Uk government reportedly demands backdoor access your apple icloud account – UK government reportedly demands backdoor access to your Apple iCloud account, raising serious concerns about privacy and security. This bold move sparks debate about the balance between national security and individual rights. The request, if legitimate, could have far-reaching implications for digital security globally, prompting a crucial discussion about the potential risks and solutions.
This article delves into the background of government requests for digital access, examining the legal and ethical considerations, and the potential consequences for users, technology companies, and international relations. It will also explore alternative solutions, public perception, technical implications, and the potential legal challenges.
Government Demands for Digital Access
The ongoing tension between government surveillance needs and individual privacy rights is a critical issue in the digital age. Governments worldwide increasingly seek access to encrypted communications and digital data, often citing national security concerns. This raises complex questions about the balance between security and liberty, particularly in the context of digital privacy and freedom of expression.The digital landscape has evolved rapidly, creating new avenues for both communication and potential threats.
This evolution has, in turn, necessitated a re-evaluation of existing legal frameworks and ethical considerations surrounding government access to digital information. The increasing reliance on encrypted communication platforms and the use of cloud services have made it more challenging for governments to monitor activities, while simultaneously raising the stakes for those seeking to safeguard their privacy.
Historical Overview of Government Requests
Governments have historically sought access to communication data for various reasons, ranging from law enforcement to national security. The advent of telecommunications technology and the subsequent digital age has broadened the scope and sophistication of these requests, requiring governments to adapt to new technologies and security challenges. Early forms of wiretapping and surveillance were often limited to phone calls and physical mail, whereas today’s requests extend to internet activity, social media posts, and encrypted messaging.
This shift underscores the evolving nature of the digital threat landscape.
Legal and Ethical Considerations
Legal frameworks governing government access to digital data vary significantly across jurisdictions. Some countries have specific laws that permit access to communications under certain circumstances, often tied to investigations of criminal activity or national security threats. However, these laws are frequently challenged on ethical grounds, raising concerns about potential abuses of power and the chilling effect on free speech and association.
The balance between national security and individual privacy remains a constant source of debate and legal scrutiny.
Potential Implications for User Privacy and Security
Government access to digital data has significant implications for user privacy and security. If the legal framework is not properly defined or if procedures for access are not transparent, it can lead to a breakdown of trust between citizens and their government. The potential for misuse of collected data, or the collection of data beyond the scope of the legal framework, poses substantial threats to personal privacy.
This risk is exacerbated when data collection and surveillance practices are not adequately scrutinized or audited.
Role of International Law and Agreements
International agreements and treaties play a crucial role in shaping the landscape of government access to digital data. These agreements often address issues of mutual legal assistance, extradition, and data protection. However, the application and interpretation of these international frameworks can vary considerably among signatory countries. Differences in legal systems, cultural norms, and national security priorities can lead to diverse interpretations of these agreements and their implications for digital access requests.
Comparison of Countries’ Approaches
| Country | Approach | Legal Basis | Privacy Concerns |
|---|---|---|---|
| United States | Historically broad powers granted to government agencies for national security. | Various statutes, including the Foreign Intelligence Surveillance Act (FISA). | Concerns exist about potential overreach and lack of transparency in surveillance programs. |
| United Kingdom | Legislation permitting access to communications data for law enforcement and national security. | Various statutes and regulations. | Concerns about the scope of powers granted to law enforcement and the potential for abuse. |
| Germany | Stringent data protection laws and limitations on government access. | Data Protection Act and similar legislation. | Strong emphasis on protecting fundamental rights and freedoms. |
The table above highlights the diverse approaches taken by different countries to government access requests. Each country’s approach reflects its unique legal and cultural context, and the balance it seeks to strike between security and privacy.
The UK government’s reported demand for backdoor access to Apple iCloud accounts is raising serious privacy concerns. While this is a major issue, it’s worth remembering that tech updates are constantly happening – like the new emoji additions on your iPhone. For instance, check out this fascinating article about all the new additions, including a pink heart, on a pink heart isnt the only new emoji on your iphone.
Ultimately, the government’s request for this access highlights a crucial balance between security and individual privacy rights.
Specifics of the Reported Demand

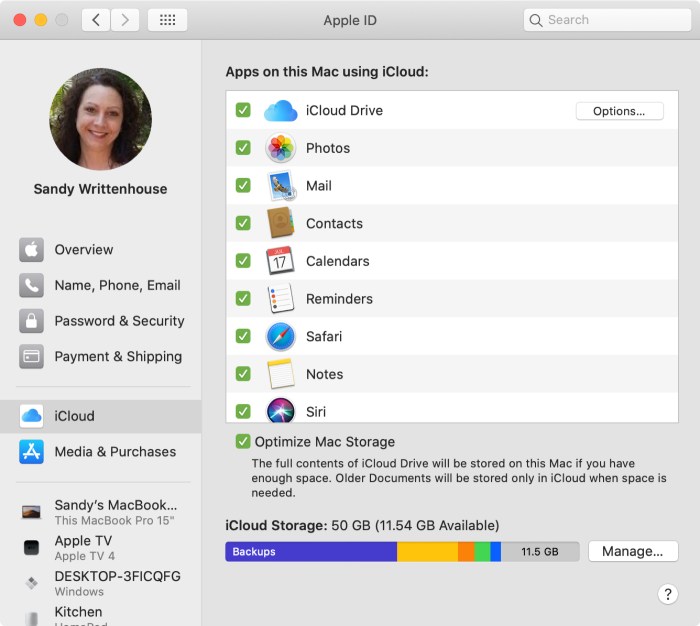
Recent reports suggest the UK government is seeking backdoor access to Apple iCloud accounts. This demand, if verified, raises significant concerns about data privacy and the balance between national security and individual liberties. The potential implications for both technology companies and citizens are substantial.The specifics of the demand are still emerging, but reports indicate a desire for the ability to access encrypted data stored within iCloud.
This would effectively bypass Apple’s security measures, allowing authorities to potentially access user information without explicit user consent.
Reported Data Sought
The types of data reportedly sought are extensive and potentially intrusive. This includes personal communications, location data, browsing history, and other sensitive information stored within iCloud accounts. The breadth of this request is alarming, raising concerns about the potential for misuse of this access.
Purported Justification for the Request
The government’s purported justification for this demand centers on national security concerns. The claim is that this access is necessary to combat terrorism and other serious crimes. However, critics argue that such broad access could potentially harm the security of ordinary citizens and erode trust in technology companies.
Examples of Similar Requests in the Past
Several countries have, in the past, sought similar access to encrypted data. These instances often sparked significant debate and controversy, with privacy advocates raising concerns about the potential for abuse. For instance, the debate around the USA’s PRISM program raised similar issues about government access to private communications. These historical examples highlight the delicate balance between national security and individual privacy rights.
Potential Impacts on Stakeholders
| Stakeholder | Potential Impact | Positive Impact | Negative Impact |
|---|---|---|---|
| Apple | Potential legal and reputational challenges, as well as disruption of business operations. Their security protocols could be compromised, potentially leading to broader security concerns for other companies. | Potentially, the government could provide specific and verifiable information to support the need for this access, thus alleviating concerns from users. | Damage to their brand image, erosion of user trust, and potential legal battles, impacting their future business practices and development of secure technologies. |
| iCloud users | Significant erosion of privacy, potential for misuse of personal data, and the loss of control over their own information. | Potentially, enhanced security of the country if used appropriately and transparently. | Increased risk of surveillance, potential for targeted harassment, and the chilling effect on free speech and expression. |
| UK Government | Potential for increased security and the ability to combat serious crimes. | Potentially, an effective tool for national security, if used transparently and with safeguards. | Damage to international reputation, undermining trust in technology companies, and potentially leading to negative international relations. |
Potential Consequences
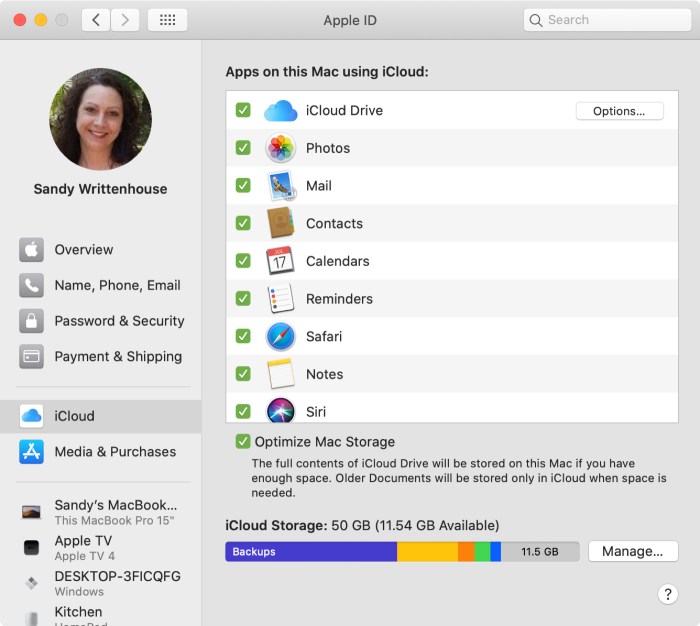
The reported demand by the UK government for backdoor access to Apple iCloud accounts raises serious concerns about the potential consequences for individuals, public trust, and international relations. This unprecedented request necessitates a careful examination of the possible ramifications. The government’s justification must be thoroughly scrutinized, and the potential for abuse considered alongside the potential benefits.The government’s request for access to encrypted data carries significant risks for individuals.
This kind of access could be exploited by malicious actors, compromising sensitive information and potentially leading to identity theft, financial fraud, and other forms of harm. The potential for misuse of such power is a critical consideration.
Consequences for Individuals
The access granted to the government could compromise the privacy and security of countless individuals. This includes access to personal communications, financial records, and other sensitive data. The potential for unauthorized access and misuse is substantial, impacting individuals’ well-being and security. A lack of clear safeguards could lead to widespread breaches of personal privacy.
Impact on Public Trust
The government’s demand for backdoor access will inevitably erode public trust in both government institutions and technology companies. This erosion of trust can have long-term implications for the relationship between citizens and their government, as well as between users and technology providers. Concerns over privacy and security will likely increase, potentially leading to a reluctance to adopt new technologies or share personal information.
The UK government’s reported demand for backdoor access to Apple iCloud accounts is raising serious privacy concerns. It’s a bit unsettling, given the recent precedent set in the Alex Jones Sandy Hook defamation trial verdict fine, which highlights the potential for misuse of such access. This kind of government overreach is worrying, and it’s important to question the justification for these requests in the context of safeguarding national security versus individual rights, especially when considering the implications for future digital freedoms.
alex jones sandy hook defamation trial verdict fine serves as a stark reminder of the importance of upholding these rights in the digital age. The UK government’s demands for backdoor access to iCloud accounts are, therefore, a cause for concern.
The perceived power imbalance between the state and the individual is a major concern.
Ramifications for International Relations, Uk government reportedly demands backdoor access your apple icloud account
The UK’s actions could set a dangerous precedent, encouraging other governments to pursue similar demands. This could trigger a global race to gain access to encrypted communications, potentially destabilizing international relations and creating a climate of distrust between nations. The potential for international legal challenges and diplomatic tensions is significant. This approach could lead to international condemnation and the UK’s isolation on the global stage.
Comparison with Similar Situations
Numerous historical and contemporary examples highlight the dangers of granting governments unchecked access to encrypted data. The erosion of privacy in the name of security has been a recurring theme in history. Such examples serve as cautionary tales, demonstrating the potential for misuse and the need for robust safeguards. The Snowden revelations, for instance, demonstrated the potential for misuse of such access.
There are numerous historical examples where similar demands, under the guise of security, ultimately led to detrimental outcomes.
Examples of Successful Legal Challenges
Several legal challenges to government demands for access to encrypted data have been successful. These examples underscore the importance of robust legal frameworks and the potential for individuals and organizations to defend their privacy rights. These challenges often highlight the importance of due process and the need for transparency in government actions.
Possible Legal Challenges
| Legal Argument | Supporting Evidence | Potential Outcome |
|---|---|---|
| Violation of fundamental rights to privacy and freedom of communication. | International human rights instruments, national constitutions, and legal precedents. | Success depends on the specific legal framework and the strength of the evidence presented. |
| Lack of proportionality between the security threat and the intrusive nature of the demand. | Evidence demonstrating a lack of direct threat or a less intrusive alternative. | Potentially successful, especially if the government’s justification is weak or if a less intrusive solution is available. |
| Unlawful overreach of government power. | Demonstrating that the demand exceeds the government’s legitimate powers. | Success depends on the specific legal framework and the court’s interpretation of the government’s authority. |
Alternative Solutions
The government’s demand for backdoor access to Apple iCloud accounts raises critical concerns about user privacy and data security. Finding a balance between national security needs and individual rights is paramount. This section explores alternative solutions that can satisfy the government’s objectives without compromising the fundamental right to privacy.
Data Minimization and Targeted Access
The government’s need for access to specific data can be addressed without requiring unrestricted access to entire accounts. Techniques like data minimization, which focuses on collecting only the necessary information, are crucial. A robust framework for identifying and specifying the exact data points required in each case is essential. This approach ensures that the government obtains the specific information it needs without compromising the broader data of the user.
Secure Data Acquisition Methods
Alternative methods of data acquisition can minimize privacy risks. For instance, encrypted channels and secure storage protocols can be employed to handle sensitive data. This approach ensures that the data remains confidential during transmission and storage, preventing unauthorized access or breaches.
Legal Frameworks and International Best Practices
Existing legal frameworks can be adapted to facilitate such requests while upholding user rights. Specific regulations and laws governing data retention, access, and usage should be reviewed and revised to reflect the evolving technological landscape. International best practices for balancing security and privacy should be studied, and collaborations with other jurisdictions should be encouraged to ensure a comprehensive and adaptable approach.
Alternative Methods for Data Access
| Method | Description | Strengths | Weaknesses |
|---|---|---|---|
| Controlled Access Protocols | Implementing secure protocols that allow for limited, controlled access to specific data points within an account. | Preserves user privacy by limiting access to only the necessary data. | Requires careful design to prevent unintended access and data leakage. |
| Third-Party Data Intermediaries | Engaging a trusted third party to extract and securely deliver the targeted data to the government, without granting access to the entire account. | Offers a secure and streamlined method for data retrieval. | Raises potential concerns about data security and potential bias in the intermediary. |
| Encrypted Data Extraction Tools | Developing or utilizing tools that can extract data while respecting the encryption of the account. | Maintains user data security while allowing data retrieval. | Requires significant technical expertise and investment. |
| Judicial Oversight and Warrants | Strict adherence to legal procedures and warrants to access data, ensuring judicial oversight and protection of user rights. | Safeguards against arbitrary access to user data. | The process may be time-consuming and potentially slow. |
Public Perception and Debate: Uk Government Reportedly Demands Backdoor Access Your Apple Icloud Account
The reported UK government demand for backdoor access to Apple iCloud accounts has ignited a firestorm of public debate, raising concerns about privacy, security, and the balance of power between citizens and the state. Public reaction has been varied and complex, ranging from outright condemnation to cautious acceptance, highlighting the deeply entrenched positions on digital rights and national security.
This section explores the diverse perspectives and the significant role media plays in shaping the narrative.
Public Reaction to the Reported Demand
Public reaction to the reported demand has been polarized. A significant portion of the population, particularly those concerned with privacy, has voiced strong opposition. Concerns about potential misuse of access and the precedent this sets for future surveillance have been widely discussed. Conversely, some have argued for the need for such access in combating crime and terrorism, viewing it as a necessary tool for national security.
This initial reaction underscores the delicate balance between security and liberty.
Arguments for and Against the Request
Proponents of the government’s request often cite national security as the primary justification. They argue that access to encrypted data is crucial for law enforcement in combating terrorism and serious crime. They emphasize the importance of protecting citizens from harm and the need for law enforcement agencies to have the tools necessary to investigate potential threats. Opponents, however, highlight the potential for abuse and the chilling effect this could have on personal privacy.
They raise concerns about the potential for government overreach and the possibility of misuse of the access, emphasizing the importance of individual freedoms and rights in a democratic society.
Potential Impact on Public Opinion
The reported demand has the potential to significantly impact public opinion on digital privacy and national security. Public trust in government institutions could be eroded if the demand is perceived as an infringement on personal liberties. Conversely, public support for the government might increase if the demand is framed as a necessary measure to combat crime and terrorism.
The UK government’s reported demand for backdoor access to Apple iCloud accounts is deeply concerning. While this raises serious privacy concerns, it’s a stark contrast to initiatives like Lyft’s new safety features for women and nonbinary users, a positive step in fostering a safer digital environment. These features, as highlighted in lyft launches safety feature for women and nonbinary users , show a commitment to security from a different perspective, highlighting the need for balance between security and privacy.
Ultimately, the government’s push for access to personal data, in the case of iCloud, needs careful consideration and public discussion, especially in light of these evolving approaches to safety.
This underscores the importance of transparency and communication in managing public perception during such sensitive events.
Role of Media in Shaping Public Discourse
The media plays a critical role in shaping public discourse surrounding the reported demand. News outlets and social media platforms have been instrumental in disseminating information and opinions on the issue. The way the media frames the debate – whether emphasizing privacy concerns or national security needs – can significantly influence public perception. This underscores the importance of media objectivity and responsible reporting.
Summary of Different Viewpoints
| Viewpoint | Argument | Supporting Evidence |
|---|---|---|
| Pro-Government Access | National security necessitates access to encrypted data for law enforcement to combat crime and terrorism. | Arguments frequently cite hypothetical scenarios where such access was crucial in apprehending criminals or preventing attacks. |
| Pro-Privacy | Granting backdoor access to encrypted data sets a dangerous precedent for future surveillance and compromises personal privacy. | Arguments frequently cite historical examples of government overreach and potential for misuse of such powers. |
| Cautious | Balancing national security with individual liberties is crucial, and a more nuanced approach is required. | Advocates for this view often propose alternative solutions that could address security concerns without compromising privacy. |
Technical Implications
The government’s reported demand for backdoor access to encrypted data raises profound technical challenges. This demand directly impacts the security and privacy of individuals and organizations. The implications extend far beyond the specific case, potentially setting a dangerous precedent for future government interventions in digital spaces. Understanding the intricacies of encrypted data access is crucial for assessing the feasibility and potential consequences of such a demand.
Accessing Encrypted Data
The process of accessing encrypted data involves reversing the encryption process, which is a computationally intensive task. The complexity of encryption algorithms varies greatly, with some being relatively simple and others extremely complex. The strength of encryption lies in the difficulty of reversing the process without the decryption key. The security of encrypted data depends heavily on the strength of the algorithm and the length of the encryption key.
The more complex the algorithm and the longer the key, the harder it is to crack.
Bypassing Security Measures
Bypassing security measures, such as those employed in Apple’s iCloud, is a significant technical undertaking. The encryption methods used by Apple are sophisticated and regularly updated to counter emerging threats. Attempts to circumvent these measures would likely require substantial resources and expertise. The security of these systems is constantly evolving, making any attempt to breach them a moving target.
The potential for success in bypassing security measures depends greatly on the specific encryption methods used and the resources available to the attacker. Historical cases of security breaches often highlight the importance of strong security protocols and continuous vulnerability assessments.
Cryptography’s Role in Data Protection
Cryptography plays a crucial role in protecting data by transforming it into an unreadable format. This process, known as encryption, safeguards sensitive information from unauthorized access. Modern cryptography relies on complex mathematical algorithms to ensure the confidentiality, integrity, and authenticity of data. The cryptographic algorithms used in systems like iCloud are designed to be resistant to various attacks.
The security of the system depends on the robustness of the cryptographic methods used and the management of the cryptographic keys.
Implications for Cybersecurity in General
The potential for government-mandated backdoor access has profound implications for cybersecurity in general. If such a demand is granted, it could encourage future attacks on encrypted systems. The existence of such a backdoor could potentially be exploited by malicious actors, including nation-states or criminal organizations. This could lead to a significant erosion of trust in digital systems and a weakening of the security infrastructure.
The widespread adoption of encryption is a crucial element of cybersecurity and this demand poses a direct threat to this paradigm.
Comparison of Encryption Methods
| Encryption Method | Strengths | Weaknesses |
|---|---|---|
| Symmetric-key encryption (e.g., AES) | Fast, efficient, suitable for large datasets | Key management is a significant challenge; if the key is compromised, all encrypted data is vulnerable. |
| Asymmetric-key encryption (e.g., RSA) | Strong key management; suitable for secure communication and digital signatures. | Slower than symmetric-key encryption; vulnerable to certain mathematical attacks if not implemented correctly. |
| Hashing algorithms (e.g., SHA-256) | Ensures data integrity; widely used in digital signatures and password storage. | Cannot be reversed to recover the original data; not suitable for confidentiality. |
This table provides a basic comparison of common encryption methods. Each method has its own set of advantages and disadvantages, and the choice of method depends on the specific security requirements of the application.
Closing Notes
The UK government’s reported demand for iCloud backdoor access highlights a critical tension between national security and individual liberties. The implications are significant, potentially setting a dangerous precedent for government access to encrypted data worldwide. This situation underscores the urgent need for robust legal frameworks and alternative solutions that safeguard both security and privacy. The ongoing debate promises to shape the future of digital rights and security, and its resolution will have long-lasting effects.