DLL side loading how to combat threat actor evasion techniques is crucial in today’s threat landscape. Malicious actors frequently employ sophisticated evasion tactics to bypass security measures when loading Dynamic Link Libraries (DLLs). This in-depth exploration delves into the methods threat actors use, how to identify these techniques, and the most effective defensive strategies to protect systems.
Understanding the intricacies of DLL side loading and the various evasion methods employed by threat actors is paramount for bolstering system security. From identifying different injection techniques to analyzing system behavior, this guide provides practical steps for preventing and responding to DLL-based attacks. This article also delves into both static and dynamic analysis techniques to effectively identify malicious DLLs, culminating in robust security monitoring solutions.
Introduction to DLL Side Loading and Evasion Techniques
DLL side loading, a technique employed by malicious actors, involves dynamically loading malicious DLLs (Dynamic Link Libraries) into a target system. This method is insidious because it often bypasses traditional security measures designed to prevent the execution of known harmful code. This stealthy approach allows attackers to execute malicious code without directly modifying or infecting legitimate files, making detection and remediation more challenging.The fundamental concept of DLL side loading lies in exploiting the operating system’s ability to load and execute external libraries at runtime.
This capability, while beneficial for software modularity, presents a significant vulnerability when not properly secured. Threat actors leverage this functionality to inject their malicious code into legitimate processes, achieving their objectives covertly. Understanding the evasion techniques used in DLL side loading is crucial to bolstering system security.
Common DLL Side Loading Evasion Techniques
Understanding how threat actors circumvent security measures during DLL side loading is essential for effective defense. They employ various methods to mask their malicious intent and avoid detection. These tactics often exploit the flexibility and complexity of the operating system’s mechanisms.
- Using legitimate process names: Threat actors often disguise their malicious DLLs by using names similar to legitimate system or application processes. This approach helps them evade detection by security software that might flag unfamiliar or suspicious DLL names.
- Employing obfuscation techniques: Obfuscation involves making the malicious code harder to understand or analyze. This might include encryption, packing, or other techniques designed to mask the true intent of the code. The goal is to make it difficult for security tools to interpret and identify the malicious payload.
- Leveraging legitimate DLLs: Malicious actors can exploit the presence of legitimate DLLs to gain access to resources or bypass security checks. This technique involves incorporating malicious code into legitimate libraries or manipulating legitimate libraries to perform malicious actions. This is an important tactic for concealing malicious intent.
- Exploiting system vulnerabilities: Known or unknown vulnerabilities in the operating system or applications can be exploited to gain unauthorized access and load malicious DLLs. These exploits are often used to escalate privileges or gain control of a system.
- Using various loading methods: Different methods for loading DLLs, such as using registry keys, environment variables, or specific application configurations, can be used to evade detection. The use of different loading methods adds another layer of complexity in trying to detect and mitigate the attack.
Significance of DLL Side Loading in Security
DLL side loading, while a legitimate software development practice, represents a significant security risk when misused. The dynamic nature of DLL loading allows threat actors to inject malicious code into existing processes without necessarily modifying those processes. This evasion capability is a critical factor in enabling sophisticated attacks.
Real-World Examples of DLL Side Loading Exploits
Numerous real-world attacks have leveraged DLL side loading to achieve malicious objectives. For instance, certain malware campaigns have employed this technique to deliver ransomware, steal sensitive data, or gain persistent access to compromised systems. These exploits often demonstrate a sophisticated understanding of system architecture and vulnerabilities.
Evasion Technique Analysis
| Evasion Technique | Description | Potential Impact on Security |
|---|---|---|
| Using legitimate process names | Masking malicious DLLs with names similar to legitimate processes. | Bypassing security tools that rely on name-based detection. |
| Employing obfuscation techniques | Making malicious code harder to understand. | Decreasing the effectiveness of static analysis tools and increasing the difficulty of reverse engineering. |
| Leveraging legitimate DLLs | Exploiting legitimate libraries to perform malicious actions. | Making detection difficult due to the presence of legitimate code. |
| Exploiting system vulnerabilities | Utilizing flaws in the operating system or applications. | Potentially leading to complete system compromise. |
| Using various loading methods | Employing different methods for loading DLLs. | Evading detection by security tools that focus on specific loading mechanisms. |
Identifying and Analyzing Evasion Techniques
DLL side-loading, while a powerful technique for malicious actors, is not without its vulnerabilities. Sophisticated threat actors constantly adapt their methods to evade detection by security tools. Understanding these evasion techniques is crucial for developing effective defenses. This section delves into the various approaches used, highlighting common characteristics and technical aspects.DLL injection techniques are often layered and combined to enhance stealth.
This complexity makes it essential for security professionals to understand the diverse strategies used and the tools required for detection. Identifying and analyzing these techniques allows for the development of more robust countermeasures and proactive security strategies.
Different Types of DLL Injection Techniques
DLL injection methods, employed by threat actors, often vary in complexity and sophistication. Understanding the diverse techniques allows for more targeted defensive measures. Techniques include direct injection using Windows API functions, remote thread creation, and using system hooks. These methods can be employed individually or in combination.
Common Characteristics of Evasion Techniques
Evasion techniques in DLL side-loading share several characteristics. They often rely on obfuscation, polymorphism, and the exploitation of system vulnerabilities. These techniques aim to bypass security mechanisms by masking malicious intent and modifying behavior at runtime. They often exploit weaknesses in security software or the operating system itself. This necessitates a comprehensive approach to detection that accounts for a range of potential behaviors.
Technical Aspects of Evading Detection Mechanisms
Threat actors often employ techniques to bypass detection mechanisms. These include using legitimate system processes or libraries to hide malicious code. Another strategy is to alter the execution flow of the DLL, making it harder to identify the malicious behavior. Also, the use of encryption or encoding to conceal malicious instructions is a common practice. Furthermore, utilizing advanced techniques such as anti-debugging and anti-analysis mechanisms to detect and prevent security analysis can hinder the detection process.
Combating threat actor evasion techniques in DLL side-loading requires a robust security strategy. One crucial element is implementing zero trust remote access for manufacturing, like the solutions detailed in zero trust remote access for manufacturing. This approach isolates manufacturing assets, limiting access to only authorized users and devices. By hardening remote access, the likelihood of successful DLL side-loading attacks is greatly reduced.
This layered security approach is key to bolstering defenses against these increasingly sophisticated evasion techniques.
Comparison and Contrast of Evasion Techniques
Various evasion techniques differ in their complexity and effectiveness. Techniques relying on code obfuscation are relatively easy to implement but can be readily detected by advanced security tools. Conversely, techniques that manipulate the system’s internal structures require more sophisticated skills but can evade detection for longer periods. Techniques like anti-debugging and anti-analysis can make it difficult to understand the exact nature of the malicious activity.
These factors must be considered when designing defensive strategies.
Table Comparing and Contrasting DLL Injection Methods
| Injection Method | Strengths | Weaknesses |
|---|---|---|
| Direct Injection using Windows APIs | Relatively simple to implement. | Easily detectable by tools that monitor API calls. |
| Remote Thread Creation | Can hide malicious activity better than direct injection. | Still leaves traces that can be detected by process monitoring tools. |
| System Hooks | Allows for modification of system behavior, making it harder to detect. | Requires deep understanding of the system and can lead to system instability if misused. |
| Code Obfuscation | Makes it more difficult to analyze the code and determine its intent. | Modern security tools can often deobfuscate and analyze the code. |
Combating Evasion Techniques
DLL side-loading attacks often rely on sophisticated evasion techniques to bypass traditional security measures. Understanding these techniques is crucial for developing effective countermeasures. This section focuses on defensive strategies and tools designed to detect and mitigate DLL side-loading threats, bolstering system security posture.
Defensive Strategies Against Evasion Techniques
Various defensive strategies can be employed to counteract the multifaceted nature of DLL side-loading evasion techniques. These strategies, ranging from enhanced monitoring to proactive hardening, collectively contribute to a more resilient security posture.
Security Tools and Technologies for Detection and Mitigation
Numerous security tools and technologies are available to detect and mitigate DLL side-loading threats. These tools leverage various approaches, including behavioral analysis, file integrity monitoring, and network traffic analysis. A robust security infrastructure incorporates these tools for comprehensive threat detection and response.
- File Integrity Monitoring (FIM): FIM solutions track changes to critical system files, including DLLs. Any unauthorized modification triggers an alert, providing a critical early warning system for potential DLL side-loading attacks. This approach complements other security measures by verifying the expected file structure and contents.
- Intrusion Detection and Prevention Systems (IDS/IPS): IDS/IPS solutions monitor network traffic for malicious patterns associated with DLL side-loading attacks. They can detect suspicious network connections, identify malicious code, and block potentially harmful traffic before it reaches the target system.
- Endpoint Detection and Response (EDR) solutions: EDR tools provide real-time monitoring of endpoint activities, including processes and file access. Sophisticated EDR solutions are capable of identifying suspicious DLL loading behavior and blocking or isolating compromised processes.
- Application Whitelisting: Restricting applications to only load authorized DLLs significantly reduces the risk of unauthorized code execution. This proactive approach isolates the system from unknown or potentially malicious code.
Enhancing System Security Posture
Strengthening the overall system security posture is paramount in preventing DLL side-loading attacks. This involves implementing a multi-layered security approach that encompasses multiple defensive strategies. Regular patching, robust access controls, and strong user awareness programs are essential elements.
- Regular Software Updates: Maintaining the latest security patches for operating systems, applications, and security tools is crucial. Patches often address vulnerabilities exploited in DLL side-loading attacks, reducing the attack surface.
- Principle of Least Privilege: Limiting user accounts to the minimum necessary privileges helps prevent unauthorized access and execution of malicious DLLs. This is a cornerstone of a well-designed security strategy.
- Security Awareness Training: Educating users about the risks of DLL side-loading attacks and phishing attempts is crucial. Training empowers users to recognize and report suspicious emails, attachments, and other potential threats.
- Hardening of the System: Applying security configurations and controls to minimize attack vectors and reduce the potential for malicious code execution. Implementing strict policies on the execution of downloaded files or external programs can be effective in mitigating this threat.
Effectiveness of Defensive Strategies
The effectiveness of defensive strategies against different DLL side-loading evasion techniques varies. This table provides a concise overview of how different techniques impact the effectiveness of various defensive approaches.
Fighting threat actors who try to hide malicious DLL side-loading is crucial. One way to do this is to investigate how apps like the Tile Scan Secure feature handle unwanted tracking tags. Recent updates to the Tile Scan secure feature app unwanted tracking tags update might reveal hidden vulnerabilities that can be exploited by threat actors to evade detection.
Understanding these techniques is vital for creating robust defenses against malicious DLL side-loading attacks.
| Defensive Strategy | Effectiveness Against Evasion Techniques |
|---|---|
| File Integrity Monitoring | High effectiveness against simple file-modification evasion. Less effective against more sophisticated techniques. |
| IDS/IPS | High effectiveness against network-based evasion. Less effective against techniques that avoid network interaction. |
| EDR | High effectiveness against behavioral evasion. Excellent for detecting anomalies in process behavior and DLL loading. |
| Application Whitelisting | Very high effectiveness against all DLL side-loading attacks. Requires careful configuration and maintenance. |
Practical Mitigation Strategies and Procedures: Dll Side Loading How To Combat Threat Actor Evasion Techniques
DLL side-loading, while a powerful technique, can be a significant security vulnerability. Implementing robust detection and response mechanisms is crucial to mitigate the risks associated with malicious DLL injection. Effective strategies for identifying, analyzing, and isolating compromised systems are essential to contain and remediate the threat.
DLL side-loading is a tricky security issue, and threat actors are constantly finding new ways to evade detection. One approach to combat this is by analyzing unusual process behavior, much like scrutinizing a sudden surge in gas-guzzling Porsche models – like those highlighted in the recent article on porsche more gas models ev slowdown. This meticulous examination can reveal suspicious patterns and help pinpoint malicious activity.
Ultimately, a layered approach to security, combining various detection methods, is key to stopping DLL side-loading attacks.
Designing a Procedure for Detecting Malicious DLLs
A proactive approach to detecting malicious DLLs involves continuous monitoring of system processes and loaded libraries. A critical aspect of this process is establishing baseline system behavior. This baseline allows for the identification of deviations from normal activity that may indicate malicious DLL loading. Regularly reviewing system logs, particularly those related to process creation and library loading, is vital.
These logs contain valuable insights into the dynamic loading of DLLs. Implementing security information and event management (SIEM) solutions can automate the aggregation and analysis of security logs, providing real-time alerts for suspicious activity.
Analyzing Suspicious DLLs
Thorough analysis of suspicious DLLs is crucial for identifying potential threats. The process begins with detailed examination of the DLL’s metadata, including file attributes, timestamps, and digital signatures. A key step is to analyze the DLL’s code using static and dynamic analysis tools. Static analysis involves examining the DLL’s code without executing it. Dynamic analysis, conversely, executes the DLL in a controlled environment to observe its behavior and identify malicious functionalities.
Utilizing reputable anti-malware tools and sandboxing environments during analysis helps prevent potential harm to the system. For example, tools like VirusTotal can rapidly scan the DLL against a vast database of known malware signatures.
Isolating Affected Systems
Immediately isolating affected systems is a critical step in containing the spread of malicious DLLs. This isolation can be achieved by physically disconnecting the system from the network or implementing network segmentation. A critical aspect of this step is to prevent further infection of other systems. Network segmentation isolates the affected system from the rest of the network.
This reduces the risk of the malware spreading laterally and impacting other critical assets.
Flowchart for Handling a DLL Side Loading Incident
 [Description: A flowchart depicting the incident response process. The flowchart starts with detecting suspicious activity. It then branches into analyzing the DLL, isolating the system, and restoring the system. Each step has specific actions and criteria to move to the next step. For instance, if the analysis reveals malicious intent, the next step is to isolate the system.]
[Description: A flowchart depicting the incident response process. The flowchart starts with detecting suspicious activity. It then branches into analyzing the DLL, isolating the system, and restoring the system. Each step has specific actions and criteria to move to the next step. For instance, if the analysis reveals malicious intent, the next step is to isolate the system.]
Procedure for Handling a DLL Side Loading Incident
| Step | Tools | Responsibilities |
|---|---|---|
| Identify Suspicious Activity | SIEM, log analysis tools | Security analysts, system administrators |
| Isolate Affected System | Network tools, system configuration | Network administrators, system administrators |
| Analyze Suspicious DLL | Static and dynamic analysis tools, anti-malware software | Security analysts, malware researchers |
| Contain and Remediate | Removal tools, system restore points | System administrators, security analysts |
| Review and Improve Procedures | Documentation tools | Security team, incident response team |
[Description: A table outlining the procedure for handling a DLL side loading incident, including steps, tools, and responsibilities. Each step clearly defines the actions required and the personnel responsible for carrying out those actions.]
Dynamic Analysis Techniques for Detection
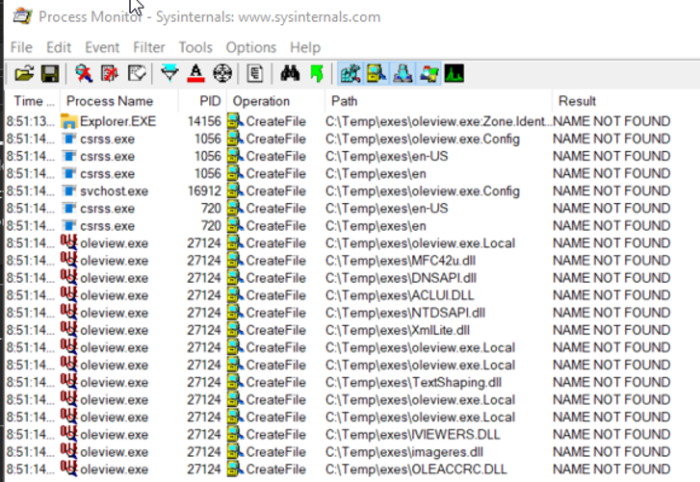
Dynamic analysis techniques are crucial for detecting malicious DLLs loaded during runtime. By observing the behavior of a process as it interacts with a loaded DLL, analysts can uncover suspicious activities that static analysis might miss. This approach allows for a real-time evaluation of the DLL’s actions within the system environment.Dynamic analysis techniques provide a powerful means to identify potentially harmful activities by a DLL.
This approach allows researchers to assess how a DLL behaves in a live environment, detecting anomalies and behaviors indicative of malicious intent. The examination of process behavior during DLL loading is pivotal in this methodology.
Process Monitoring during DLL Loading
Monitoring the behavior of a process during DLL loading is vital for identifying suspicious activities. This involves tracking system calls related to file access, registry manipulation, network communication, and other potentially harmful actions. Observing the sequence and timing of these actions provides valuable context for detecting deviations from expected behavior. For instance, rapid changes to system settings or unexpected network connections initiated by the process can raise suspicion.
Detecting Anomalies in System Behavior
Detecting anomalies in system behavior is critical for identifying malicious DLLs. Anomalies can manifest in various ways, such as unusual file accesses, registry modifications, or unusual network traffic patterns. These anomalies can be identified by comparing the observed behavior to established baselines or expected patterns for normal process execution. Machine learning algorithms can be trained to recognize these anomalies, allowing for the detection of previously unknown attack patterns.
Tools for Dynamic Analysis
Several tools are available for dynamic analysis of DLL side-loading. These tools provide features for observing process behavior, capturing system calls, and analyzing network traffic. They allow analysts to examine the interaction between the process and the loaded DLL in real-time. Examples include debuggers like WinDbg and OllyDbg, which allow for detailed examination of system calls and memory modifications.
Furthermore, tools specializing in process monitoring and analysis can provide a comprehensive view of the process behavior.
Table of Dynamic Analysis Techniques and Tools
| Dynamic Analysis Technique | Corresponding Tools | Description |
|---|---|---|
| System Call Monitoring | WinDbg, Process Monitor | Tracking system calls made by the process during DLL loading, looking for suspicious or unauthorized actions. |
| Memory Analysis | WinDbg, IDA Pro | Examining memory modifications, allocations, and data structures used by the DLL to identify unusual or malicious behavior. |
| Network Traffic Monitoring | Wireshark, tcpdump | Capturing and analyzing network traffic generated by the process during DLL loading, looking for communication with malicious servers or unusual patterns. |
| Registry Modification Monitoring | Process Monitor, RegMon | Monitoring registry changes made by the process and the loaded DLL. |
| Process Behavior Analysis | Process Explorer, SysInternals Suite | Observing process interactions, threads, and resources, looking for unusual or suspicious behavior patterns. |
Static Analysis Techniques for Detection
Static analysis is a crucial component of any robust DLL side-loading detection strategy. It involves examining the code and its associated metadata without actually running the program. This approach is highly valuable for identifying malicious patterns and potential threats embedded within DLLs, allowing for proactive threat prevention before execution. This proactive nature reduces the attack surface and allows for quicker responses to emerging threats.Static analysis techniques provide a way to analyze DLLs to identify potential malicious behaviors or signatures.
By examining the DLL’s structure and contents, security analysts can often detect suspicious code or patterns that would otherwise only be visible during runtime. This analysis method is often the first line of defense against DLL-based attacks, enabling the identification of potential threats well before they can manifest themselves.
Analyzing DLL Headers
DLL headers contain crucial metadata about the DLL, including its version, dependencies, and other important attributes. Analyzing these headers is essential for identifying potential malicious characteristics. Malicious actors may manipulate header information to evade detection or mask their true intentions.Examining the DLL’s entry point, export functions, and other header attributes can reveal irregularities. For example, a suspicious number of exports or an unusual entry point could be red flags, potentially indicating an attempt to conceal malicious functionality.
Analyzing DLL Imports, Dll side loading how to combat threat actor evasion techniques
DLL imports list the functions the DLL calls from other libraries. A significant part of static analysis involves carefully scrutinizing these imports. Malicious actors may use legitimate imports to mask malicious activity, making the analysis more complex.Unusual or unexpected imports from libraries not commonly associated with the DLL’s function are potential indicators of malicious intent. Moreover, the frequency and nature of these imports can be analyzed to detect patterns suggestive of malicious activity.
For instance, imports to system libraries for unauthorized file access or network communication are significant red flags.
Identifying Malicious Code Signatures
Malicious code often contains unique characteristics or signatures that can be identified through static analysis. These signatures can range from specific instructions to patterns in data structures. Tools that can analyze and identify these signatures are critical for automating the detection process.These signatures can be part of known malicious code families or contain specific strings that can indicate malicious functionality.
By scanning the DLL’s code for known malicious signatures, security systems can proactively detect and prevent potential threats.
Static Analysis Techniques and Use Cases
| Technique | Description | Use Case |
|---|---|---|
| Import Address Table (IAT) Analysis | Examines the imported functions and their addresses to detect suspicious patterns or unusual calls. | Identifying hidden or malicious API calls. |
| Code Signature Verification | Validates the digital signature of the DLL to ensure it hasn’t been tampered with. | Verifying the authenticity of the DLL. |
| String Analysis | Searches for suspicious strings or s within the DLL’s code. | Detecting malicious commands, URLs, or hardcoded paths. |
| Control Flow Graph (CFG) Analysis | Creates a visual representation of the program’s execution flow to identify unusual or complex logic. | Detecting obfuscated or complex malicious algorithms. |
| PE Header Analysis | Examines the Portable Executable (PE) header to find potential malicious modifications or anomalies. | Detecting malicious code packing or modifications to the header. |
Integrating Static Analysis into a Security Monitoring Pipeline
Static analysis tools can be integrated into a security monitoring pipeline to automatically scan DLLs and report potential threats. This proactive approach is essential for preventing malicious DLLs from being loaded and executed. A robust pipeline should consist of a combination of automated tools and human review to maintain accuracy and efficiency.The pipeline can be configured to automatically scan new or updated DLLs against a database of known malicious signatures and patterns.
Results from the static analysis should be correlated with other security data points to provide a more comprehensive understanding of the threat landscape.
Developing Robust Security Monitoring Solutions
Building a robust security monitoring solution for DLL side-loading requires a multi-faceted approach that combines both proactive and reactive measures. This involves scrutinizing the entire process, from initial code execution to final DLL interaction, to identify and mitigate potential threats. The core principle is to detect anomalies and suspicious behaviors that deviate from expected patterns, effectively acting as a shield against sophisticated evasion techniques.
Developing a Comprehensive Monitoring Solution
A comprehensive monitoring solution should encompass a broad range of analysis techniques to detect DLL side-loading attempts and associated evasion strategies. It needs to be adaptable to various attack vectors and capable of evolving alongside emerging threats. This requires integrating multiple layers of security controls, each contributing unique insights to the overall threat detection picture.
Incorporating Dynamic and Static Analysis
Dynamic analysis, observing the execution of code in real-time, provides insights into the behavior of loaded DLLs. This involves observing file system activity, registry modifications, network connections, and process interactions. Static analysis, examining the code without execution, helps identify malicious patterns within DLL code. Combining these techniques offers a more complete picture of the threat, allowing for the identification of both the initial attempt to load the DLL and the underlying malicious intent.
Integrating Monitoring Solutions into Existing Infrastructure
Integrating the monitoring solution into existing security infrastructure is crucial for seamless operation. This should involve integrating with existing intrusion detection systems (IDS), security information and event management (SIEM) systems, and endpoint detection and response (EDR) tools. The integration should ensure data flow and correlation across various security tools, allowing for a unified view of the threat landscape.
This centralized approach simplifies threat analysis and facilitates rapid response.
Customizing Monitoring Tools for Evasion Detection
Monitoring tools need to be adaptable and customizable to detect specific evasion techniques. This involves developing custom rules and signatures that specifically identify techniques like obfuscation, anti-debugging, or polymorphism. These rules should be regularly updated to counter the evolving tactics of threat actors. Tools should also be equipped with machine learning capabilities to detect novel and previously unseen evasion techniques.
Components of a Comprehensive Security Monitoring Solution
| Component | Description | Integration Points |
|---|---|---|
| Dynamic Analysis Engine | Monitors system activity in real-time, observing file operations, registry changes, and network interactions. | Endpoint agents, network taps, security information and event management (SIEM) |
| Static Analysis Engine | Examines the code of DLLs without execution, looking for malicious code patterns and known indicators of compromise (IOCs). | Code repositories, package managers, threat intelligence feeds |
| Behavioral Analysis Engine | Identifies anomalies in application behavior, including unusual process interactions, unexpected network activity, and unusual file access patterns. | Endpoint agents, network taps, security information and event management (SIEM) |
| Threat Intelligence Feed | Provides up-to-date information on emerging threats, evasion techniques, and associated indicators of compromise (IOCs). | Dynamic and static analysis engines, behavioral analysis engine |
| Security Information and Event Management (SIEM) System | Centralized platform for collecting, correlating, and analyzing security events from various sources. | All components of the monitoring solution |
Final Review

In conclusion, securing against DLL side loading attacks requires a multi-faceted approach, combining technical expertise with proactive security measures. By understanding the tactics employed by threat actors, implementing effective detection methods, and establishing robust response procedures, organizations can significantly mitigate the risks associated with DLL side loading. The practical strategies and defensive techniques Artikeld in this article empower security professionals to effectively combat this persistent threat.












