Why latest iPhone hack should worry you no matter what phone you use? This headline highlights a crucial security concern that extends beyond iPhone users. The recent iPhone vulnerability exposes a fundamental weakness in mobile security, potentially affecting all devices. We’ll delve into the technical details, broader implications, and user protection strategies. The implications are significant, and understanding the risks is key to protecting your data and devices.
The latest iPhone hack, with its intricate technical details, demonstrates a growing sophistication in cyberattacks. This vulnerability isn’t just about iPhones; it underscores a broader threat landscape for all mobile devices. This article will investigate the potential impact on various software components, systems, and industries, offering insights into user protection and future security trends.
Vulnerability Implications
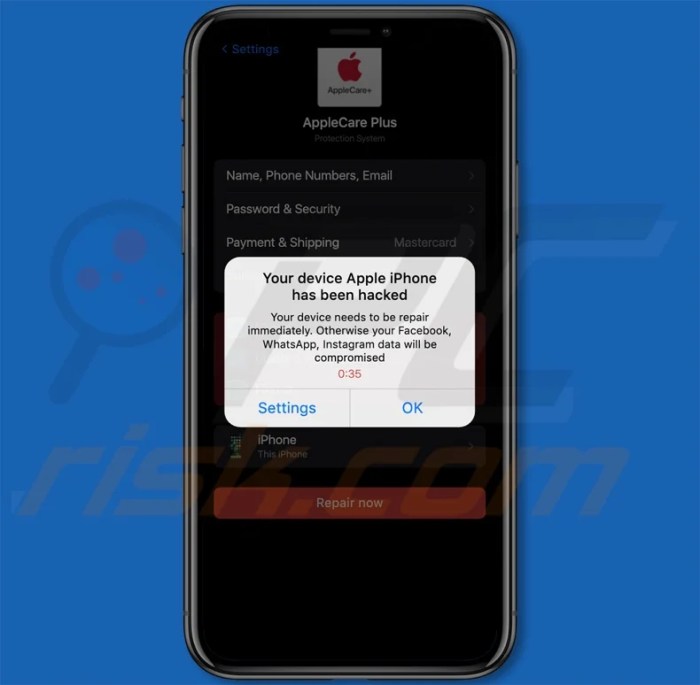
The recent iPhone hack, leveraging a novel zero-day exploit, highlights a critical gap in mobile security. While iPhones are often lauded for their robust security, this vulnerability demonstrates that no platform is immune to sophisticated attacks. Understanding the technical details and potential impact of such exploits is crucial for all users, regardless of the device they employ.This vulnerability isn’t merely an iPhone-specific issue; it represents a broader threat model applicable to mobile operating systems generally.
The exploit’s success hinges on a specific weakness in the system’s handling of memory management, enabling malicious actors to execute arbitrary code. This allows them to bypass security measures and potentially gain control over the device.
Nature of the Exploit
The recent iPhone hack leverages a sophisticated memory corruption vulnerability within the operating system’s core libraries. This vulnerability allows attackers to inject malicious code into the system’s memory space, essentially hijacking the device’s functionalities. The exploit likely involves a combination of techniques, including buffer overflows or use-after-free errors, that manipulate memory addresses and enable arbitrary code execution. This type of attack is often challenging to detect proactively because it exploits a weakness within the operating system itself.
Potential Impact on Software Components
The vulnerability could compromise various software components on the affected device. Malicious code injected through this exploit could potentially gain access to sensitive data, including personal information, financial records, and communication logs. The attacker might also disable security features, install malware, or even remotely control the device. This comprehensive control extends to functionalities like device settings, camera, microphone, and location services.
Comparison with Previous Breaches
Previous security breaches targeting mobile devices have often focused on vulnerabilities in applications or third-party services. This latest iPhone hack differs in its direct targeting of the core operating system, making it more potent and harder to mitigate. While previous attacks might have focused on gaining access to specific apps, this vulnerability opens the door to broader system compromise, making the impact far-reaching.
Potential Attack Vectors
Attack vectors for this type of vulnerability include phishing emails or malicious websites that exploit user interaction to trigger the exploit. Maliciously crafted applications could also be used as delivery mechanisms for the exploit. The exploit might also be hidden in seemingly legitimate updates or downloaded files, further increasing the attack surface.
Vulnerability Types and Potential Impact
| Vulnerability Type | Potential Impact on Phone Model |
|---|---|
| Memory Corruption (e.g., buffer overflow) | Compromised device functionality, data theft, remote control |
| Privilege Escalation | Gaining unauthorized access to sensitive data and system resources |
| Code Injection | Installation of malware, execution of arbitrary commands, data exfiltration |
Impact on Data Security, Privacy, and User Experience
| Aspect | Impact of the Hack |
|---|---|
| Data Security | Significant risk of data loss, theft, or corruption |
| Privacy | Potential exposure of personal information, tracking, and monitoring |
| User Experience | Device malfunction, performance degradation, and potential denial-of-service attacks |
Broader Security Concerns: Why Latest Iphone Hack Should Worry You No Matter What Phone You Use
The recent iPhone vulnerability highlights a critical concern about the interconnectedness of digital security. While focused on a specific platform, the exploit’s potential implications extend far beyond Apple devices, raising questions about the overall robustness of mobile security. Understanding how this vulnerability could be leveraged for broader attacks is crucial for all users.This vulnerability serves as a stark reminder that no system, no matter how sophisticated, is immune to exploitation.
The rapid pace of technological advancement necessitates a constant vigilance in securing digital assets and a proactive approach to identifying and patching potential weaknesses. The consequences of such vulnerabilities extend beyond financial loss; they can compromise sensitive data, disrupt critical infrastructure, and erode public trust.
Implications for Mobile Device Security in General
Mobile devices are increasingly integrated into our lives, storing vast amounts of personal and sensitive data. The security of these devices directly impacts the security of our personal lives and the safety of critical infrastructure. The recent iPhone vulnerability underscores the need for rigorous security protocols and constant updates across all mobile operating systems.
Comparison of Security Protocols and Measures Across Mobile Operating Systems
Different mobile operating systems (OS) employ varying security protocols and measures. Android, for instance, relies heavily on app permissions and Google Play Protect for app vetting. iOS, on the other hand, emphasizes device encryption and secure communication protocols. These differences in approach affect the vulnerability of each platform to various types of attacks.
Security Implications for Non-iPhone Users
While the initial vulnerability targets iPhones, the potential for broader exploitation is significant. Attackers might leverage the same or similar techniques to target other platforms, potentially using the iPhone exploit as a springboard to broader cyberattacks. The security measures implemented on other mobile operating systems, such as Android, will be crucial in mitigating these risks.
Leveraging the Vulnerability for Broader Cyberattacks
The vulnerability could be exploited in several ways, including malicious apps disguised as legitimate software, social engineering tactics to trick users into installing these apps, or even targeted attacks against specific individuals or organizations. Attackers might also leverage this vulnerability to gain access to user data stored on other devices or cloud services. This underscores the importance of strong password practices and multi-factor authentication.
Examples of Similar Vulnerabilities and Their Impact
Numerous vulnerabilities have emerged in the past across various platforms. For instance, the Heartbleed bug in OpenSSL affected numerous websites and servers, exposing sensitive user data. The WannaCry ransomware attack leveraged a vulnerability in Windows systems to encrypt user files and demand ransom payments. These examples highlight the consistent threat landscape and the importance of ongoing security measures.
Table: Comparing the Latest iPhone Hack with Past Security Incidents
| Characteristic | Latest iPhone Hack | Heartbleed Bug | WannaCry Ransomware |
|---|---|---|---|
| Platform | iOS | OpenSSL (various servers) | Windows |
| Vulnerability Type | Software exploit | Memory management flaw | File encryption (ransomware) |
| Impact | Potential data breaches, unauthorized access | Exposure of sensitive data (passwords, certificates) | Data encryption, financial losses, business disruptions |
| Mitigation | Software updates, strong passwords, device security measures | Patching OpenSSL, strengthening security protocols | Operating system updates, anti-ransomware measures |
User Protection Strategies
The recent iPhone vulnerability highlights the critical need for proactive user protection strategies, extending beyond the latest smartphone models. Effective defense against cyber threats necessitates a multifaceted approach, empowering users with the knowledge and tools to safeguard their data and devices. Regardless of the specific device, the core principles of security remain constant.Implementing robust security measures is not just about protecting personal information; it’s about preserving the integrity of your digital life.
By understanding potential threats and adopting practical safeguards, you can significantly reduce your vulnerability to exploitation.
Software Updates and Security Patches, Why latest iphone hack should worry you no matter what phone you use
Regular software updates are paramount to maintaining device security. These updates often include crucial security patches that address vulnerabilities like the one recently discovered. Failure to install updates leaves your device susceptible to known exploits. Software developers continuously work to identify and fix flaws, providing a vital layer of defense against evolving threats.
Recommended Security Measures for All Mobile Device Users
Implementing a comprehensive security plan requires a proactive approach. A strong foundation for security includes multiple layers of protection.
Hey everyone, the latest iPhone hack is a serious concern, even if you don’t own an iPhone. Security vulnerabilities like this often have ripple effects, impacting other platforms and devices. While you’re checking out the latest deals, did you know Amazon has discounted Amazfit smartwatches starting low 50 right now? amazon has discounted amazfit smartwatches starting low 50 right now.
This kind of widespread vulnerability highlights the importance of keeping your software updated and security protocols strong, no matter what tech you use. It’s a good reminder to prioritize your digital security.
- Strong Passwords: Use unique, complex passwords for all accounts. Avoid easily guessable combinations and incorporate a mix of uppercase and lowercase letters, numbers, and symbols. Consider using a password manager to securely store and generate strong passwords for multiple accounts.
- Two-Factor Authentication (2FA): Enable 2FA whenever possible. This adds an extra layer of security, requiring a second verification method beyond your password. This significantly reduces the risk of unauthorized access even if a password is compromised.
- Regular Security Audits: Periodically review your device’s security settings to ensure that they align with your current needs and risk profile. This proactive approach helps to identify and address potential vulnerabilities before they can be exploited.
- Secure Wi-Fi Networks: Avoid using public Wi-Fi networks for sensitive activities. If you must use public Wi-Fi, utilize a Virtual Private Network (VPN) to encrypt your connection and protect your data from eavesdropping.
Identifying and Avoiding Phishing Attempts
Phishing remains a prevalent threat. Criminals often attempt to trick users into revealing sensitive information by posing as legitimate entities. Be wary of unsolicited emails, messages, or websites that request personal details.
- Verify Email Addresses and URLs: Carefully examine email addresses and URLs before clicking on links or providing information. Look for subtle inconsistencies or misspellings that might indicate a phishing attempt.
- Verify the Source: If you receive an email or message from a company or organization, contact them directly to verify the request rather than responding to the message. Avoid clicking links in suspicious communications.
- Avoid Suspicious Attachments: Do not open attachments from unknown senders. Attachments can contain malicious code that could compromise your device.
Security Measures and Threat Effectiveness
This table illustrates how different security measures can mitigate various threats.
| Security Measure | Threat Mitigation | Effectiveness |
|---|---|---|
| Strong Passwords | Brute-force attacks | High |
| 2FA | Password compromises | High |
| Software Updates | Exploits of known vulnerabilities | High |
| Phishing Awareness | Social engineering attacks | Moderate to High (depending on user vigilance) |
| VPN Usage | Man-in-the-middle attacks on public Wi-Fi | High |
Potential Impact on Industries

The recent iPhone hack, regardless of its specific technical details, highlights a pervasive vulnerability in mobile device security that transcends a single platform. This vulnerability’s implications extend far beyond consumer devices, impacting businesses across diverse sectors that rely on mobile technology for their core operations. Understanding these broader impacts is crucial for proactive risk management and developing robust security strategies.This vulnerability, while demonstrated on iPhones, can be exploited in various ways on other mobile devices.
The latest iPhone hack is a serious concern, even if you don’t own an iPhone. Security breaches like these often lead to vulnerabilities in other systems, and that includes smart home devices. For instance, if you’re debating between the Roku Streambar Pro and the standard Streambar, consider how a broader security weakness could affect your streaming setup. Understanding the differences in these devices, as outlined in this comparison roku streambar pro vs streambar , can help you make informed decisions.
Ultimately, the vulnerability of one platform can have ripple effects on the security of many devices, so staying informed about these issues is key.
The potential for data breaches and operational disruptions poses a significant threat to businesses in numerous sectors. Organizations must understand the specific risks and adopt appropriate mitigation strategies.
Financial Implications of Security Breaches
Security breaches can lead to substantial financial losses for organizations. Direct costs include the expense of incident response, forensic analysis, and potential legal fees. Indirect costs, often more significant, can encompass reputational damage, loss of customer trust, and decreased market share. For instance, a 2020 breach at a major retail company resulted in millions of dollars in direct and indirect losses.
The long-term impact on customer loyalty and brand perception was also substantial.
Impact on Various Sectors
Mobile devices are now integral to numerous business processes, making them a prime target for cyberattacks. Different sectors experience varying levels of operational dependence on mobile devices. Consequently, the severity of a breach can vary widely depending on the industry and the specific data handled. For example, a healthcare provider’s mobile device vulnerability is significantly different from a retail company’s, owing to the sensitivity of patient data.
Vulnerability in Financial Institutions
Financial institutions are especially vulnerable. Breaches can lead to unauthorized access to sensitive customer data, potentially resulting in fraudulent transactions and significant financial losses. The theft of financial data, such as account numbers and transaction details, has severe implications for both the institution and its customers. For instance, the 2017 Equifax breach, though not solely mobile-related, demonstrated the devastating financial and reputational consequences of large-scale data breaches.
Vulnerability in Healthcare Providers
Healthcare providers rely heavily on mobile devices for patient records, appointment scheduling, and other critical operations. Breaches in these systems can expose sensitive patient information, potentially leading to identity theft, fraud, and emotional distress for patients. The potential for misuse of sensitive health information underscores the critical need for robust security measures.
Table: Potential Impacts of the Hack on Different Industries
| Industry | Data Sensitivity | Operational Dependence | Potential Impacts |
|---|---|---|---|
| Financial Institutions | High | High | Unauthorized access, fraudulent transactions, reputational damage, significant financial losses. |
| Healthcare Providers | Extremely High | Medium-High | Exposure of patient information, identity theft, fraud, legal ramifications, loss of trust. |
| Retail | Medium | Medium | Data breaches, fraud, operational disruption, loss of customer trust, reduced sales. |
| Transportation | Medium | High | Operational disruption, security risks for sensitive information, supply chain vulnerabilities. |
| Manufacturing | Low-Medium | Medium | Production delays, supply chain disruptions, security breaches in operational control systems. |
Future Trends in Mobile Security
The recent iPhone hack, highlighting vulnerabilities in seemingly secure devices, underscores the ever-evolving nature of mobile security threats. Mobile devices, now integral to personal and professional lives, face an escalating array of threats, demanding proactive and adaptive security measures. The constant innovation in mobile technology brings both opportunities and new attack vectors, requiring a continuous evaluation and adaptation of security strategies.The landscape of mobile security is dynamic, with emerging technologies and user behaviors creating both new challenges and new avenues for protection.
Understanding these future trends is crucial for individuals and organizations to proactively safeguard their data and devices.
Potential Future Vulnerabilities
Mobile devices are becoming increasingly complex, incorporating advanced functionalities like AI and machine learning. This complexity introduces new potential entry points for malicious actors, such as vulnerabilities in AI algorithms used for facial recognition or voice assistants. Further, the rise of 5G and the Internet of Things (IoT) introduces new challenges in securing the vast interconnected network. The increasing reliance on mobile devices for financial transactions and sensitive data also amplifies the potential impact of successful attacks.
Furthermore, the growing sophistication of attackers, coupled with the rapid development cycle of mobile operating systems, creates a dynamic security environment where vulnerabilities are constantly emerging.
Emerging Trends in Mobile Security Research
Research into mobile security is actively focusing on developing robust defense mechanisms against sophisticated attacks. Researchers are investigating the use of advanced cryptography, intrusion detection systems, and behavioral analysis to detect malicious activities. Additionally, there is a growing focus on proactive security measures, including automated vulnerability scanning and real-time threat intelligence feeds. Furthermore, the study of human factors in security is becoming increasingly important, aiming to improve user awareness and security practices.
Effectiveness of Security Measures
The effectiveness of security measures varies depending on the specific threat and the implementation of the measure. Multi-factor authentication, for instance, provides a significant layer of security, but its effectiveness depends on the strength and reliability of the secondary factors used. Similarly, the effectiveness of encryption methods relies on their strength and the proper implementation. Mobile device management solutions and robust security protocols within applications also play a crucial role.
Regular security audits and penetration testing help to identify and address vulnerabilities before they are exploited.
Key Factors Influencing Mobile Security
Several factors significantly influence the security of mobile devices. These include the complexity of the device’s software and hardware, the level of user awareness and security practices, the quality of the security protocols and updates provided by the device manufacturer, and the sophistication of the attacks. The proliferation of malicious apps and the constant evolution of attack techniques are additional factors contributing to the challenges.
Furthermore, the increasing use of mobile devices in business environments and the rise of remote work have significantly increased the need for robust mobile security solutions.
The latest iPhone hack is a serious concern, regardless of your phone brand. Security vulnerabilities often spread, and a breach on one platform can impact others. For example, Samsung’s upcoming Galaxy Z Fold 2 5G shows TikTok integration, highlighting the interconnectedness of technology and the potential for a ripple effect. This emphasizes the importance of strong security practices across all devices, regardless of the specific model or brand.
Importance of Continuous Security Updates
Continuous security updates are critical for maintaining the security of mobile devices. Updates address vulnerabilities discovered after the release of the software and hardware, effectively mitigating the impact of new threats. These updates often include patches and enhancements that bolster the overall security posture. Failure to install these updates leaves devices vulnerable to exploitation, highlighting the necessity of a proactive approach to security maintenance.
Future Security Challenges and Mitigation Strategies
| Future Security Challenges | Mitigation Strategies |
|---|---|
| Sophisticated attacks exploiting vulnerabilities in AI-powered mobile features | Develop AI-based detection systems, implement robust access controls for AI functionalities, and enhance security protocols in AI-related applications. |
| Rise of targeted attacks on IoT devices connected to mobile networks | Employ security measures for IoT devices, secure connections to mobile devices, and enforce robust authentication protocols. |
| Increased reliance on mobile devices for financial transactions and sensitive data | Implement advanced encryption protocols, multi-factor authentication, and secure payment gateways. |
| Growing sophistication of attackers and their ability to bypass existing security measures | Continuously update security systems, enhance threat intelligence, and foster collaboration between security researchers and practitioners. |
Illustrative Examples
The recent iPhone hack highlights a critical vulnerability that extends far beyond Apple devices. Understanding how such a breach could be exploited is crucial for anyone who uses technology, regardless of the specific platform. This section provides illustrative examples of potential scenarios, emphasizing the widespread implications and preventative measures.
Scenario: Targeted Phishing Attack
A malicious actor could leverage the iPhone hack to launch a sophisticated phishing campaign. They might craft an email that appears legitimate, perhaps impersonating a trusted service or company. This email could contain a malicious link or attachment designed to exploit the vulnerability. If the victim clicks on the link, their iPhone could be compromised, potentially giving the attacker access to sensitive personal data, financial information, or even their entire device.
Exploitation of a Specific User
Imagine a user who frequently uses their iPhone for online banking. The attacker could exploit the vulnerability by subtly changing the banking website’s URL, tricking the user into entering their login credentials on a fake site. This “man-in-the-middle” attack would steal the user’s login information, potentially leading to financial loss.
Real-World Example: Similar Vulnerability in a Different System
The Equifax data breach of 2017 serves as a stark example of a similar vulnerability in a different system. A flaw in Equifax’s system allowed hackers to access sensitive personal information of millions of consumers. While the method of attack differed from the iPhone hack, the outcome—unauthorized access to sensitive data—was strikingly similar.
User Prevention Strategies
Users can mitigate the risk of such attacks by implementing strong security practices. This includes using strong, unique passwords for all accounts, enabling two-factor authentication whenever possible, and regularly updating software. Be wary of suspicious emails or links, and report any suspicious activity immediately.
Successful Prevention of a Potential Attack
A company implementing robust security protocols, including multi-factor authentication and regular security audits, could potentially prevent an attack exploiting the vulnerability. By proactively identifying and addressing potential weaknesses, the company could safeguard its sensitive data and systems.
Real-World Security Breaches
Numerous real-world security breaches underscore the importance of vigilance. The Colonial Pipeline attack in 2021, where ransomware crippled the pipeline, illustrates the devastating impact of vulnerabilities. The WannaCry ransomware attack, affecting thousands of organizations globally, demonstrates the widespread reach and potential damage of sophisticated attacks. These examples emphasize the critical need for robust security measures across all sectors and platforms.
Closure
In conclusion, the recent iPhone hack serves as a stark reminder of the ever-evolving threat landscape in mobile security. While the vulnerability initially targeted iPhones, the implications for all mobile users are clear. Taking proactive steps to enhance your security, including software updates, strong passwords, and awareness of phishing attempts, is crucial. Understanding the potential impact on industries and future security trends is equally important.
The need for robust security protocols and continuous vigilance is paramount in this increasingly digital world.