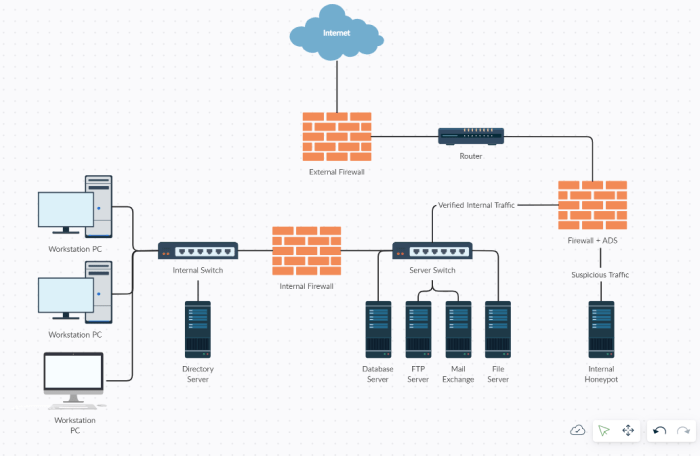
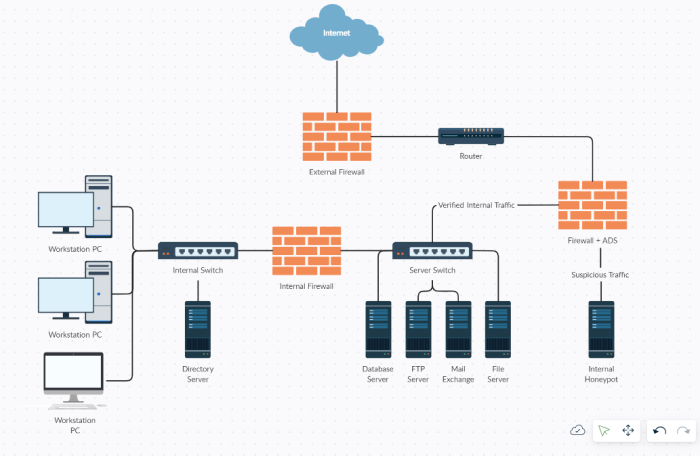
Tip sheet build secure applications and infrastructure provides a comprehensive guide to creating robust and secure software and infrastructure. From fundamental security concepts to advanced threat modeling, this guide covers the entire spectrum of building secure applications. It emphasizes practical application, offering actionable advice and real-world examples to help you proactively address security concerns.
This guide dives deep into secure coding practices, covering different programming languages and illustrating how to avoid common vulnerabilities. It also addresses the importance of secure infrastructure, discussing various types, security measures, and configuration management. The inclusion of case studies of security breaches further strengthens the practical understanding of the topic.
Introduction to Secure Application Development
Secure application development is the systematic process of designing, implementing, and testing software applications with inherent security considerations. It’s not just about adding security features after the fact, but rather building security into the very foundation of the application. This proactive approach minimizes vulnerabilities and safeguards against potential attacks. This proactive mindset is crucial in today’s digital landscape, where cyber threats are constantly evolving.The importance of security in modern software development cannot be overstated.
Building secure applications and infrastructure is crucial, and a good tip sheet can be a lifesaver. Thinking about the latest mobile processors, like the Qualcomm Snapdragon 750G official qualcomm snapdragon 750g official , shows how critical security is across the board. Ultimately, a strong understanding of secure design principles is key when building anything, from apps to entire systems.
In an increasingly interconnected world, applications handle sensitive data – financial information, personal details, and intellectual property. Vulnerabilities in these applications can lead to significant financial losses, reputational damage, and legal ramifications. Furthermore, breaches can have far-reaching consequences, impacting not only the application’s users but also the broader ecosystem. The need for robust security measures is paramount to ensure data protection and maintain user trust.
Key Principles and Best Practices for Secure Application Design
Secure application design is underpinned by several key principles. These principles encompass the entire software development lifecycle, from initial design to deployment and maintenance. A robust security posture involves meticulous planning and implementation throughout the process.
- Principle of Least Privilege: Granting users and applications only the necessary access rights to perform their tasks. This minimizes the impact of a potential compromise. For instance, a user should not have access to data they do not need to fulfill their job function.
- Input Validation: Scrutinizing all user inputs to prevent malicious code injection, SQL injection, or cross-site scripting (XSS) attacks. This crucial step involves carefully validating and sanitizing all data before it is used in the application’s logic. For example, carefully checking the format and type of input data to ensure it adheres to expected parameters.
- Secure Coding Practices: Adhering to established coding guidelines and avoiding common security vulnerabilities. Using secure coding libraries and frameworks can significantly reduce the risk of common exploits. For instance, utilizing parameterized queries instead of string concatenation when interacting with databases.
- Regular Security Assessments: Conducting regular security assessments throughout the development lifecycle. This can involve penetration testing, code reviews, and vulnerability scanning. These assessments are critical for identifying and mitigating security flaws before deployment.
Comparison of Security Frameworks and Standards
Various frameworks and standards provide guidance for building secure applications. These frameworks offer valuable insights and methodologies to enhance security practices.
| Framework/Standard | Key Focus | Notable Features |
|---|---|---|
| OWASP (Open Web Application Security Project) | Focuses primarily on web application security | Provides a comprehensive catalog of web application vulnerabilities, along with practical mitigation strategies and secure coding guidelines. |
| NIST (National Institute of Standards and Technology) | Provides a broader range of security guidelines for various types of systems and applications. | Offers a framework for managing risks and vulnerabilities across the entire software development lifecycle, from design to implementation and deployment. |
| ISO 27001 | Provides a framework for information security management systems. | Offers a comprehensive approach to security risk management, focusing on policies, procedures, and controls across the entire organization. |
Building Secure Infrastructure
Securing your infrastructure is crucial for protecting sensitive data and maintaining business continuity. A robust security posture extends beyond individual applications; it encompasses the underlying systems and networks that support them. This involves a multifaceted approach, addressing vulnerabilities in hardware, software, and configurations across various infrastructure types. From on-premises data centers to cloud environments, a consistent security strategy is vital to mitigate threats and ensure data integrity.Infrastructure security goes beyond just installing firewalls.
It’s about proactively identifying potential risks, implementing preventative measures, and responding effectively to incidents. A comprehensive approach encompasses everything from secure configuration management to robust access controls and regular security audits. This ensures the continued availability and confidentiality of your valuable assets.
Fundamental Security Concepts for Infrastructure, Tip sheet build secure applications and infrastructure
Infrastructure security relies on several fundamental concepts. These include the principles of least privilege, defense in depth, and the principle of separation of duties. Implementing these concepts across your infrastructure reduces the attack surface and improves the resilience of your systems. Least privilege ensures that users and processes have only the necessary permissions to perform their tasks, limiting the potential damage from a compromise.
Defense in depth means implementing multiple layers of security controls, so even if one layer is breached, others can prevent further harm. Separation of duties ensures that no single individual has complete control over a critical process, reducing the risk of fraud or malicious activity.
Types of Infrastructure and Their Security Considerations
Different infrastructure types present unique security challenges. Understanding these differences is essential to tailor security measures appropriately.
- On-Premises Infrastructure: On-premises infrastructure, typically located within a company’s physical data center, requires careful physical security measures to prevent unauthorized access. Network segmentation, intrusion detection systems, and robust access controls are essential. Regular security audits and vulnerability assessments are crucial to identify and address potential threats. Physical security measures, like access control systems and surveillance cameras, are critical.
Vulnerabilities in the underlying hardware and software must be regularly patched.
- Cloud Infrastructure: Cloud environments introduce new security considerations, including shared responsibility models. While cloud providers manage some security aspects, organizations still bear responsibility for securing their data and applications running within the cloud. Data encryption, access control policies, and regular security monitoring are essential. Careful consideration of security best practices for cloud environments, such as secure configuration of virtual machines, is crucial.
Implementing multi-factor authentication and regular security assessments are vital.
Secure Configuration Management
Proper configuration management is essential for maintaining security across infrastructure components. Automated tools and processes ensure consistency in configurations and prevent human error. This ensures that systems are running with the most up-to-date security settings. A documented configuration baseline, which acts as a blueprint for secure configurations, is vital for adherence and tracking.
Common Infrastructure Security Vulnerabilities
| Component | Common Vulnerability | Mitigation Strategies |
|---|---|---|
| Operating Systems | Outdated software, improper patching, default configurations | Regular patching, automated updates, configuration hardening |
| Databases | SQL injection vulnerabilities, insecure authentication, insufficient access controls | Parameterization of queries, secure password storage, least privilege access |
| Web Servers | Cross-site scripting (XSS), insecure direct object references (IDOR), insufficient input validation | Input validation, output encoding, secure coding practices |
| Network Devices | Misconfigured firewalls, default credentials, weak encryption | Regular configuration reviews, strong passwords, updated firmware |
Secure Coding Practices
Building secure applications and infrastructure requires a proactive approach to identifying and mitigating potential vulnerabilities. A crucial aspect of this process is understanding and implementing secure coding practices. These practices, when consistently applied throughout the development lifecycle, significantly reduce the risk of exploitation and enhance the overall security posture of the application. By focusing on defensive programming and anticipating potential threats, developers can create more resilient and trustworthy systems.
Secure Input Validation
Input validation is a cornerstone of secure coding. Applications often receive data from external sources, such as user input, network requests, or configuration files. Malicious actors may attempt to exploit these inputs to introduce vulnerabilities. Effective input validation prevents these attacks by carefully checking and sanitizing data before using it in the application.
- Data Type Validation: Ensuring that the input data conforms to the expected data type (e.g., integer, string, date) is crucial. Incorrect data types can lead to unexpected behavior or crashes, potentially exposing vulnerabilities. For instance, if a password field is designed to accept only alphanumeric characters, validating the input to ensure it matches this criteria is critical.
- Length Validation: Checking the length of the input data prevents buffer overflows and denial-of-service attacks. Limiting input length to a reasonable maximum prevents attacks that exploit vulnerabilities due to excessively long inputs.
- Format Validation: Validating input format helps prevent injection attacks. For instance, checking if an email address conforms to a valid email format prevents attacks that might use a malformed email to execute malicious code.
- Sanitization: Sanitizing user-supplied input prevents script injection attacks. This involves removing or encoding potentially harmful characters or code segments to prevent them from being interpreted as executable commands.
Secure Authentication and Authorization
Authentication and authorization are fundamental security mechanisms that control access to resources. Strong authentication verifies the identity of users, while authorization determines what resources they can access.
- Multi-Factor Authentication (MFA): Employing MFA significantly enhances security by requiring multiple verification methods. This adds an extra layer of security, making it harder for attackers to gain unauthorized access even if they have compromised one authentication factor.
- Strong Password Policies: Implementing strong password policies is crucial for protecting user accounts. These policies should enforce complex password requirements, preventing simple or easily guessable passwords.
- Secure Session Management: Implementing secure session management is vital to prevent session hijacking attacks. Sessions should be timely invalidated and stored securely to prevent unauthorized access to user accounts.
- Role-Based Access Control (RBAC): RBAC defines specific roles and permissions, enabling administrators to control user access based on their roles and responsibilities. This granular control helps restrict access to only necessary resources.
Secure Coding Practices for Different Languages
Different programming languages have specific security considerations. The following table summarizes key secure coding guidelines for Java and Python.
| Language | Secure Coding Guideline | Example |
|---|---|---|
| Java | Use parameterized queries to prevent SQL injection | PreparedStatement stmt = conn.prepareStatement("SELECT
|
| Java | Validate user input before using it in the application | if (!input.matches("[a-zA-Z0-9]+")) throw new IllegalArgumentException("Invalid input."); |
| Python | Use parameterized queries to prevent SQL injection | cursor.execute("SELECT
|
| Python | Sanitize user input before displaying it on a webpage | safe_string = html.escape(user_input) |
Threat Modeling and Vulnerability Assessment
Building secure applications and infrastructure requires proactive identification and mitigation of potential threats. Threat modeling and vulnerability assessments are crucial steps in this process, helping developers and security teams understand potential attack vectors and vulnerabilities within their systems. A well-executed threat modeling exercise informs subsequent vulnerability assessments, leading to more targeted and effective security measures.
Threat Modeling Process
Threat modeling is a structured approach to identifying potential security threats to a system. It involves analyzing the system’s architecture, functionalities, and data flows to determine how attackers might exploit weaknesses. This process typically involves brainstorming potential attack scenarios, assessing the likelihood and impact of each threat, and prioritizing mitigation strategies.
Threat Modeling Techniques
Several techniques facilitate the threat modeling process. Understanding these techniques helps in a more comprehensive threat analysis.
- STRIDE: This technique categorizes potential threats into six categories: Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege. Each category represents a different type of attack vector. For example, a spoofing attack involves an attacker impersonating a legitimate user or system.
- DREAD: This framework categorizes threats based on their potential impact and likelihood. DREAD stands for Damage potential, Reproducibility, Exploitability, Affected users, and Discoverability. Each factor is assessed on a scale to determine the overall risk level of the threat. High scores in any category signify a significant threat.
Vulnerability Assessment
A vulnerability assessment systematically identifies security weaknesses within a system or application. This involves using automated tools and manual techniques to scan for known vulnerabilities. The goal is to pinpoint potential points of entry for attackers and understand their potential impact. The output of a vulnerability assessment is a report that lists identified vulnerabilities, their severity, and recommendations for remediation.
Penetration Testing
Penetration testing simulates real-world attacks to assess the effectiveness of security controls. Ethical hackers attempt to exploit vulnerabilities in a controlled environment to identify weaknesses that automated scans might miss. Penetration testing results provide a more realistic evaluation of a system’s security posture, as opposed to just identifying known vulnerabilities. It allows for testing the response and resilience of security measures in place.
Vulnerability Assessment Tools Comparison
Comparing different vulnerability assessment tools helps in selecting the right tool for a specific need. Functionality and efficiency vary significantly among tools.
| Tool | Functionality | Strengths | Weaknesses |
|---|---|---|---|
| Nessus | Comprehensive vulnerability scanning, network and host scanning, and reporting | Wide range of scans, extensive database of known vulnerabilities | Can be resource-intensive, requires specialized expertise for advanced usage |
| OpenVAS | Open-source vulnerability scanner that can scan networks and systems for vulnerabilities | Cost-effective, highly customizable | Requires more technical expertise to configure and maintain |
| QualysGuard | Cloud-based vulnerability management platform that offers continuous scanning and reporting | Automated scanning, real-time reporting, scalability | Subscription-based model, may not be suitable for all budgets |
Secure Deployment and Maintenance
Securing applications and infrastructure extends beyond development. A robust security posture demands careful consideration during deployment and ongoing maintenance. This crucial phase often exposes vulnerabilities if not handled proactively. Effective strategies for deployment, patching, monitoring, and incident response are vital for mitigating risks and safeguarding sensitive data.
Secure Deployment Strategies
Deployment strategies must prioritize security. This involves employing secure configurations, utilizing automated deployment pipelines, and rigorously testing deployments in controlled environments. Proper configuration management is essential to ensure that deployed systems adhere to security policies. For example, using configuration management tools like Ansible or Puppet can automate the deployment of secure configurations across multiple servers. Employing containerization technologies (e.g., Docker) and orchestration platforms (e.g., Kubernetes) can enhance the security and consistency of deployments.
Secure Software Patching and Updates
Regular patching and updating are critical to maintaining system security. A proactive approach involves implementing automated patching mechanisms to address vulnerabilities promptly. A well-defined patching schedule, coupled with thorough testing of updates in staging environments, is crucial to minimize disruptions and mitigate risks. Organizations should prioritize security advisories and follow best practices Artikeld by security experts and vendors.
Importance of Monitoring and Logging
Monitoring and logging play a significant role in detecting and responding to security incidents. Comprehensive monitoring tools can track system performance, resource utilization, and user activity, enabling early detection of anomalies. Robust logging mechanisms record events and activities, providing crucial information for forensic analysis in case of incidents. These mechanisms are vital for security operations and incident response.
Real-time monitoring allows for quick identification and resolution of emerging threats.
Methods for Incident Response and Recovery
A well-defined incident response plan is paramount. This plan should Artikel procedures for detecting, containing, responding to, and recovering from security incidents. It should include clear roles and responsibilities for incident responders, communication protocols, and strategies for data recovery. Regularly testing and updating the incident response plan ensures its effectiveness and readiness. Effective communication during an incident is essential for minimizing damage and maintaining trust.
Best Practices for Secure Deployment and Maintenance
| Aspect | Best Practice | Explanation |
|---|---|---|
| Deployment | Secure Configuration Management | Ensure deployed systems comply with security policies and configurations through automated tools. |
| Patching | Automated Patching | Automate patching processes to address vulnerabilities promptly and efficiently. |
| Monitoring | Comprehensive Monitoring | Utilize monitoring tools to track system performance, resource utilization, and user activity for anomaly detection. |
| Incident Response | Well-Defined Plan | Develop a comprehensive incident response plan with clear roles, responsibilities, communication protocols, and recovery strategies. |
| Logging | Robust Logging | Implement robust logging mechanisms to record events and activities for forensic analysis. |
Secure Data Handling and Storage
Data security is paramount in today’s digital landscape. Protecting sensitive information from unauthorized access, use, disclosure, disruption, modification, or destruction is crucial for maintaining trust, compliance, and operational stability. Robust data handling and storage practices are essential to mitigate risks and ensure the confidentiality, integrity, and availability of data throughout its lifecycle.
Building secure applications and infrastructure is crucial, especially with the increasing reliance on technology. Considering recent news like Amazon CEO Andy Jassy’s announcement regarding remote employees returning to the office ( amazon ceo andy jassy remote employees return to office ), it highlights the importance of robust security measures across all platforms. This tip sheet will help navigate the complexities of creating a secure environment for any business.
Importance of Data Security
Data breaches can have severe consequences, ranging from financial losses and reputational damage to legal liabilities and loss of customer trust. The value of data is undeniable, and protecting it is a critical business function. Security measures must be implemented at every stage of the data lifecycle, from collection and processing to storage and disposal. Protecting sensitive data is not just a technical concern; it’s a critical aspect of organizational risk management.
Building secure applications and infrastructure is crucial, and a good tip sheet can really help. Thinking about the latest tech, like the OnePlus Watch vs. the Samsung Galaxy Watch Active 2, oneplus watch vs samsung galaxy watch active 2 is a fascinating comparison, but the core principles of security remain the same regardless of the device. Understanding these fundamentals is key for any developer, and that tip sheet will be a great asset for that.
Data Encryption Techniques
Encryption is a fundamental technique for securing data in transit and at rest. It transforms readable data into an unreadable format, making it unintelligible to unauthorized individuals. Various encryption algorithms exist, each with its strengths and weaknesses. Symmetric-key encryption, such as AES (Advanced Encryption Standard), uses the same key for encryption and decryption. Asymmetric-key encryption, like RSA (Rivest–Shamir–Adleman), uses separate keys for encryption and decryption, enhancing security by enabling secure communication without prior key exchange.
Hashing algorithms, such as SHA-256, generate unique fingerprints of data, crucial for verifying data integrity. The choice of encryption method depends on the sensitivity of the data and the specific security requirements.
Secure Data Storage Practices
Secure data storage necessitates a multi-layered approach. Data should be stored on secure servers with access controls to restrict access to authorized personnel only. Regular backups and disaster recovery plans are vital to safeguard against data loss due to hardware failures or natural disasters. Data should be stored in encrypted format, both in transit and at rest.
Implementing robust access control measures is critical to limit who can access sensitive data. Furthermore, regular security audits and penetration testing should be conducted to identify vulnerabilities and address them proactively.
Access Control Mechanisms for Sensitive Data
Access control mechanisms are essential to limit access to sensitive data based on the principle of least privilege. This principle dictates that users should only have the necessary permissions to perform their tasks. Implementing a role-based access control (RBAC) system allows administrators to assign roles with specific permissions to users. Furthermore, multi-factor authentication (MFA) adds an extra layer of security, requiring users to provide multiple forms of identification to gain access.
Regular audits and reviews of access permissions are critical to maintain the effectiveness of access control measures.
Data Security Policies and Implementation
| Policy | Implementation |
|---|---|
| Data Encryption at Rest | Encrypting data stored on databases, file servers, and other storage devices. |
| Data Encryption in Transit | Using secure protocols like HTTPS for communication channels. |
| Access Control Lists (ACLs) | Defining specific permissions for users and roles to access data. |
| Regular Security Audits | Conducting periodic assessments to identify vulnerabilities and enforce compliance. |
| Data Loss Prevention (DLP) | Implementing measures to prevent sensitive data from leaving the organization’s control. |
Secure Software Development Lifecycle (SDLC)
Integrating security into the software development lifecycle (SDLC) is crucial for building robust and reliable applications. A proactive approach to security throughout all phases of development significantly reduces vulnerabilities and improves the overall security posture of the final product. This involves more than just patching vulnerabilities after they are discovered; it’s about embedding security considerations into the very fabric of the development process.Security is not an afterthought; it’s an integral part of the software development process.
By implementing security controls at each stage of the SDLC, organizations can create more secure applications that are resistant to attacks and provide a better user experience.
Security Requirements Gathering
Understanding the security needs and constraints of an application is paramount from the outset. Thorough requirements gathering involves identifying potential threats and vulnerabilities that the application might face. This phase includes defining security goals, identifying sensitive data, and establishing security controls. For instance, if the application handles financial transactions, explicit requirements should be documented to protect against fraud and data breaches.
Clear security requirements are vital for guiding development decisions throughout the lifecycle.
Security Design
This phase focuses on designing the application architecture with security in mind. Security considerations should be embedded in the application’s design, from the choice of programming languages to the selection of security libraries and frameworks. For example, choosing secure coding practices and libraries from the start helps reduce the likelihood of common vulnerabilities. Design choices should anticipate potential threats and incorporate mechanisms to mitigate them.
Secure Coding Practices
Implementing secure coding practices throughout the development process is vital. Developers should be aware of common vulnerabilities and be trained to avoid them. This includes following secure coding guidelines, using secure libraries, and avoiding common pitfalls. The use of secure coding standards, such as OWASP guidelines, helps reduce the risk of vulnerabilities.
Security Testing
Thorough testing is essential to identify vulnerabilities. Various testing methods, including penetration testing, vulnerability scanning, and code reviews, should be employed to ensure the application meets security requirements. Regular penetration testing simulates real-world attacks to assess the application’s resilience. Examples of testing include checking for SQL injection, cross-site scripting, and other common vulnerabilities.
Secure Deployment and Maintenance
Secure deployment strategies are critical to ensure the application is deployed securely. This includes secure configuration management, access control, and regular security updates. For example, enforcing strict access controls during deployment minimizes unauthorized access to sensitive resources. Ongoing maintenance and updates should include addressing security patches and vulnerabilities promptly.
Secure Data Handling and Storage
Data security is paramount. Protecting sensitive data throughout its lifecycle is essential. This involves encryption, access controls, and secure storage mechanisms. Using encryption for data at rest and in transit is crucial, along with strong access control policies. For instance, encrypting sensitive data stored in databases protects it from unauthorized access.
Visual Representation of a Secure SDLC
(A simple flowchart depicting the sequential phases of the SDLC with security considerations integrated at each stage. The flow would show Requirements gathering, Design, Development, Testing, Deployment, Maintenance, and Feedback loops.)
Security Awareness Training for Developers
Providing security awareness training to developers is a critical component of the secure SDLC. This training should cover common vulnerabilities, secure coding practices, and threat modeling techniques. Training sessions should emphasize the importance of security and how their actions directly impact the application’s security. Examples of training topics include SQL injection prevention, cross-site scripting mitigation, and authentication best practices.
Security Tools and Technologies
Building secure applications and infrastructure relies heavily on the right tools and technologies. Choosing and implementing these tools effectively is crucial for mitigating risks and maintaining a robust security posture. This section delves into various security tools, their functionalities, and integration into the development lifecycle, emphasizing the importance of selecting appropriate tools for specific needs.
Overview of Common Security Tools
A wide array of security tools are available, each designed to address specific security concerns. These tools range from static analysis tools to dynamic application security testing (DAST) tools and penetration testing frameworks. Effective security management requires a comprehensive suite of tools, rather than relying on a single solution. This multifaceted approach helps identify and remediate vulnerabilities across the entire application lifecycle.
Choosing Appropriate Security Tools
Selecting the right security tools involves careful consideration of several factors. The size and complexity of the application, the development methodology, and the specific security risks need to be assessed. For example, a small web application might benefit from a basic vulnerability scanner, while a large enterprise application might require a more sophisticated suite of tools encompassing various stages of the development lifecycle.
Consider the cost-benefit analysis, the availability of skilled personnel to manage the tool, and the potential impact on development workflow. Furthermore, ensure that the tools are compatible with existing infrastructure and development processes.
Functionality and Benefits of Different Security Tools
Various security tools offer unique functionalities. Static Application Security Testing (SAST) tools analyze code without running it, identifying potential vulnerabilities in the codebase. Dynamic Application Security Testing (DAST) tools simulate real-world attacks to detect vulnerabilities in running applications. Vulnerability scanners automate the identification of known security vulnerabilities across applications and infrastructure. Penetration testing tools simulate real-world attacks to evaluate the effectiveness of security measures and discover vulnerabilities that automated tools may miss.
Intrusion Detection/Prevention Systems (IDS/IPS) monitor network traffic for malicious activity and either alert or block suspicious behavior. Security Information and Event Management (SIEM) systems collect and analyze security logs to identify patterns and threats.
Integration into the Development Pipeline
Effective integration of security tools into the development pipeline is vital for building secure applications. SAST tools can be integrated into the CI/CD pipeline to automatically scan code changes and flag vulnerabilities early in the development process. DAST tools can be integrated to perform tests during testing phases, identifying vulnerabilities that emerge from the interactions between different parts of the application.
Vulnerability scanners can be scheduled to automatically check for vulnerabilities across the infrastructure. This integration streamlines the security process and helps prevent vulnerabilities from entering production systems.
Table of Popular Security Tools
| Tool | Features | Use Cases |
|---|---|---|
| OWASP ZAP | Open-source DAST tool for web applications; performs various automated and manual tests; integrates with other tools | Finding vulnerabilities in web applications, identifying cross-site scripting (XSS) flaws, testing security configurations |
| SonarQube | Open-source platform for code quality analysis, incorporating SAST and code smells detection | Improving code quality, identifying potential security vulnerabilities, enhancing code maintainability |
| Nessus | Powerful vulnerability scanner for applications and infrastructure; provides detailed reports and vulnerability remediation guidance | Scanning for vulnerabilities in operating systems, networks, and applications; Identifying misconfigurations and outdated software |
| Wireshark | Network protocol analyzer that captures and analyzes network traffic; allows for detailed examination of communications | Troubleshooting network issues, analyzing network security threats, debugging network applications |
Case Studies of Security Breaches
Learning from past mistakes is crucial in the ever-evolving landscape of cybersecurity. Analyzing real-world security breaches provides invaluable insights into vulnerabilities, attack vectors, and the overall impact of these incidents. By examining these cases, we can identify patterns and develop robust strategies to prevent similar occurrences in our own applications and infrastructure.Understanding the causes and consequences of past security breaches allows us to proactively address potential threats and implement preventive measures.
This approach, rooted in the lessons learned from historical incidents, empowers organizations to build more secure systems and maintain a strong security posture.
Examples of High-Profile Security Breaches
High-profile breaches, often involving large organizations, demonstrate the significant consequences of inadequate security measures. These incidents highlight the critical need for continuous security improvement and vigilance. The Target data breach in 2013, for instance, exposed millions of customer records due to a vulnerability in a third-party vendor’s system. This breach underscores the importance of securing not only internal systems but also the supply chain.
Causes of Security Breaches
Security breaches are often the result of a combination of factors, including inadequate security controls, flawed software development practices, and human error. In the Equifax breach of 2017, a vulnerability in a publicly accessible Apache Struts library allowed attackers to gain unauthorized access to sensitive data. This underscores the importance of rigorous security testing and continuous monitoring. Poorly configured systems, insufficient access controls, and the exploitation of known vulnerabilities often play a significant role.
Consequences of Security Breaches
The consequences of security breaches can be far-reaching, impacting not only the organization but also its customers and stakeholders. Financial losses, reputational damage, legal liabilities, and regulatory penalties are just some of the consequences. The Sony Pictures Entertainment hack in 2014, for instance, resulted in significant financial and reputational damage. Furthermore, the breaches often lead to a loss of trust among customers and partners.
Lessons Learned from Security Breaches
Analyzing security breaches reveals critical lessons that can inform security best practices. The Capital One data breach in 2019 highlighted the importance of securing sensitive data throughout its lifecycle. This incident emphasizes the need for robust data encryption, secure storage, and access controls. From these breaches, we can gather essential knowledge to improve our defenses.
Security Best Practices Derived from Case Studies
Based on the analysis of numerous breaches, several security best practices emerge as crucial elements in building secure applications and infrastructure. These include:
- Regular Security Assessments: Regular penetration testing, vulnerability assessments, and security audits are essential to identify and address potential weaknesses before attackers exploit them.
- Secure Coding Practices: Developers should be trained on secure coding principles to prevent vulnerabilities at the source. This includes using validated inputs and following industry best practices.
- Strong Access Controls: Implementing strong access controls, including multi-factor authentication and least privilege principles, is critical to limit the potential damage from unauthorized access.
- Incident Response Plan: Having a well-defined incident response plan is crucial to effectively address and mitigate security incidents.
Key Takeaways for Preventing Similar Breaches
By understanding the root causes of security breaches, organizations can develop and implement proactive strategies to prevent similar incidents. Key takeaways include:
- Proactive Security Measures: Implement a proactive security posture that includes continuous monitoring, vulnerability scanning, and regular security assessments.
- Employee Training: Invest in security awareness training for all employees to raise their awareness of potential threats and best practices.
- Third-Party Vendor Management: Establish rigorous security requirements for third-party vendors and ensure they adhere to these requirements.
- Regular Updates and Patches: Keep all software and systems updated with the latest security patches to address known vulnerabilities.
Future Trends in Secure Application Development and Infrastructure
The digital landscape is constantly evolving, demanding a proactive approach to security. Emerging technologies, coupled with sophisticated threat actors, necessitate a forward-thinking strategy for securing applications and infrastructure. This section explores key future trends, focusing on the impact of AI, machine learning, and evolving attack surfaces.
Emerging Trends in Application Security
The security landscape is shifting from reactive measures to proactive strategies. Organizations are increasingly recognizing the importance of integrating security into the entire software development lifecycle (SDLC). This shift emphasizes preventing vulnerabilities rather than simply patching them after they are discovered. Proactive measures like threat modeling and penetration testing at various stages of development are becoming standard practice.
Impact of AI and Machine Learning on Security
AI and machine learning are transforming both the nature of attacks and the tools used for defense. Sophisticated AI-powered attacks are becoming more frequent and difficult to detect. Meanwhile, machine learning algorithms are being employed to identify anomalies, predict potential threats, and automate security tasks. This creates a dynamic arms race, with defenders relying on AI and machine learning to stay ahead of attackers.
For example, machine learning models can analyze vast amounts of network traffic to detect malicious patterns, significantly improving threat detection capabilities.
Future Technologies and Practices
Several emerging technologies are reshaping the security landscape. These include serverless computing, cloud-native architectures, and containerization. Serverless computing, for example, shifts the operational burden from the user to the cloud provider. This demands a reassessment of security protocols and a focus on secure configuration and access management to prevent unauthorized access and data breaches.
Challenges and Opportunities in the Field
The future of secure application development and infrastructure presents both significant challenges and exciting opportunities. The increasing complexity of systems, the rapid pace of technological advancements, and the growing sophistication of cyber threats pose significant obstacles. However, the opportunities for innovation and proactive security measures are equally substantial. The rise of AI and machine learning in security provides an opportunity to automate security tasks, improve threat detection, and enhance overall security posture.
Addressing these challenges requires a continuous commitment to learning and adaptation.
Anticipating Future Trends
Staying ahead of future trends in security requires a proactive and informed approach. Organizations need to continuously monitor and analyze the emerging threat landscape, invest in research and development, and foster a culture of security awareness and continuous learning. This means engaging in ongoing security training for developers, understanding the potential implications of new technologies, and actively participating in the broader security community.
Closing Notes: Tip Sheet Build Secure Applications And Infrastructure
In conclusion, building secure applications and infrastructure is an ongoing process, requiring vigilance and adaptation to emerging threats. This tip sheet serves as a valuable resource, equipping you with the knowledge and best practices to build resilient systems. The key takeaway is that proactive security measures are paramount to mitigate risks and safeguard your digital assets. By implementing the strategies Artikeld in this guide, you can create systems that are not only functional but also secure against evolving threats.