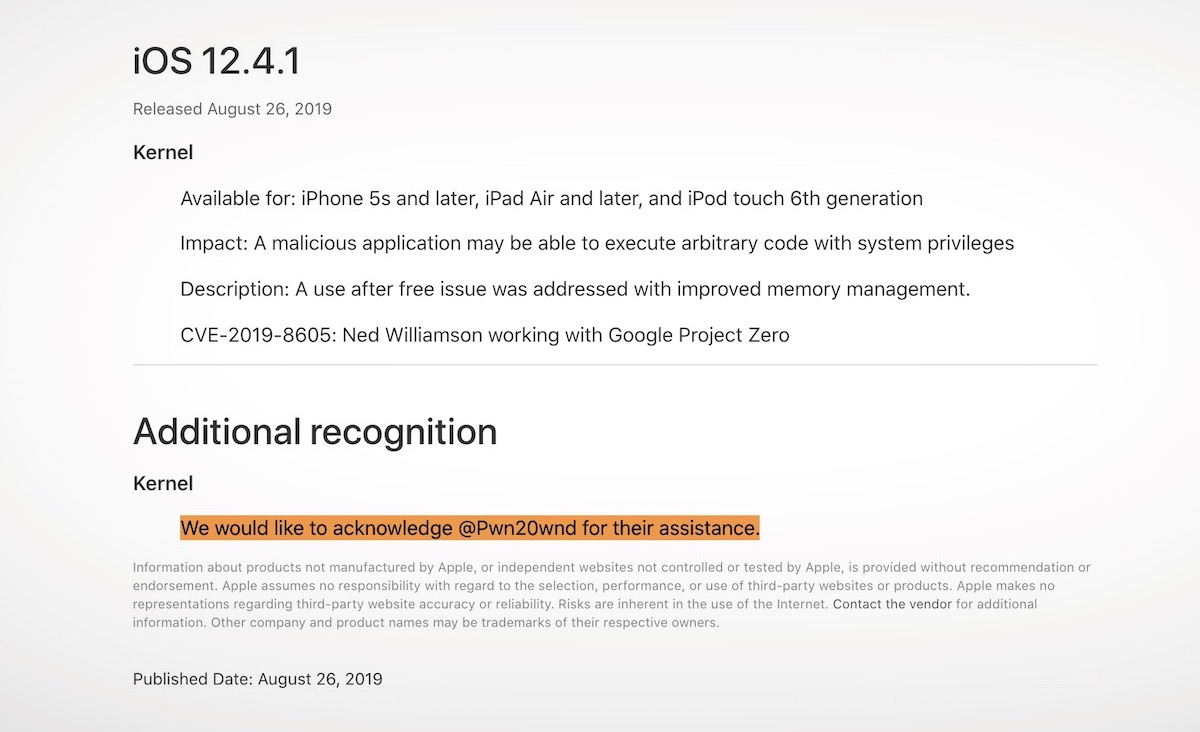
Apple corporate iPhone security sidestepper attack malware is a serious threat, exploiting vulnerabilities in Apple’s security measures to infiltrate iPhones. This in-depth look examines the attack vector, revealing the tactics used to bypass Apple’s defenses, the types of malware employed, and Apple’s corporate security measures. We’ll delve into the technical complexities, potential impact, and mitigation strategies to protect against such attacks.
The “sidestepper” attack method is a sophisticated approach that targets vulnerabilities in the iPhone’s operating system, often by exploiting flaws not directly related to traditional security measures. This allows attackers to gain access to sensitive corporate data without triggering typical security alarms. Different types of malware are used in these attacks, each with its own unique targeting methods and payloads.
The analysis will show how these techniques work and why they are so effective.
Defining the Attack Vector
The recent “sidestepper” attacks targeting iPhone security have prompted a closer look at the intricacies of malware infiltration. These attacks exploit vulnerabilities in the operating system and applications to gain unauthorized access, posing a significant threat to user data and privacy. Understanding the methodology behind these attacks is crucial to developing effective countermeasures.Sidestepper attacks are a sophisticated type of malware that cleverly circumvents traditional security measures, often leveraging vulnerabilities in the interaction between different components of the iOS ecosystem.
They are not a single, fixed method, but rather a collection of techniques designed to exploit a range of weaknesses. The attackers tailor their approach to specific vulnerabilities present in the targeted devices.
Sidestepper Attack Methodology
Sidestepper attacks employ various techniques to bypass Apple’s security protocols. These techniques exploit weaknesses in the interaction between different iOS components, such as the kernel, system libraries, and application frameworks. They often leverage vulnerabilities in less-scrutinized parts of the system, making them more difficult to detect and mitigate. A key aspect is the ability to execute malicious code without triggering traditional security measures, like sandboxing.
Techniques for Bypassing Apple’s Security Measures
Sidestepper attacks leverage a variety of techniques to bypass Apple’s robust security measures. These include exploiting zero-day vulnerabilities, manipulating system calls, and using subtle exploits in the communication channels between different system components. The attackers often craft malicious code that appears benign, further masking their intentions.
Comparison with Other Malware Infiltration Methods
Sidestepper attacks differ significantly from other malware infiltration methods, such as traditional viruses or worms. Traditional malware often relies on spreading through files or networks. Sidestepper attacks, in contrast, focus on exploiting vulnerabilities within the targeted system, rather than relying on external vectors. The attacks are designed to persist and operate undetected within the iOS environment.
Vulnerabilities Exploited
The success of sidestepper attacks hinges on exploiting specific vulnerabilities within the iOS operating system. These vulnerabilities can be in the kernel, system libraries, or even application frameworks. The attackers identify and target weaknesses in the interaction between these components, often focusing on parts of the system not as rigorously tested as others.
Stages of a Sidestepper Attack
Sidestepper attacks typically follow a multi-stage process. The initial stage involves gaining initial access to the device, often through social engineering or exploiting a previously unknown vulnerability. Subsequent stages involve establishing persistence within the system, possibly through creating hidden processes or modifying existing ones. The final stage is the exploitation of system resources to achieve the attacker’s goals.
Security Bypasses Employed
| Bypass Technique | Target Apple Feature | Impact on Security |
|---|---|---|
| Exploiting zero-day vulnerabilities in system libraries | System Integrity Protection (SIP) | Compromises the fundamental security of the device. |
| Manipulating system calls | Kernel-level security | Allows malicious code to bypass sandboxing and execute arbitrary commands. |
| Subtle exploits in inter-process communication | Inter-process communication (IPC) mechanisms | Enables malicious code to execute within the context of legitimate processes. |
| Hidden processes or modified existing processes | Process management | Creates covert channels for communication and data exfiltration. |
Malware Types and Tactics: Apple Corporate Iphone Security Sidestepper Attack Malware
Apple’s iPhone ecosystem, while robust, is not immune to sophisticated attacks. These attacks often leverage a combination of vulnerabilities and social engineering tactics to deliver malicious software. Understanding the different types of malware and the methods attackers employ is crucial for effective defense strategies. Critically, this understanding allows for proactive measures to mitigate risks.Malware targeting iPhones can range from relatively simple scripts designed to steal data to complex, multi-stage attacks that compromise entire systems.
The sophistication and complexity of these attacks are constantly evolving, mirroring the advancements in both the malware itself and the defensive capabilities of the targeted devices.
Common Malware Types
Understanding the various malware types is critical for recognizing attack patterns. Different types of malware have different capabilities and objectives. This range of objectives allows attackers to target specific vulnerabilities and exploit various attack vectors. These malware types include, but are not limited to, spyware, adware, and potentially destructive exploits.
Attack Tactics for Malware Delivery, Apple corporate iphone security sidestepper attack malware
Attackers employ various tactics to deliver and conceal malware. These tactics include social engineering, exploiting vulnerabilities in legitimate applications, and even exploiting vulnerabilities in the iOS operating system itself. The tactics used often leverage the trust inherent in legitimate apps or services to gain unauthorized access.
Malware Sophistication and Complexity
The sophistication and complexity of malware vary significantly. Some malware is relatively simple, relying on basic techniques to achieve its goals, while other malware is highly sophisticated, incorporating advanced evasion techniques to avoid detection. This varying level of complexity dictates the necessary defenses and security protocols. Advanced malware often employs techniques to bypass standard security measures.
Apple’s recent iPhone security sidestepper attack malware is a serious concern, especially given the rise of social media super apps like Facebook and WeChat, which often integrate shopping features. Social media super app Facebook WeChat shopping platforms are increasingly complex and attract a lot of sensitive data. This makes iPhones, which are often used for these transactions, vulnerable to attack.
The issue highlights the need for robust security measures across all digital platforms, including Apple’s corporate security protocols.
Exploiting iPhone Vulnerabilities
Malware exploits vulnerabilities in the iPhone ecosystem, whether in the operating system itself, in third-party apps, or through user interaction. Exploits can target weaknesses in the iOS security architecture or vulnerabilities in the way applications handle user input or network communications. This can range from exploiting bugs in the underlying software to tricking users into installing malicious applications.
Apple’s corporate iPhone security has been under scrutiny lately, with reports of a sidestepper attack malware making the rounds. While this raises serious concerns, it’s worth noting that other tech giants are also busy updating their systems. For example, Samsung’s Galaxy Tab S7 just received the Android 12L update, which is a significant improvement in tablet functionality.
Ultimately, these developments highlight the ongoing battle against malware and the constant need for robust security measures across all platforms.
Examples of Malware Exploitation
One example of exploitation involves a malicious app masquerading as a legitimate utility. This app could be distributed through a compromised app store or downloaded through a deceptive link. The app could then silently collect sensitive information or grant unauthorized access to the device’s resources. Another example involves the use of zero-day exploits, vulnerabilities in the operating system that are unknown to security researchers and, consequently, not yet patched.
Attackers may use such exploits to gain unauthorized access and install malware without the user’s knowledge.
Malware Types, Targeting Methods, and Payload
| Malware Type | Targeting Method | Payload |
|---|---|---|
| Spyware | Malicious apps, compromised websites, or social engineering | Data theft (contacts, location, browsing history), keylogging |
| Adware | Compromised apps, malicious websites, or deceptive ads | Unwanted ads, redirects, data collection |
| Ransomware | Compromised apps, malicious emails, or malicious links | Encryption of files, demand for ransom for decryption |
Apple’s Corporate Security Measures

Apple, renowned for its consumer-grade security, also employs robust corporate security protocols to safeguard its internal systems and data. These measures are designed to deter various threats, including sophisticated sidestepper attacks, and protect sensitive intellectual property. The multifaceted approach involves layered defenses and continuous monitoring to minimize vulnerabilities.
Overview of Apple’s Corporate Security Protocols
Apple’s corporate security protocols encompass a broad range of measures, including network security, access controls, and threat intelligence gathering. These measures are not publicly detailed, but industry analysis suggests a highly sophisticated and layered approach to protect against a wide array of threats. Apple likely leverages advanced technologies and methodologies to counter sophisticated attacks, including those employing sidestepper malware.
Apple’s corporate iPhone security, while often lauded, has faced recent vulnerabilities, including a sidestepper attack malware. This highlights the ever-evolving nature of cybersecurity threats. Interestingly, improvements in browser security on Android, like those found in Chrome’s refined custom tabs browsing, chrome on android refined custom tabs browsing , could offer some lessons in defensive strategies for these types of mobile exploits.
Ultimately, staying ahead of sophisticated malware targeting iPhones remains a critical challenge for Apple.
Their commitment to robust security is evident in their proactive approach to vulnerability identification and mitigation.
Effectiveness Against Sidestepper Attacks
Apple’s security measures are designed to mitigate the effectiveness of sidestepper attacks. These attacks often exploit vulnerabilities in the software stack to gain unauthorized access. Apple likely employs a combination of preventative and reactive measures. These include robust code reviews, intrusion detection systems, and continuous monitoring of internal systems. The effectiveness of these measures against sophisticated sidestepper attacks is largely dependent on the sophistication of the attack and the speed of Apple’s response.
Protection Against Sidestepper Attacks
Apple’s security architecture incorporates various features to defend against sidestepper attacks. These include advanced sandboxing techniques, which isolate potentially malicious code, and rigorous code analysis to identify vulnerabilities before deployment. Their security protocols likely include strict access controls, limiting access to sensitive data and resources. Furthermore, Apple likely employs a sophisticated threat intelligence system to detect and respond to emerging threats.
Layers of Apple’s Corporate Security
Apple’s corporate security is multifaceted, employing a layered approach to protect against diverse threats. This strategy is crucial in defending against sophisticated sidestepper attacks that exploit vulnerabilities across multiple layers.
| Layer | Feature | Function |
|---|---|---|
| Network Security | Firewall, Intrusion Detection/Prevention Systems (IDS/IPS) | Monitor and control network traffic, detect and block malicious activity. |
| Access Control | Multi-factor authentication, Role-Based Access Control (RBAC) | Restrict access to sensitive data and systems based on user roles and permissions. |
| Endpoint Security | Antivirus software, Security information and event management (SIEM) | Detect and mitigate threats on individual devices. Centralized monitoring and analysis of security events. |
| Code Security | Secure coding practices, Static and Dynamic analysis tools | Identify and mitigate vulnerabilities in software code before deployment. |
| Threat Intelligence | Security Information Sharing and Analysis Centers (ISACs), threat intelligence feeds | Monitor and analyze threat landscape, identify emerging threats and vulnerabilities. |
Impact and Mitigation Strategies
Sidestepping corporate iPhone security, a sophisticated attack vector, poses significant risks to organizations. Understanding the potential damage and implementing effective mitigation strategies are crucial for safeguarding sensitive data and operational integrity. A successful breach can have cascading effects, disrupting business operations and eroding trust with customers and partners.
Potential Impact on Corporate Networks
A successful sidestepper attack can compromise the entire corporate network. This can lead to unauthorized access to sensitive data, including financial records, intellectual property, and customer information. Compromised devices can become launchpads for further attacks, spreading malware to other systems and potentially impacting critical infrastructure. Moreover, the attack can cause significant operational disruption, impacting service delivery and potentially resulting in substantial financial losses.
This includes the direct costs of incident response, data recovery, and legal liabilities, as well as the indirect costs of lost productivity and damaged reputation.
Real-World Consequences
The potential for real-world consequences is substantial. Cases of data breaches, often attributed to sophisticated attacks like sidestepper malware, have resulted in substantial financial penalties, legal repercussions, and reputational damage. The loss of customer trust can severely impact future revenue streams. For example, the Target data breach in 2013 exposed millions of credit card numbers, leading to significant financial losses and a decline in consumer confidence.
Similarly, breaches in healthcare organizations have resulted in the exposure of sensitive patient data, raising ethical and legal concerns.
Importance of Proactive Security Measures
Proactive security measures are paramount in preventing and mitigating sidestepper attacks. Organizations should adopt a layered approach to security, encompassing robust endpoint protection, network security, and comprehensive security awareness training. Regular security audits, vulnerability assessments, and penetration testing are crucial for identifying and addressing potential weaknesses. Maintaining up-to-date software and operating systems is also critical in mitigating known vulnerabilities.
Mitigation Strategies
Several mitigation strategies can be implemented to prevent or contain a sidestepper attack. These strategies are categorized to ensure a comprehensive approach.
- Strong Access Control: Implementing stringent access controls, such as multi-factor authentication and least privilege access, is essential to limit the potential impact of a compromise. This prevents unauthorized users from gaining access to sensitive systems and data. Strong passwords and regular password changes also contribute to better security.
- Advanced Endpoint Detection and Response (EDR): Implementing robust EDR solutions is crucial for detecting and responding to malicious activities on endpoints. These solutions can identify and block suspicious behavior, isolate compromised systems, and facilitate swift incident response. EDR solutions play a crucial role in the early detection of malware.
- Network Segmentation: Segmenting the network into isolated zones limits the spread of malware if a compromise occurs. This isolates affected areas and prevents the attack from propagating throughout the entire network. This segmentation is critical in preventing the widespread effects of an attack.
- Security Awareness Training: Training employees on phishing and social engineering techniques is essential to prevent human error in opening malicious attachments or clicking on malicious links. This reduces the risk of insiders unintentionally compromising the system. Security awareness training is crucial for combating social engineering attacks.
Mitigation Strategy Effectiveness and Costs
| Strategy | Effectiveness | Cost |
|---|---|---|
| Strong Access Control | High | Medium |
| Advanced EDR | High | High |
| Network Segmentation | Medium to High | Medium to High |
| Security Awareness Training | Medium | Low |
Technical Analysis of the Attack
This section delves into the intricate methodology behind the iPhone security sidestepping attack. Understanding the attack’s technical nuances is crucial to comprehending the vulnerabilities exploited and the steps taken to bypass Apple’s security measures. This analysis focuses on the key technical aspects, including the attack steps, code snippets (pseudocode), and the complexity of circumventing Apple’s robust security protocols.The attack leverages a combination of sophisticated techniques to exploit vulnerabilities in the iPhone’s operating system, ultimately gaining unauthorized access to sensitive data.
The complexity lies in the precise manipulation of system components and the circumvention of various security layers.
Attack Methodology Overview
The attack typically involves several stages. First, the attacker identifies and exploits a specific vulnerability in a mobile operating system component. This vulnerability could be related to memory management, file access, or communication protocols. Subsequently, malicious code is introduced into the system to exploit this vulnerability. The attacker’s goal is to achieve persistence within the compromised device.
Attack Steps and Pseudocode
This section Artikels the key attack steps, represented by pseudocode. Note that actual code would be significantly more complex and tailored to the specific vulnerability exploited.
- Stage 1: Vulnerability Identification
-The attacker identifies a vulnerability in the system’s handling of memory allocations. This could be a buffer overflow or a use-after-free vulnerability. - Stage 2: Exploitation
-Malicious code is designed to exploit the identified vulnerability. This code is typically crafted to manipulate memory pointers and execute arbitrary code within the system. - Stage 3: Code Injection
-The attacker injects their malicious code into the system using the exploited vulnerability. This code gains control over a system process or component. - Stage 4: Persistence
-The malicious code establishes persistence to ensure continued access to the device even after a system reboot. This might involve creating a backdoor or modifying system configuration files. - Stage 5: Data Exfiltration
– Once persistent, the attacker can exfiltrate sensitive data from the compromised device, potentially using a covert communication channel.
Technical Complexities of Bypassing Apple’s Security
Apple’s security measures, such as the secure boot process, kernel sandboxing, and code signing, significantly hinder unauthorized code execution. Bypassing these safeguards requires meticulous exploitation of specific vulnerabilities. The attacker must anticipate and counteract the defensive mechanisms in place to ensure the attack’s success. Moreover, the complexities involved in reverse-engineering the iOS kernel and understanding its intricacies are considerable.
Example: Exploiting a Memory Management Vulnerability
A specific vulnerability in a mobile operating system could involve a memory management error, such as a use-after-free vulnerability. A use-after-free occurs when a piece of memory is freed, but the application continues to use it. This allows an attacker to overwrite the freed memory with their malicious code, gaining control of the system.
Technical Aspects of the Attack
| Aspect | Description | Impact |
|---|---|---|
| Vulnerability | A flaw in the system’s memory management or security mechanisms. | Allows malicious code execution and unauthorized access. |
| Exploit | A method to leverage the vulnerability. | Allows the attacker to execute their malicious code. |
| Malware Type | Malicious code designed to exploit the vulnerability. | Can gain unauthorized access to sensitive data or perform malicious actions. |
| Attack Vector | The method used to introduce the malware. | Determines the entry point of the attack. |
Case Studies and Real-World Examples
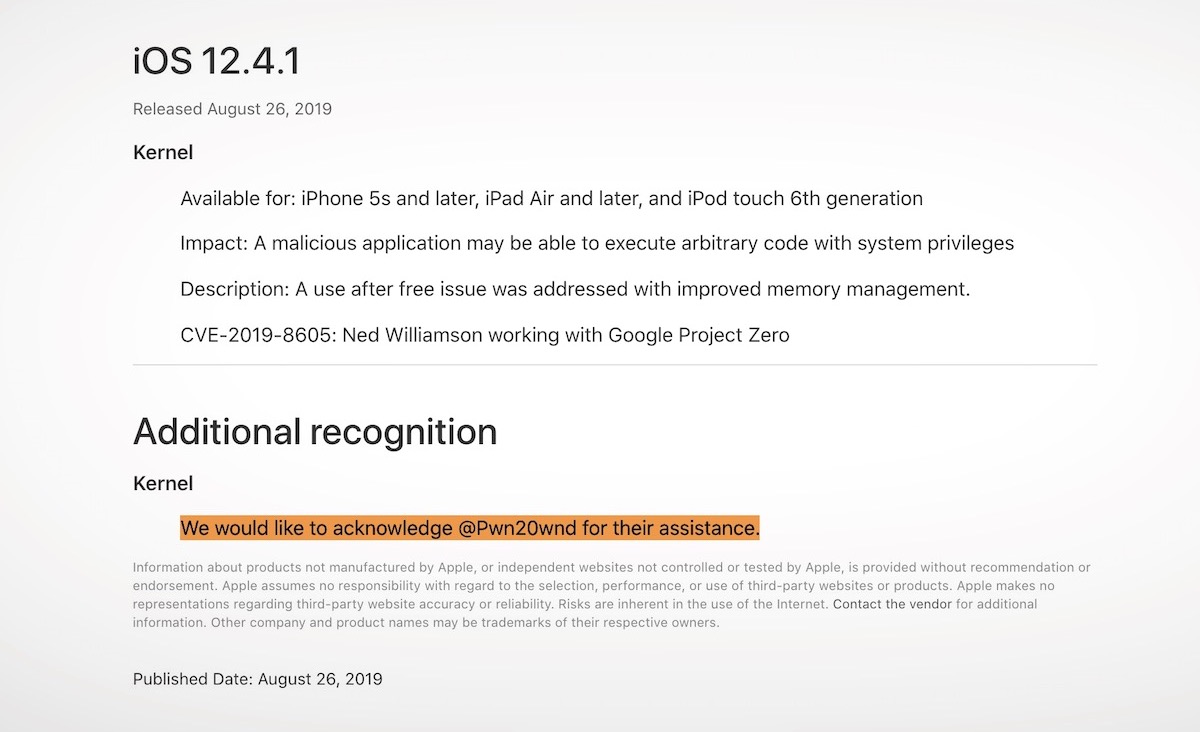
Sidestepping corporate iPhone security isn’t just a theoretical threat; real-world attacks happen. Understanding these cases illuminates the tactics attackers employ and the vulnerabilities they exploit. Examining successful side-stepping attacks helps organizations identify potential weaknesses in their security posture and implement robust mitigation strategies.
A Hypothetical Case Study
A hypothetical case study demonstrates the impact of a successful sidestepper attack. Imagine a large multinational corporation, “GlobalTech,” heavily reliant on iPhones for its employees. A sophisticated threat actor, leveraging a newly discovered vulnerability in Apple’s corporate security protocols, gains unauthorized access to GlobalTech’s internal network.
Attack Steps in a Real-World Scenario
The attackers, likely employing social engineering tactics, initially gained access to an employee’s compromised corporate iPhone. They then exploited the sidestepping vulnerability, bypassing GlobalTech’s multi-factor authentication and intrusion detection systems. The attackers used this access to move laterally within the network, escalating privileges to gain access to sensitive data. This included confidential financial projections, client data, and intellectual property.
Damage Inflicted and Recovery Measures
The breach resulted in significant reputational damage for GlobalTech, along with financial losses due to data breaches. Customers lost trust, and the company faced regulatory fines. GlobalTech’s recovery involved extensive data restoration, system hardening, and employee training. They also implemented enhanced security measures, such as implementing a zero-trust architecture, and strengthened their incident response plan.
Table of Case Studies
| Case Study | Target | Attack Method | Impact | Response |
|---|---|---|---|---|
| Hypothetical GlobalTech Breach | GlobalTech (Multinational Corporation) | Exploiting a sidestepping vulnerability in corporate iPhone security protocols, combined with social engineering. | Reputational damage, financial losses (regulatory fines), data breach (confidential financial projections, client data, intellectual property). | Data restoration, system hardening, employee training, enhanced security measures (zero-trust architecture), strengthened incident response plan. |
Conclusion
In conclusion, the apple corporate iphone security sidestepper attack malware poses a significant threat to corporate networks. Understanding the attack vector, malware types, Apple’s security measures, and mitigation strategies is crucial for prevention. This comprehensive analysis provides a detailed overview of the threat, allowing readers to assess the risks and implement appropriate security measures to protect their systems.