Cloud NGFW for Azure privacy is crucial for securing sensitive data in the cloud. This deep dive explores the vital role of next-generation firewalls in safeguarding Azure deployments, covering everything from fundamental concepts to practical implementation and future trends. We’ll delve into privacy considerations, security features, and real-world case studies to understand how to leverage cloud NGFWs effectively in the Azure ecosystem.
Azure’s expansive cloud environment, while powerful, necessitates robust security measures to ensure data privacy and compliance. A cloud NGFW acts as a critical layer of defense, providing comprehensive protection against threats and vulnerabilities. This post examines the specifics of implementing and configuring these firewalls within Azure, offering practical insights for organizations seeking to enhance their security posture.
Introduction to Cloud NGFW for Azure Privacy
Cloud Next-Generation Firewalls (NGFWs) are essential security tools in the cloud environment, especially for platforms like Microsoft Azure. They act as the first line of defense against malicious threats and unauthorized access, extending the core security capabilities of Azure to the network level. This is particularly crucial for maintaining data privacy and compliance in the cloud. This blog post will delve into the benefits of using cloud NGFWs within Azure, explore their evolution, and compare different solutions available.Implementing a cloud NGFW within Azure provides a significant boost to security posture.
By combining the power of a dedicated firewall with Azure’s robust infrastructure, organizations can proactively protect sensitive data and applications from a wider array of threats, including sophisticated attacks. This enhanced security contributes to greater data privacy and compliance with industry regulations.
Key Benefits of Cloud NGFWs for Azure Privacy
Implementing a cloud NGFW in Azure offers several advantages for enhanced privacy. These benefits include:
- Improved Security Posture: NGFWs provide granular control over network traffic, enabling organizations to define and enforce security policies that align with their specific needs and regulatory requirements. This proactive approach reduces the risk of unauthorized access and data breaches.
- Enhanced Threat Protection: Cloud NGFWs are designed to detect and block sophisticated attacks, including advanced persistent threats (APTs), malware, and zero-day exploits. This proactive threat protection is crucial for maintaining data privacy in a dynamic threat landscape.
- Increased Compliance: Implementing an NGFW often helps organizations meet various compliance standards and regulations, including HIPAA, GDPR, and PCI DSS. This is because NGFWs can enforce security policies that align with these requirements, reducing the risk of non-compliance and associated penalties.
- Centralized Management: Cloud NGFWs often offer a centralized management console, simplifying administration and reducing the complexity of managing security across multiple locations and applications.
Evolution of Cloud NGFWs
Cloud NGFWs have evolved significantly from their predecessors. Early firewalls focused primarily on packet filtering. However, modern cloud NGFWs incorporate advanced features like application awareness, intrusion prevention systems (IPS), and advanced threat intelligence feeds, enabling a more comprehensive and dynamic security approach. This evolution reflects the increasing sophistication of cyber threats and the need for more robust security measures.
Their evolution is crucial for safeguarding sensitive data and systems in the ever-changing cloud environment.
Comparison of Cloud NGFW Solutions for Azure
Different vendors offer cloud NGFW solutions compatible with Azure. The following table provides a comparative overview, focusing on key features and functionalities:
| Vendor | Solution Name | Key Features | Pricing Model |
|---|---|---|---|
| Vendor A | Solution A | Advanced threat intelligence, application control, and deep packet inspection. Integrates seamlessly with Azure Security Center. | Subscription-based, tiered pricing. |
| Vendor B | Solution B | Comprehensive security features, including user and entity behavior analytics (UEBA), and strong support for Azure Active Directory integration. | Pay-as-you-go model, with options for dedicated resources. |
| Vendor C | Solution C | Focuses on ease of deployment and management, with pre-configured templates for common Azure workloads. | Fixed monthly fees, based on throughput. |
This comparison highlights the different features and pricing models offered by various vendors, enabling organizations to choose the solution best suited to their specific needs and budget. Understanding these nuances is crucial for selecting the right security solution for a cloud environment.
Securing your Azure cloud environment with a next-generation firewall (NGFW) is crucial for privacy. Knowing how to manage administrator privileges in group chats on platforms like Facebook Messenger can surprisingly offer valuable insights into securing data. Understanding these kinds of group chat permissions is a good starting point for understanding broader data security strategies, like the best practices for cloud NGFW in Azure.
For more details on Facebook Messenger administrator privileges in group chats, check out this helpful guide: facebook messenger administrator privileges group chat. Ultimately, the lessons from social media security can help reinforce the need for a robust cloud NGFW solution for Azure.
Privacy Considerations in Azure Cloud NGFWs
Azure Cloud Network Gateways (NGFWs) are crucial for securing virtual networks in Azure. However, deploying these solutions necessitates a strong understanding of privacy implications, particularly concerning data sovereignty and compliance. Implementing Azure NGFWs effectively requires meticulous consideration of these factors to ensure data security and meet regulatory mandates.Protecting sensitive data within Azure deployments is paramount. Cloud NGFWs, while providing robust security, must be configured and managed with a focus on data privacy.
This necessitates understanding the specific privacy concerns inherent in cloud-based solutions and implementing best practices to mitigate risks.
Data Sovereignty and Compliance
Data sovereignty dictates that data must be stored and processed within a specific geographical region, often mandated by national laws or regulations. Compliance with regulations like GDPR and HIPAA is equally crucial. Azure’s global infrastructure allows for the deployment of NGFWs to support diverse data sovereignty needs. Azure offers various compliance certifications, like ISO 27001, to demonstrate adherence to industry best practices, thus reassuring users of the security and privacy of their data.
Addressing Privacy Concerns with Cloud NGFWs
Cloud NGFWs can directly address privacy concerns by implementing robust access controls. These controls restrict data access to authorized personnel, thereby limiting potential breaches. NGFWs can also utilize encryption techniques to safeguard sensitive data in transit and at rest. This dual approach—access control and encryption—is essential for mitigating privacy risks in cloud environments.
Encryption and Access Controls
Encryption is fundamental to protecting sensitive data both in transit and at rest. Cloud NGFWs utilize various encryption methods, such as Transport Layer Security (TLS) for encrypted communication channels. Secure storage of encryption keys is critical and must be implemented with meticulous attention to security best practices. Access controls are vital in limiting access to data and resources. These controls include granular permissions and multi-factor authentication (MFA), which significantly reduce the risk of unauthorized access.
Effective encryption and access controls, implemented correctly, are cornerstones of robust privacy protections.
Industry-Specific Privacy Regulations
Numerous industry-specific regulations dictate how sensitive data must be handled and protected. For example, GDPR (General Data Protection Regulation) mandates stringent data protection measures for European Union citizens’ data. HIPAA (Health Insurance Portability and Accountability Act) in the US dictates strict regulations for protecting healthcare information. Cloud NGFWs can help organizations achieve compliance with these regulations by providing a secure and controlled environment for handling sensitive data.
This includes implementing the necessary access controls, encryption protocols, and logging mechanisms to demonstrate compliance.
Potential Vulnerabilities in Cloud NGFW Configurations
Improper configuration of cloud NGFWs can introduce vulnerabilities that compromise privacy. Examples include weak passwords, inadequate logging mechanisms, and insufficient monitoring. A thorough understanding of NGFW functionalities, combined with careful configuration and regular security audits, helps mitigate these risks. The importance of proactive security measures cannot be overstated. Regular updates and patches for the NGFW software are essential to address known vulnerabilities.
Implementing secure configurations and employing robust security protocols are key to maintaining data privacy.
Implementing Cloud NGFW for Azure Privacy
Protecting sensitive data in the cloud is paramount. Azure Network Security Groups (NSGs) and Azure Firewall are crucial components for achieving this. Implementing a Cloud NGFW (Next Generation Firewall) within the Azure environment provides a layered security approach, enhancing privacy and bolstering overall data protection. This involves a meticulous deployment process and strategic configuration of security policies.Implementing a cloud NGFW in Azure allows for granular control over network traffic, bolstering privacy and security by creating a robust defense perimeter.
This proactive approach mitigates risks associated with unauthorized access and malicious activities.
Deploying a Cloud NGFW in an Azure Environment, Cloud ngfw for azure privacy
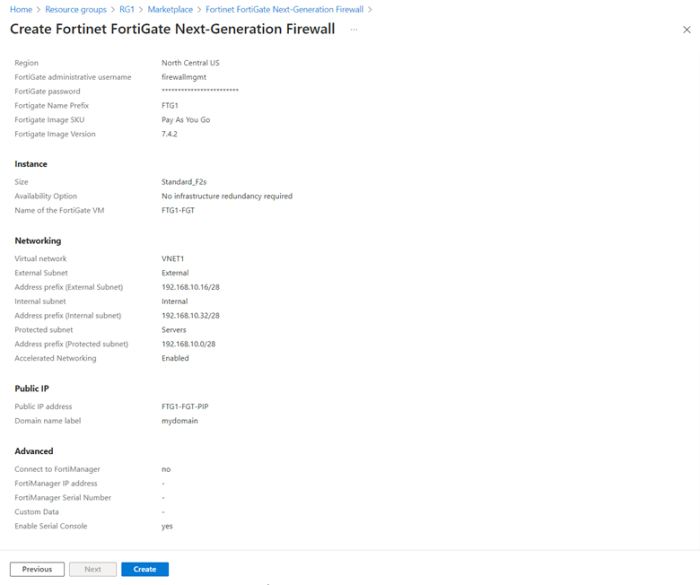
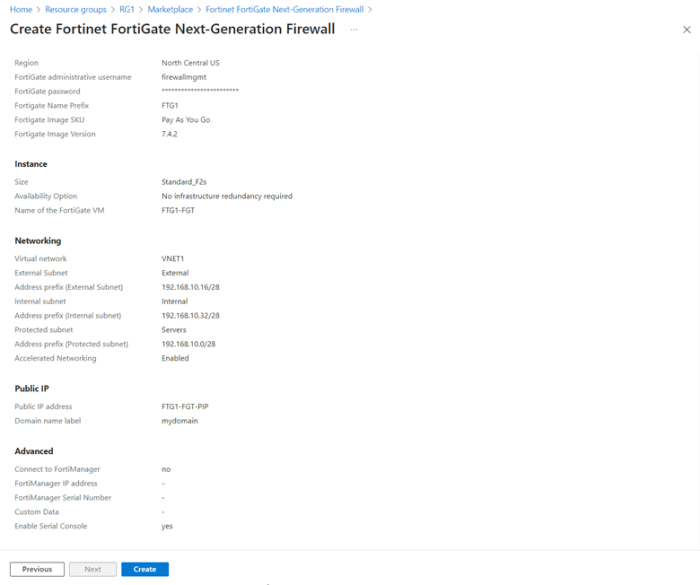
The deployment process involves several key steps. First, select the appropriate NGFW service provider and ensure compatibility with Azure’s infrastructure. Next, define the deployment location and resources within Azure. This includes the virtual network and subnets where the NGFW will operate. Finally, configure the NGFW appliance, including necessary security policies and rules.
This process often involves leveraging Azure Resource Manager templates for automation, minimizing manual configuration errors.
Configuring Security Policies
Security policies are the cornerstone of effective network security. They define the rules that govern network traffic flow, dictating which traffic is allowed and which is blocked. Defining these policies requires meticulous consideration of permitted traffic types, network protocols, and source/destination IP addresses. Using Azure Firewall policies allows for the application of specific rules based on application protocols, ports, and user identities.
Network Segmentation and Access Control
Network segmentation isolates different parts of the network, limiting the impact of security breaches. Azure allows for segmentation through virtual networks and subnets. Access control policies are implemented to restrict access to specific resources, based on user roles, and enforcing the principle of least privilege. Using network security groups (NSGs) allows fine-grained control over inbound and outbound traffic at the subnet level.
Integrating with Azure Security Features
Integrating the cloud NGFW with Azure’s security features enhances overall protection. Azure Security Center provides centralized management and threat detection capabilities. Integrating the NGFW with Azure Monitor enables real-time monitoring of network traffic and security events. Integration with Azure Active Directory allows for authentication and authorization based on user identities.
Role of Threat Intelligence in Maintaining Privacy
Threat intelligence plays a critical role in maintaining privacy. Utilizing up-to-date threat intelligence feeds provides the NGFW with insights into emerging threats. This information enables the NGFW to proactively block malicious traffic and adapt security policies to counter new vulnerabilities. Regularly updating threat intelligence databases is crucial to maintain effectiveness against evolving threats. Threat intelligence feeds from reputable sources are paramount to effective protection.
For instance, a real-world example includes a bank updating their NGFW’s threat intelligence to identify and block a newly discovered malware targeting financial institutions.
Security Features and Benefits
Cloud Next-Generation Firewalls (NGFWs) in Azure offer a robust suite of security features that significantly enhance the privacy and security posture of your Azure environment. These features are designed to proactively identify and mitigate threats, preventing data breaches and unauthorized access while aligning with stringent privacy regulations. This section delves into the key security features and their implications for maintaining Azure privacy.Various security features are available from different providers, each with unique strengths and weaknesses.
Understanding these nuances is crucial in selecting the appropriate NGFW for your specific Azure deployment needs.
Intrusion Prevention System (IPS)
Intrusion Prevention Systems (IPS) in cloud NGFWs actively monitor network traffic for malicious patterns and anomalies. These systems are crucial in detecting and preventing attacks like denial-of-service (DoS) and zero-day exploits, thereby enhancing Azure privacy by blocking threats at the network level. The efficacy of an IPS depends on the quality of its threat intelligence database and its ability to adapt to evolving threats.
Azure’s cloud Next-Generation Firewall (NGFW) is crucial for privacy, especially considering recent security breaches. The recent CBI crackdown on technology support fraud involving Amazon and Microsoft in India ( amazon microsoft india cbi crackdown technology support fraud ) highlights the importance of robust security measures. Strong cloud NGFWs are essential to protect sensitive data and maintain privacy in the face of such incidents.
This underscores the need for robust security solutions in cloud environments.
Web Application Firewall (WAF)
Cloud NGFWs often include Web Application Firewalls (WAFs) to protect web applications from common attacks like cross-site scripting (XSS) and SQL injection. WAFs inspect incoming web traffic and block malicious requests, ensuring the confidentiality and integrity of data processed by your applications. This feature is particularly important for protecting sensitive data exposed through web interfaces. Different WAF providers offer varying levels of protection, such as custom rules, signature-based detection, and anomaly detection.
Threat Intelligence Integration
Modern cloud NGFWs integrate with various threat intelligence feeds, providing real-time updates on emerging threats. This integration enhances the effectiveness of the IPS and WAF by incorporating the latest threat information to proactively block known and unknown attacks. This continuous threat intelligence monitoring enhances Azure privacy by adapting to the ever-changing threat landscape. The quality and comprehensiveness of the threat intelligence feeds directly impact the accuracy and responsiveness of the NGFW.
For example, a provider that incorporates data from multiple reputable sources, including industry research and security advisories, is more likely to detect and mitigate emerging threats.
Data Breach Prevention
Cloud NGFWs act as a critical first line of defense against data breaches by preventing unauthorized access to sensitive data. By blocking malicious traffic and identifying suspicious activity, cloud NGFWs can prevent the compromise of confidential information, which directly contributes to upholding Azure privacy. Comprehensive security configurations, including robust access controls and multi-factor authentication (MFA), combined with cloud NGFWs, create a strong security posture.
Improved Security Posture
Cloud NGFWs in Azure improve the overall security posture by centralizing security controls and simplifying management. They provide a unified platform for managing network security, application security, and threat intelligence, resulting in a more streamlined and efficient security approach. This centralization of security allows for better visibility and control over network traffic, ultimately enhancing Azure privacy by reducing the attack surface.
Centralized management also allows for easier compliance with security standards and regulations.
Case Studies and Use Cases
Cloud Network Firewalls (NGFWs) in Azure are rapidly gaining traction as a crucial component for enhancing privacy in various organizational settings. Their ability to enforce granular security policies, coupled with the scalability and flexibility of the Azure cloud platform, offers compelling advantages for businesses seeking to protect sensitive data while optimizing operational efficiency. This section delves into real-world examples and use cases, highlighting how cloud NGFWs in Azure contribute to meeting privacy compliance requirements.Organizations across diverse sectors are increasingly recognizing the importance of implementing robust security measures to safeguard customer data and maintain regulatory compliance.
Cloud NGFWs in Azure provide a dynamic and adaptable solution to these challenges, offering a secure and scalable architecture to manage network traffic, enforce access controls, and mitigate threats effectively.
Real-World Examples of Enhanced Privacy
Cloud NGFWs in Azure are employed by numerous organizations to enhance data privacy. For example, a financial institution leveraging Azure NGFWs can implement strict access controls to customer accounts, ensuring that only authorized personnel can access sensitive financial information. This layered security approach significantly reduces the risk of data breaches and strengthens the institution’s commitment to protecting customer privacy.
Similarly, a healthcare provider can utilize cloud NGFWs to comply with HIPAA regulations, safeguarding patient data and ensuring secure access to electronic health records.
Specific Use Cases Demonstrating Advantages
Several specific use cases showcase the advantages of cloud NGFWs in Azure. One such use case involves a retail company that utilizes cloud NGFWs to secure its e-commerce platform. By implementing granular access controls, the company can restrict access to sensitive customer data and payment information, ensuring compliance with data privacy regulations like PCI DSS. This proactive approach significantly reduces the likelihood of unauthorized access and financial fraud.
Another example involves a manufacturing company that utilizes cloud NGFWs to protect its industrial control systems (ICS) from cyber threats. This proactive measure helps maintain operational security and safeguards sensitive manufacturing data, critical for production processes.
Compliance Requirements in Different Industry Sectors
Cloud NGFWs in Azure play a pivotal role in meeting privacy compliance requirements across various industry sectors. For instance, in the healthcare sector, cloud NGFWs help healthcare providers comply with HIPAA regulations by securing sensitive patient data. Likewise, in the financial sector, cloud NGFWs enable financial institutions to meet stringent regulations such as PCI DSS, ensuring the protection of customer financial information.
Furthermore, in the education sector, cloud NGFWs can safeguard student data and ensure compliance with relevant data privacy laws.
Deployment Model Comparison
| Deployment Model | Benefits | Drawbacks |
|---|---|---|
| Hybrid | Combines on-premises and cloud resources, providing flexibility and control. | Can be complex to manage and maintain, potentially requiring specialized expertise. |
| Native Cloud | Fully integrated with Azure, offering scalability and ease of management. | Reliance on cloud infrastructure, potential vendor lock-in. |
| Managed Service | Simplified management, minimal infrastructure overhead. | Limited customization options, potential for vendor dependence. |
The table above summarizes the advantages and disadvantages of different deployment models, allowing for a comparative analysis.
Cloud NGFWs for Azure privacy are crucial, ensuring secure data transmission. A key aspect of this is understanding how virtual machine series NGFWs and IS5 communications, like those detailed in vm series ngfw and is5 communications raptor , impact overall security. Ultimately, robust cloud NGFW solutions are essential for maintaining Azure privacy.
Cloud NGFW Contribution to Improved Regulatory Compliance
Cloud NGFWs significantly contribute to improved regulatory compliance by enabling organizations to implement granular security policies. For instance, by enforcing strict access controls and monitoring network traffic, cloud NGFWs in Azure help organizations adhere to data privacy regulations like GDPR, HIPAA, and PCI DSS. These policies, combined with the scalability and reliability of the Azure cloud platform, enhance an organization’s ability to meet its regulatory obligations.
This proactive approach ensures that sensitive data remains protected and that organizations avoid potential penalties associated with non-compliance.
“A robust cloud NGFW provides a critical layer of security, enabling organizations to effectively address privacy concerns and regulatory mandates.”
Future Trends and Innovations
Cloud NGFWs are rapidly evolving, driven by the increasing complexity of cloud environments and the need for enhanced security. These advancements are not only reshaping the landscape of cloud security but also significantly impacting how Azure privacy is maintained and enforced. The future of cloud security hinges on the ability to adapt to emerging trends and integrate innovative technologies.The ongoing evolution of cloud-native security architectures, combined with the continuous sophistication of cyber threats, necessitates a proactive approach to future-proofing cloud infrastructure.
This involves not only anticipating future needs but also adapting to current challenges to ensure robust and reliable security measures.
Emerging Trends in Cloud NGFWs
Cloud NGFWs are evolving beyond simple perimeter defenses. New trends focus on advanced threat detection, dynamic policy enforcement, and seamless integration with other cloud security services. The integration of AI and machine learning is a key driver of these developments, enabling more sophisticated threat analysis and automated response mechanisms.
Impact on Azure Privacy
The adoption of these trends directly affects Azure privacy. Cloud NGFWs need to be designed and implemented in a way that respects user data privacy while maintaining high security standards. This necessitates a deep understanding of Azure’s privacy policies and compliance requirements, which must be incorporated into the NGFW design and operational procedures. Furthermore, rigorous auditing and monitoring mechanisms are crucial for ensuring adherence to privacy regulations.
AI and Machine Learning Enhancements
AI and machine learning are transforming cloud NGFW functionalities. These technologies can analyze massive datasets of network traffic in real-time, identify anomalies, and proactively block malicious activity. For instance, AI can be used to detect and respond to zero-day threats, while machine learning algorithms can adapt to changing threat patterns and improve the accuracy of threat detection over time.
This enhances the overall security posture while minimizing false positives and ensuring that legitimate user activity is not interrupted.
Future Direction of Azure Cloud Security Services
Azure is committed to providing comprehensive cloud security services, and NGFWs are a crucial component of this strategy. Future enhancements will likely focus on automation, integration with other Azure services, and a more proactive security posture. This could involve tightly integrating NGFWs with Azure Identity and Access Management (IAM) services to provide more granular control over access permissions.
Furthermore, advancements in security information and event management (SIEM) capabilities will likely allow for more sophisticated threat hunting and analysis within Azure environments.
Zero-Trust Architectures in Cloud NGFWs
Zero-trust architectures are becoming increasingly important in the future of cloud NGFWs. The zero-trust model assumes that no user or device is inherently trusted and mandates continuous verification of identities and access requests. This approach will be critical in cloud environments, where access to resources is dynamic and distributed. Cloud NGFWs will need to be capable of supporting and enforcing these policies, enabling fine-grained control over access based on context and intent.
Zero trust allows for a more granular and dynamic approach to security, enhancing overall privacy. A robust zero-trust framework is vital for securing sensitive data in multi-tenant environments.
Cloud NGFW Architecture Diagrams
Cloud Network Firewalls (NGFWs) deployed in Azure environments offer a robust and flexible security solution. Understanding their architecture is crucial for effective implementation and management. This section dives into the design diagrams, components, and integrations with Azure resources.A well-designed cloud NGFW architecture in Azure is critical for maintaining security and performance. It must effectively segment networks, control traffic flow, and integrate seamlessly with other Azure services.
Proper configuration and monitoring are essential to ensure optimal security posture.
Cloud NGFW Architecture in Azure
The architecture of a cloud NGFW in Azure typically involves several key components. These components work together to provide a secure and scalable network infrastructure. The deployment model and specific needs will influence the exact components and their interconnections.
Components of a Cloud NGFW in Azure
The core components of a cloud NGFW in Azure typically include a virtual appliance residing within a Virtual Network (VNet), integrated with Azure Load Balancers, and potentially utilizing Azure Storage for logs and configurations.
- Virtual Network (VNet): The VNet acts as the foundational network infrastructure where the NGFW appliance resides. It provides the virtualized network environment for traffic routing and isolation. The VNet should be appropriately segmented to isolate different zones of the application and network infrastructure.
- Cloud NGFW Appliance: This is the core component, acting as the central security gateway. It performs deep packet inspection, stateful firewalling, and other security functions. The appliance is typically a virtual machine (VM) running NGFW software, deployed within the VNet.
- Azure Load Balancer: The Load Balancer distributes incoming traffic to the NGFW appliance, ensuring high availability and performance. It can also perform additional tasks such as health checks and SSL termination.
- Azure Storage Account: Storage accounts store logs, configuration data, and other operational information generated by the NGFW. This allows for efficient monitoring, auditing, and analysis of network traffic.
- Azure Security Center: This Azure service provides centralized security management and monitoring for the entire Azure environment. Integration with Security Center allows for automated threat detection, proactive security posture assessments, and security alerts relating to the NGFW.
Integration with Azure Resources
A key aspect of cloud NGFW deployments is the seamless integration with other Azure resources.
- Virtual Networks (VNet): The NGFW appliance resides within a Virtual Network, ensuring traffic flows through the NGFW for inspection and control.
- Storage Accounts: Data generated by the NGFW, such as logs and configuration information, is stored in Azure Storage accounts for long-term retention and analysis.
- Azure Security Center: The NGFW is often integrated with Azure Security Center for centralized security management, threat detection, and compliance reporting.
Architectural Options
Different deployment scenarios may require various architectural approaches. The following table summarizes several options.
| Architecture | Description |
|---|---|
| Single NGFW Appliance | A single NGFW appliance is deployed within a VNet to provide basic security for the application network. |
| Multi-NGFW Appliance with High Availability | Multiple NGFW appliances are deployed in a high-availability configuration using Azure Load Balancers to ensure redundancy and resilience. |
| NGFW with Azure Firewall integration | The NGFW is integrated with Azure Firewall for enhanced security and management, particularly beneficial for perimeter protection. |
Detailed Explanation of Components
A detailed explanation of each component helps to understand their function and interaction.
- Virtual Network (VNet): Provides a virtualized network for isolating and managing network traffic. The VNet provides a secure and controlled environment for the NGFW appliance.
- Cloud NGFW Appliance: A dedicated virtual machine running NGFW software, providing deep packet inspection, firewall rules enforcement, and other security services. Its role is crucial in filtering and controlling network traffic.
End of Discussion
In conclusion, cloud NGFWs offer a powerful solution for bolstering Azure privacy. We’ve explored the core principles, implementation strategies, and future trends. By understanding the importance of data sovereignty, implementing robust security features, and leveraging threat intelligence, organizations can significantly enhance their Azure security posture. The future of cloud security is inextricably linked to the evolution of cloud NGFWs, and this post provides a comprehensive guide to navigate this exciting landscape.