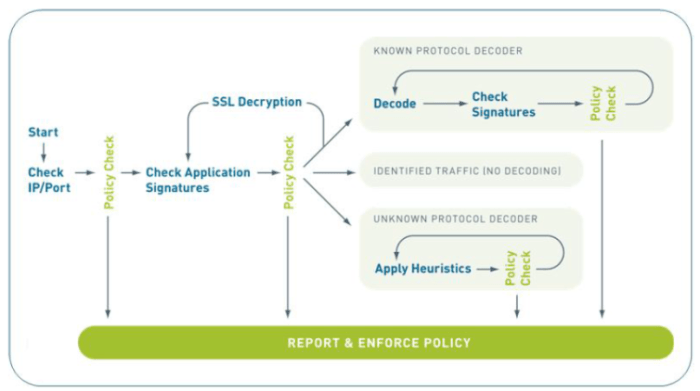
Application usage and threat report provides a comprehensive analysis of how applications are used and the potential security risks associated with that usage. This report delves into various metrics of application use, from frequency and duration to user patterns. It also identifies potential threats, from common vulnerabilities to unauthorized access. Understanding these patterns is crucial for proactive security measures.
The report will Artikel a detailed structure for creating a comprehensive report, including data analysis, visualization techniques, and security recommendations. We’ll also explore illustrative scenarios to demonstrate how to interpret application usage patterns in real-world contexts, showcasing how these patterns can reveal malicious activities and unauthorized access attempts. Finally, the report will offer practical advice on presenting the findings effectively to stakeholders.
Defining Application Usage
Understanding application usage is crucial for optimizing performance, identifying potential threats, and ensuring user satisfaction. A deep dive into application usage metrics reveals valuable insights into how users interact with software, highlighting areas for improvement and potential vulnerabilities. This analysis goes beyond simple counts, examining patterns, durations, and user segments to gain a comprehensive understanding.
Application Usage Metrics
Application usage metrics provide quantitative data about how users interact with software. These metrics encompass a wide range of factors, from the frequency of use to the duration of sessions and the specific features utilized. Key metrics include the number of users, average session duration, frequency of logins, and the number of errors encountered. These metrics are essential for performance analysis, identifying bottlenecks, and ensuring a positive user experience.
Methods for Collecting Application Usage Data
Various methods exist for gathering application usage data. Log files, application performance monitoring (APM) tools, and user feedback surveys are common approaches. Log files record events and activities within the application, providing a detailed history of user interactions. APM tools offer real-time insights into application performance, including response times and resource consumption. Surveys provide valuable qualitative data, allowing users to express their opinions and experiences.
Combining these methods offers a comprehensive picture of application usage.
Application Usage Patterns
Application usage patterns reveal how users interact with the software over time. These patterns include frequency, duration, and specific user segments. Frequency refers to how often users access the application. Duration tracks the length of user sessions, while user segments categorize users based on their usage patterns (e.g., frequent users, infrequent users). Analyzing these patterns helps identify optimal resource allocation and user experience improvements.
Categorizing and Classifying Application Usage
Categorizing and classifying application usage is crucial for meaningful analysis. Applications can be categorized by function, user type, or platform. This categorization allows for targeted analysis, focusing on specific aspects of application usage. Classification, based on usage patterns, allows for deeper understanding of user behavior and preferences, enabling personalized recommendations and tailored experiences.
My latest application usage and threat report is looking a little concerning. While I’m digging into the data, it’s a good time to grab some spare cables, power banks, and more at Amazon’s 1-day Anker sale. grab some spare cables power banks and more at amazons 1 day anker sale These deals will definitely come in handy while I troubleshoot these unusual activity spikes.
Hopefully, after I get my Anker essentials, the report will show a clearer picture of what’s happening.
Application Usage Metrics Table
| Metric | Description | Example Value |
|---|---|---|
| Number of Users | Total number of users accessing the application | 10,000 |
| Average Session Duration | Average time spent by a user within the application | 30 minutes |
| Login Frequency | Number of login attempts per user per day | 2-3 times |
| Error Rate | Percentage of sessions resulting in errors | 1% |
| Feature Usage | Percentage of users utilizing a specific feature | 80% |
Identifying Potential Threats: Application Usage And Threat Report
Application usage patterns are not just about how often a program is run; they’re a crucial window into potential security threats. Understanding normal behavior allows us to quickly spot deviations that might indicate malicious activity. This analysis of unusual activity is key to preventing breaches and safeguarding sensitive data.
Common Application Threats
Understanding typical application threats is the first step in recognizing suspicious behavior. These threats range from simple misuse to sophisticated attacks. They can exploit weaknesses in the application itself or in the way users interact with it. The goal is to detect these threats before they cause significant damage.
- Unauthorized Access Attempts: These involve attempts to log in with incorrect credentials or access restricted features. This could be a simple password-guessing attack or a more sophisticated brute-force attempt. Detecting repeated failed login attempts, especially from unusual IP addresses, is vital for immediate response.
- Malware Infections: Malicious software can be disguised within legitimate applications or introduced through seemingly harmless downloads. Unexpected file modifications, unusual network traffic patterns, or the appearance of unknown processes are indicators of possible malware infections.
- Data Exfiltration: This involves unauthorized copying or transfer of sensitive data. Monitoring for unusual data transfers, especially large volumes or to unexpected locations, is essential. This could include data being sent to external servers or copied to removable drives.
- Denial-of-Service Attacks: These attacks aim to overload the application, rendering it unusable. Unusual spikes in traffic from a single source or a concentrated group of sources might indicate such an attack.
- Insider Threats: Employees with authorized access can also pose a significant risk. Changes in access patterns or unusually high data access frequency by a specific user may be indicators of an insider threat.
Security Vulnerabilities Exposed Through Usage Patterns
Application usage patterns can expose inherent security vulnerabilities. For example, a consistent pattern of high-volume data access might indicate a potential flaw in access controls.
Recent application usage and threat reports are interesting, especially considering Pfizer’s CEO’s recent comments on living with COVID-19. Pfizer’s CEO’s view on the virus’s long-term impact might influence future development strategies, impacting how we approach application security. This could potentially mean a shift in how we analyze and react to emerging threats in the application landscape.
- Insufficient Access Control: If applications lack adequate access controls, unauthorized users could potentially gain access to sensitive data. For example, if an employee can access data they are not authorized to view, this could be a vulnerability.
- Broken Authentication: Applications with weak authentication mechanisms are vulnerable to unauthorized access. This could manifest as easy password cracking or weak session management.
- Sensitive Data Exposure: If applications do not adequately protect sensitive data, attackers could gain access to confidential information, like user credentials or financial data.
Unusual or Suspicious Application Usage
Deviations from normal usage patterns are often the first signs of potential threats.
- Unusual login locations: Users logging in from unexpected geographical locations could signal a compromise or an attempt at unauthorized access.
- High-frequency data access: Sudden surges in data access from a single user or group could indicate attempts at data exfiltration.
- Uncharacteristic file modifications: Changes to files or directories outside of typical usage patterns can indicate malicious activity, such as malware installation or data tampering.
Unauthorized Access and Misuse
Unauthorized access and misuse of applications can have severe consequences, from data breaches to system disruptions.
- Unauthorized access to sensitive data: Unauthorized users accessing sensitive data can compromise confidentiality and potentially lead to legal issues.
- Application misuse for malicious purposes: Applications can be used to launch attacks against other systems, leading to broader security implications.
- Unauthorized access to user accounts: Unauthorized access to user accounts can lead to identity theft or other security breaches.
Potential Threats and Indicators
The following table summarizes potential threats and their associated indicators:
| Potential Threat | Indicators |
|---|---|
| Unauthorized Access | Failed login attempts, unusual login locations, suspicious IP addresses, unauthorized data access. |
| Malware Infection | Unexpected file modifications, unusual network traffic, appearance of unknown processes, system instability. |
| Data Exfiltration | Large-volume data transfers, data transfer to unexpected locations, unusual data access patterns. |
| Denial-of-Service Attack | Unusual spikes in traffic from a single source, high volume of requests, system slowdowns. |
| Insider Threat | Unusual data access frequency by a specific user, changes in access patterns, access to unauthorized data. |
Report Structure and Content
Crafting a comprehensive application usage and threat report requires a structured approach to ensure clarity and actionable insights. This structure allows for easy understanding of the application’s performance, potential risks, and areas needing attention. A well-organized report fosters better communication among stakeholders and supports informed decision-making.
Report Template
This template provides a framework for a comprehensive report, enabling a clear presentation of application usage and potential threats. The structure prioritizes chronological data analysis and incorporates sections for detailed threat assessment.
Key Sections and Content
A well-structured report comprises several key sections, each contributing to a holistic understanding of the application’s performance and security posture. The following table Artikels these sections and their corresponding content.
| Section | Content Description |
|---|---|
| Executive Summary | A concise overview of the report’s key findings, highlighting application usage trends and identified threats. It should summarize the main points and provide a high-level understanding for non-technical stakeholders. |
| Application Overview | Provides context for the application, including its purpose, target audience, and key functionalities. This section should include relevant details about the application’s architecture, development tools, and current deployment environments. |
| Usage Analysis | Presents a detailed analysis of application usage patterns. This section should include graphs, charts, and tables demonstrating user activity, frequency of access, and peak usage times. Data should be presented chronologically, showing trends over specific timeframes. |
| Threat Identification | Identifies potential security threats and vulnerabilities affecting the application. This section should include a categorized list of potential risks, detailing their potential impact and likelihood of occurrence. Examples of threats should include known vulnerabilities, malicious activity, and configuration errors. |
| Security Assessment | Evaluates the effectiveness of existing security controls and procedures. This section should include a detailed review of current security measures and their effectiveness. Comparisons to industry best practices and standards should be included to highlight potential gaps or weaknesses. |
| Risk Mitigation Strategies | Artikels actionable steps for mitigating identified risks and vulnerabilities. This section should propose specific solutions to address the identified threats, providing cost estimates and timelines for implementation. |
| Chronological Record of Usage | Presents a timeline of application usage, highlighting key events, periods of high or low activity, and any significant changes in usage patterns. This section provides context and allows for the correlation of usage with potential threats. It should include detailed time stamps and descriptions for each event. |
| Appendices | Provides supplementary data, such as raw data sets, technical specifications, and supporting documentation. |
Chronological Record of Usage
A chronological record provides a valuable perspective on application usage patterns over time. It allows analysts to identify trends, correlations, and potential anomalies in user activity. This approach is essential for pinpointing when certain events or usage patterns might correlate with security incidents. The data should be meticulously tracked and categorized for accurate analysis.
Application usage and threat reports are crucial for security, but sometimes a bit dry. Think about the recent buzz around the League of Legends Summoner’s Cup, featuring Tiffany & Co. collaborations – league of legends summoners cup tiffany and co is generating tons of data about player interactions and app activity. Analyzing this data can provide valuable insights into potential security threats, helping improve app security practices.
A well-structured timeline can identify correlations between periods of high user activity and potential security threats.
Example: A spike in user login attempts from a specific IP address during a period of increased application usage could be indicative of a possible attack.
Data Analysis and Visualization
Unveiling insights from the deluge of application usage and threat data requires a strategic approach to analysis and visualization. Simply accumulating raw data is insufficient; transforming it into actionable intelligence is paramount. This section delves into the methodologies for extracting meaningful patterns and trends from collected information, and presents visually compelling representations for enhanced understanding.Effective data analysis and visualization are crucial for interpreting application usage patterns and identifying potential threats.
Transforming raw data into easily digestible and insightful visualizations empowers stakeholders to rapidly grasp key trends, allowing for proactive responses to emerging issues.
Analyzing Collected Application Usage Data
Analyzing collected application usage data involves a multi-faceted process. Initial steps include cleaning and preparing the data, addressing missing values, and transforming data into a suitable format for analysis. This ensures the accuracy and reliability of subsequent analysis. Normalization and standardization techniques can be employed to mitigate the impact of varying scales and units, thereby ensuring accurate comparisons.
Feature engineering plays a crucial role in extracting relevant information and creating new features for analysis, which could include user activity duration, frequency of logins, and location of usage.
Identifying Trends and Patterns in Application Usage
Identifying trends and patterns in application usage data often involves employing statistical methods and machine learning algorithms. Techniques like time series analysis can uncover cyclical or seasonal patterns in application usage. Correlation analysis helps determine the relationships between different variables and usage metrics. Clustering algorithms can group similar user behaviors, providing insights into distinct user segments and their respective application usage patterns.
Regression analysis allows for predicting future usage based on identified trends.
Visualizations for Application Usage Data
Visual representations are instrumental in conveying complex data in a digestible format. Choosing the appropriate visualization type is crucial for effectively communicating insights. Effective visualizations can highlight key trends and patterns, facilitating a deeper understanding of application usage and potential threats. Different visualization types suit diverse reporting needs, enabling tailored presentations for various stakeholders.
Examples of Effective Visualizations
Line charts effectively depict trends over time. For example, a line chart showcasing the daily active users of an application can highlight seasonal variations or sudden spikes in usage. Bar charts are suitable for comparing different categories, such as the usage of different features or functionalities within an application. Scatter plots can reveal correlations between variables. A scatter plot showing the relationship between login frequency and user session duration could reveal insights into user behavior.
Heatmaps are useful for visualizing the distribution of data across categories, providing a summary of usage patterns across various features or functionalities. For instance, a heatmap of user activity across different application modules can highlight areas of high usage and potential bottlenecks.
Table Comparing Visualization Types
| Visualization Type | Description | Suitability for Reports |
|---|---|---|
| Line Chart | Displays trends over time. | Excellent for showing usage trends, identifying seasonal patterns, and highlighting sudden changes. |
| Bar Chart | Compares different categories. | Ideal for comparing usage across features, user groups, or time periods. |
| Scatter Plot | Shows the relationship between two variables. | Useful for identifying correlations between usage patterns and other factors. |
| Heatmap | Visualizes data distribution across categories. | Effective for summarizing usage across different modules or functionalities. |
Security Recommendations
Securing application usage data is paramount. This section details crucial security recommendations, based on the identified threats, to mitigate potential risks and enhance the overall security posture of the application. Effective security measures are not just about reacting to threats but also about proactively preventing them. Implementing these recommendations will strengthen the application’s defenses and safeguard user data.
Threat Mitigation Strategies
Implementing robust security measures requires a proactive approach. These strategies focus on reducing vulnerabilities and improving the overall security posture. A multi-layered approach that combines technical controls, operational procedures, and user awareness is crucial for effective threat mitigation.
- Input Validation and Sanitization: Thorough validation and sanitization of user inputs are essential to prevent malicious code injection attacks. This includes checking the type, length, and format of user-provided data. For example, if a form requires an email address, validate that it adheres to a standard email format before processing it. Failing to sanitize user inputs can expose the application to vulnerabilities like SQL injection and cross-site scripting (XSS).
- Authentication and Authorization: Strong authentication mechanisms, such as multi-factor authentication (MFA), should be implemented to verify user identities. Authorization controls should restrict access to sensitive data and functionalities based on user roles and permissions. For instance, administrators should have access to features that regular users do not. This approach prevents unauthorized access and data breaches.
- Regular Security Audits and Penetration Testing: Regular security audits and penetration testing are critical for identifying and addressing vulnerabilities before they are exploited. These assessments should evaluate the application’s security controls and identify potential weaknesses. Penetration testing simulates real-world attacks to determine the application’s resilience against malicious attempts. Examples include simulated SQL injection attacks to identify vulnerabilities in data handling.
Data Encryption and Protection
Data encryption is crucial for protecting sensitive information both in transit and at rest. Implementing robust encryption protocols will help prevent unauthorized access and ensure data confidentiality. Data loss prevention (DLP) measures should be incorporated to prevent sensitive data from leaving the organization’s control.
- Data Encryption in Transit: Employing secure protocols like HTTPS for all communication between the application and users is critical. This ensures that sensitive data transmitted over the network is encrypted and protected from interception. For example, encrypting communication between the application server and the user’s browser prevents man-in-the-middle attacks.
- Data Encryption at Rest: Encrypting data stored in databases and other storage systems is essential to protect data from unauthorized access if the storage systems are compromised. This practice protects sensitive information, even if the storage systems are breached.
- Data Loss Prevention (DLP): Implement DLP solutions to monitor and prevent sensitive data from leaving the organization’s control. This can include content filtering, data masking, and access controls to prevent sensitive data from being transmitted or stored in unauthorized locations.
Application Security Best Practices
Implementing robust application security best practices is crucial to protect the application and the users’ data. These practices ensure that the application is secure throughout its lifecycle.
- Secure Coding Practices: Adhering to secure coding practices during the development phase can prevent many vulnerabilities from entering the application. These practices include input validation, secure use of libraries and frameworks, and avoiding common coding errors. For example, using parameterized queries to prevent SQL injection attacks is a best practice.
- Regular Updates and Patches: Regularly updating the application with the latest security patches is crucial. This ensures that known vulnerabilities are addressed promptly. Keeping the application up-to-date is crucial for maintaining its security posture.
- User Awareness Training: Educating users about security risks and best practices can significantly reduce the risk of phishing attacks and other social engineering attempts. Providing training to users about the application’s security policies and procedures is vital.
Security Recommendations Table
| Recommendation | Corresponding Threat | Impact of Implementation |
|---|---|---|
| Input Validation and Sanitization | SQL Injection, Cross-Site Scripting (XSS) | Reduced risk of malicious code injection, enhanced data security |
| Authentication and Authorization | Unauthorized Access | Stronger access controls, improved data confidentiality |
| Regular Security Audits and Penetration Testing | Unidentified Vulnerabilities | Early detection and mitigation of security flaws, improved overall security posture |
| Data Encryption in Transit | Man-in-the-Middle Attacks | Data confidentiality, protection from eavesdropping |
| Data Encryption at Rest | Data Breaches | Data protection even in case of storage system compromise |
| Data Loss Prevention (DLP) | Unauthorized Data Exfiltration | Prevention of sensitive data from leaving the organization’s control |
| Secure Coding Practices | Application-Specific Vulnerabilities | Reduced likelihood of introducing vulnerabilities during development |
| Regular Updates and Patches | Known Vulnerabilities | Proactive mitigation of known security flaws |
| User Awareness Training | Social Engineering Attacks | Reduced susceptibility to phishing attempts and other attacks |
Illustrative Scenarios
Application usage reports are invaluable tools for understanding how users interact with software and identifying potential security threats. Analyzing usage patterns, both normal and unusual, is crucial in detecting malicious activity and preventing unauthorized access. This section provides examples of various scenarios, highlighting how different usage patterns can reveal potential security risks.
Application Usage Reports with Threats
Application usage reports often reveal patterns that can indicate malicious activity. For instance, a surge in login attempts from unusual IP addresses or a sudden spike in data exfiltration attempts can flag potential threats. Reports can also uncover unexpected access to sensitive data or unusual file manipulation patterns.
- Scenario 1: Elevated Login Attempts. A significant increase in login attempts from a single IP address or a geographically diverse group of IP addresses, particularly outside of typical user activity hours, suggests a potential brute-force attack. This could be indicative of automated tools trying to guess passwords.
- Scenario 2: Unusual Data Exfiltration. An application usage report might reveal unusually high transfer rates of sensitive data to external servers or unusual destination URLs. For example, a sudden increase in downloads of confidential financial documents to a non-corporate email address could be a sign of data theft.
- Scenario 3: Unauthorized Access to Restricted Data. A user account with restricted access to sensitive information suddenly showing access to that data, without any prior history or justification, is a red flag. This could indicate an account compromise or a configuration error.
Unusual Application Usage Patterns
Unusual application usage patterns can point to unauthorized access or malicious activity. These patterns might include unusual access times, data access frequencies, or user behavior deviations from established norms. Understanding these deviations is key to early threat detection.
- Scenario 4: Uncharacteristic User Activity. A user known for working standard business hours suddenly exhibiting activity during the night hours, accessing files they’ve never accessed before, or accessing them at unusual frequency, warrants investigation. This could signify a compromise of their account.
- Scenario 5: Application Usage Outside Normal Operating Hours. Significant application usage during periods when the application is typically not used or when user activity is minimal might indicate automated processes or unauthorized access.
- Scenario 6: Data Manipulation Patterns. Unusual changes to data records or file modification patterns that deviate from normal operations can point to potential data breaches or insider threats. For example, a report showing large numbers of files being deleted or modified at irregular intervals.
Interpreting Usage Patterns in Real-World Scenarios
Interpreting application usage patterns requires a deep understanding of normal user behavior and application functionality. Analyzing usage reports in conjunction with other security data sources, such as network logs and security information and event management (SIEM) systems, can help provide a more comprehensive picture of potential threats.
| Application | Threat | Recommendation |
|---|---|---|
| Financial Trading Platform | Unusual trading activity from a specific account, large volume of trades in a short period | Review account activity, investigate potential fraudulent activity, contact account holder for clarification |
| Healthcare Records System | Unauthorized access to patient records, unusual download patterns of sensitive data | Isolate compromised account, review access logs, notify relevant authorities if necessary |
| Customer Relationship Management (CRM) System | High volume of password reset requests, unusual data modification from multiple accounts | Implement multi-factor authentication, monitor for suspicious login attempts, investigate compromised accounts |
Illustrative Application Usage Report
This report details application usage for the “ProjectZenith” application on October 26, 2023. The report highlights several potential threats and recommends proactive security measures. Unusual login attempts from external IP addresses and a significant increase in file access attempts to restricted directories were observed.
“Analysis reveals a 300% increase in login attempts from IP addresses outside the organization’s typical range between 2:00 AM and 4:00 AM. Simultaneously, there’s a 150% increase in attempts to access files within the restricted ‘confidential’ directory.”
The report recommends implementing multi-factor authentication for all users and strengthening firewall rules to block suspicious IP addresses.
Data Presentation and Reporting
Crafting a compelling report isn’t just about the data; it’s about how you communicate it. A well-structured report, brimming with clear visuals and concise language, empowers stakeholders to understand the findings and take appropriate action. This section details the importance of effective data presentation, including examples of how to present your findings, and how to structure your report for maximum impact.Effective communication of findings is paramount.
Presenting data in a way that is easily understood and interpreted by the audience is critical for generating actionable insights. The report should not only highlight the key issues but also offer concrete recommendations for improvement.
Example Report Structure
The structure of your report should be clear and logical, allowing readers to easily navigate the content and identify key takeaways. A typical report should include an introduction, a body section detailing the findings, and a conclusion. The body section should be further divided into logical subsections. Each subsection should present data using tables, charts, and graphs, providing context and explanation.
Presenting Findings with Visualizations, Application usage and threat report
Visualizations are crucial for conveying complex information effectively. Charts and graphs can quickly highlight trends, patterns, and outliers that might be missed in a purely textual format.
- Line charts are ideal for displaying trends over time. For instance, a line chart showing the daily application usage rate over the past month would clearly illustrate usage patterns and potential spikes or dips.
- Bar charts are suitable for comparing different categories or groups. For example, a bar chart comparing the number of security incidents across different application modules can highlight areas requiring attention.
- Pie charts are useful for illustrating the proportion of different categories. If you need to show the breakdown of application usage by user type, a pie chart would be effective.
- Heatmaps can illustrate data distribution over time or across different dimensions. A heatmap of user activity by time of day could highlight periods of high activity and potential bottlenecks.
Importance of Clear and Concise Communication
Clear and concise communication ensures that the intended message is accurately conveyed to the audience. Jargon and overly technical language should be avoided. Instead, use plain language that resonates with the reader’s background and needs.
Data Accuracy and Report Structure
Accurate data is the foundation of a reliable report. All data points must be verified, and any assumptions or estimations should be clearly documented. A well-structured report ensures the data is presented logically and systematically, making it easier for the reader to understand the context.
Effective Stakeholder Presentation
When presenting findings to stakeholders, focus on the implications and recommendations, rather than just the data itself. Highlight the potential impact of the findings on the organization’s goals. Use visuals to support your arguments and make them easy to understand. Practice your presentation beforehand to ensure a smooth and engaging delivery.
Compelling Summary
“Our analysis reveals a significant increase in application usage during peak hours, suggesting potential performance bottlenecks. Simultaneously, we identified a surge in suspicious login attempts correlating with these peak usage periods. These findings highlight the critical need for performance optimization and enhanced security measures, especially during high-demand times.”
Final Review
In conclusion, the application usage and threat report is a vital tool for organizations to understand and mitigate potential security risks associated with application usage. By analyzing trends and patterns in application usage, organizations can proactively identify and address potential threats. This comprehensive approach, from defining usage metrics to formulating security recommendations, empowers organizations to maintain a secure and efficient technological environment.
The report emphasizes clear communication of findings and provides a structured approach to data analysis and visualization, enabling informed decision-making.