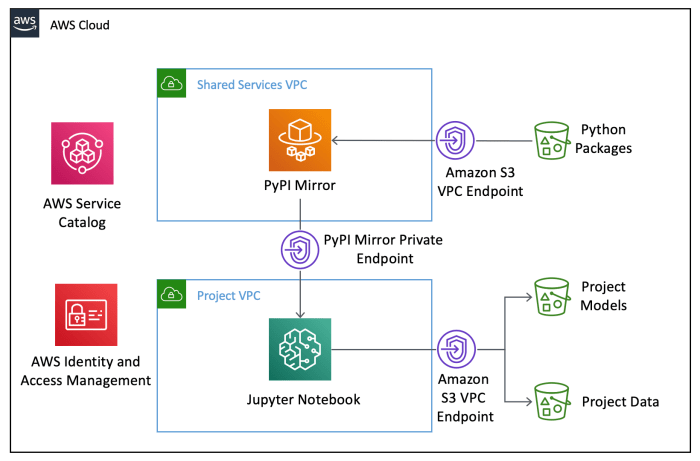
A primer on machine learning in endpoint security dives deep into the world of modern cybersecurity. This guide explores how machine learning algorithms are revolutionizing endpoint protection, from detecting sophisticated threats to automating incident responses. We’ll examine the core principles, techniques, and practical applications of machine learning in safeguarding your systems, outlining the evolving threat landscape and the critical role of AI in the fight against cybercrime.
This primer will walk you through the different types of machine learning techniques, including supervised and unsupervised learning, used to detect and respond to threats. We’ll explore the various data sources and the model training process, focusing on the importance of data quality and handling imbalanced datasets. The practical application of machine learning in endpoint security will be demonstrated through real-world scenarios and examples.
Introduction to Endpoint Security
Endpoint security encompasses the protection of individual computing devices, such as desktops, laptops, smartphones, and tablets, from cyber threats. These devices are often the initial entry point for malicious actors seeking to compromise an organization’s network and sensitive data. This critical role demands a multi-layered approach that combines technical safeguards with user awareness training.The threat landscape is constantly evolving, with cybercriminals employing increasingly sophisticated techniques to exploit vulnerabilities in endpoint systems.
This includes the rise of ransomware attacks, sophisticated phishing campaigns, and the proliferation of malware designed to evade traditional security measures. The ever-changing nature of these threats underscores the need for adaptable and proactive security solutions.
Evolving Threats to Endpoint Security
The cyber threat landscape is a dynamic and complex environment. Sophisticated attacks are increasingly common, targeting vulnerabilities in endpoint devices to gain access to networks and steal sensitive data. Ransomware, for instance, is a significant concern, as attackers encrypt data and demand payment for its release. Phishing, which deceives users into revealing personal information or clicking malicious links, remains a potent threat.
Moreover, the rise of mobile devices and the Internet of Things (IoT) has expanded the attack surface, creating new vectors for exploitation.
Ever wondered how machine learning is changing endpoint security? It’s a fascinating field, and a primer on the subject is a great place to start. While exploring this topic, it’s interesting to consider how advancements in technology like, say, hyperloop one fastest test 192 mph , push the boundaries of what’s possible. Ultimately, a deeper understanding of machine learning’s role in endpoint security is key to future-proofing your digital defenses.
The Importance of Machine Learning in Endpoint Security
Traditional endpoint security methods, relying on signature-based detection, often struggle to keep pace with the ever-evolving threat landscape. Machine learning (ML) provides a more adaptable and proactive approach, enabling security solutions to identify and respond to previously unknown threats. ML algorithms can learn from vast amounts of data, identifying patterns and anomalies indicative of malicious activity, allowing for rapid response and prevention.
Core Principles of Machine Learning in Endpoint Security
Machine learning algorithms, used in endpoint security, leverage several core principles. Supervised learning, for example, trains models on labeled data sets (known malicious and benign activities), enabling the system to classify new activities. Unsupervised learning, on the other hand, identifies patterns and anomalies in data without prior labeling, allowing the detection of previously unseen threats. Reinforcement learning adapts security measures in real-time based on interactions with the system, refining its ability to detect and respond to threats.
Comparing Traditional and Machine Learning-Based Endpoint Security
| Feature | Traditional Endpoint Security | Machine Learning-Based Endpoint Security |
|---|---|---|
| Threat Detection | Relies on known signatures of malware. | Identifies patterns and anomalies, including previously unknown threats. |
| Adaptability | Slow to adapt to new threats. | Continuously learns and adapts to new threats. |
| False Positives | High potential for false positives, requiring manual review. | Lower potential for false positives, with more automated analysis. |
| Resource Requirements | Lower computational requirements. | Higher computational requirements for training and ongoing analysis. |
| Response Time | Slower response time to emerging threats. | Faster response time to emerging threats. |
Traditional endpoint security methods rely on predefined rules and signatures, often struggling to detect sophisticated, zero-day attacks. Machine learning-based solutions, in contrast, leverage the power of pattern recognition and anomaly detection, significantly improving the ability to identify and respond to a wider range of threats.
Machine Learning Techniques in Endpoint Security
Machine learning (ML) is rapidly transforming endpoint security, moving beyond simple signature-based detection to proactive threat identification and response. By analyzing vast amounts of data from endpoints, ML algorithms can identify subtle anomalies and patterns indicative of malicious activity, significantly improving threat detection accuracy and speed. This approach enables a more sophisticated and dynamic defense against evolving threats.The core principle behind applying ML to endpoint security is the ability to learn from historical data.
By training models on known malicious and benign activities, ML algorithms can build a profile of what constitutes a threat. This profile is then used to identify new threats that exhibit similar characteristics. This adaptive learning capability is crucial in the face of constantly evolving malware.
Different Machine Learning Algorithms Used
Various machine learning algorithms are employed in endpoint security. Each algorithm possesses unique strengths and weaknesses, making it suitable for specific tasks. Understanding these differences is vital for optimizing security solutions.
- Supervised Learning algorithms, such as Support Vector Machines (SVMs) and Decision Trees, learn from labeled data. This data contains examples of both malicious and benign activities, allowing the algorithm to classify new data points. SVMs excel at identifying complex patterns in high-dimensional data, while decision trees provide a clear and interpretable representation of the decision-making process. For instance, an SVM model trained on samples of known malware and clean files can classify new files as malicious or benign based on learned features.
- Unsupervised Learning algorithms, like clustering algorithms (e.g., k-means), identify patterns and anomalies in unlabeled data. These algorithms group similar data points together, highlighting unusual data points that might indicate malicious activity. For example, k-means clustering can group network traffic based on similarities, revealing unusual clusters that might signify a network intrusion.
- Reinforcement Learning algorithms learn through trial and error. In the context of endpoint security, these algorithms could adjust security policies and responses based on observed threats and their impact. For instance, a reinforcement learning agent might learn to block a particular type of malware more effectively over time by analyzing its effectiveness against various samples and adapting its approach.
Detection and Response Mechanisms
Machine learning algorithms are employed to analyze various data sources from endpoints, including file behavior, network traffic, registry modifications, and system calls. These algorithms identify patterns that deviate significantly from normal behavior, potentially indicating malicious activity.
- Anomaly Detection is a key application of ML in endpoint security. Algorithms identify deviations from expected patterns in endpoint activities. This helps detect zero-day exploits and novel malware variants that haven’t been encountered before. For instance, if a process suddenly starts making unusually frequent network requests to a suspicious IP address, this could trigger an alert indicating malicious activity.
- Malware Classification algorithms analyze characteristics of files, such as code structure, file size, and network activity, to classify them as malicious or benign. This approach aids in identifying and blocking new malware variants before they can cause damage.
- Intrusion Prevention Systems can be enhanced by integrating ML algorithms. These algorithms learn from past intrusions to identify and block similar future attacks in real time. For instance, if a specific type of exploit has been identified in the past, the ML model can learn to recognize and block similar attempts.
Training Machine Learning Models
Training ML models for endpoint security involves several critical steps:
- Data Collection: Gathering a large and representative dataset of endpoint activities, including both malicious and benign examples, is essential. This dataset needs to be comprehensive and cover various aspects of endpoint behavior.
- Feature Engineering: Extracting relevant features from the collected data is crucial for effective model training. Features might include file characteristics, network traffic patterns, and system call sequences. Appropriate selection and processing of these features are critical for optimal performance.
- Model Selection: Choosing the right ML algorithm depends on the specific task and characteristics of the data. Consider factors such as the size of the dataset, the complexity of the patterns, and the desired level of interpretability.
- Model Evaluation: Assessing the performance of the trained model is crucial. Metrics like precision, recall, and F1-score are used to evaluate the model’s ability to correctly classify malicious and benign activities. Regular testing and validation are vital to maintain accuracy.
Supervised vs. Unsupervised Learning
Supervised learning algorithms require labeled data, whereas unsupervised learning algorithms work with unlabeled data. The choice between supervised and unsupervised learning depends on the specific security needs.
| Characteristic | Supervised Learning | Unsupervised Learning |
|---|---|---|
| Data | Labeled data (malicious/benign) | Unlabeled data |
| Task | Classification, Regression | Clustering, Anomaly Detection |
| Example | Identifying known malware | Detecting unusual network traffic patterns |
Data Sources and Model Training
Machine learning models in endpoint security rely heavily on the quality and variety of data used for training. A robust dataset, encompassing various types of events and behaviors, is crucial for accurate threat detection and prevention. The process of collecting, preparing, and validating this data significantly impacts the model’s performance and ultimately, the effectiveness of the security solution.
A primer on machine learning in endpoint security delves into how AI can identify and stop threats. This is crucial for protecting systems, and understanding how these systems work can be a game changer in security. For example, Sony’s recent announcement regarding the PlayStation 5’s impressive 99% backward compatibility with PS4 games, as detailed in this article ps5 playstation 5 99 percent backward compatible ps4 games jim ryan , highlights the power of technological advancements.
Ultimately, machine learning’s role in security is a critical topic for staying ahead of evolving cyber threats.
Data quality, handling imbalanced datasets, and selecting appropriate sources are critical factors for building a reliable machine learning-powered endpoint security system.
Data Types for Model Training
Various data sources contribute to training endpoint security models. These include system logs, network traffic data, user behavior patterns, and security event logs. Each data type provides unique insights into potential threats and malicious activities. The combination of these diverse data points enables the model to learn and recognize complex attack patterns more effectively.
Data Collection and Preparation
Collecting raw data is only the first step. Data preparation involves transforming raw data into a usable format for the machine learning algorithm. This often involves cleaning, filtering, and normalizing the data. For example, raw log files might require parsing to extract relevant fields, such as timestamps, event types, and user IDs. This structured data can then be used to train the model, improving its accuracy and reliability.
Data preparation techniques like feature engineering, normalization, and data augmentation significantly enhance the model’s learning capacity.
Data Quality and Model Performance
Data quality plays a pivotal role in the success of machine learning models for endpoint security. Inaccurate, incomplete, or inconsistent data can lead to poor model performance, potentially missing or misclassifying threats. Maintaining data quality throughout the process, from collection to model training, is crucial for developing an effective security solution. Regular data validation, data cleansing, and data quality checks are essential to ensure accuracy and reliability.
For instance, inconsistent log formats or missing timestamps can significantly affect the model’s ability to identify threats accurately.
Handling Imbalanced Datasets
Endpoint security datasets often exhibit class imbalance, where certain types of events or threats are significantly less frequent than others. This imbalance can lead to models that favor the majority class, potentially missing critical minority classes that represent real threats. Techniques like oversampling the minority class or undersampling the majority class are crucial to address this issue. Another method involves using cost-sensitive learning, where misclassifying a minority class event carries a higher penalty than misclassifying a majority class event.
These techniques ensure that the model pays sufficient attention to both frequent and infrequent events.
Examples of Data Sources
- System Logs: System logs record events related to file access, process creation, and registry changes. These logs provide crucial information about suspicious activities on the endpoint. Examples include Windows Event Logs, application logs, and security logs.
- Network Traffic Data: Network traffic data captures communication patterns between the endpoint and the network. This includes details like IP addresses, ports, and data transfer volumes. Unusual network activity can signal malicious connections or data exfiltration attempts. Analyzing this data helps identify anomalies and potential threats.
- User Behavior Patterns: User behavior data includes information on login times, application usage, and file access patterns. Deviation from normal user behavior could indicate compromised accounts or malicious actions. This data provides context for understanding the overall security posture of the endpoint.
Enhancing Endpoint Security with Machine Learning
Machine learning (ML) is rapidly transforming endpoint security, moving beyond reactive measures to proactive threat detection and response. By leveraging the power of algorithms to learn from data, security teams can identify subtle patterns indicative of malicious activity, often before traditional signature-based systems can detect them. This approach offers a significant advantage in the fight against advanced threats like APTs, which often evade traditional security measures.ML’s ability to adapt and learn from new data is crucial for maintaining a robust security posture in a constantly evolving threat landscape.
This adaptive capability allows security systems to remain effective even when faced with novel attacks or emerging threats. Furthermore, automating incident response processes with ML can drastically reduce response times, minimizing the potential damage caused by security breaches.
Preventing Advanced Persistent Threats (APTs) with Machine Learning
ML excels at identifying subtle anomalies that often characterize APT attacks. These threats frequently operate for extended periods, employing sophisticated techniques to evade detection. Machine learning models can analyze vast amounts of endpoint data, including network traffic, file system activity, and user behavior, to identify patterns indicative of malicious activity. For example, an ML model trained on historical data of known APT campaigns can recognize unusual data access patterns, or unusual communication protocols that are characteristic of an APT attack, enabling early detection and response.
Automating Incident Response with Machine Learning
Automating incident response through ML offers significant improvements in efficiency and speed. Once a threat is identified, ML algorithms can trigger automated responses, such as isolating affected systems, blocking malicious communications, or initiating remediation procedures. This automation can significantly reduce the time required to contain and remediate a security incident, mitigating potential damage. A well-trained model can analyze logs, network traffic, and system events, automatically categorize the incident type, and initiate the appropriate response procedures.
This drastically reduces the response time and minimizes the window of opportunity for attackers.
Enhancing Security Posture and Reducing the Attack Surface with Machine Learning
ML can be used to proactively identify and mitigate vulnerabilities in the endpoint environment. By analyzing historical data of exploits and vulnerabilities, ML models can predict potential attack vectors and suggest appropriate mitigation strategies, such as patching systems or configuring security controls. Furthermore, ML can reduce the attack surface by automating the process of identifying and prioritizing vulnerabilities based on their likelihood of exploitation.
This proactive approach can strengthen security posture, preventing attacks from occurring in the first place. For instance, a model can flag a particular configuration that leaves a system vulnerable to a known exploit, allowing administrators to proactively remediate it before an attacker can exploit the vulnerability.
Benefits of Integrating Machine Learning into Existing Security Tools and Infrastructures
Integrating ML into existing security tools and infrastructures enhances their effectiveness by providing enhanced threat detection capabilities. ML models can analyze data from various sources, including logs, network traffic, and user behavior, and combine this information to produce a more comprehensive security picture. This improved understanding allows for more accurate threat assessments and more targeted security responses. Furthermore, ML can significantly improve the efficiency of existing security tools, enabling them to prioritize threats and automate responses, ultimately reducing the workload on security teams.
Implementing Machine Learning in an Endpoint Security Solution: A Framework, A primer on machine learning in endpoint security
Implementing ML in an endpoint security solution requires a well-defined framework to ensure effective integration and optimal results. A phased approach is recommended, starting with data collection and preparation. This is followed by model training and validation, and finally, integration into the existing security infrastructure. Continuous monitoring and refinement of the ML models are crucial to ensure their effectiveness in the ever-changing threat landscape.
- Data Collection: Gather relevant data from various sources, including endpoint logs, network traffic, system events, and user behavior. This data should be comprehensive and cover a broad range of activities to ensure accurate representation of the environment.
- Data Preparation: Preprocess and clean the collected data, addressing inconsistencies and missing values. This crucial step ensures the data quality and reliability required for accurate model training.
- Model Training and Validation: Select appropriate machine learning algorithms based on the specific needs and challenges of the environment. Rigorous validation and testing against a variety of known threats and attack vectors is essential.
- Model Deployment and Integration: Integrate the trained model into existing security tools and infrastructures. This ensures seamless operation and proactive threat detection and response.
- Continuous Monitoring and Refinement: Continuously monitor the model’s performance and update it with new data to ensure its effectiveness in a dynamic threat landscape. Regular model retraining and adaptation are critical for sustained security.
Deployment and Implementation Considerations: A Primer On Machine Learning In Endpoint Security

Deploying a machine learning model into an endpoint security solution is a crucial step that requires careful planning and execution. It’s not just about integrating the model; it’s about ensuring its effectiveness, reliability, and long-term viability within the security infrastructure. This involves not only the initial deployment but also ongoing monitoring, evaluation, and retraining to adapt to evolving threats.Successful deployment hinges on understanding the intricacies of the chosen model and its limitations, along with the specific needs and constraints of the endpoint environment.
The goal is not just to implement a solution, but to build a system that effectively complements existing security measures and proactively detects and responds to emerging threats.
Model Deployment Process
The deployment process typically involves integrating the trained machine learning model into the endpoint security agent. This integration could involve using APIs, custom scripting, or pre-built integrations, depending on the architecture of the endpoint security solution. Key considerations include minimizing disruption to existing operations, ensuring seamless data flow between the model and the security agent, and guaranteeing the model’s ability to handle diverse endpoint configurations and operating systems.
This often necessitates careful testing and validation in a controlled environment before full deployment.
A primer on machine learning in endpoint security is crucial for staying ahead of evolving threats. The recent Google Stadia shutdown, as discussed in the google stadia shutdown precedent editorial , highlights the need for robust security measures in the digital age. Ultimately, understanding and applying machine learning techniques to endpoint security is vital to protecting valuable data and systems.
Model Performance Monitoring and Evaluation
Monitoring the performance of a deployed machine learning model is essential for maintaining its effectiveness. Metrics such as precision, recall, F1-score, and accuracy should be continuously tracked and analyzed. A crucial aspect is the detection of anomalies or deviations from expected performance, which could signal the need for model retraining or adjustments. Real-time monitoring tools and dashboards can provide valuable insights into model behavior and identify potential issues.
Regular reporting on these metrics is also vital for understanding the model’s performance trends over time and adapting to changing threat landscapes.
Deployment Checklist
- Thorough Testing: Rigorous testing is critical to identify potential issues before deployment. This includes comprehensive unit tests, integration tests, and end-to-end tests to validate the model’s functionality and robustness across various endpoint configurations.
- Security Hardening: The deployed model must be secured to prevent unauthorized access or manipulation. Implementing appropriate access controls and security protocols is essential to protect the model and its data.
- Scalability: The deployment architecture must be scalable to accommodate future growth in the number of endpoints and the volume of data processed. This includes considerations for distributed processing and cloud-based solutions.
- Integration: Smooth integration with existing endpoint security tools and systems is crucial for seamless operation. This includes ensuring compatibility with existing data pipelines and security workflows.
- Documentation: Comprehensive documentation is vital for maintaining and updating the deployed system. This includes detailed procedures for model retraining, troubleshooting, and system maintenance.
Continuous Model Retraining and Updating
Machine learning models are not static. They require continuous retraining and updating to adapt to evolving threat patterns. This process involves regularly feeding new data into the model, retraining it, and evaluating its performance. This iterative approach ensures the model remains effective in identifying and mitigating new threats. The frequency of retraining will depend on the rate of change in the threat landscape.
A model that is not continuously updated will lose its accuracy and effectiveness. For example, if the model is trained on malware from 2020, its ability to detect newer malware families will decrease.
Challenges and Risks
Deploying machine learning models in endpoint security presents several challenges and risks. These include potential overfitting to the training data, leading to poor generalization on unseen data, and the risk of false positives or negatives, which can disrupt legitimate operations. Maintaining model accuracy and robustness over time requires continuous monitoring and adjustments. Another concern is the potential for adversarial attacks, where malicious actors try to exploit vulnerabilities in the model to bypass detection.
The security of the model itself is crucial.
Illustrative Examples of Machine Learning in Action
Machine learning algorithms are proving increasingly valuable in endpoint security, enabling proactive detection and response to threats. This section provides practical examples of how machine learning can be deployed to enhance security posture, focusing on detecting novel malware, predicting insider threats, and improving incident response.These examples highlight the potential of machine learning to automate and improve security operations, leading to a more robust and resilient security infrastructure.
From identifying subtle anomalies to prioritizing critical alerts, machine learning provides a powerful toolset for modern security teams.
Novel Malware Detection
Machine learning excels at identifying previously unknown malware variants. By analyzing behavioral patterns, file characteristics, and network communication, a machine learning model can detect subtle indicators of malicious activity that traditional signature-based detection systems might miss. For instance, a new ransomware variant might exhibit unusual file encryption patterns or network communication protocols that are not yet included in a signature database.
A machine learning model trained on a vast dataset of known and unknown malware can identify these novel behaviors, raising an alert even without a pre-existing signature. This proactive approach significantly reduces the time it takes to detect and respond to emerging threats.
Insider Threat Prediction
Machine learning models can be trained to identify patterns of behavior indicative of potential insider threats. These patterns could include unusual access requests, data exfiltration attempts, or unusual login times. For example, an employee who normally logs in from a specific location during business hours might suddenly start logging in from a different location at odd hours, potentially indicating suspicious activity.
By monitoring these patterns, a machine learning model can flag such anomalies for investigation, allowing security teams to take preventive measures and mitigate potential risks.
Machine Learning Incident Response Stages
| Stage | Description |
|---|---|
| Data Collection | Gathering relevant data from various sources, including logs, network traffic, and system events. |
| Feature Engineering | Extracting meaningful features from the collected data, which can be used to train the machine learning model. |
| Model Training | Developing and training a machine learning model to recognize patterns associated with specific incidents. |
| Incident Detection | Using the trained model to identify and flag incidents based on their predicted characteristics. |
| Analysis and Response | Investigating detected incidents, determining their severity, and implementing appropriate response measures. |
| Post-Incident Analysis | Evaluating the effectiveness of the response, and updating the machine learning model to improve future detection. |
A structured incident response process, aided by machine learning, is crucial for timely and effective containment and remediation of security breaches.
Prioritizing Security Alerts
“Machine learning algorithms can analyze various factors, such as the source of the alert, the severity level, and the frequency of similar alerts, to prioritize security events based on their potential impact.”
By weighting different criteria, machine learning helps prioritize critical alerts, directing security analysts to the most pressing issues first. This focused approach optimizes resource allocation, allowing security teams to respond more effectively to critical incidents.
Phishing Attack Prevention
A machine learning-based system for preventing phishing attacks can be implemented in several stages:
- Data Collection: Gather data on various phishing attempts, including email subject lines, sender addresses, and the content of the emails.
- Feature Engineering: Extract relevant features from the data, such as the presence of suspicious s, unusual formatting, and links to malicious websites.
- Model Training: Train a machine learning model to recognize patterns associated with phishing attempts. This model can be a classifier, identifying phishing emails as such.
- Email Filtering: Deploy the trained model to filter incoming emails. Emails flagged as potentially malicious are quarantined or blocked.
- User Education: Provide users with information about the detected phishing attempts and educate them on how to identify and avoid similar attacks in the future.
- Continuous Monitoring and Improvement: Continuously monitor the performance of the system and update the model to adapt to new phishing techniques.
This multi-faceted approach significantly enhances the effectiveness of phishing attack prevention.
Closing Notes
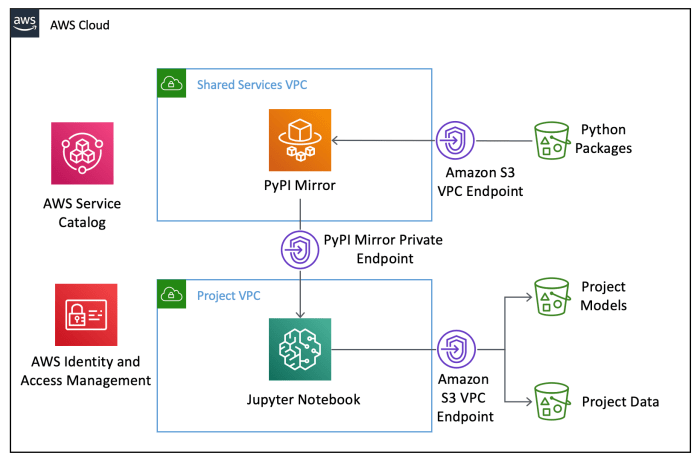
In conclusion, a primer on machine learning in endpoint security reveals the transformative power of AI in modern cybersecurity. From identifying subtle anomalies to automating incident responses, machine learning is rapidly reshaping how we protect our endpoints. This guide has provided a comprehensive overview, highlighting the importance of data quality, model training, and continuous improvement in building robust and effective endpoint security solutions.
By understanding these concepts, organizations can better leverage machine learning to enhance their security posture and mitigate potential cyber threats.