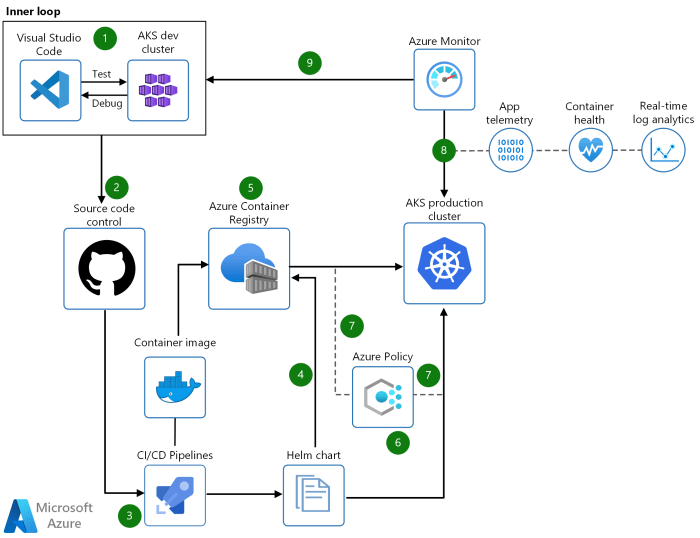
Poisoned pipeline execution cicd sec4 – Poisoned pipeline execution CI/CD sec4 describes the malicious introduction of harmful code into a Continuous Integration/Continuous Delivery (CI/CD) pipeline. Attackers exploit vulnerabilities in these pipelines to compromise software development lifecycles. This can lead to devastating consequences, ranging from data breaches to system takeovers. Understanding the methods attackers use, the potential impacts, and how to secure pipelines is crucial for organizations.
This exploration delves into the strategies to defend against such attacks and implement secure CI/CD practices.
This in-depth analysis of poisoned pipeline execution within CI/CD pipelines covers a wide range of topics, from the fundamentals of poisoned pipelines to the latest security measures. It also explores common vulnerabilities, best practices, and detailed case studies to provide practical insights for implementing robust security protocols.
Introduction to Poisoned Pipeline Execution in CI/CD
Poisoned pipeline execution is a sophisticated attack vector targeting the Continuous Integration/Continuous Delivery (CI/CD) pipeline. It involves injecting malicious code into the pipeline’s workflow, potentially leading to the deployment of compromised software. This attack can bypass traditional security measures and have significant repercussions for the affected organization. Understanding the methods, impacts, and mitigation strategies for poisoned pipeline attacks is crucial for robust CI/CD security.
Common Attack Methods
Attackers employ various tactics to introduce malicious code into CI/CD pipelines. These often exploit vulnerabilities in the pipeline’s configuration, build tools, or even the repository itself. Common methods include modifying build scripts, manipulating configuration files, or inserting malicious code into source code repositories. Attackers may leverage vulnerabilities in automated tools or use social engineering to gain access to sensitive areas of the CI/CD infrastructure.
Potential Impacts on the Software Development Lifecycle
A successful poisoned pipeline attack can have devastating consequences on the software development lifecycle. Malicious code deployed through the compromised pipeline can lead to data breaches, unauthorized access, financial losses, and reputational damage. The attack can disrupt the development process, cause significant delays, and erode customer trust. The consequences are often widespread and long-lasting.
Real-World Examples
Several instances of poisoned pipeline attacks have been reported in the cybersecurity landscape. One example involves a team unknowingly integrating malicious code into their CI/CD pipeline, resulting in a compromised application and a data breach. Another case highlights the vulnerability of open-source components used in the CI/CD pipeline, where attackers exploited vulnerabilities in these components to inject malicious code.
Attack Vectors and Consequences
| Attack Vector | Description | Impact | Mitigation Strategy |
|---|---|---|---|
| Compromised Build Scripts | Attackers modify build scripts to include malicious code that is then executed during the pipeline’s build process. | Malicious code is integrated into the final product, potentially leading to unauthorized access or data breaches. | Implement strict access controls to build scripts, utilize code analysis tools to detect anomalies, and regularly audit build scripts for malicious code. |
| Manipulated Configuration Files | Attackers modify configuration files used by the CI/CD pipeline, altering the pipeline’s behavior to facilitate malicious code injection. | Malicious code is integrated into the build process, leading to the deployment of a compromised product. | Implement robust access controls and version control for configuration files. Employ tools to detect changes to configuration files and prevent unauthorized modifications. |
| Malicious Code Injection into Source Code Repositories | Attackers insert malicious code into the source code repository, which is then automatically integrated into the project by the CI/CD pipeline. | Compromised code is integrated into the final product, potentially leading to security vulnerabilities and data breaches. | Implement robust security measures for source code repositories, including multi-factor authentication, code review processes, and automated security scanning. |
| Exploiting Vulnerabilities in Automated Tools | Attackers leverage vulnerabilities in CI/CD tools or components to gain unauthorized access and inject malicious code into the pipeline. | Compromised CI/CD pipeline allows malicious code to be deployed, leading to security vulnerabilities and data breaches. | Regularly update CI/CD tools and components to patch vulnerabilities. Employ security scanning tools to detect vulnerabilities in the pipeline. |
Securing the CI/CD Pipeline from Poisoning
Protecting your CI/CD pipeline from malicious code injections, often referred to as “poisoned pipelines,” is paramount to maintaining the integrity and security of your software development process. A compromised pipeline can lead to the deployment of vulnerable or even malicious software, potentially causing significant damage to your organization and its users. This necessitates a robust security strategy that goes beyond basic access controls.A robust security posture for CI/CD pipelines requires a multi-layered approach, addressing vulnerabilities at various stages of the development lifecycle.
This includes proactive measures to prevent malicious code from entering the pipeline, as well as reactive measures to detect and mitigate the effects of a successful attack.
Robust Security Strategy for Preventing Poisoned Pipelines
A strong security strategy necessitates a layered approach, incorporating several key elements. These elements work together to create a secure environment for code development and deployment. A robust security strategy involves implementing multiple safeguards at different stages of the CI/CD pipeline to prevent malicious code from entering the pipeline.
Poisoned pipeline execution in CI/CD security, specifically sec4, is a serious concern. Understanding these vulnerabilities is crucial for building robust systems. Interestingly, while researching this, I stumbled upon an LG V60 Android 12 update, LG V60 Android 12 update which highlights the importance of keeping software updated to patch potential weaknesses. Ultimately, proactive security measures are key to preventing issues like poisoned pipeline execution.
Importance of Code Signing and Validation
Code signing and validation are crucial elements in verifying the authenticity and integrity of code artifacts. Digital signatures, generated using a private key, allow developers to prove that the code hasn’t been tampered with during transit. Validating these signatures ensures that the deployed code matches the signed version, thus preventing unauthorized modifications. This verification process is essential to prevent malicious actors from injecting compromised code into the pipeline.
Role of Secure Code Repositories and Access Control
Secure code repositories and stringent access controls are essential to preventing unauthorized access to source code and sensitive information. Employing strong authentication mechanisms, least privilege access, and regular audits helps maintain the integrity of the codebase. This approach reduces the potential for malicious code introduction through unauthorized access to repositories. For example, limiting access to specific branches or files, enforcing two-factor authentication, and implementing rigorous code review procedures significantly enhance security.
Detecting Anomalies in Build Processes and Pipeline Execution, Poisoned pipeline execution cicd sec4
Monitoring for anomalies in build processes and pipeline execution is vital for detecting potential malicious activity. This includes detecting deviations from expected behavior, such as unusually long build times, unexpected errors, or unusual code changes. Implementing tools for real-time monitoring and analysis helps identify suspicious patterns that may indicate malicious code injection. For instance, a sudden surge in the number of build failures or a drastic change in code metrics could signal the presence of malicious code.
Implementing Secure CI/CD Practices
Implementing secure CI/CD practices requires a structured approach, encompassing various steps. This table Artikels the steps for establishing a secure CI/CD environment.
| Step | Description | Tools/Techniques | Implementation Considerations |
|---|---|---|---|
| Establish a strong access control model | Implement role-based access control (RBAC) to limit access to sensitive resources and restrict pipeline execution permissions. | RBAC implementations, identity and access management (IAM) systems | Define clear roles and permissions for each team member, regularly review and update access controls. |
| Employ code signing and validation | Use digital signatures to verify the authenticity and integrity of code artifacts before deployment. | OpenSSL, GPG, code signing tools | Ensure that all code changes are signed before being integrated into the pipeline. |
| Utilize secure code repositories | Employ code repositories that provide strong security features, such as advanced access control and encryption. | GitLab, GitHub Enterprise, Bitbucket | Enforce strict access control and security best practices within the repository. |
| Implement vulnerability scanning | Integrate vulnerability scanners to detect potential security flaws in code and configurations. | Snyk, SonarQube, OWASP ZAP | Schedule regular scans to identify and address vulnerabilities before deployment. |
| Monitor pipeline execution for anomalies | Track pipeline execution for unusual behavior, such as failed builds or unexpected delays. | Pipeline monitoring tools, log analysis tools | Configure alerts to notify security personnel about suspicious activity. |
Analyzing Vulnerabilities and Threats
CI/CD pipelines, while automating software delivery, can become vulnerable entry points if not meticulously secured. Understanding the potential weaknesses and threats is crucial for proactive defense. This section delves into common vulnerabilities, the risks of misconfigurations, and the importance of automated security scanning and proactive threat modeling.Identifying and mitigating these vulnerabilities strengthens the overall security posture of the CI/CD pipeline, preventing potential exploits and ensuring the integrity of deployed software.
Common Vulnerabilities in CI/CD Pipelines
CI/CD pipelines are susceptible to various vulnerabilities, stemming from insecure configurations, outdated tools, and poorly implemented security controls. These vulnerabilities can be exploited by attackers to inject malicious code, compromise sensitive data, or disrupt the entire pipeline. Examples include weak authentication mechanisms, insecure storage of secrets, and inadequate input validation. The potential consequences range from data breaches to complete system compromise.
Potential Risks of Insecure Configuration Settings and Misconfigurations
Insecure configuration settings and misconfigurations are significant threats to CI/CD pipelines. Improperly configured servers, repositories, or tools can expose sensitive information, enable unauthorized access, or allow malicious actors to manipulate pipeline processes. For example, an improperly configured artifact repository can allow access to sensitive code or configuration files. This can lead to the exposure of intellectual property or allow for the insertion of malicious code.
Significance of Automated Security Scanning and Vulnerability Assessments
Automated security scanning and vulnerability assessments play a critical role in identifying potential weaknesses in the CI/CD pipeline. These tools automatically scan code, configurations, and dependencies for known vulnerabilities. Early detection of vulnerabilities through these automated processes enables timely remediation and minimizes the risk of exploitation.
Importance of Proactive Threat Modeling in CI/CD Pipeline Design
Proactive threat modeling in CI/CD pipeline design is essential for anticipating potential attacks and vulnerabilities. By proactively identifying potential threats and attack vectors, organizations can design the pipeline with built-in security controls. This reduces the likelihood of vulnerabilities being exploited during the software development lifecycle. A well-defined threat model helps guide the development of security controls and safeguards.
CI/CD Pipeline Security Policy
A well-defined CI/CD pipeline security policy is vital for maintaining a robust security posture. The policy should address various security aspects, including access controls, vulnerability management, and incident response.
| Policy Element | Description | Example Implementation | Rationale |
|---|---|---|---|
| Access Control | Define and enforce access permissions for users and systems interacting with the pipeline. | Restrict access to sensitive components (e.g., repositories, servers) using role-based access control (RBAC). | Prevent unauthorized access and manipulation of sensitive resources. |
| Secret Management | Implement a secure way to store and manage sensitive information like API keys and passwords. | Use a dedicated secret management system (e.g., HashiCorp Vault) to store and retrieve secrets securely. | Protect sensitive data from exposure and unauthorized access. |
| Input Validation | Validate all inputs to prevent injection attacks. | Sanitize user input before processing and validate it against expected formats. | Prevent malicious code from being executed. |
| Regular Vulnerability Scanning | Schedule automated scans to identify and remediate vulnerabilities. | Integrate vulnerability scanning tools (e.g., Snyk, Checkmarx) into the CI/CD pipeline. | Proactively identify and address vulnerabilities before they are exploited. |
Incident Response and Recovery
Poisoned pipeline execution attacks, while insidious, are not insurmountable. A robust incident response plan is crucial for minimizing damage and restoring functionality. This plan should be well-documented and regularly reviewed, ensuring all team members are familiar with the procedures. A swift and coordinated response is essential to mitigate the impact of a compromised pipeline.Effective incident response involves a systematic approach to detection, containment, restoration, and remediation.
This process aims to quickly isolate the threat, restore the pipeline to a known good state, and ultimately prevent future occurrences. A well-defined process allows for a controlled and predictable recovery, minimizing the impact on development and deployment processes.
Detecting a Poisoned Pipeline Execution Attack
Identifying a poisoned pipeline execution attack often relies on proactive monitoring and anomaly detection. Regular analysis of pipeline logs, metrics, and build artifacts can uncover suspicious patterns. Unusual build times, unexpected failures, or discrepancies in build artifacts are potential indicators. Implementing automated tools to monitor pipeline health and trigger alerts for deviations from expected behavior is crucial.
For instance, a sudden spike in build failures or a significant increase in build time across multiple jobs could indicate a malicious injection.
Isolating and Containing the Affected Components
Immediately isolating the affected components of the pipeline is paramount. This involves temporarily halting the execution of the compromised pipeline or specific stages. Identify the pipeline stage or branch where the malicious code or artifact was introduced. Temporarily isolate the pipeline stage or branch to prevent further propagation of the attack. This should be done in a controlled manner, preventing disruptions to other, unaffected parts of the CI/CD system.
Poisoned pipeline execution in CI/CD security (sec4) is a serious concern. It’s like a hidden threat lurking in your automated processes. This vulnerability can really mess things up, and unfortunately, sometimes the most basic system components are the weakest. It’s interesting to note that sometimes the cheapest iPhone has a more powerful processor than the most expensive Android phone, highlighting how seemingly disparate things can be connected.
This article on processing power differences is a good example of this. Ultimately, understanding and mitigating poisoned pipeline execution remains crucial in maintaining robust CI/CD security.
Restoring the Pipeline to a Known Good State
Restoring the pipeline to a known good state is a critical step. This involves reverting to a previous, known-good version of the codebase or pipeline configuration. Maintaining frequent backups of the codebase and pipeline configuration is essential for a swift recovery. Employing version control systems allows for a straightforward rollback to a previously functioning version. Verify the integrity of the restored components.
Poisoned pipeline execution in CI/CD security, specifically Sec4, is a real concern. It’s all about vulnerabilities in the automated build and deployment process. Understanding these risks is crucial, but it also makes me think about the rapid advancements in EV technology and why people are willing to pay a premium for them. Here’s why people are willing to pay more for an EV – factors like battery technology and the long-term cost savings of reduced fuel expenses.
Ultimately, this highlights the importance of secure CI/CD pipelines to avoid costly security breaches and maintain consumer trust, even in the face of exciting new technologies.
Remediating the Compromised Code or Artifacts
Addressing the compromised code or artifacts is a crucial part of the recovery process. This includes identifying and removing malicious code or artifacts, and applying appropriate security hardening measures to prevent future attacks. Thoroughly review the codebase and artifacts affected by the attack, searching for malicious code, backdoors, or other suspicious changes. Utilize static analysis tools and vulnerability scanners to pinpoint and remove the malicious code.
Handling a Poisoned Pipeline Attack Checklist
| Step | Action | Resources | Timeframe |
|---|---|---|---|
| 1 | Identify the compromised pipeline stage or branch. | Pipeline logs, monitoring tools | Immediate |
| 2 | Isolate the affected components. | Pipeline configuration management tools | Within 1 hour |
| 3 | Rollback to a known good version of the codebase or pipeline configuration. | Version control system, backup system | Within 2 hours |
| 4 | Analyze the compromised code or artifacts for malicious code. | Security scanners, static analysis tools | Within 24 hours |
| 5 | Remove or fix the malicious code or artifacts. | Development team, security experts | Within 24-48 hours |
| 6 | Re-validate the pipeline with a known-good configuration. | Testing environment | Within 48 hours |
| 7 | Implement security hardening measures. | Security guidelines, best practices | Ongoing |
Tools and Technologies for Securing Pipelines
CI/CD pipelines, while crucial for modern software development, are susceptible to various security threats. Protecting these pipelines from malicious actors, often referred to as “poisoned pipelines,” requires robust tools and technologies. This section details some key solutions for securing CI/CD pipelines and showcases how to implement them effectively.Implementing security measures in the CI/CD pipeline is vital for mitigating risks.
Failure to adequately secure these pipelines can lead to significant vulnerabilities, impacting the integrity and reliability of software deployments.
Security Scanning Tools
Comprehensive security scanning tools are essential for identifying vulnerabilities early in the pipeline. These tools analyze code, configurations, and dependencies, flagging potential weaknesses. The earlier vulnerabilities are detected, the less costly and time-consuming they are to address.
- Snyk: Snyk is a widely used tool for detecting vulnerabilities in dependencies. It helps identify and address vulnerabilities in open-source libraries and packages. Snyk integrates with popular CI/CD platforms and offers a comprehensive vulnerability management solution.
- SonarQube: SonarQube is a platform for analyzing code quality and security issues. It provides comprehensive metrics, identifying code smells, security vulnerabilities, and potential bugs. It supports various programming languages and integrates well with CI/CD pipelines.
- Checkmarx: Checkmarx provides a comprehensive platform for static and dynamic application security testing (SAST and DAST). It analyzes code and runtime behavior, identifying vulnerabilities and weaknesses. Checkmarx’s platform offers a broad range of features and capabilities.
Vulnerability Detection Tools
These tools are crucial for identifying weaknesses in applications throughout the development lifecycle.
- OWASP Dependency-Check: This open-source tool identifies vulnerabilities in software dependencies. It scans the project’s dependencies for known vulnerabilities, providing a comprehensive report for remediation.
- Fortify: Fortify offers a suite of tools for security testing, including static analysis and dynamic analysis. It helps detect and analyze vulnerabilities, including those in code, configurations, and dependencies. The platform offers various testing options, allowing teams to adapt to their specific needs.
Implementing a Secure CI/CD Pipeline with Snyk
Implementing Snyk in a CI/CD pipeline involves integrating it with the pipeline’s stages. This integration allows Snyk to scan code and dependencies during the build and test phases, flagging any identified vulnerabilities. Upon detecting vulnerabilities, Snyk generates reports and notifications, enabling prompt remediation.
# Example pipeline (using a hypothetical pipeline definition language)
stages:
-build:
commands:
-npm install
-snyk test
-test:
dependencies: [build]
commands:
-npm test
on_failure: [notify_slack]
This example demonstrates a basic pipeline integrating Snyk. The `snyk test` command runs Snyk’s vulnerability analysis during the build phase.
If vulnerabilities are found, the pipeline will fail, and a notification will be sent to Slack. This ensures that vulnerabilities are detected and addressed early in the development process.
Best Practices for Preventing Poisoned Pipeline Attacks: Poisoned Pipeline Execution Cicd Sec4
Poisoned pipeline attacks represent a significant threat to the integrity and security of Continuous Integration/Continuous Delivery (CI/CD) pipelines. These attacks can compromise software quality, introduce vulnerabilities, or even disrupt the entire development process. Implementing robust security measures within the CI/CD pipeline is crucial to mitigate these risks. Proactive measures are essential to avoid costly downtime and reputational damage.
Effective CI/CD pipeline security requires a multi-layered approach that considers the entire software development lifecycle. This involves incorporating security best practices at every stage, from code development to deployment. This proactive approach helps prevent malicious code from entering the pipeline and reaching production environments.
Improving Pipeline Visibility and Logging
Thorough logging and monitoring are essential for detecting anomalous activities within the CI/CD pipeline. Comprehensive logging provides insights into the pipeline’s behavior, enabling rapid identification of suspicious activities and potential attacks. Real-time monitoring of pipeline stages allows for quick detection and response to potential issues.
- Implement detailed logging at each stage of the pipeline, including timestamps, user actions, and system events. This allows for a complete audit trail, providing valuable insights into the pipeline’s operations and helping identify deviations from normal behavior.
- Utilize centralized logging systems for collecting and analyzing logs from various pipeline components. Centralized systems facilitate the search for patterns and anomalies, enabling faster identification of potential security issues.
- Configure alerts and notifications to immediately flag suspicious activities. This helps to quickly respond to threats and prevent them from escalating.
Enforcing Secure Development Practices
Implementing secure coding practices throughout the software development lifecycle is paramount. These practices help prevent vulnerabilities from being introduced in the first place, reducing the likelihood of a poisoned pipeline attack.
- Conduct regular security code reviews to identify and address potential vulnerabilities in code before it enters the pipeline. This includes examining code for common vulnerabilities like SQL injection, cross-site scripting (XSS), and insecure API usage.
- Establish and enforce coding standards that prioritize security. This involves defining specific guidelines for handling sensitive data, validating inputs, and avoiding known vulnerabilities.
- Train developers on secure coding practices and best practices. Regular training sessions can reinforce the importance of security and improve the awareness of potential vulnerabilities.
Strong Access Controls and Authorization
Strict access controls and authorization mechanisms are vital for preventing unauthorized access to the CI/CD pipeline and its resources. This restricts who can access specific pipeline stages, ensuring that only authorized personnel can make changes.
- Implement role-based access control (RBAC) to restrict access based on individual roles and responsibilities. This ensures that only necessary personnel can access sensitive components of the pipeline.
- Use strong authentication mechanisms, such as multi-factor authentication (MFA), to verify user identities and prevent unauthorized access attempts. This adds an extra layer of security to the pipeline.
- Regularly review and update access permissions to ensure that they remain aligned with the organization’s security needs and minimize unnecessary access privileges.
Automated Security Testing
Automated security testing plays a crucial role in detecting vulnerabilities and issues early in the development process. These tests can identify potential weaknesses in the code and infrastructure before they are exploited by attackers.
- Integrate automated security testing tools into the CI/CD pipeline. This allows for continuous scanning of code and infrastructure for vulnerabilities, providing early warnings.
- Implement automated vulnerability scanning tools to identify potential security issues in the codebase. Tools such as Snyk, OWASP ZAP, and others can identify vulnerabilities and provide remediation recommendations.
- Employ penetration testing tools and techniques to simulate real-world attacks and assess the pipeline’s resilience to potential threats. This proactive approach helps to identify potential weaknesses and vulnerabilities.
Case Studies and Examples
Poisoned pipeline attacks are a growing threat to CI/CD systems. Understanding real-world examples, the lessons learned, and the impact on organizations is crucial for building robust defenses. These attacks exploit vulnerabilities in the automation process, potentially leading to significant damage and costly delays.
Real-World Examples of Poisoned Pipeline Attacks
Real-world instances of poisoned pipeline attacks highlight the devastating potential of such malicious activities. These attacks often involve carefully crafted malicious code or data, subtly introduced into the pipeline’s workflow. The attackers aim to corrupt or compromise the build, test, or deployment stages, causing unexpected and harmful results.
-
A software company experienced a poisoned pipeline attack during the deployment phase. An attacker inserted malicious code into a dependency package, resulting in the deployment of a compromised version of the application. This compromised version included a backdoor, allowing unauthorized access to sensitive data. The attack went unnoticed for several weeks, causing significant damage and a breach of security.
This incident demonstrates the importance of rigorous dependency management and thorough code reviews in CI/CD pipelines.
-
Another example involves a cloud-based service provider that faced a poisoned pipeline attack during the testing phase. An attacker infiltrated the CI/CD system and injected malicious code into the test scripts. This resulted in the false reporting of successful test runs, masking vulnerabilities in the application. The attack remained undetected until a critical production deployment, causing widespread service disruptions and a loss of customer trust.
This underscores the importance of automated security testing and comprehensive vulnerability scanning in CI/CD pipelines.
-
A small startup experienced a poisoned pipeline attack during the code review process. An attacker exploited a vulnerability in the code review tool, introducing malicious code into the codebase. This code was designed to trigger a series of automated deployments that eventually led to the release of a compromised version of the product. The company suffered significant reputational damage and lost customers due to the compromised product.
This highlights the importance of robust access controls and security measures for code review tools.
Lessons Learned from Poisoned Pipeline Attacks
The attacks discussed highlight critical lessons about securing CI/CD pipelines. Understanding these lessons is essential for preventing similar incidents.
- Thorough code reviews and security testing are essential. Regular audits of code repositories, dependency checks, and security testing can help identify vulnerabilities and prevent malicious code from entering the pipeline.
- Robust access controls and authentication are critical. Restrict access to sensitive areas of the CI/CD pipeline to authorized personnel only. Implement multi-factor authentication and strong passwords to protect against unauthorized access.
- Automated security testing should be incorporated. Implement automated security testing tools to identify vulnerabilities at different stages of the pipeline, from code analysis to deployment.
Impact of Poisoned Pipeline Attacks on Organizations
The impact of poisoned pipeline attacks on organizations can be severe, affecting various aspects of the business. The consequences extend beyond immediate technical disruptions.
- Financial losses: Data breaches, service disruptions, and remediation efforts can result in significant financial losses.
- Reputational damage: A compromised product or service can damage the organization’s reputation and lead to a loss of customer trust.
- Operational disruptions: Disruptions to service or critical business operations can lead to significant operational challenges and delays.
Summary Table of Case Studies
| Case Study | Description | Impact | Lessons Learned |
|---|---|---|---|
| Example 1 | Malicious code in dependency package | Deployment of compromised application, data breach | Rigorous dependency management, code reviews |
| Example 2 | Malicious code in test scripts | False positive test results, production deployment issues | Automated security testing, vulnerability scanning |
| Example 3 | Exploitation of code review tool | Release of compromised product, reputational damage | Robust access controls, secure code review tools |
Final Conclusion
In conclusion, safeguarding CI/CD pipelines from poisoned execution requires a multifaceted approach. Implementing robust security measures, including code signing, secure repositories, and anomaly detection, is critical. Continuous monitoring, threat modeling, and incident response plans are essential for effective mitigation. This comprehensive guide equips organizations with the knowledge and strategies to protect their CI/CD pipelines and maintain the integrity of their software development lifecycle.