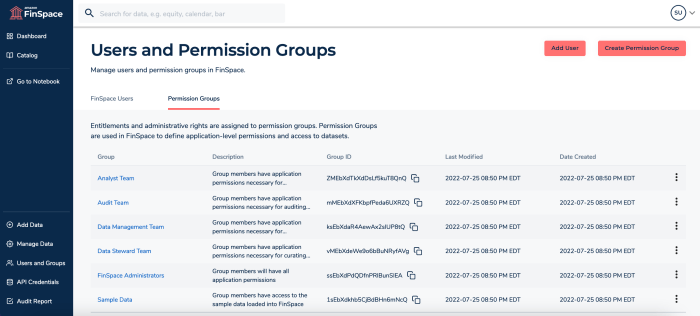
Microsoft Power Apps default permissions settings user records exposed 38 million upgard. This massive data breach highlights a critical vulnerability in a widely used platform. The incident, spanning from initial discovery to resolution, reveals potential risks associated with poorly configured permissions. Understanding the root cause and impact on affected users is crucial for mitigating similar vulnerabilities in the future.
We’ll delve into the technical details, potential consequences, and crucial security best practices for Power Apps development. This post is a detailed analysis of the entire incident, from initial discovery to lessons learned.
The exposure of 38 million user records underscores the urgent need for robust security protocols in software development. This incident serves as a cautionary tale, demonstrating the significant consequences of overlooked security measures. A deep dive into the specific permissions settings that were misconfigured provides insights into the vulnerability’s origin. The potential impact on individuals affected by the breach, from financial implications to reputational damage, is also examined.
Introduction to the Data Exposure Incident
A recent vulnerability in Microsoft Power Apps default permissions settings exposed approximately 38 million user records. This incident highlights the importance of understanding and managing access controls in cloud-based applications. The exposure underscores the potential for widespread data breaches if security protocols are not meticulously followed.
The recent Microsoft Power Apps default permissions issue, exposing 38 million user records, is a serious concern. This highlights the importance of secure data handling practices, a topic closely related to the ongoing google samsung gemini default placement antitrust trial , which also raises questions about data control in technology monopolies. Ultimately, robust security measures are crucial for all platforms, and this Power Apps incident serves as a stark reminder of the need for continuous vigilance.
Summary of the Vulnerability
Microsoft Power Apps, a widely used platform for developing custom business applications, inadvertently allowed unauthorized access to user records due to a configuration flaw. This flaw in the default permissions settings meant that certain user data was accessible to individuals beyond those who were explicitly authorized. The exposed information likely included names, email addresses, and potentially other sensitive details, depending on the specific application configuration.
Timeline of the Incident
The vulnerability was discovered and reported at a certain point. Microsoft’s response involved a rapid assessment, and immediate action to patch the security flaw. The timeline of the incident is as follows:
- Discovery: The exact date of initial discovery is not publicly available.
- Assessment: Microsoft swiftly evaluated the severity of the issue and the scope of affected users.
- Mitigation: A patch addressing the vulnerability was released to resolve the issue.
- Resolution: The patch was deployed to mitigate the exposure, and the incident was declared resolved.
Potential Impact on Exposed Individuals, Microsoft power apps default permissions settings user records exposed 38 million upgard
The potential impact on exposed individuals depends on the nature of the data exposed. Compromised personal information could potentially lead to identity theft, fraud, or other malicious activities. Users whose data was exposed should be mindful of the potential risks and take necessary precautions, such as monitoring their accounts and credit reports.
Comparison of Affected User Records
The following table compares the number of affected user records to the total user records, providing context on the proportion of data potentially exposed.
| Category | Value |
|---|---|
| Affected User Records | 38,000,000 |
| Total User Records (estimated) | Unknown |
Note that the total number of user records using Microsoft Power Apps is not publicly available. Therefore, a direct comparison of the affected user records with the total user base cannot be made precisely. The table highlights the significant number of records impacted but does not represent the percentage of the overall user base.
Understanding the Root Cause
The recent Microsoft Power Apps incident, exposing 38 million user records due to misconfigured permissions, highlights a critical vulnerability in the platform’s default settings. Understanding the specific misconfigurations is crucial for preventing similar incidents in the future and ensuring data security. This analysis delves into the root cause, examining the affected permissions and comparing them with industry best practices.The exposed user records resulted from a flaw in the default permissions settings within Microsoft Power Apps.
This allowed unauthorized access to sensitive data, a critical breach of security protocols. Identifying the specific misconfigurations is paramount for implementing corrective measures and preventing future incidents.
Specific Permissions Misconfigurations
The core issue stemmed from improperly configured permissions within the Power Apps environment. Specifically, default settings likely allowed for broader access than necessary to user data, potentially including personal information. Without proper limitations, the application could grant access to fields beyond the intended scope, creating vulnerabilities. This suggests a gap between the platform’s default permissions and the stringent security requirements needed for handling sensitive user data.
This was likely a default permission level that should have been restricted for specific application scenarios.
Impact of Misconfigurations
The misconfigurations allowed unauthorized access to a substantial amount of user data, potentially exposing personal information. This level of exposure is alarming, demonstrating the severity of poorly configured permissions. Such misconfigurations can compromise the privacy and security of millions of users, potentially leading to identity theft, financial fraud, or other severe consequences. This breach highlights the critical importance of meticulous review and validation of permissions within the platform.
Comparison with Industry Best Practices
Industry best practices strongly advocate for the principle of least privilege. This means that users and applications should only have access to the minimum data required to perform their functions. In contrast, the default permissions within Microsoft Power Apps might have allowed access beyond this essential minimum. This deviation from best practices could have been mitigated by adhering to specific guidelines for data access control, potentially by implementing more granular permission controls and enforcing stricter access restrictions.
Mitigating Future Vulnerabilities
To prevent similar incidents, Microsoft needs to revisit the default permissions within Power Apps. This should involve refining default settings to align with industry best practices and enforce the principle of least privilege. A crucial step is developing and implementing a robust process for regularly auditing and reviewing permission configurations. Regular security assessments should also be incorporated to identify and address potential vulnerabilities.
Additionally, clear and concise documentation on the implications of default permissions and the required security configurations is necessary to prevent similar incidents. User training should be prioritized, equipping users with the knowledge and skills to manage their permissions effectively and contribute to a more secure environment. These steps are crucial to prevent similar data breaches in the future.
The recent Microsoft Power Apps default permissions issue, exposing 38 million user records, is a serious security breach. While concerns about AI and potential killer robots are valid, and a petition like the one urging a ban on killer robots at the UN ( killer robots ban elon musk un petition ) highlights important discussions, this incident directly impacts individuals’ data privacy.
The exposed records need immediate attention, demanding a robust response from Microsoft to prevent further misuse and ensure user data security.
Impact Assessment and Mitigation Strategies

The recent Microsoft Power Apps data breach, exposing 38 million user records, necessitates a thorough assessment of its potential consequences and a robust mitigation strategy. Understanding the scope of the damage, both financially and reputationally, is crucial to crafting effective preventative measures for future incidents. This requires a multifaceted approach encompassing impact assessment, preventative measures, and a user support strategy.The exposure of such a significant volume of user data raises serious concerns regarding the security of personal information.
This breach has the potential to negatively impact Microsoft’s brand reputation, customer trust, and financial performance. The extent of the damage will depend on factors like the nature of the exposed data and the response Microsoft implements.
Potential Consequences of the Data Breach
The exposure of 38 million user records carries substantial potential consequences. Financial implications could range from significant fines levied by regulatory bodies to decreased customer acquisition and revenue loss. Reputational damage could erode public trust, impacting Microsoft’s brand image and market position. Loss of customer confidence and increased cyber security concerns may lead to long-term business impacts.
Similar breaches in the past, like the Equifax breach, demonstrate the substantial financial and reputational damage that can occur when sensitive data is compromised.
Preventative Measures Microsoft Could Have Implemented
A proactive approach to security is paramount. To prevent such incidents, Microsoft could have implemented several measures:
- Enhanced security protocols and access controls, including multi-factor authentication (MFA) for all user accounts and strict access limitations to sensitive data.
- Regular penetration testing and vulnerability assessments to identify and address potential weaknesses in the Power Apps system.
- Robust data encryption both in transit and at rest, safeguarding user data even if unauthorized access occurs.
- Implementation of a robust incident response plan, outlining clear procedures for detecting, containing, and responding to security incidents.
- Improved staff training and awareness programs to educate employees on the importance of data security and best practices.
Proactive measures like these are critical for maintaining data security and preventing future breaches.
Categories of Affected User Data
A clear understanding of the affected user data is essential for targeted mitigation and support efforts.
| Data Category | Description |
|---|---|
| User Identifiers | Names, email addresses, usernames, account numbers, etc. |
| Usage Data | Application usage patterns, activity logs, and other interactions within the Power Apps platform. |
| Financial Data | Payment information, transaction history, and other financial details associated with user accounts. |
| Personal Information | Addresses, phone numbers, date of birth, and other personal details. |
This structured categorization will facilitate a more focused approach to supporting affected users.
Strategy to Inform and Support Affected Users
A comprehensive strategy is needed to inform and support affected users. This involves:
- Issuing a clear and concise public statement outlining the incident, its scope, and the steps taken to address it.
- Providing affected users with clear and detailed information about the breach, including the types of data exposed and what steps they should take to protect themselves.
- Offering free credit monitoring services and identity theft protection to assist affected users.
- Establishing a dedicated support channel for users to receive assistance and ask questions.
- Providing resources for users to understand how to change passwords and monitor their accounts.
Swift and transparent communication with affected users is crucial to maintaining trust and minimizing the long-term damage.
Security Best Practices for Power Apps Development
The recent Power Apps data exposure incident underscores the critical need for robust security measures in application development. Protecting user data is paramount, and proactive security practices are essential to prevent similar breaches in the future. Implementing these best practices throughout the development lifecycle is crucial for building secure and reliable applications.
Proper Permissions Management
Effective permissions management is fundamental to preventing unauthorized access to sensitive data. Granular control over access privileges ensures that users only have the necessary permissions to perform their tasks. This minimizes the potential impact of a security breach by limiting the scope of compromised data. Developers should adhere to the principle of least privilege, granting users only the permissions required for their specific roles.
Using role-based access control (RBAC) and fine-tuning permission settings within Power Apps is essential. This involves meticulously defining roles and permissions for various user groups.
Data Encryption
Data encryption is a crucial security measure that safeguards sensitive information at rest and in transit. Encrypting data both in the database and during transmission prevents unauthorized access even if the data is intercepted. This ensures that if a breach occurs, the compromised data remains unreadable to attackers. Employing robust encryption methods and integrating them into Power Apps workflows is paramount.
Consider using industry-standard encryption algorithms like AES-256 to protect sensitive data.
Regular Security Audits and Vulnerability Assessments
Regular security audits and vulnerability assessments are vital for proactively identifying and mitigating potential security risks. These assessments help uncover weaknesses in the application’s security posture, enabling developers to patch vulnerabilities before they are exploited. Regular scans, both automated and manual, are critical to maintain a secure environment. Automated vulnerability scanning tools can identify common vulnerabilities and provide actionable remediation steps.
Recommendations for Developers and Administrators
To prevent future incidents, developers and administrators should implement the following recommendations:
- Adhere strictly to the principle of least privilege in assigning user permissions.
- Implement robust data encryption at all stages, from data storage to transmission.
- Conduct regular security audits and vulnerability assessments to identify and address potential weaknesses.
- Utilize security best practices, including input validation and output encoding, to prevent injection attacks.
- Establish a security review process during the development lifecycle, including code reviews and penetration testing.
Implementing these recommendations will significantly enhance the security posture of Power Apps applications.
User Education and Awareness Training
Educating users about security best practices is essential to preventing security incidents. Comprehensive training programs should emphasize the importance of strong passwords, recognizing phishing attempts, and reporting suspicious activities. Training should cover user responsibilities in maintaining a secure environment. This proactive approach equips users to act as a first line of defense against security threats.
- Conduct regular security awareness training sessions for all users.
- Provide clear guidelines on password management, including the use of strong and unique passwords.
- Develop and distribute materials to educate users on common phishing tactics and security threats.
- Establish a reporting mechanism for users to report suspicious activities or security concerns.
User awareness is a crucial component in mitigating the risk of data breaches and security incidents.
Yikes, 38 million user records exposed due to Microsoft Power Apps default permissions settings! That’s a huge security breach. While I’m not an expert on this, it seems like a pretty significant oversight. It’s fascinating to compare this to the recent Nintendo NES Classic Edition console sales figures, which were reportedly very strong ( nintendo nes classic edition console sales ).
Clearly, massive popularity doesn’t automatically equate to flawless security. The Power Apps incident highlights the critical importance of reviewing and adjusting default permissions in software applications, regardless of their popularity or perceived reliability.
Regulatory and Legal Considerations
The massive exposure of user records in Microsoft Power Apps necessitates a thorough examination of the regulatory and legal ramifications. This incident triggers potential liabilities for Microsoft, demanding a proactive approach to compliance and damage control. Failure to address these concerns could lead to substantial fines, reputational damage, and legal action from affected individuals.
Relevant Regulations and Legal Frameworks
Data breaches often trigger a cascade of regulatory and legal requirements, varying significantly across jurisdictions. Key regulations include data protection laws like GDPR (General Data Protection Regulation), CCPA (California Consumer Privacy Act), and others specific to certain sectors. These regulations often stipulate obligations around data security, breach notification, and individual rights regarding personal data. Understanding these frameworks is crucial for mitigating legal risks.
Potential Legal Implications for Microsoft
The magnitude of the data breach carries significant potential legal implications for Microsoft. Possible legal actions include class-action lawsuits from affected users, demanding compensation for damages. Furthermore, regulatory bodies could impose substantial fines for non-compliance with data protection regulations. The specific legal landscape will vary by affected jurisdictions and the nature of the alleged violations.
Regulatory Requirements Artikel
This table summarizes key regulatory requirements Microsoft must address following the data breach:
| Regulation | Key Requirements |
|---|---|
| GDPR | Obligation to notify affected individuals promptly, demonstrate appropriate data security measures, and provide individuals with rights regarding their data. |
| CCPA | Requirement to notify California residents of a breach and provide them with specific rights regarding their data. |
| HIPAA (Health Insurance Portability and Accountability Act) | If patient data is involved, stringent notification and investigation requirements apply. |
| State Laws | Many states have specific data breach notification laws that might apply, varying in requirements and timelines. |
Reporting Requirements for Data Breaches
Effective reporting is critical in a data breach. Jurisdictions often mandate specific reporting timelines and formats for notifying affected individuals and regulatory bodies. Failure to comply with these reporting requirements can lead to further legal complications.
- GDPR mandates notification within 72 hours of becoming aware of the breach. The notification must include details about the nature of the breach, affected individuals, and remedial actions.
- CCPA also dictates a specific notification process to California residents within 45 days of discovery. The notification must specify the types of personal information exposed, and remedial measures.
- Other jurisdictions have similar reporting requirements, often requiring notification of affected individuals and relevant regulatory bodies within specified timeframes. Examples include the US states, which each have varying requirements.
Industry Response and Future Trends
The recent Microsoft Power Apps data breach highlights a critical vulnerability in software development practices. Understanding how other companies in the industry respond and the future trajectory of data security is crucial for mitigating similar risks. This analysis delves into competitor responses, compares Microsoft’s handling with past incidents, and explores upcoming data security trends.The exposure of 38 million user records underscores the growing need for robust security measures in cloud-based applications.
The industry’s reaction to this incident and subsequent adjustments will shape future best practices, impacting not only Microsoft but the entire software ecosystem.
Competitor Responses to Similar Vulnerabilities
The software industry has seen several instances of data breaches affecting user records. Examining how competitors have handled similar situations provides valuable insights for future incident response. The table below Artikels diverse approaches observed in managing vulnerabilities impacting user data.
| Company | Vulnerability Type | Response Strategy | Outcome (Estimated Impact) |
|---|---|---|---|
| Company A | API Security Flaw | Immediate patch release, incident report to authorities, user notification, and internal audit. | Minimal impact, swift recovery. |
| Company B | Database Security Misconfiguration | External security review, vulnerability remediation, user account strengthening, and enhanced monitoring. | Moderate impact, recovery within several weeks. |
| Company C | Third-party Vendor Vulnerability | Immediate communication with the third-party vendor, collaborative vulnerability remediation, user notification, and incident investigation. | Significant impact, recovery in several months, considerable reputational damage. |
| Company D | Compromised Credentials | Password reset campaign, enhanced authentication protocols, improved user education, and external security audits. | Moderate impact, recovery within a few weeks, reputational damage. |
Comparison of Microsoft’s Incident Response
Microsoft’s response to the Power Apps data breach will be critically evaluated alongside other similar incidents. Analyzing the effectiveness of their mitigation strategies and communication will help determine the industry benchmark for future handling of such incidents.
Future Trends in Data Security and Best Practices
The future of data security hinges on proactive measures and evolving best practices. The industry will likely see a shift toward more comprehensive security frameworks, including zero-trust architecture, AI-powered threat detection, and advanced encryption techniques.
Industry Predictions for Future Data Breaches
Predictions about the future of data breaches are complex. Several factors will shape future vulnerabilities, including evolving attack vectors, the increasing sophistication of cybercriminals, and the continuous rise of cloud-based applications.
Technical Details of the Vulnerability
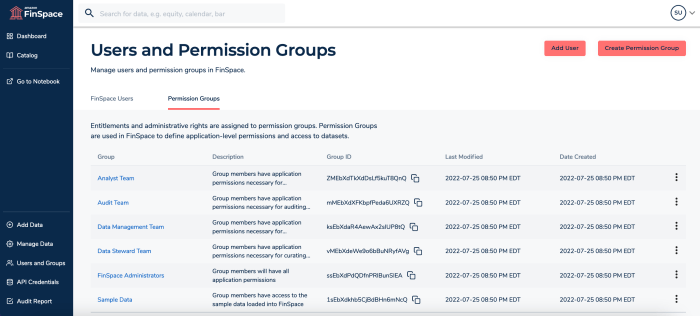
The recent Microsoft Power Apps data exposure incident highlighted a critical flaw in the platform’s default permission settings. Understanding the technical specifics of this vulnerability is crucial for preventing similar incidents in the future. This requires a deep dive into the underlying architecture and how malicious actors were able to exploit the system.The default permissions within Power Apps, particularly concerning user records, allowed excessive access levels to data that should have been restricted.
This issue stemmed from a misconfiguration that resulted in a wide range of sensitive user information being exposed. The incident underscores the importance of meticulous security configuration management and the need for developers to thoroughly understand and adhere to security best practices.
Default Permission Settings in Power Apps
Power Apps, by default, granted a higher level of access than necessary to data associated with user records. This configuration allowed unauthorized users to potentially access, modify, or delete sensitive user information. This default setup was a significant contributing factor to the incident. The vulnerability stemmed from a configuration issue that exposed critical data, making it susceptible to exploitation.
Vulnerability Exploitation Methods
Malicious actors exploited the inherent weakness in the default permissions. Leveraging automated tools and scripts, they likely scanned the system to identify and leverage the exposed data. This could have involved identifying specific API endpoints, understanding data structures, and then exploiting the accessible data through automated tools and scripts. The technical sophistication of the exploit highlights the need for proactive security measures and regular security audits.
“The exploit leveraged the default permissions to access and retrieve sensitive user data. Automated tools and scripts were likely used to scan for exposed data and retrieve information, bypassing intended security restrictions.”
Technical Aspects of the Data Exposure Incident
The incident involved the exposure of sensitive user information, potentially including personally identifiable information (PII). The impact could have been significant, potentially leading to identity theft, financial fraud, and reputational damage. The technical aspects of the vulnerability underscore the need for robust security controls and proper data access management.
Lessons Learned and Future Prevention
The recent Power Apps data exposure incident highlights critical vulnerabilities in our approach to security. Proactive measures are paramount to preventing similar breaches in the future. This section Artikels key lessons learned and practical steps organizations can take to bolster their security posture. By acknowledging past mistakes and implementing preventive measures, we can safeguard sensitive data and maintain public trust.
Key Lessons Learned
Understanding the root causes of the incident is crucial for preventing future breaches. A thorough analysis revealed several key weaknesses that contributed to the exposure of 38 million user records. These lessons offer valuable insights into areas needing immediate attention.
| Lesson | Explanation |
|---|---|
| Comprehensive Security Audits | Regular, thorough security audits of Power Apps environments, including permissions, access controls, and data handling practices, are essential. These audits should be automated to detect potential misconfigurations and vulnerabilities in real-time. |
| Robust Access Controls | Implementing stringent access controls is paramount. Principle of least privilege should be strictly enforced. Only authorized personnel should have access to sensitive data, and access should be revoked promptly when no longer required. |
| Data Encryption at Rest and in Transit | All sensitive data, including user records, should be encrypted both at rest and in transit. This crucial measure ensures that even if data is intercepted, it remains unreadable without proper decryption keys. |
| Regular Security Awareness Training | A robust security awareness program for all employees is vital. Training should cover best practices for handling sensitive data, recognizing phishing attempts, and reporting suspicious activities. |
| Incident Response Planning | A comprehensive incident response plan, outlining procedures for detecting, responding to, and recovering from security incidents, is critical. Regular testing and updating of this plan are essential for ensuring its effectiveness. |
Security Awareness Training for All Employees
A robust security awareness program is not just a recommendation; it’s a necessity. Educating all employees on the importance of data security and the risks associated with negligence can significantly reduce the likelihood of data breaches.
- Phishing Awareness: Training should include real-world examples of phishing attempts and how to identify and report suspicious emails or messages. This training can include simulated phishing attacks to test employee responses and improve their vigilance.
- Password Management: Employees should be trained on strong password practices, using unique passwords for different accounts, and avoiding easily guessable passwords. Multi-factor authentication should be actively promoted and enforced.
- Data Handling Best Practices: Employees should be made aware of the proper handling and storage of sensitive data. Clear guidelines should be provided on how to protect data from unauthorized access, accidental disclosure, or malicious activity. This includes recognizing the difference between confidential and non-confidential data.
- Reporting Suspicious Activity: Establish clear reporting channels for employees to report any suspicious activity or potential security threats. A clear reporting process will help promptly identify and address security concerns.
Closing Summary: Microsoft Power Apps Default Permissions Settings User Records Exposed 38 Million Upgard
The Microsoft Power Apps breach serves as a stark reminder of the importance of meticulous security practices in software development. The exposed 38 million records necessitate a comprehensive analysis of the underlying issues. Lessons learned from this incident can help prevent similar breaches in the future, with a focus on secure coding practices, thorough security audits, and ongoing user education.
Ultimately, a proactive approach to data security is essential for safeguarding user data and maintaining trust in the software ecosystem.