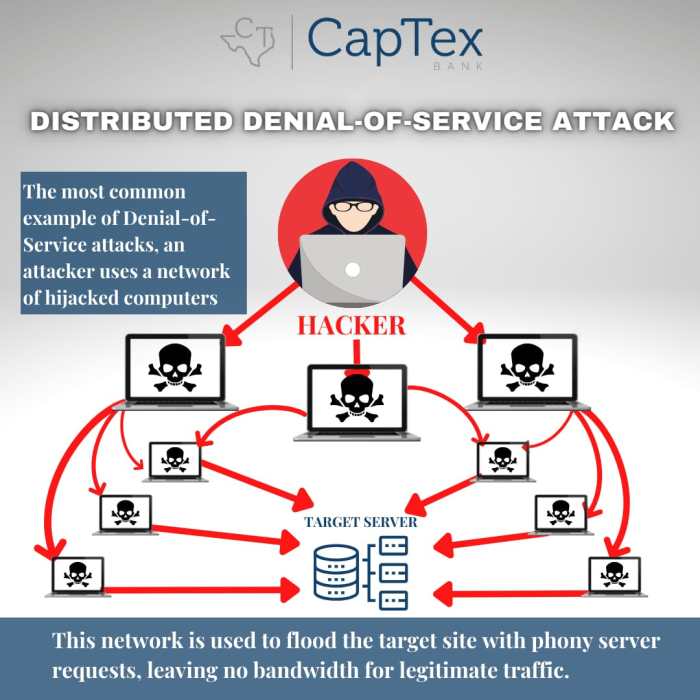
DDoS attack internet of things security problems dns mirai is a significant threat to internet infrastructure. This complex issue involves distributed denial-of-service attacks targeting Internet of Things (IoT) devices, often leveraging vulnerabilities in DNS systems and amplified by the Mirai botnet. Understanding these attack vectors and the underlying security weaknesses is crucial to mitigating the growing impact of these attacks.
This article delves into the intricacies of DDoS attacks, focusing on the exploitation of IoT devices, the role of DNS, and the destructive power of the Mirai botnet. We’ll explore various attack types, examine vulnerabilities in IoT systems, and discuss mitigation strategies, including the use of cloud-based protection services.
Introduction to DDoS Attacks: Ddos Attack Internet Of Things Security Problems Dns Mirai

Distributed Denial-of-Service (DDoS) attacks are malicious attempts to disrupt the normal functioning of a network, service, or website by overwhelming it with a flood of traffic. These attacks exploit the finite resources of targeted systems, rendering them unavailable to legitimate users. The fundamental principle is to exhaust the target’s capacity to handle requests, effectively crippling its operations.DDoS attacks rely on the coordinated efforts of multiple compromised systems, often referred to as a botnet.
These compromised systems, or bots, act as puppets, unknowingly participating in the attack. This distributed nature makes DDoS attacks exceptionally challenging to mitigate, as identifying and shutting down the source of the attack requires a multifaceted approach.
Different Types of DDoS Attacks
Various attack vectors exploit different vulnerabilities in network protocols and infrastructure. IoT devices, with their inherent vulnerabilities and ease of compromise, are increasingly targeted.
IoT-Specific DDoS Attacks
The proliferation of Internet of Things (IoT) devices, such as smart home appliances, security cameras, and industrial control systems, presents a unique challenge. These devices often have weak security configurations, making them susceptible to compromise and subsequent use in large-scale DDoS attacks. Attackers can easily recruit these devices into botnets, overwhelming targeted networks with massive amounts of traffic.
The Mirai botnet, a notorious example, exploited vulnerabilities in IoT devices to create a significant threat.
Impact on Internet Infrastructure
DDoS attacks can have significant repercussions for internet infrastructure. They can disrupt critical services, causing widespread outages and financial losses. Businesses reliant on online services, such as e-commerce platforms and online banking, can experience substantial revenue losses due to downtime. Furthermore, DDoS attacks can damage the reputation of affected organizations, leading to a loss of customer trust.
Comparison of DDoS Attack Vectors
| Attack Vector | Mechanism | Target | Impact |
|---|---|---|---|
| SYN Flood | Exploits the TCP handshake process by sending a large number of SYN packets without completing the connection. | TCP-based services | Consumes server resources, leading to denial of service. |
| UDP Flood | Overwhelms the target with a massive volume of UDP packets. | UDP-based services, especially DNS | Overloads network bandwidth and server resources. |
| HTTP Flood | Generates a high volume of HTTP requests to the target website. | Web servers | Consumes server resources, leading to website unavailability. |
IoT Vulnerabilities in DDoS Attacks
The Internet of Things (IoT) has revolutionized numerous aspects of our lives, but this interconnectedness comes with significant security risks. IoT devices, often designed with ease of use and low cost in mind, frequently lack robust security measures. This vulnerability makes them prime targets for malicious actors seeking to launch Distributed Denial-of-Service (DDoS) attacks. These attacks exploit the inherent weaknesses in these devices, causing disruptions to services and potentially crippling entire networks.Exploiting these vulnerabilities allows attackers to leverage the collective power of compromised IoT devices to overwhelm targeted systems with malicious traffic.
This overwhelming flood of requests can render the target inaccessible to legitimate users. The result is a significant loss of service and potential financial damage to organizations and individuals.
Common IoT Vulnerabilities
Many IoT devices share common vulnerabilities that attackers leverage for DDoS attacks. These vulnerabilities often stem from a lack of secure design principles and inadequate security updates. Poor authentication protocols, default passwords, and weak encryption are frequently encountered weaknesses.
- Default Credentials: Many IoT devices are shipped with default usernames and passwords. Attackers can use readily available lists of these default credentials to gain unauthorized access to the devices.
- Lack of Secure Communication Protocols: Some devices use insecure communication protocols, which allow attackers to intercept and manipulate data transmitted between the device and the network.
- Limited or No Security Updates: Manufacturers often fail to provide timely security updates for IoT devices. This allows attackers to exploit known vulnerabilities that haven’t been patched.
- Poor Code Quality: Bugs and vulnerabilities in the software running on the devices can be exploited by attackers to gain control and launch attacks.
Exploitation Techniques, Ddos attack internet of things security problems dns mirai
Attackers employ various techniques to exploit these vulnerabilities. One common method involves using automated tools to scan for vulnerable devices and then remotely compromise them. Once compromised, these devices are added to a botnet, a network of infected devices, used to generate malicious traffic. Another approach involves exploiting known vulnerabilities in device firmware or applications to gain control.
IoT Devices in Amplification Attacks
IoT devices play a crucial role in amplification attacks, where attackers leverage the device’s ability to respond to requests significantly larger than the original request. This amplification effect can dramatically increase the volume of malicious traffic directed at the target, making it even more challenging to defend against the attack.
Examples of Vulnerable IoT Devices
Numerous IoT devices have been identified as vulnerable to DDoS attacks. These devices range from smart home appliances to industrial sensors.
- Smart Cameras: Many smart cameras use insecure protocols and default passwords, making them susceptible to being exploited in DDoS attacks.
- Internet-Connected Routers: Routers, often overlooked in security assessments, can be vulnerable to attacks that can disrupt network traffic.
- Smart TVs: Some smart TVs use weak authentication protocols, making them potential targets for exploitation.
- Network-Attached Storage Devices: NAS devices, which store and manage data, can be vulnerable if not properly secured.
IoT Device Attack Surface Analysis
The following table Artikels different categories of IoT devices and their respective attack surface, highlighting the potential vulnerabilities associated with each category.
| Device Category | Attack Surface |
|---|---|
| Smart Home Appliances (e.g., thermostats, lights) | Default credentials, weak encryption, limited or no security updates |
| Industrial IoT Devices (e.g., sensors, actuators) | Vulnerable firmware, lack of secure communication protocols, limited or no security updates |
| Smart City Infrastructure (e.g., traffic lights, parking meters) | Default credentials, weak encryption, potential for critical infrastructure disruption |
| Wearable Devices (e.g., fitness trackers) | Limited security features, insecure data transmission, lack of secure storage |
The Role of DNS in DDoS Attacks
The Domain Name System (DNS) is the internet’s phone book. It translates human-readable domain names (like example.com) into machine-readable IP addresses, allowing us to access websites and services. Without DNS, the internet as we know it wouldn’t function. However, this crucial system also makes it vulnerable to exploitation in DDoS attacks.DNS servers are distributed globally, meaning a request for a domain name can be routed through multiple servers.
This decentralized nature can be a double-edged sword, as it can also be leveraged to amplify the impact of attacks.
DNS Functionality in Internet Communication
DNS servers act as intermediaries, resolving domain names to IP addresses. When a user types a domain name into their browser, a request is sent to a DNS resolver. This resolver queries various DNS servers until it locates the authoritative DNS server for that domain. The authoritative server provides the corresponding IP address, which the resolver then returns to the user’s browser.
This process ensures that users can access websites without needing to know their complex numerical IP addresses.
DNS Exploitation for DDoS Amplification Attacks
DNS servers are vulnerable to exploitation, making them a prime target for DDoS amplification attacks. A malicious actor can send a spoofed DNS query to an open or vulnerable DNS server, effectively tricking it into responding to a request that appears to come from a legitimate user. However, the response is massive, sent to a target victim, causing significant network overload and disruption.
This amplification effect is the core of a DNS reflection attack. The attacker uses the DNS server as a proxy, amplifying the attack’s volume, and overwhelming the victim with traffic.
DNS Reflection Attacks
DNS reflection attacks exploit the open nature of many DNS servers. These servers often respond to DNS queries regardless of the source, making them susceptible to being used as amplification tools. Attackers craft spoofed DNS queries, faking the source address to appear as if the request originated from the target. The legitimate DNS server then responds with a large volume of data to the target, overwhelming its resources.
Mirai Botnet and DNS Amplification
The Mirai botnet, notorious for its IoT-based DDoS attacks, frequently leveraged DNS amplification. Mirai-infected devices were programmed to send spoofed DNS requests to open DNS resolvers. These requests were directed to a victim’s IP address, causing a massive influx of traffic. The result was a significant disruption to the target’s online services.
Impact on Internet Performance and Availability
DNS amplification attacks can severely impact internet performance and availability. Targets experiencing these attacks often experience website outages, slow loading times, or complete network inaccessibility. This impacts businesses, individuals, and critical infrastructure, disrupting operations and causing significant financial losses. For example, a DNS amplification attack can overwhelm a bank’s online services, blocking customers from accessing their accounts.
Comparison of DNS Record Types and Susceptibility
| DNS Record Type | Description | Susceptibility to DDoS Exploitation |
|---|---|---|
| A (Address) | Maps a domain name to an IPv4 address. | Lower |
| AAAA (IPv6 Address) | Maps a domain name to an IPv6 address. | Lower |
| CNAME (Canonical Name) | Creates an alias for another domain. | Lower |
| MX (Mail Exchange) | Specifies mail servers for a domain. | Higher |
| NS (Name Server) | Specifies the authoritative name servers for a domain. | Higher |
| TXT (Text) | Stores arbitrary text. | Lower |
DNS record types vary in their susceptibility to DDoS exploitation. MX and NS records, which often carry more data, are more prone to amplification attacks. A, AAAA, and CNAME records, containing basic address information, are less susceptible. Understanding these vulnerabilities is crucial in mitigating the risks of DNS-based DDoS attacks.
The Mirai Botnet and its Impact
The Mirai botnet, a formidable force in the world of Distributed Denial-of-Service (DDoS) attacks, has left an indelible mark on internet security. Its sophistication and the sheer scale of its attacks have highlighted the vulnerabilities of the Internet of Things (IoT) and the urgent need for robust security measures. This botnet has demonstrated the potential for coordinated attacks to overwhelm even the most resilient online infrastructure.The Mirai botnet operates as a vast network of compromised devices, effectively turning them into unwitting instruments of malicious intent.
Its core functionality is based on exploiting vulnerabilities in internet-connected devices, such as routers, cameras, and other smart home appliances. This exploitation allows the botnet to command and control these devices, turning them into a powerful weapon capable of launching massive DDoS attacks.
Mirai Botnet Structure and Functionality
Mirai’s structure is built around a client-server architecture. Malicious software, the Mirai malware, infects vulnerable IoT devices, transforming them into “bots.” These bots then communicate with a central command-and-control server (C&C), which orchestrates the attacks. The C&C server directs the bots to flood a target with traffic, effectively shutting down the target’s services. The malware is specifically designed to target various IoT devices and exploits their vulnerabilities.
Mirai Botnet Targeting Strategies
Mirai’s targeting strategies are often opportunistic, aiming for large, easily accessible networks of vulnerable IoT devices. Common targets include online gaming platforms, e-commerce websites, and even critical infrastructure. The botnet seeks to exploit the ease of access to these networks, which are often inadequately protected. This strategy leverages the sheer volume of compromised devices to overwhelm targets.
How Mirai Leverages IoT Devices
The Mirai botnet capitalizes on the widespread adoption of IoT devices, which often lack robust security measures. These devices, including cameras, routers, and smart appliances, are typically configured with default usernames and passwords, making them easy targets for the botnet. Exploiting these vulnerabilities, Mirai effectively transforms these devices into agents of the attack. This widespread adoption of IoT devices without adequate security protocols has created a fertile ground for botnet infections.
Impact on Internet Infrastructure and Security
The Mirai botnet’s impact on internet infrastructure and security has been significant and far-reaching. Large-scale DDoS attacks launched by Mirai can cripple websites, services, and even critical infrastructure. These attacks can cause significant financial losses for businesses, disrupt essential services, and erode public trust in online systems. The sheer volume of compromised devices in Mirai’s arsenal makes it a significant threat.
Identifying and Mitigating Mirai Infections
Identifying and mitigating Mirai infections requires a multi-faceted approach. Regular security audits of IoT devices, updating firmware to the latest versions, and implementing strong passwords are crucial steps. Using intrusion detection systems and firewalls can also help detect and block malicious traffic originating from infected devices. Security awareness training for users is also important.
IoT security vulnerabilities, like DDoS attacks leveraging DNS and Mirai botnets, are a real concern. Thankfully, advancements like chrome on android refined custom tabs browsing in mobile web browsing can offer a different kind of security layer, focusing on user experience and privacy. Ultimately, though, robust security protocols and proactive measures are still critical to address these complex DDoS attack issues.
Stages of a Mirai Infection and Mitigation Actions
| Stage | Description | Mitigation Actions |
|---|---|---|
| Discovery and Exploitation | Mirai scans for vulnerable devices with default credentials. | Regular security audits, updating firmware, and implementing strong passwords. |
| Infection | Malicious code is downloaded and executed on the compromised device. | Intrusion detection systems and firewalls. |
| Recruitment | The infected device joins the Mirai botnet network. | Implementing security measures, monitoring networks for suspicious activity, and utilizing specialized security tools. |
| Command and Control | The botnet’s C&C server issues commands to the infected devices. | Utilizing security solutions to block C&C communications. |
| Attack | The infected devices are used to launch DDoS attacks. | DDoS mitigation services and proactive security measures. |
Security Problems in IoT Environments
The proliferation of Internet of Things (IoT) devices has revolutionized various aspects of modern life, but this interconnectedness comes with significant security vulnerabilities. These devices, often designed with cost and convenience as primary concerns, frequently lack robust security measures, creating a significant attack surface for malicious actors. Understanding these vulnerabilities is crucial for mitigating risks and ensuring the safety and reliability of IoT systems.
DDoS attacks targeting IoT devices, particularly vulnerabilities in DNS like Mirai, are a serious security concern. While the complex world of AI and deep learning continues to advance, like in the alphago deepmind go match 3 result , these attacks still pose a real threat to internet stability. We need to continue focusing on patching these security holes in IoT systems to prevent further disruption.
Security Gaps in IoT System Design and Deployment
IoT devices are often designed and deployed with limited resources, leading to compromises in security features. This includes inadequate hardware capabilities, restricted processing power, and limited memory. These constraints frequently result in simplified security protocols that are easily bypassed by attackers. Furthermore, the lack of standardization in IoT device architectures makes it difficult to implement and enforce consistent security measures across different platforms and manufacturers.
This lack of interoperability further exacerbates the problem.
IoT Device Authentication and Authorization Issues
Insecure authentication and authorization mechanisms pose a major threat to IoT security. Many IoT devices employ weak or default passwords, making them easily accessible to attackers. The lack of multi-factor authentication and strong cryptographic techniques leaves devices susceptible to unauthorized access and control. Furthermore, the absence of robust user authentication mechanisms for device management and configuration updates allows attackers to gain control without proper authorization.
Lack of Security Updates and Patching for IoT Devices
A significant challenge in securing IoT systems is the infrequent or nonexistent security updates and patches for many devices. Manufacturers often prioritize speed of deployment over long-term security, leading to a large number of devices running outdated software vulnerable to known exploits. This lack of proactive security maintenance makes IoT devices easy targets for attacks. Furthermore, the complexity of updating firmware on these devices can be daunting for both manufacturers and users.
Insecure Default Credentials and Configurations
Default credentials and configurations on many IoT devices are often easily guessed or readily available online. Attackers frequently leverage publicly available databases of default credentials to gain unauthorized access to these devices. This problem is further exacerbated by a lack of user awareness and education about changing default passwords and configurations. These devices, often deployed without user intervention, remain vulnerable to attacks based on easily predictable default settings.
Summary of Major Security Challenges in IoT Systems
| Security Challenge | Description | Impact |
|---|---|---|
| Inadequate Security Design | Limited resources, simplified protocols, lack of standardization in architectures. | Increased attack surface, easier exploitation. |
| Weak Authentication/Authorization | Default passwords, lack of multi-factor authentication, poor user authentication. | Unauthorized access, device takeover. |
| Lack of Security Updates | Infrequent or absent updates, complex update processes. | Exposure to known exploits, prolonged vulnerability. |
| Insecure Default Credentials/Configurations | Publicly available default credentials, lack of user awareness. | Easy compromise through default settings. |
Mitigation Strategies for DDoS Attacks
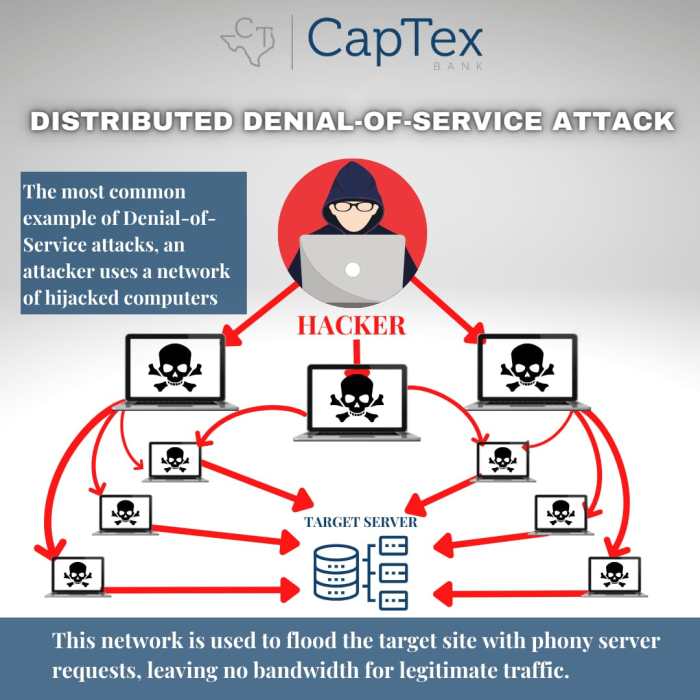
Defending against Distributed Denial-of-Service (DDoS) attacks, particularly those leveraging Internet of Things (IoT) devices, requires a multifaceted approach. Simply reacting to an attack is often insufficient. Proactive measures, including robust network security infrastructure and proactive threat detection, are crucial to minimizing the impact of these attacks and safeguarding critical services. Effective mitigation strategies depend on understanding the attack vectors, implementing appropriate filtering mechanisms, and leveraging cloud-based solutions for scalability and resilience.
Detecting and Identifying IoT-Targeted DDoS Attacks
Identifying DDoS attacks targeting IoT devices requires advanced monitoring tools and techniques. Anomaly detection systems are essential, identifying unusual traffic patterns originating from numerous devices that deviate significantly from baseline network activity. Analyzing network traffic for patterns indicative of malicious activity, such as high volumes of connection requests from a specific IP address range or a surge in UDP traffic, is a key element in early detection.
Correlation of these indicators with known IoT device characteristics, such as operating system versions and unique device identifiers, enhances the accuracy of attack identification. Security information and event management (SIEM) systems play a vital role in aggregating and correlating various security logs to pinpoint attack origins and identify compromised IoT devices.
Importance of Robust Network Security Infrastructure
Implementing a robust network security infrastructure is paramount in mitigating DDoS attacks. Firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS) should be strategically placed throughout the network to monitor and block malicious traffic. These systems must be configured to recognize and filter specific attack patterns associated with IoT devices, such as SYN floods, UDP floods, and application-layer attacks.
Regular security audits and penetration testing are essential to identify vulnerabilities in the network infrastructure and implement appropriate safeguards.
Strategies for Mitigating DDoS Attacks
Various strategies are employed to mitigate DDoS attacks. These include traffic filtering, rate limiting, and employing specialized DDoS mitigation services. Load balancing distributes traffic across multiple servers, preventing a single point of failure and absorbing the impact of the attack. Caching mechanisms store frequently accessed data, reducing the load on the origin servers during peak demand. Diversion techniques reroute malicious traffic to decoy servers, minimizing the damage to legitimate servers.
Rate Limiting and Traffic Filtering
Rate limiting and traffic filtering are fundamental techniques for mitigating DDoS attacks. Rate limiting controls the rate at which requests are processed from individual sources, preventing overwhelming the system with excessive traffic. This technique is effective against floods of requests from a single IP address or a group of compromised devices. Traffic filtering involves analyzing network traffic to identify and block malicious packets based on predefined criteria, such as source IP addresses, ports, or protocols.
This method is crucial in identifying and filtering unwanted traffic originating from compromised IoT devices.
Implementing a Robust DDoS Mitigation System
Implementing a robust DDoS mitigation system requires a layered approach. The system should incorporate proactive threat detection and response mechanisms, combined with robust network security infrastructure. This involves a combination of hardware and software solutions, including firewalls, intrusion detection systems, and cloud-based mitigation services. Regular security assessments and continuous monitoring are critical to identifying and addressing evolving threats.
Cloud-Based DDoS Protection Services
Cloud-based DDoS protection services provide a scalable and cost-effective solution for mitigating DDoS attacks. These services utilize geographically distributed scrubbing centers to absorb and filter malicious traffic, protecting the network from being overwhelmed. Their inherent scalability allows for quick response to evolving attack patterns and ensures that the system can handle increasing traffic demands. These services typically offer various features, including traffic filtering, rate limiting, and attack detection.
Comparison of DDoS Mitigation Techniques
| Mitigation Technique | Description | Strengths | Weaknesses |
|---|---|---|---|
| Rate Limiting | Controls the rate of requests from a single source. | Simple to implement, effective against flood attacks. | May not be effective against sophisticated attacks, can impact legitimate users. |
| Traffic Filtering | Analyzes traffic and blocks malicious packets. | Effective in identifying and blocking malicious traffic. | Requires careful configuration to avoid blocking legitimate traffic. |
| Load Balancing | Distributes traffic across multiple servers. | Increases system resilience, improves performance. | Requires a complex infrastructure and careful setup. |
| Cloud-Based Mitigation | Uses geographically distributed scrubbing centers. | Highly scalable, cost-effective, and quick response to attacks. | Dependence on third-party service, potential latency issues. |
Case Studies and Examples
Real-world DDoS attacks targeting IoT devices and DNS infrastructure have demonstrated the significant vulnerability of interconnected systems. These attacks, often orchestrated by sophisticated botnets, have far-reaching consequences for businesses and individuals, disrupting services and impacting critical infrastructure. Understanding these attacks, their impacts, and the responses of affected organizations is crucial for developing effective mitigation strategies.
Impact on Businesses and Individuals
DDoS attacks targeting IoT devices can cripple businesses by disrupting online services, halting production, and causing substantial financial losses. Individuals can also be affected, experiencing slowdowns or complete service outages. The impact extends beyond immediate financial loss, as reputational damage and customer churn can be long-lasting.
Specific DDoS Attack Case Study: Dyn DNS Attack of 2016
The 2016 DDoS attack against Dyn DNS, a major domain name system provider, serves as a stark example of the potential damage from such attacks. This attack, leveraging a massive botnet composed largely of compromised IoT devices, brought down numerous popular websites, impacting millions of users worldwide.
Talking about DDoS attacks and IoT security woes, like DNS amplification and Mirai botnets, is important. However, the recent partnership between Google, Meta, Ray-Ban, and EssilorLuxottica, focusing on augmented reality glasses, could lead to interesting security challenges down the road. This partnership could open new avenues for attacks, potentially impacting the very infrastructure these companies are trying to build.
So, while we’re excited about innovative tech like the one in google meta ray ban essilorluxottica partnership , we still need to address the core issue of securing the internet of things from similar DDoS attacks.
Impact on Affected Organizations
The Dyn attack highlighted the vulnerability of critical infrastructure to coordinated attacks. Affected organizations experienced significant service disruptions, leading to lost revenue, damage to reputation, and potential legal repercussions.
Response Mechanisms of Affected Organizations
In the wake of the attack, Dyn and other affected organizations implemented various response mechanisms. These included upgrading their infrastructure to handle higher traffic loads, implementing advanced DDoS mitigation techniques, and strengthening security measures to prevent future attacks. The attack also spurred industry-wide discussions about IoT security best practices.
Mitigation Strategies Used
The Dyn attack, and other similar incidents, underscored the need for proactive mitigation strategies. These include robust security measures for IoT devices, regular vulnerability assessments, and the implementation of DDoS mitigation services. Improved collaboration between security researchers and organizations is also critical for sharing threat intelligence and developing more effective defenses.
Future Trends and Predictions
The landscape of cybersecurity is constantly evolving, and the Internet of Things (IoT) presents a unique set of challenges. As more devices connect to the internet, the potential attack surface expands, making DDoS attacks increasingly sophisticated and dangerous. Predicting future trends requires careful consideration of emerging technologies, evolving threat actors, and the constant race between attackers and defenders.The future of IoT security hinges on our ability to anticipate and adapt to these evolving threats.
Proactive measures, encompassing robust security protocols, improved device hardening, and user education, are critical to safeguarding the expanding IoT ecosystem. We must move beyond reactive measures and embrace a proactive approach that anticipates and mitigates potential vulnerabilities before they can be exploited.
Evolving DDoS Attack Threats
The nature of DDoS attacks is shifting. Traditional volumetric attacks are becoming less effective as defenses improve. Instead, attackers are focusing on more targeted, application-layer attacks that exploit specific vulnerabilities within IoT devices and networks. This evolution necessitates a shift in defensive strategies. Sophistication in attack techniques is a key aspect of the evolving threat.
Moreover, the combination of multiple attack vectors and the use of sophisticated tools and techniques pose a significant challenge.
Future Trends in IoT Security
The increasing complexity of IoT ecosystems necessitates continuous advancements in security measures. A key trend involves the development of more robust and resilient security protocols, such as those employing advanced encryption and authentication mechanisms. The growing adoption of machine learning and artificial intelligence (AI) plays a crucial role in automating threat detection and response. Furthermore, the emergence of blockchain technology offers the potential to enhance the security and transparency of IoT networks.
Emerging Threats and Vulnerabilities in IoT Ecosystems
The interconnected nature of IoT devices creates a complex network of potential vulnerabilities. As devices become increasingly sophisticated, so do the attack vectors. Emerging vulnerabilities stem from software bugs, insecure communication protocols, and weak default configurations. This necessitates a comprehensive approach to security, encompassing both device-level and network-level safeguards.
Need for Ongoing Security Research and Development
The continuous evolution of attack methods demands ongoing research and development in security technologies. Researchers must remain vigilant in identifying and mitigating new vulnerabilities. This includes exploring novel approaches to security, such as using hardware-based security mechanisms and developing more advanced intrusion detection systems. Furthermore, security research must keep pace with the ever-changing threat landscape.
Importance of Educating Users About IoT Security Best Practices
User education is critical in bolstering IoT security. Users need to be aware of potential risks and understand best practices for securing their devices and networks. Education programs should cover topics such as strong passwords, regular software updates, and recognizing suspicious activities.
Role of Government Regulations and Industry Standards
Government regulations and industry standards play a crucial role in shaping IoT security practices. Establishing clear guidelines and regulations for device manufacturers and users will help standardize security measures. This will foster a more secure and trustworthy IoT ecosystem. Additionally, collaborations between governments and industries are vital for developing and implementing effective security solutions.
Potential Future Trends in IoT DDoS Attacks
| Trend | Description |
|---|---|
| Increased Sophistication | Attacks will become more complex, leveraging multiple attack vectors and exploiting vulnerabilities in application layers. |
| Targeted Attacks | Attackers will focus on specific vulnerabilities in IoT devices, targeting critical infrastructure and services. |
| Automated Attacks | Attackers will utilize automated tools and techniques to launch and coordinate DDoS attacks more efficiently. |
| AI-powered Attacks | Attackers will leverage AI and machine learning to adapt their attacks in real-time and evade defenses. |
| Supply Chain Attacks | Attackers may target IoT device manufacturers to compromise devices before they reach consumers. |
| Blockchain-based Attacks | Attackers may exploit vulnerabilities in blockchain-based IoT security systems. |
Last Word
In conclusion, the increasing sophistication of DDoS attacks, particularly those leveraging IoT devices and DNS vulnerabilities like Mirai, poses a critical threat to internet stability and security. Mitigating these attacks requires a multi-faceted approach, including strengthening IoT security practices, improving DNS security, and deploying robust network defenses. Continued research and development, coupled with user education, are vital in addressing this evolving threat landscape.