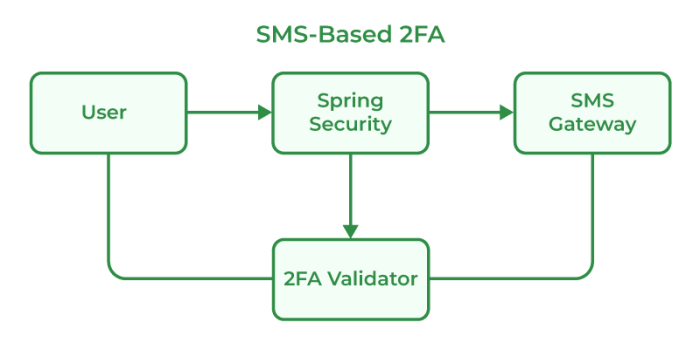
Its time stop using services force you use sms based two factor authentication – It’s time to stop using services that force you to use SMS-based two-factor authentication. SMS-based 2FA, while seemingly convenient, is surprisingly vulnerable to attacks like SIM swapping and phishing. This article dives deep into the security risks of relying on SMS for authentication, explores more secure alternatives, and provides a practical guide to switching to them.
Traditional SMS-based two-factor authentication, despite its ease of use, often falls short in terms of security. This article will explore why this is the case and offer alternative methods that provide better protection without sacrificing convenience. We’ll also look at practical steps for switching and address common concerns along the way.
Introduction to SMS-based 2FA: Its Time Stop Using Services Force You Use Sms Based Two Factor Authentication
SMS-based two-factor authentication (2FA) is a widely used security measure to enhance account protection. It adds an extra layer of verification beyond a username and password, making it significantly harder for unauthorized individuals to access accounts. This method relies on sending a one-time code via text message to a user’s phone.The process typically involves a user logging in with their username and password.
The system then sends a unique, time-sensitive code to the user’s registered mobile phone number. The user enters this code into the system to complete the authentication process. This code is usually valid for a short period, further bolstering security.
Security Risks of SMS-based 2FA
SMS-based 2FA, while convenient, presents several security vulnerabilities. A significant risk is the potential for SIM swap attacks. Malicious actors can gain access to a user’s phone number by convincing the mobile provider to swap the SIM card. Once the SIM card is replaced, the attacker gains access to the verification codes, thereby compromising the account. Phishing attacks targeting SMS messages also pose a serious threat.
Malicious actors may send messages designed to trick users into revealing their verification codes. Compromised mobile devices and carrier vulnerabilities also pose potential security risks.
Comparison of Authentication Methods, Its time stop using services force you use sms based two factor authentication
A comparison of SMS-based 2FA with alternative methods reveals differing strengths and weaknesses.
| Feature | SMS-based 2FA | Authenticator App-based 2FA | Biometric Authentication |
|---|---|---|---|
| Security | Vulnerable to SIM swap attacks, phishing, and potentially compromised devices. Relies on the security of the mobile carrier and user’s phone. | Generally more secure, as codes are generated locally on the user’s device. Less susceptible to SIM swap attacks. | Highly secure, as it relies on unique biological traits. Difficult to replicate or spoof. |
| Convenience | Relatively convenient, as it requires only a phone. | Requires a dedicated app, potentially introducing a new security element to manage. | Convenient, once set up, but requires user interaction to authenticate. |
| Cost | Typically free, as it utilizes existing mobile network infrastructure. | May involve a small fee for the app or associated services. | May involve initial costs for the biometric device. |
Alternatives to SMS-based 2FA
SMS-based two-factor authentication (2FA) has become a standard security measure, but its reliance on SMS messages introduces vulnerabilities. This reliance on a potentially insecure channel raises concerns about security and convenience. Alternatives offer a more robust and user-friendly approach to securing accounts.These alternatives provide improved security and user experience, addressing the limitations of SMS-based 2FA. They leverage more secure channels and methods, leading to a more secure and convenient authentication process.
App-based 2FA
App-based 2FA, such as Google Authenticator or Authy, generates time-based one-time passwords (TOTP). These apps use cryptographic algorithms to create unique codes, reducing the risk of interception compared to SMS. The codes are generated on a device, further enhancing security.This method significantly enhances security by relying on a trusted device and cryptographic principles. This eliminates the need to transmit sensitive information over an potentially insecure channel.
It’s high time we stopped using services that force SMS-based two-factor authentication. Security’s important, but relying solely on text messages is a major vulnerability. Fortunately, there are great tech deals out there, like amazing deals on HomePods, Surface Go’s, Samsung Galaxy phones, and Microsoft Xboxes. Check out these deals if you’re looking for some new tech.
But in the meantime, let’s work towards a more secure future where we don’t have to depend on such easily compromised methods for two-factor authentication.
Hardware Tokens
Hardware tokens are physical devices that generate one-time passwords (OTPs). These tokens, like YubiKeys, use hardware-based cryptographic security. The tokens are often more secure than software-based methods.Hardware tokens provide a high level of security due to their physical separation from the network and use of specialized cryptographic hardware. They also offer a convenient alternative to relying on software for generating security codes.
Comparison of Authentication Methods, Its time stop using services force you use sms based two factor authentication
| Feature | SMS-based 2FA | App-based 2FA | Hardware Tokens |
|---|---|---|---|
| Security | Vulnerable to interception and SIM swapping. Relies on SMS infrastructure. | More secure than SMS, utilizing cryptographic algorithms on a trusted device. | Extremely secure, leveraging hardware-based cryptography and physical separation. |
| Convenience | Convenient for users with reliable SMS service. | Convenient, as codes are generated on a user’s device. | Convenient, though initial setup might take a little longer. |
| Cost | Generally low cost, often included with mobile service plans. | Low cost, as apps are typically free to download and use. | Higher upfront cost for hardware tokens. Ongoing maintenance costs are negligible. |
These comparisons demonstrate the trade-offs between different authentication methods. SMS-based 2FA is convenient but vulnerable. App-based and hardware-based alternatives offer significantly improved security, albeit with differing degrees of convenience and cost.
It’s high time we stopped using services that force SMS-based two-factor authentication. Frankly, it’s incredibly annoying, especially when dealing with a game as exciting as Diablo, which is coming to Game Pass soon! Diablo is coming to game pass. These methods are often insecure and unreliable, making it way too easy for hackers to gain access.
Let’s move towards more robust and secure authentication solutions.
Security Considerations for 2FA
SMS-based two-factor authentication (2FA) is a popular method for adding an extra layer of security to online accounts. However, it’s crucial to understand its vulnerabilities and how to mitigate them. While convenient, SMS-based 2FA isn’t without its inherent risks. This section delves into the key security weaknesses and offers practical strategies for bolstering your account protection.SMS-based 2FA, despite its widespread use, is susceptible to various attacks, often due to the reliance on SMS messages as a verification channel.
Understanding these vulnerabilities is essential to adopting robust security practices. A critical aspect of safeguarding your accounts is recognizing the weaknesses in this method and adopting more secure alternatives when possible.
SMS-Based 2FA Vulnerabilities
SMS-based 2FA relies on the security of the mobile phone number linked to the account. This makes it susceptible to attacks that compromise this link, such as SIM swapping and phishing. Malicious actors can gain access to verification codes if they control the mobile device or trick the user into revealing them.
SIM Swapping
SIM swapping is a sophisticated attack where attackers gain control of a user’s mobile phone number and associated SIM card. By convincing the mobile carrier to transfer the SIM card to their device, attackers obtain the victim’s SMS-based verification codes. This allows them to access the victim’s accounts. The process often involves social engineering tactics, making it crucial to be wary of suspicious requests from unknown parties.
Phishing Attacks
Phishing attacks aim to trick users into revealing sensitive information, including verification codes. Attackers may send deceptive messages that appear to be from legitimate organizations, prompting the user to click links or enter their codes. The messages might look genuine, using convincing branding and design to mimic official communication.
Importance of Strong Passwords
A strong password, in conjunction with 2FA, significantly strengthens account security. Even with 2FA, a weak password can be exploited if an attacker gains access to the account credentials. Robust passwords are essential to prevent unauthorized access. Consider using a password manager to create and store strong, unique passwords for different accounts.
It’s high time we stopped using services that force SMS-based two-factor authentication. Think about the recent geopolitical events, like the Russia-Roscosmos withdrawal from the International Space Station partnership with NASA, here’s a good overview of that. These situations highlight the vulnerabilities of relying on easily disrupted communication channels like SMS for crucial security. We need more robust and secure alternatives.
Security Best Practices
Implementing robust security practices is essential to protect your accounts from various threats.
| Practice | Description | Implementation Steps |
|---|---|---|
| Strong Passwords | Creating unique, complex passwords that are difficult to guess. | Use a password manager to generate and store strong passwords. Combine uppercase and lowercase letters, numbers, and symbols. Avoid using easily guessable information like birthdays or names. |
| Multi-Factor Authentication (MFA) | Using multiple authentication methods to verify user identity. This involves combining login credentials with a secondary verification method, such as a security key or authenticator app. | Enable MFA whenever possible for all your accounts. Choose methods that offer the highest level of security. Consider using a hardware security key for the strongest protection. |
| Regular Security Audits | Regularly reviewing your accounts and security settings to identify and address potential vulnerabilities. | Check your account settings regularly for any suspicious activity. Enable alerts for login attempts from unknown devices. Monitor your financial accounts for unauthorized transactions. Review your security settings to ensure they are up-to-date. |
Practical Steps for Switching to Alternatives
Switching from SMS-based 2FA to more secure alternatives is crucial for safeguarding your accounts. SMS-based authentication relies on easily intercepted text messages, making it vulnerable to phishing and SIM swapping attacks. Implementing stronger authentication methods like authenticator apps or hardware tokens significantly enhances your account security.Implementing alternative authentication methods offers several advantages. These alternatives provide a more robust layer of security, often relying on verification through unique codes generated by apps or physical devices.
This reduces reliance on SMS, which is susceptible to interception and compromises.
Disabling SMS-based 2FA
Disabling SMS-based 2FA varies depending on the platform. Typically, you’ll find an account security or settings section where you can manage authentication methods. Each service has its own procedure, so careful attention to the platform’s instructions is paramount.
Setting Up Alternative 2FA Methods
Numerous alternative 2FA methods are available. Popular choices include authenticator apps (like Google Authenticator or Authy), which generate time-based codes, and hardware tokens, providing physical security. These alternatives are generally more secure than SMS-based authentication.
Examples of Services Offering Different Authentication Options
Many services support various 2FA methods beyond SMS. For example, Google allows using apps like Google Authenticator for account protection. Microsoft offers similar options, including authenticator apps and hardware tokens. Many banking and e-commerce platforms provide comparable choices.
Step-by-Step Guide: Switching from SMS to Google Authenticator (Example)
| Step | Action | Screenshot Description |
|---|---|---|
| Step 1 | Open your account settings. This is usually accessible from the profile or account menu. | The screenshot shows a typical account settings page with a navigation menu. Look for a section labeled “Security,” “Settings,” or similar. |
| Step 2 | Locate the 2FA section. This section will typically Artikel your current authentication methods. | The screenshot highlights the section dedicated to managing 2FA. A list of existing authentication methods is displayed, including the SMS-based option. |
| Step 3 | Disable SMS-based 2FA. Follow the instructions provided by the platform to disable this method. | The screenshot shows a confirmation prompt asking to disable SMS-based authentication. There is a clear button to confirm the action. |
| Step 4 | Download and install a 2FA authenticator app (like Google Authenticator). | The screenshot displays the Google Authenticator app icon or a download page for the app. |
| Step 5 | Configure the authenticator app on the platform. You’ll need to scan a QR code or manually enter the setup code provided by the platform. | The screenshot shows the QR code displayed by the platform. A corresponding QR code scanner within the authenticator app is also visible. |
| Step 6 | Verify the setup. The authenticator app should display a code. Enter this code into the platform to confirm the setup. | The screenshot shows a verification code displayed on the Google Authenticator app. A field to enter this code on the platform is shown. |
| Step 7 | Verify the setup. The authenticator app should display a code. Enter this code into the platform to confirm the setup. | The screenshot displays a confirmation message or a successful setup notification. |
Potential Benefits of Transitioning
Moving beyond SMS-based two-factor authentication (2FA) unlocks a world of enhanced security and user experience. This transition isn’t just about replacing a method; it’s about bolstering your defenses against increasingly sophisticated cyber threats and creating a more seamless and secure digital environment for yourself and your users. The potential benefits extend far beyond immediate security improvements, impacting long-term costs and user satisfaction.The primary benefit of abandoning SMS-based 2FA lies in the inherent vulnerabilities of SMS itself.
SMS messages are susceptible to interception and manipulation, making them a weak link in the security chain. Alternatives offer a significantly stronger foundation for protecting your accounts.
Enhanced Security
SMS-based 2FA relies on the security of the SMS channel, which is notoriously vulnerable. Alternatives, like authenticator apps and hardware tokens, generate unique codes tied to your device, minimizing the risk of interception and making your accounts far more resistant to breaches.
Preventing Account Compromises
Transitioning to alternative authentication methods can dramatically reduce the likelihood of account compromises. For instance, if an attacker intercepts an SMS message containing your 2FA code, they can gain access to your account. Using an authenticator app or a hardware token prevents this, as these methods don’t rely on the SMS channel. Sophisticated phishing attacks can often trick users into revealing their SMS-based 2FA codes, but alternative methods are more resistant to these types of attacks.
This is exemplified in the increased security measures taken by financial institutions and e-commerce platforms that have already moved away from SMS-based 2FA.
Improved User Experience
Alternative authentication methods often provide a more streamlined and intuitive user experience compared to SMS-based 2FA. Authenticator apps typically generate codes on demand, reducing the need to manually input lengthy codes and reducing friction during login processes. Hardware tokens provide a similarly convenient and secure alternative. This enhanced user experience translates into increased user satisfaction and reduced frustration during login attempts.
Long-Term Cost Savings
While the initial investment in implementing alternative authentication methods might seem costly, the long-term benefits in terms of reduced security incidents and the potential for data breaches far outweigh the short-term expense. The cost savings stem from decreased incident response time, reduced recovery costs, and the avoidance of potential legal and reputational damage resulting from compromised accounts. For example, a single data breach can cost organizations millions of dollars in remediation efforts, fines, and lost revenue.
The investment in more robust authentication methods is an investment in safeguarding your assets and reputation, thus avoiding these long-term financial risks.
Addressing User Concerns
Switching to alternatives to SMS-based two-factor authentication (2FA) can sometimes raise concerns among users. Understanding these concerns and proactively addressing them is crucial for a smooth transition. This section Artikels strategies to alleviate user apprehension and ensure a positive experience during the migration process.Users often express concerns about the complexity of alternative authentication methods. They might feel intimidated by unfamiliar procedures or worry about remembering new security codes.
Addressing these concerns requires a multi-faceted approach, combining clear explanations with readily available support.
Simplifying Alternative Methods
A key strategy for mitigating user concerns is to present alternative authentication methods in a user-friendly manner. Avoid technical jargon and focus on clear, concise explanations. Visual aids, such as diagrams or step-by-step instructions, can significantly enhance understanding. For example, a simple flow chart demonstrating the process of authenticating via a dedicated authenticator app can greatly reduce confusion.
Providing Comprehensive Support
Offering readily available support channels is vital. This includes creating detailed FAQs, providing access to online tutorials, and offering dedicated customer support personnel to answer user queries. A comprehensive help center should cover common questions and technical issues. Dedicated phone numbers and email addresses for customer support should be readily accessible. Additionally, a knowledge base with downloadable guides and video tutorials will help users navigate new procedures.
Transition Strategy
A well-defined transition strategy can effectively mitigate user apprehension. Start by gradually rolling out the alternative methods, allowing users to familiarize themselves with the new procedures before a complete switch. Provide ample time for users to adapt and seek assistance if needed. This gradual approach prevents overwhelming users with a sudden change and fosters a more comfortable transition.
A phased rollout allows for feedback collection and allows the organization to identify and address potential issues before a full-scale deployment. This iterative approach reduces stress for all users involved.
User Assistance Resources
A dedicated resource page for users seeking assistance is crucial. This page should include links to FAQs, step-by-step guides, and contact information for customer support. The page should also provide links to frequently used security resources. Clear and easy-to-understand language is key for maximum impact. Interactive demos or short video tutorials can provide valuable hands-on experience for users.
Last Point

In conclusion, while SMS-based two-factor authentication might seem convenient, the inherent security risks make it a less than ideal choice. By switching to more secure alternatives like app-based authentication or hardware tokens, you can significantly bolster your account security and peace of mind. This guide provides the knowledge and steps needed to make the switch, ensuring a safer online experience.
Take control of your security today!