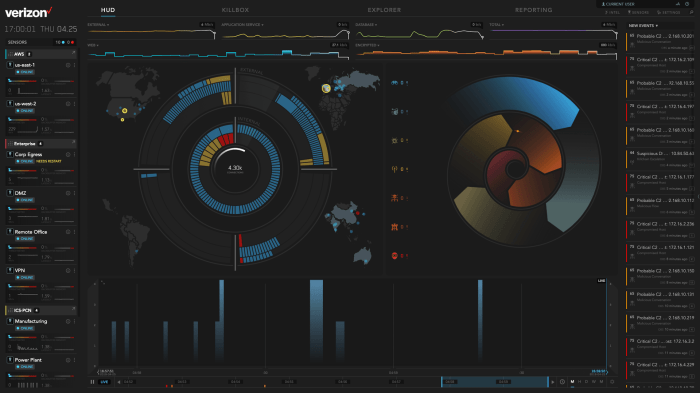
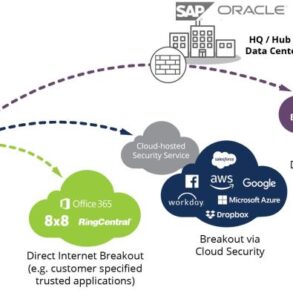
Network visibility detection and response.viewer provides a comprehensive view of your network, allowing for proactive threat detection and rapid incident response. It goes beyond basic monitoring, offering insights into potential security vulnerabilities and performance bottlenecks. This in-depth look at network traffic, combined with automated response capabilities, ensures a robust security posture and optimized network performance.
The platform empowers users with a user-friendly interface, enabling easy navigation and analysis of network data. Powerful filtering and querying tools allow for targeted investigation and identification of anomalies. Integration with SIEM systems enhances threat detection capabilities, while detailed use cases and examples showcase the practical application of network visibility in various scenarios.
Introduction to Network Visibility: Network Visibility Detection And Response.viewer
Network visibility is the ability to see and understand what’s happening within a network. In today’s complex and interconnected environments, it’s no longer a luxury, but a necessity for effective network management and security. Understanding network traffic, identifying potential threats, and optimizing performance all hinge on having a clear picture of the data flowing through the network. Without visibility, troubleshooting becomes a time-consuming guessing game, and security vulnerabilities can remain undetected, potentially leading to significant disruptions.Network visibility provides the crucial context needed to understand network activity.
This understanding is essential for responding to incidents, optimizing performance, and ensuring the security of sensitive data. Network visibility enables proactive identification and resolution of problems, minimizing downtime and maximizing productivity.
Network visibility detection and response.viewer tools are crucial for IT teams. While I’m personally glued to the upcoming Apple iPhone SE, iPad Pro event live stream blog ( apple iphone se ipad pro event time live stream blog ), understanding network performance is equally important. These tools provide a comprehensive view of network traffic, enabling swift identification and resolution of issues, ultimately keeping systems running smoothly.
Knowing what’s happening on the network is key for troubleshooting and optimizing performance.
Methods of Achieving Network Visibility
Various methods allow organizations to gain visibility into their networks. These techniques range from passive monitoring to active probing. The appropriate method depends on the specific needs and goals of the organization.
- Packet Capture: This involves intercepting and recording network traffic, providing a detailed view of every packet traversing the network. This method allows for in-depth analysis of network traffic, identifying anomalies and security threats. For example, a packet capture can reveal malicious traffic patterns, like unusual port scans or data exfiltration attempts.
- Network Monitoring Tools: Specialized software and hardware tools provide comprehensive insights into network performance, security, and usage. These tools aggregate data from various sources to create a unified view of the network. Examples include tools from SolarWinds, Nagios, and PRTG.
- Flow-based Monitoring: This approach collects aggregated data about network traffic, summarizing flows of packets rather than capturing every packet individually. This significantly reduces the data volume while still offering valuable insights into network activity. Tools like sFlow and NetFlow are commonly used for this purpose.
Benefits of Network Visibility
Having network visibility offers numerous advantages that contribute to improved network management and enhanced security.
- Improved Security: Network visibility facilitates the identification of malicious activities and vulnerabilities. Real-time analysis of network traffic allows security teams to detect anomalies, suspicious patterns, and potential threats promptly. This enables rapid response and mitigation, reducing the risk of data breaches and system compromise.
- Optimized Performance: Network visibility provides insight into bottlenecks and areas of congestion. Identifying these issues allows administrators to optimize network configuration and resource allocation, resulting in improved performance and reduced latency.
- Enhanced Troubleshooting: By providing a clear picture of network activity, visibility simplifies the process of troubleshooting network problems. Identifying the source of outages or performance degradation becomes significantly faster and more efficient.
Comparison of Network Visibility Solutions
The table below compares different network visibility solutions based on key characteristics.
| Solution | Mechanism | Data Volume | Granularity | Cost |
|---|---|---|---|---|
| SNMP | Agent-based polling | Low | Limited | Low |
| sFlow | Passive sampling | Moderate | Moderate | Moderate |
| NetFlow | Passive sampling | Moderate | Moderate | Moderate |
Detection Mechanisms
Network visibility is crucial for effective threat detection and response. Understanding how different detection mechanisms work within the context of network visibility is paramount for proactively identifying and mitigating security risks. A comprehensive approach leverages various data sources and security protocols to gain a holistic view of network activity, enabling rapid identification of anomalies and potential threats.
Network Intrusion Detection Systems (NIDS)
NIDS are vital components in network security. They continuously monitor network traffic for malicious activities and patterns. By comparing observed traffic against predefined rules and signatures, NIDS can identify intrusions and anomalies, escalating alerts to security personnel. The effectiveness of NIDS hinges on the accuracy and comprehensiveness of the rulesets used. Regular updates and proactive analysis are essential to ensure the system remains effective against evolving threats.
NIDS provide a critical first line of defense, providing early warning and aiding in incident response.
Network Intrusion Prevention Systems (NIPS)
NIPS are proactive security measures that go beyond detection. These systems not only identify malicious activity but also actively block or mitigate threats. NIPS act as a firewall, intercepting malicious packets and preventing them from reaching their target. Their effectiveness relies on real-time analysis and the ability to dynamically adjust to evolving threats. NIPS, in conjunction with NIDS, provide a robust defense mechanism.
Their role is not just reactive but also preventative, safeguarding network resources from damage.
Security Information and Event Management (SIEM) Systems
SIEM systems collect and analyze security logs from various sources across the network. This comprehensive view enables the identification of patterns, correlations, and anomalies that might indicate malicious activity. The ability of SIEM systems to correlate events from disparate sources is critical for threat detection. These systems also provide a centralized platform for security analysts to manage and respond to alerts.
By aggregating data from various sources, SIEMs offer a holistic view of security events.
Data Sources for Threat Detection, Network visibility detection and response.viewer
Multiple data sources are crucial for comprehensive threat detection. These include network traffic logs, security logs from firewalls and intrusion detection systems, system logs from servers and workstations, and even user activity logs. The more diverse the data sources, the more complete the picture of network activity becomes. Integration and analysis of data from various sources provide a comprehensive picture of potential threats.
Security Protocols for Threat Detection and Response
| Protocol | Strengths | Weaknesses |
|---|---|---|
| Snort | Open-source, highly configurable, extensive rule set. Known for its flexibility and adaptability to diverse threats. | Requires expert configuration and maintenance. False positives can be problematic. |
| Suricata | High performance, lightweight, open-source. Excellent for high-volume networks and real-time threat detection. | Requires specialized expertise for effective rule management. Performance can be affected by complex rule sets. |
| IDS/IPS Solutions (e.g., Cisco Firewalls) | Integrated with other security tools. Can provide comprehensive threat protection. Often include advanced features like anomaly detection. | Can be expensive, and the vendor’s proprietary nature limits flexibility. Rule updates may be less frequent. |
Response Strategies
Network visibility, while crucial for detecting security threats, is only half the battle. Effective incident response strategies are equally vital for mitigating the impact of vulnerabilities and minimizing potential damage. A robust response plan needs to be adaptable and well-rehearsed to effectively handle incidents and prevent future occurrences. This section delves into various response strategies, the critical role of automation, and best practices for incident response procedures.Effective incident response goes beyond simply identifying a problem; it encompasses a structured approach to contain, eradicate, and recover from a security breach.
This involves coordinating diverse teams, utilizing automated tools, and implementing proven methodologies to restore normal operations as quickly as possible. A comprehensive plan is essential for minimizing disruption, protecting sensitive data, and maintaining the integrity of the network.
Various Response Strategies
Different security incidents demand tailored responses. Strategies range from containment and eradication to recovery and post-incident analysis. Containment aims to limit the impact of the incident by isolating affected systems and data. Eradication focuses on removing the threat and restoring compromised systems to a secure state. Recovery involves restoring normal operations and data integrity.
Post-incident analysis examines the incident’s cause and identifies weaknesses in security posture to prevent future occurrences.
The Role of Automation in Incident Response
Automation significantly accelerates incident response processes. Automated tools can automatically detect anomalies, trigger alerts, and initiate containment measures. This capability is critical in today’s dynamic threat landscape, enabling rapid response to emerging threats. Automation streamlines tasks such as log analysis, threat hunting, and security information and event management (SIEM) integration.
Best Practices for Incident Response Procedures
Adherence to best practices is paramount for efficient and effective incident response. These practices include establishing a dedicated incident response team, developing clear communication protocols, and implementing a comprehensive incident response plan. This plan should detail roles and responsibilities, procedures for containment and eradication, and recovery strategies. Thorough documentation and regular training are crucial components of a successful response.
Stages of a Security Incident Response Plan
A structured incident response plan is essential for maintaining order and efficiency during a security incident. The plan should clearly define the stages involved in handling a security incident.
| Stage | Description |
|---|---|
| Preparation | Defining roles, responsibilities, and procedures. Developing a communication plan, identifying potential threats, and establishing baseline security measures. |
| Identification | Detecting and confirming a security incident. Gathering information about the incident, assessing the impact, and prioritizing actions. |
| Containment | Limiting the spread of the incident. Isolating affected systems, securing data, and preventing further damage. |
| Eradication | Removing the root cause of the incident. Recovering and restoring compromised systems, and patching vulnerabilities. |
| Recovery | Restoring normal operations. Recovering data, testing systems, and verifying the effectiveness of security controls. |
| Post-Incident Analysis | Evaluating the incident’s impact and identifying lessons learned. Improving security controls, documenting the incident, and preventing future occurrences. |
Viewer Tools and Features
Network visibility tools are crucial for effective security operations. They provide a centralized platform to monitor network traffic, identify potential threats, and facilitate rapid response. A robust viewer tool is more than just a display; it’s a powerful investigative and analytical instrument. The user interface, filtering capabilities, and comparative analysis features play a vital role in the efficiency of network security teams.Viewer tools act as the central command center for network visibility.
These tools transform raw data streams into actionable insights, allowing security personnel to quickly pinpoint anomalies, identify attackers, and remediate security incidents. This is accomplished through a combination of intuitive interfaces, sophisticated filtering options, and powerful analytical tools.
Role of Viewer Tools in Network Visibility and Response
Viewer tools play a critical role in network visibility by providing a comprehensive view of network traffic and activities. This visibility is essential for detecting anomalies and threats. By monitoring network flows, user behavior, and application usage, security teams can identify unusual patterns and potential malicious activity. These tools are pivotal in facilitating rapid response to incidents.
They enable security teams to quickly isolate and contain threats, minimizing the impact of security breaches.
Features and Functionalities of Network Visibility Viewer Tools
Network visibility viewer tools offer a wide range of features designed to enhance security operations. These tools typically include real-time monitoring of network traffic, visualization of network topology, and the ability to track user activities. Key functionalities often include:
- Real-time Network Traffic Monitoring: This allows security teams to track network activity in real-time, providing immediate insights into ongoing network flows. This includes the ability to filter and sort traffic based on various criteria, like source and destination IP addresses, ports, and protocols. This real-time visibility is vital for detecting and responding to threats as they occur.
- Network Topology Visualization: Visual representations of the network structure aid in understanding the flow of data and identifying potential bottlenecks or vulnerabilities. These visual representations can be interactive, allowing users to drill down into specific segments of the network for detailed analysis.
- User Activity Tracking: Viewer tools often track user behavior, such as access to resources, file transfers, and application usage. This allows security teams to identify suspicious activity or unauthorized access attempts. Detailed logs and activity reports are usually available.
- Threat Detection and Alerting: Sophisticated tools can analyze network traffic for known attack signatures and anomalous behavior. Automated alerts are often triggered when suspicious activity is detected, allowing for swift response and mitigation.
- Security Incident Response: Tools often provide features to support incident response activities, including isolating affected systems, gathering forensic data, and implementing remediation measures.
Importance of User-Friendly Interfaces
A user-friendly interface is paramount for efficient network visibility and response. Complex interfaces can hinder the ability of security personnel to quickly identify and address potential threats. A well-designed interface with intuitive navigation, clear visualizations, and customizable dashboards enables security teams to focus on critical issues without being bogged down by complex functionalities.
Filtering and Querying Capabilities
Powerful filtering and querying capabilities are critical for effective threat detection and incident response. These capabilities allow security teams to focus on specific aspects of network activity, isolating relevant data and quickly identifying potential threats. Filtering capabilities commonly include:
- Filtering by IP Address/Hostname: This allows for targeting specific hosts or networks for detailed analysis. This is crucial for isolating malicious actors or analyzing specific segments of the network.
- Filtering by Protocol/Port: This facilitates the analysis of traffic based on the protocols (e.g., TCP, UDP) and ports used. This is essential for identifying anomalous communication patterns.
- Filtering by Application: Identifying application-specific traffic allows for detecting unusual application behavior, potentially indicative of malicious activity. This capability can include filtering based on application names, ports, or other characteristics.
- Customizable Filtering: This allows users to create complex queries combining multiple criteria, focusing the analysis on specific events or characteristics.
Comparison of Viewer Tools
A comprehensive comparison of viewer tools is challenging due to the variety of tools and features. However, a table outlining some key factors can provide a comparative overview.
| Tool | Features | Pricing | User Reviews |
|---|---|---|---|
| Tool A | Real-time monitoring, advanced filtering, detailed reporting | Enterprise-level pricing | High ratings for performance and ease of use |
| Tool B | Basic monitoring, limited filtering, simple reporting | Affordable pricing | Mixed reviews; some users found it lacking in advanced features |
| Tool C | Cloud-based, comprehensive features, robust reporting | Subscription-based pricing | High user satisfaction with cloud integration and scalability |
Note: This is a simplified comparison; pricing, features, and user reviews can vary significantly depending on specific implementations and use cases.
Integration with Security Information and Event Management (SIEM) Systems
Seamless integration with Security Information and Event Management (SIEM) systems is crucial for modern security operations. Network visibility tools provide a wealth of data about network traffic, user activity, and device behavior. Combining this data with SIEM capabilities allows for a more comprehensive understanding of potential threats and a faster response time. This integration enhances threat detection by correlating network events with security logs from other sources, leading to a more accurate picture of the security posture.Integrating network visibility data into a SIEM platform empowers security analysts to quickly identify anomalies and suspicious activities.
By combining network flow data with user and endpoint logs, security teams can build a more holistic view of the attack surface, enabling faster incident response and improved threat hunting capabilities. This allows for a proactive approach to security, enabling swift identification and mitigation of threats before they escalate into major incidents.
Network visibility detection and response.viewer tools are super helpful for security teams. They’re like a detective’s magnifying glass, letting them see everything happening on their network. But, sometimes, even with the best tools, things can get a little confusing, like trying to figure out who’s behind all the phone calls and messages in a show like “Pretty Little Liars” pretty little liars all the phones.
Thankfully, these viewers help clarify exactly what’s going on and who’s involved in the communication, providing a clear picture of the network activity for better incident response.
Importance of SIEM Integration
Integrating network visibility data with SIEM systems provides a significant advantage in threat detection and response. This integration allows security analysts to correlate network events with other security logs, producing a more accurate and comprehensive understanding of security incidents. The combined data helps identify patterns and anomalies that might be missed with either system alone. By combining network traffic data with user and device logs, security teams can gain a more complete picture of the attack surface and improve their ability to respond to threats effectively.
Technical Aspects of Integration
The technical aspects of integrating network visibility data with SIEM systems often involve standardized data formats and APIs. Network visibility tools typically export data in formats like JSON, XML, or CSV. SIEM systems need to be configured to accept these formats and integrate the data with existing logs. A crucial aspect is ensuring that the data feeds are reliable and have low latency, as timely data is essential for proactive threat detection.
Data normalization is another key technical challenge, as the format and structure of data from different sources can vary. This requires standardization processes and automated tools for transforming and enriching data to make it consistent with the SIEM platform. Proper configuration and testing of the integration are vital to ensure data integrity and prevent any issues with the flow of data.
Data Formats for Integration
- JSON (JavaScript Object Notation): JSON is a lightweight data-interchange format that is widely used for exchanging data between systems. It’s easily parsed and understood by both network visibility tools and SIEM systems, offering a common language for data exchange. JSON data often contains structured information, like timestamps, IP addresses, ports, and user IDs, enabling detailed analysis.
- XML (Extensible Markup Language): XML is another popular data format for structured data exchange. It’s a more verbose format than JSON but offers more flexibility in defining custom data elements, which can be beneficial for specific use cases. XML is often used when complex data structures are required.
- CSV (Comma-Separated Values): CSV is a simple text-based format suitable for basic data exchange. It’s often used for exporting data from network visibility tools for manual analysis or further processing. However, for real-time SIEM integration, CSV might not be the most efficient format due to its lack of structure.
| Data Format | Description | Suitability for SIEM Integration |
|---|---|---|
| JSON | Lightweight, human-readable format | Excellent; widely supported and easily parsed |
| XML | Flexible, structured format | Good; allows for complex data structures |
| CSV | Simple, text-based format | Limited; not ideal for real-time integration |
Use Cases and Examples
Network visibility isn’t just a theoretical concept; it’s a powerful tool with tangible benefits for organizations of all sizes. Understanding the flow of data within your network, identifying potential threats, and optimizing performance are crucial for success in today’s digital landscape. This section dives into practical applications of network visibility across various scenarios.
DDoS Attack Detection and Response
Network visibility tools provide crucial insights into network traffic patterns, allowing for the rapid identification of anomalous activities that could indicate a DDoS attack. By monitoring network traffic volume, source IP addresses, and packet types, these tools can detect unusual spikes and identify the origins of the attack. Real-time data analysis enables swift response mechanisms, such as traffic filtering or routing changes, minimizing the impact on legitimate users.
Network Performance Optimization
Network visibility tools provide granular data on network traffic flows, enabling IT teams to pinpoint bottlenecks and optimize network performance. Analyzing bandwidth consumption by application or user group allows for targeted adjustments, such as upgrading network infrastructure or implementing traffic shaping policies. This proactive approach to network management reduces latency, improves application responsiveness, and enhances user experience.
Compliance and Auditing Procedures
Network visibility plays a critical role in ensuring compliance with industry regulations and internal policies. Detailed logs and reports generated by these tools provide a comprehensive audit trail of network activity, facilitating regulatory compliance. By tracking user access, data transfers, and network configurations, organizations can demonstrate adherence to security policies and industry standards. This is crucial for preventing potential penalties and maintaining a positive reputation.
Specific Network Visibility Scenarios
- Identifying bandwidth hogs: Network visibility tools can identify users or applications consuming excessive bandwidth. This allows IT administrators to take action to address the issue, whether it’s a software glitch, a user error, or a malicious actor. A network administrator might discover a particular user streaming high-definition video for extended periods during work hours, consuming a significant portion of the available bandwidth.
This information helps in proactively adjusting bandwidth allocation and preventing service degradation for other users.
- Detecting unauthorized access: Network visibility solutions monitor network traffic for unusual patterns and suspicious activities. These tools can detect unauthorized access attempts, identify the source of the attempts, and initiate security alerts. For example, a network visibility tool might detect a series of failed login attempts from a specific IP address, which could indicate a brute-force attack or a malicious actor trying to compromise the system.
- Troubleshooting network connectivity issues: By visualizing network traffic, network visibility tools pinpoint the source of network connectivity problems. This granular view of network communication allows administrators to identify bottlenecks, configuration errors, or device malfunctions that are causing disruptions. For example, a network visibility tool might detect a significant drop in throughput between two specific servers, enabling an administrator to diagnose the issue quickly and effectively.
Challenges and Considerations
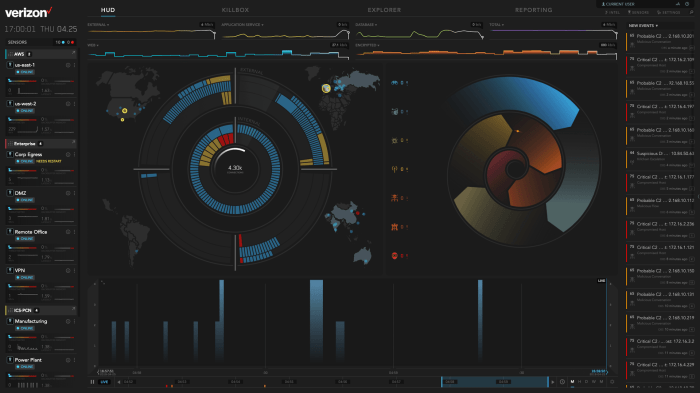
Network visibility and response solutions, while powerful, come with inherent challenges. Implementing these systems effectively requires careful consideration of various factors, from scalability and performance to data management and security. Understanding these hurdles is crucial for organizations seeking to leverage the full potential of these solutions without encountering unexpected obstacles.
Scalability and Performance
Network visibility tools need to handle massive amounts of data generated by modern networks. Solutions must scale effectively to accommodate growth in network traffic and the addition of new devices without compromising performance. Poorly designed systems can lead to slow response times, data loss, and ultimately, a failure to detect critical security events. A key consideration is the ability to adapt to changes in network architecture and topology, ensuring consistent performance and data collection across diverse environments.
For instance, a system designed for a small office network might struggle to maintain visibility and responsiveness in a large enterprise environment with complex, multi-layered networks.
Data Management and Analysis
The sheer volume of data collected by network visibility tools presents a significant challenge. Effective data management strategies are critical for storing, processing, and analyzing the information to extract actionable insights. Sophisticated tools for data normalization, correlation, and visualization are essential to identify patterns, anomalies, and potential threats. Without robust data management, the collected information becomes a mere data dump, lacking the value needed for effective threat detection and response.
Poorly structured data or lack of clear analysis protocols can result in false positives and missed genuine security events.
Network visibility detection and response.viewer tools are crucial for understanding and reacting to potential threats. Thinking about how a music identification app like Shazam’s iMessage integration on iOS leverages network data for its core functionality, it becomes clear that similar systems are key to modern security solutions. Ultimately, effective network visibility detection and response.viewer tools are essential to safeguard our interconnected digital world.
Security Considerations
Implementing network visibility solutions introduces security risks. Data breaches, especially if the solution itself is compromised, can expose sensitive information. Ensuring the security of the visibility platform itself is paramount, requiring robust authentication, authorization, and encryption measures. Data collected from the network should be handled with the same care as any other sensitive information. This includes implementing access controls and logging to monitor access attempts and potential unauthorized activities.
Solutions should also be regularly audited and updated to mitigate vulnerabilities and address security threats.
Common Pitfalls and Solutions
| Pitfall | Solution |
|---|---|
| Insufficient Visibility: Inability to see all relevant network traffic, leading to blind spots in security monitoring. | Comprehensive Network Coverage: Implement sensors strategically throughout the network to capture all relevant traffic types and data points. Employ a variety of collection methods (e.g., SPAN ports, TAPs, network packet capture) to capture comprehensive data from different points of the network. |
| Lack of Threat Correlation: Difficulty in connecting seemingly unrelated events to form a complete picture of an attack. | Advanced Correlation Engines: Invest in SIEM (Security Information and Event Management) systems with robust correlation capabilities. Develop custom rules and scripts to identify and analyze patterns specific to the organization’s threat landscape. |
| Poor Data Management: Difficulty in storing, processing, and analyzing the vast amounts of data collected. | Scalable Storage Solutions: Choose storage systems with high capacity and performance to handle growing data volumes. Implement data normalization and cleansing procedures to improve data quality and consistency. Develop a clear data retention policy. |
| Inadequate Security Measures: Vulnerability of the visibility solution itself, potentially exposing sensitive information. | Robust Security Architecture: Implement strong authentication and authorization mechanisms, regular security audits, and security updates for the visibility solution. Follow industry best practices for security configurations and threat modeling. Segment network traffic and the visibility platform itself from sensitive resources. |
Future Trends
The landscape of network visibility and response is rapidly evolving, driven by technological advancements and increasing security threats. Staying ahead of these changes is crucial for organizations to maintain a robust defense posture. This section explores emerging trends, the impact of AI/ML, the future of tools, and the evolving cloud visibility landscape.
Emerging Trends in Network Visibility and Response
The field is experiencing a convergence of technologies, creating a more integrated and sophisticated approach to security. Automation is becoming increasingly prevalent, allowing for quicker detection and response to threats. This automation is fueled by the rise of orchestration and automation platforms, enabling security teams to streamline their workflows. The focus is shifting from reactive measures to proactive threat hunting and vulnerability management.
Impact of Artificial Intelligence and Machine Learning on Network Visibility
AI and machine learning (ML) are revolutionizing network visibility by enabling automated threat detection and analysis. These technologies can sift through vast amounts of network data, identifying patterns and anomalies that might be missed by traditional methods. For example, AI algorithms can learn to distinguish between legitimate user activity and suspicious behavior, significantly improving threat detection accuracy. This allows security teams to focus on more complex, high-value threats, rather than getting bogged down in routine alerts.
Furthermore, ML models can adapt and improve their performance over time, learning from new data and refining their detection capabilities.
Future of Network Visibility Tools
Network visibility tools are evolving to become more intuitive and user-friendly, enabling easier threat detection and response. The trend is towards integrated platforms that combine various security functions, providing a holistic view of the network. These tools will likely incorporate advanced visualization capabilities to present complex data in easily understandable formats. Real-time dashboards and interactive visualizations are becoming increasingly important, providing immediate insights into network activity and potential threats.
Tools are also adapting to support hybrid and multi-cloud environments, handling the complexity of diverse network architectures.
Cloud-Based Network Visibility Evolution
Cloud-based network visibility is evolving rapidly, becoming more sophisticated and capable of handling the unique challenges of cloud environments. Tools are increasingly focused on providing visibility into virtual machines, containers, and microservices, allowing for more granular threat detection and response. Cloud-specific security analytics are being incorporated to help organizations better understand and respond to cloud-native threats. The ability to monitor and manage security policies across multiple cloud providers is a key feature.
Cloud-based tools also need to adapt to the dynamic and ever-changing nature of cloud deployments.
Projections on Future Developments in Network Visibility
Future developments in network visibility will likely involve greater automation, integration, and sophistication. Predictive analytics and threat intelligence will become more critical, allowing organizations to anticipate and mitigate potential threats before they cause damage. Expect to see an increase in the use of zero-trust architectures, with greater emphasis on micro-segmentation and access controls. There will be an increased need for skilled security professionals capable of leveraging these advanced technologies.
The combination of AI/ML, cloud-native security, and zero-trust models will define the future of network visibility.
Conclusion
In conclusion, network visibility detection and response.viewer offers a robust solution for modern network environments. By providing a comprehensive overview of network activity, coupled with advanced detection mechanisms and automated response strategies, it ensures a secure and high-performing network. The future of network visibility looks promising, with ongoing developments in AI, cloud-based solutions, and improved integration with existing security systems.