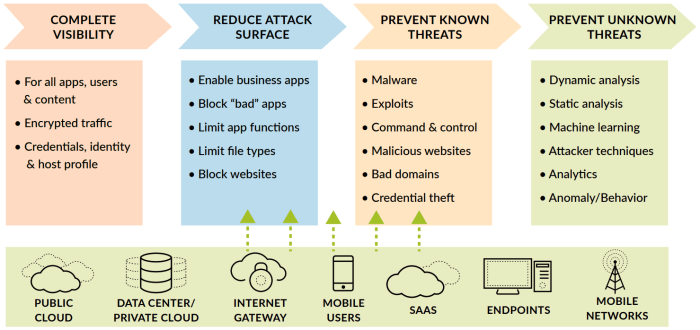
Transforming to a prevention based architecture – Transforming to a prevention-based architecture sets the stage for a fascinating exploration into proactive systems design. This framework shifts from reacting to problems to anticipating and preventing them altogether. We’ll delve into the core principles, components, and strategies for building a robust prevention-based approach across various domains, from cybersecurity to public health. Understanding the crucial differences between reactive and proactive approaches is key to effectively implementing this transformative shift.
This exploration covers everything from defining prevention-based architecture and identifying its key components to implementing effective strategies, measuring their impact, and addressing potential challenges. Real-world case studies and a look at future trends round out this comprehensive guide.
Defining Prevention-Based Architecture: Transforming To A Prevention Based Architecture
A prevention-based architecture shifts the focus from reacting to incidents to proactively mitigating potential threats. This approach prioritizes building systems and processes that inherently reduce the likelihood of vulnerabilities being exploited. It’s a paradigm shift that moves security from a reactive posture to a proactive one, aiming to prevent attacks before they even occur.This proactive strategy necessitates a deep understanding of potential threats and vulnerabilities.
It goes beyond simple patching and involves a comprehensive analysis of the entire system lifecycle, from design and development to deployment and maintenance. Ultimately, the goal is to build resilient systems that are less susceptible to compromise.
Core Principles of a Prevention-Based Architecture
Prevention-based architectures are built on several key principles. These principles emphasize a holistic approach to security, addressing vulnerabilities at multiple layers of the system.
- Proactive Threat Modeling: Instead of waiting for attacks to happen, proactive threat modeling anticipates potential threats and vulnerabilities. This involves identifying potential attack vectors, evaluating their likelihood and impact, and designing countermeasures accordingly. For instance, a well-designed threat model might identify a specific software library with a known vulnerability and develop a plan to avoid its use, or to implement a security solution that mitigates the threat.
- Security by Design: Security is integrated into every stage of the system’s lifecycle. This principle ensures that security considerations are not an afterthought, but a fundamental aspect of the system’s design, development, and deployment. This approach is not just about implementing security controls after the system is built, but designing the system itself to be secure.
- Continuous Monitoring and Improvement: Prevention-based architectures demand ongoing monitoring and improvement. Systems must be continuously assessed for new threats and vulnerabilities. Security practices and tools must be regularly updated and refined to adapt to evolving threats. A company that continuously monitors its systems and improves security practices can stay ahead of attackers.
Reactive vs. Prevention-Based Approach
The fundamental difference between reactive and prevention-based architectures lies in their approach to security. Reactive architectures respond to incidents after they occur, while prevention-based architectures aim to prevent incidents from happening in the first place.
| Aspect | Reactive Architecture | Prevention-Based Architecture |
|---|---|---|
| Cost | Higher long-term costs due to damage control, incident response, and recovery efforts. The cost of fixing the damage is higher than the cost of preventing the damage in the first place. | Lower long-term costs due to fewer incidents, reduced recovery time, and improved operational efficiency. Preventing vulnerabilities in the design phase is cheaper than dealing with the consequences of a breach later. |
| Speed | Slow response times, as incident response processes are triggered only after an attack occurs. This often leads to increased downtime and damage. | Faster response to emerging threats, as proactive measures are already in place. The systems are already configured to deal with potential issues. |
| Resource Allocation | Resource allocation is primarily focused on incident response teams and recovery efforts. | Resource allocation is focused on proactive security measures, threat modeling, and continuous improvement. |
| Recovery | Recovery often involves significant downtime and data loss. | Recovery is faster and less disruptive, minimizing data loss and downtime. |
| Security Posture | Security is often reactive, focusing on patching vulnerabilities after they’re discovered. | Security is proactive, aiming to build security into the system from the outset. |
Benefits of Prevention-Based Architecture
A prevention-based approach offers substantial benefits. These benefits encompass financial savings, enhanced operational efficiency, and improved overall security posture.
- Reduced Downtime: Prevention minimizes the likelihood of incidents that disrupt operations, resulting in less downtime and improved productivity. A prevention-based approach can significantly reduce the time spent recovering from security incidents.
- Lower Costs: Proactive measures reduce the need for expensive incident response and recovery, resulting in lower overall costs. Implementing security measures early in the process can save significant resources in the long run.
- Enhanced Security Posture: Prevention-based architectures foster a more robust security posture, decreasing the attack surface and minimizing the likelihood of successful breaches.
Identifying Key Components

A prevention-based architecture isn’t just about reacting to incidents; it’s about proactively identifying and mitigating potential threats. This approach requires a robust framework that integrates various components, technologies, and processes to anticipate and prevent problems before they escalate. This detailed look at the key components will provide a practical understanding of how to build such a system.Essential components for a prevention-based architecture are interconnected and require careful consideration.
They span various layers, from data collection and analysis to proactive response mechanisms. Understanding the interplay between these components is crucial for effective implementation and achieving the desired outcome of a secure and resilient system.
Essential Components of a Prevention-Based Architecture
The foundation of any prevention-based architecture rests on comprehensive data collection, analysis, and the subsequent implementation of preventative measures. A thorough understanding of potential risks, vulnerabilities, and their interdependencies is essential. Effective risk assessment and threat modeling are key processes to identify these potential issues.
Data Collection and Analysis Techniques
A proactive approach to prevention relies heavily on data analysis. This involves collecting various types of data, ranging from system logs and user activity to external threat intelligence feeds. This data is then processed and analyzed to identify patterns, anomalies, and potential indicators of compromise (IOCs). Machine learning algorithms and predictive modeling play a vital role in this process, enabling automated threat detection and proactive responses.
For instance, identifying unusual login patterns from a specific IP address could signal a potential intrusion attempt.
- System Logs: System logs provide valuable information about system activity, including errors, warnings, and security events. Analyzing these logs can reveal suspicious patterns or anomalies that could indicate a potential security breach. A comprehensive log management system is essential for efficient collection and analysis.
- User Activity Data: User activity data, including login attempts, file access, and application usage, can be crucial in identifying suspicious behavior. For example, a user accessing files they shouldn’t have permission to access or a surge in unusual login attempts from a single IP address could indicate malicious activity.
- External Threat Intelligence: External threat intelligence feeds provide real-time information about emerging threats, vulnerabilities, and attack patterns. This data can help organizations proactively adapt their defenses and implement preventive measures against known threats.
Predictive Modeling and Data Analysis
Predictive modeling techniques can forecast potential threats and vulnerabilities based on historical data and trends. By analyzing patterns in past security events, these models can identify potential future threats and provide early warnings. For example, if a specific type of malware has been successfully used to breach systems in the past, predictive models can flag similar patterns and prevent potential infections.
- Machine Learning Algorithms: Machine learning algorithms can identify subtle patterns and anomalies in data that might be missed by traditional methods. These algorithms can learn from historical data to identify potential threats and vulnerabilities in real-time.
- Statistical Analysis: Statistical analysis can be used to identify trends and correlations in data that might indicate potential risks. This can help to identify unusual patterns or anomalies that could indicate a potential security breach.
Data Types for Prevention
The types of data collected for prevention extend beyond just security logs. Comprehensive data collection also includes user behavior, network traffic patterns, and system performance metrics.
- Network Traffic Data: Network traffic data can reveal unusual patterns or anomalies in network activity, which could indicate malicious activity. Analyzing network traffic data can help identify suspicious connections or data flows.
- System Performance Metrics: System performance metrics can identify unusual spikes or drops in performance, which could indicate a denial-of-service attack or other malicious activity.
Relationship Between Components
A prevention-based architecture requires a well-defined relationship between its various components. Effective communication and integration between different systems and processes are crucial for a comprehensive approach.
| Component | Data Type | Relationship to Other Components |
|---|---|---|
| Data Collection Systems | System logs, user activity, network traffic | Feeds data to analysis tools and triggers alerts |
| Data Analysis Tools | Processed data from various sources | Identifies anomalies, patterns, and potential threats |
| Predictive Modeling Tools | Historical data, analysis results | Predicts potential threats and vulnerabilities |
| Security Information and Event Management (SIEM) Systems | Aggregated security data | Centralizes security events and alerts |
Implementing Prevention Strategies
Building a prevention-based architecture hinges on robust strategies that anticipate and mitigate potential threats. This approach moves beyond reactive measures to proactively identify vulnerabilities and establish safeguards before incidents occur. This shift necessitates a comprehensive understanding of various prevention tactics and their application across different domains.Effective prevention strategies require a proactive mindset, shifting the focus from damage control to preventative measures.
This approach emphasizes early detection and intervention, minimizing the impact of potential threats and maximizing the effectiveness of security protocols.
Prevention Strategies and Tactics
Proactive prevention strategies encompass a wide range of methods, from technological solutions to cultural shifts. These strategies are crucial for establishing a resilient and secure environment, minimizing potential risks and ensuring the long-term sustainability of systems and processes. This section Artikels key strategies and tactics for various domains.
Shifting to a prevention-based architecture is crucial for long-term security, but the constant barrage of online ads can be a real pain point. Think about how much time is wasted sifting through irrelevant ads, especially when you’re trying to focus on something specific like, say, ctrl walt delete podcast online ads. Ultimately, a robust prevention strategy tackles these issues head-on, minimizing the need for reactive measures and ensuring a smoother user experience.
This proactive approach is key to a truly secure and efficient system.
- Threat Modeling: Threat modeling involves systematically identifying potential threats and vulnerabilities in a system or process. This involves considering potential malicious actors, their motivations, and the methods they might employ. Thorough threat modeling helps prioritize vulnerabilities and allocate resources effectively for mitigation. A well-defined threat model provides a roadmap for identifying vulnerabilities and implementing preventative measures.
- Vulnerability Assessment: Vulnerability assessments involve identifying weaknesses in systems, processes, and infrastructure. These assessments use automated tools and manual reviews to pinpoint vulnerabilities that could be exploited. Regular vulnerability assessments are crucial for staying ahead of emerging threats. For example, penetration testing and vulnerability scanning are critical components of a robust assessment strategy.
- Security Awareness Training: Human error often plays a significant role in security breaches. Security awareness training programs educate users about potential threats, safe practices, and how to identify and report suspicious activity. This approach aims to foster a security-conscious culture where employees actively participate in safeguarding systems.
Methods for Identifying Potential Threats and Vulnerabilities
Identifying potential threats and vulnerabilities is critical for effective prevention. This involves a combination of technical and analytical approaches. Proactive threat intelligence gathering is essential for staying informed about emerging threats.
- Threat Intelligence Gathering: Threat intelligence gathering involves collecting and analyzing information about current and emerging threats. This includes monitoring online forums, news reports, and academic publications for clues about new threats and attack vectors. For example, by tracking known vulnerabilities in software, organizations can implement updates and patches proactively.
- Penetration Testing: Penetration testing simulates real-world attacks to identify vulnerabilities in systems and applications. Ethical hackers attempt to exploit potential weaknesses, providing valuable insights into system vulnerabilities. This proactive approach helps organizations understand their defenses and strengthen them against future attacks.
- Security Audits: Security audits are systematic reviews of security policies, procedures, and controls. They ensure that existing security measures are effective and up-to-date. Regular audits can reveal gaps and inconsistencies in security protocols, enabling timely corrective actions.
Preventive Measures in Different Domains
Implementing prevention strategies requires tailored approaches for different domains. This section provides examples of preventive measures in cybersecurity, public health, and infrastructure.
- Cybersecurity: Implementing strong passwords, multi-factor authentication, and regular software updates are essential preventive measures. Firewalls, intrusion detection systems, and data encryption protect sensitive data from unauthorized access. Regular security assessments and penetration testing identify and mitigate vulnerabilities.
- Public Health: Vaccination programs, public health campaigns, and surveillance systems are essential for preventing disease outbreaks. Early detection of potential outbreaks and rapid response protocols are critical components of a strong public health prevention strategy.
- Infrastructure: Regular maintenance, infrastructure inspections, and early warning systems for natural disasters are crucial preventive measures. Investing in resilient infrastructure and implementing contingency plans are essential to ensure continued operation during emergencies.
Comparison of Prevention Strategies
The effectiveness of prevention strategies varies depending on the specific context and threat landscape. This table summarizes different prevention strategies and their effectiveness.
| Prevention Strategy | Effectiveness | Examples |
|---|---|---|
| Threat Modeling | High | Identifying potential attack vectors, defining potential impact |
| Vulnerability Assessment | Medium-High | Penetration testing, vulnerability scanning |
| Security Awareness Training | Medium | Employee training, phishing simulations |
Proactive Monitoring and Early Warning Systems
Proactive monitoring and early warning systems are essential components of a prevention-based architecture. These systems allow for real-time threat detection and enable rapid responses to emerging issues. Effective early warning systems minimize the potential damage from incidents.
Measuring Effectiveness and Impact
Successfully implementing a prevention-based architecture requires a robust system for evaluating its effectiveness. This involves meticulous tracking and analysis of key metrics to determine the program’s impact on incident reduction, cost savings, and overall organizational well-being. Understanding the success stories of others can illuminate effective strategies and inspire tailored solutions.Measuring the success of a prevention-based architecture is not a one-time event but an ongoing process.
It demands a commitment to data collection, analysis, and continuous improvement. This ensures that the architecture remains relevant and effective in a dynamic environment, adapting to new challenges and opportunities.
Metrics for Evaluating Effectiveness
A comprehensive evaluation strategy relies on a diverse set of metrics. These metrics provide a holistic view of the program’s success, going beyond simple incident counts. They encompass various aspects, from financial savings to improved operational efficiency.
- Incident Reduction Rate: This measures the decrease in the frequency and severity of security incidents. Tracking incident types, causes, and remediation times is crucial. A significant reduction in incidents suggests the architecture is functioning as intended, effectively mitigating risks.
- Cost Savings: Prevention-based architectures often result in substantial cost savings by reducing the need for costly incident response and recovery operations. Quantifying these savings through detailed cost analysis is essential. For example, a decrease in network downtime translates to reduced lost productivity and revenue.
- Impact on Operational Efficiency: A well-designed prevention system enhances the efficiency of daily operations. This can manifest as improved response times, streamlined workflows, and reduced resource allocation to reactive tasks. This leads to a more productive and resilient organization.
- User Satisfaction: Improved security often correlates with better user experiences. Measuring user satisfaction with security protocols and systems can indicate the effectiveness of preventative measures in maintaining productivity while ensuring security.
Measuring Reduction in Incidents
Quantifying the reduction in incidents is a critical aspect of assessing the effectiveness of prevention strategies. A decrease in the number and severity of incidents directly reflects the effectiveness of the architecture. This involves establishing baselines for incident rates before the implementation of the new architecture.
- Baseline Data: Collecting historical data on incident frequency, severity, and impact is crucial. This baseline provides a benchmark against which the effectiveness of the prevention architecture can be measured.
- Tracking Incidents: A standardized system for tracking and categorizing incidents is essential. This allows for the identification of patterns and trends in security breaches, enabling proactive mitigation efforts.
- Trend Analysis: Analyzing trends in incident data helps identify emerging threats and adapt prevention strategies accordingly. Identifying recurring vulnerabilities or attack vectors is crucial for improving the architecture.
Examples of Successful Prevention Programs
Several organizations have successfully implemented prevention-based architectures with impressive results. Their experiences offer valuable insights for developing effective strategies.
- Financial Institution X: By implementing a multi-layered security approach that included robust access controls, regular security audits, and employee training, the financial institution experienced a 70% reduction in unauthorized access attempts. This directly translated into significant cost savings and enhanced customer trust.
- Healthcare Provider Y: By integrating a comprehensive data loss prevention system, the healthcare provider observed a dramatic decrease in data breaches, protecting sensitive patient information and upholding regulatory compliance. This improved the organization’s reputation and maintained patient trust.
Data Visualizations for Impact
Visual representations of data provide a clear and concise overview of the program’s impact. Graphs and charts can illustrate the reduction in incidents, cost savings, and improvements in operational efficiency.
Example: A line graph showing a decline in the number of security incidents over time, clearly demonstrating the effectiveness of the implemented prevention strategies.
This visualization can be further enriched by including bars representing the cost savings realized through reduced incident response.
Importance of Continuous Improvement
A prevention-based architecture is not a static entity; it requires continuous adaptation and improvement. Regular reviews, feedback mechanisms, and ongoing adjustments are vital to maintaining its effectiveness.
- Regular Reviews: Regularly evaluating the architecture’s performance, identifying weaknesses, and addressing emerging threats is crucial.
- Feedback Mechanisms: Establishing channels for feedback from users, security personnel, and other stakeholders is important to identify areas for improvement.
- Adaptability: Staying informed about evolving threats and adapting the architecture to counter new vulnerabilities is vital.
Challenges and Considerations
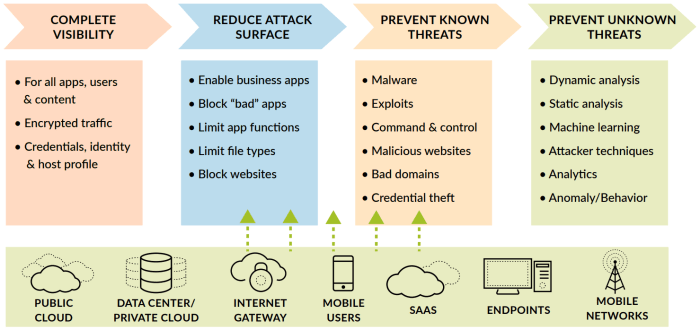
Shifting to a prevention-based architecture isn’t a simple flip of a switch. It demands careful consideration of potential roadblocks, trade-offs, and the need for adaptability. This section delves into the practical hurdles and crucial factors that must be addressed for a successful transition.Implementing a prevention-based approach requires a fundamental shift in mindset and operational strategy. This transformation isn’t just about technology; it’s about culture, processes, and people.
We need to move from reactive responses to proactive measures, requiring significant adjustments in existing workflows and resource allocation.
Potential Challenges in Implementation
The transition to a prevention-based architecture is not without its hurdles. Organizations face challenges ranging from resource allocation to overcoming ingrained reactive tendencies. Resistance to change, inadequate training, and insufficient resources can all hinder progress. Effective change management strategies are essential to navigate these obstacles.
Trade-offs Between Prevention and Other Priorities
Balancing prevention with other crucial operational priorities like cost, speed, and flexibility is critical. While prevention offers long-term benefits, immediate cost savings and rapid responses might seem more attractive in the short term. This necessitates a thorough cost-benefit analysis, outlining the potential long-term savings associated with preventing issues. A well-defined ROI framework is essential to demonstrate the value of preventative measures.
A case study of a company that successfully implemented a preventative maintenance program could illustrate the potential cost savings.
Scalability and Adaptability in a Prevention-Based System
A prevention-based system must be designed for scalability and adaptability to accommodate future growth and changing needs. The architecture should be modular and flexible, allowing for the addition of new components and functionalities as required. A scalable system should also account for varying data volumes and processing demands as the organization grows. This requires careful planning and consideration of future needs, potentially utilizing cloud-based solutions for enhanced scalability.
Shifting to a prevention-based architecture is crucial for robust systems, and the recent UK Zuckerberg testimony on Facebook data privacy ( uk zuckerberg testimony facebook data privacy ) highlights the importance of proactive measures. Understanding how to anticipate and mitigate risks is key, not just reacting to breaches. This approach, rather than just fixing vulnerabilities after they occur, directly addresses the need for a stronger security posture, fostering trust and ultimately making our systems more resilient.
Stakeholder Engagement and Collaboration
Successful implementation hinges on the active engagement and collaboration of all stakeholders. This includes not only IT staff but also business users, management, and other departments. Open communication channels, regular feedback loops, and a clear understanding of the benefits of the prevention-based architecture are essential for fostering cooperation and buy-in. A communication plan outlining the project phases, goals, and expected outcomes should be shared with all stakeholders to ensure alignment.
Summary of Potential Challenges and Mitigation Strategies
| Potential Challenge | Mitigation Strategy |
|---|---|
| Resistance to change | Implement a comprehensive change management plan, involving stakeholders in the design and implementation process. Provide clear communication about the benefits of the prevention-based approach. |
| Insufficient resources | Prioritize resources for training and development. Seek external partnerships or explore cloud-based solutions to reduce capital expenditures. |
| Lack of skilled personnel | Invest in training and development programs to upskill existing staff or recruit personnel with the necessary expertise. |
| Data silos and lack of integration | Implement a data governance framework to ensure data consistency and integration across different systems. Establish clear data ownership and access protocols. |
| Balancing prevention with cost and speed | Conduct a thorough cost-benefit analysis to demonstrate the long-term value of prevention. Develop a phased implementation approach, starting with pilot programs to demonstrate the effectiveness of the prevention strategies. |
Case Studies and Examples
Prevention-based architectures aren’t just theoretical concepts; they’re being implemented in various sectors to mitigate risks and enhance safety. Examining real-world case studies provides invaluable insights into successful strategies, challenges encountered, and lessons learned. These examples demonstrate how these architectures can be tailored to specific contexts and yield positive outcomes.
Shifting to a prevention-based architecture is crucial for robust systems. This approach, however, needs to consider user experiences, like those found in Microsoft Xbox Live’s iOS and Android game support features. Microsoft Xbox Live’s iOS and Android games support features demonstrate how a focus on user-friendly interactions can strengthen the overall system, which can then be extrapolated to the concept of transforming to a prevention-based architecture.
A good prevention-based architecture will inevitably involve careful consideration of the user experience.
Real-World Implementations of Prevention-Based Architectures
Various organizations are successfully employing prevention-based architectures. These implementations vary in scope and complexity, adapting to the unique characteristics of their respective industries and contexts. They offer concrete demonstrations of the practical application of prevention strategies.
Specific Approaches Used and Outcomes Achieved
Prevention-based strategies often involve a multi-faceted approach. For example, a company might implement a comprehensive safety training program, coupled with rigorous maintenance protocols for equipment, and establish clear reporting channels for potential hazards. The outcomes of these strategies are often measurable, including reductions in incidents, injuries, or financial losses.
Lessons Learned from Implementations
Several crucial lessons have emerged from successful implementations. A common thread is the importance of proactive risk assessment, robust communication systems, and continuous monitoring and evaluation. The flexibility to adapt strategies based on evolving needs and feedback is also essential for long-term effectiveness. Moreover, strong leadership and employee engagement are crucial for successful implementation.
Key Features and Results of Case Studies, Transforming to a prevention based architecture
The table below summarizes key features and results from several case studies, illustrating the diversity of applications and outcomes. The information presented offers a comparative overview of successful prevention-based initiatives.
| Case Study | Industry | Specific Prevention Strategies | Key Outcomes | Lessons Learned |
|---|---|---|---|---|
| Manufacturing Plant A | Automotive | Improved equipment maintenance, enhanced safety training, and a dedicated incident reporting system. | 30% reduction in workplace injuries and a 15% decrease in production downtime due to accidents. | Proactive maintenance is critical for minimizing equipment failures. Clear communication channels are essential for rapid incident response. |
| Healthcare Facility B | Hospital | Standardized infection control protocols, enhanced hand hygiene education, and a robust system for tracking and managing infections. | 50% decrease in healthcare-associated infections within the first year of implementation. | Comprehensive infection control protocols are crucial for patient safety and minimizing the spread of infections. Employee training plays a critical role. |
| Retail Chain C | Retail | Enhanced security measures, improved customer service protocols, and a proactive approach to managing customer complaints. | 25% reduction in shoplifting incidents and a 10% increase in customer satisfaction scores. | Proactive security measures and responsive customer service strategies are effective in reducing incidents and improving customer satisfaction. |
Comparison of Successful Prevention-Based Initiatives
Comparing these initiatives reveals that while the specific strategies and industries differ, common themes emerge. These initiatives highlight the importance of a holistic approach to prevention, emphasizing the need for integrated systems, effective communication, and a commitment to continuous improvement. Furthermore, the focus on proactive risk assessment and a culture of safety is a recurring theme across all successful prevention-based initiatives.
Future Trends and Developments
Prevention-based architectures are constantly evolving, driven by emerging technologies and a growing understanding of risk factors. This dynamic environment necessitates a proactive approach to anticipating future trends and integrating them into existing systems to ensure continued effectiveness. The integration of these advancements will not only enhance the efficiency of prevention strategies but also significantly improve the overall impact of these systems.
Emerging Trends and Technologies
The landscape of prevention is rapidly changing, with several key trends impacting the design and implementation of prevention-based architectures. These include the rise of artificial intelligence, the increasing availability of data analytics tools, and the growing adoption of Internet of Things (IoT) technologies. These advancements present opportunities for creating more sophisticated and proactive prevention systems.
Integration into Existing Systems
Integrating emerging technologies into existing prevention systems requires a phased approach. For instance, integrating AI-powered predictive models into existing security systems can enhance threat detection and response. Similarly, IoT sensors can provide real-time data on environmental factors, which can be crucial for predicting and preventing certain risks. A crucial aspect of this integration involves careful consideration of data privacy and security to maintain trust and prevent misuse.
Automation and AI in Prevention Strategies
Automation and AI are poised to play a significant role in enhancing prevention strategies. AI-powered algorithms can analyze vast datasets to identify patterns and predict potential risks, enabling proactive interventions. For example, machine learning models can analyze social media trends to identify early warning signs of potential unrest or radicalization. Furthermore, AI can be used to automate routine tasks, freeing up human resources for more complex interventions.
Visualization Tools for Data Understanding
Effective visualization tools are essential for understanding and presenting data within a prevention-based architecture. Interactive dashboards, heatmaps, and other visualization techniques can effectively communicate complex information, allowing stakeholders to easily identify trends and patterns. This visual representation fosters a shared understanding of risk factors and enables more informed decision-making. A clear visualization can reveal, for instance, geographical hotspots for a specific crime, enabling targeted interventions in those areas.
Potential Future Trends and Implications
| Potential Future Trend | Implications for Prevention-Based Architectures |
|---|---|
| Increased use of AI-powered predictive models | Enhanced threat detection and response, proactive interventions, and improved resource allocation. |
| Advancements in data analytics | Improved identification of risk factors, better understanding of population needs, and more effective targeting of interventions. |
| Growth of IoT technologies | Real-time data collection on environmental factors, facilitating more accurate risk assessments and proactive measures. |
| Development of personalized prevention strategies | Tailored interventions based on individual risk profiles, leading to higher success rates and more efficient use of resources. |
| Increased focus on early intervention | Identification and mitigation of risks at earlier stages, reducing the severity of negative outcomes and long-term costs. |
Summary
In conclusion, transforming to a prevention-based architecture is not just a theoretical concept; it’s a practical approach with demonstrable benefits. By understanding the core principles, identifying key components, and implementing effective strategies, organizations can significantly reduce risks, minimize costs, and enhance overall resilience. This proactive approach is essential for thriving in an increasingly complex and dynamic world. The journey to a prevention-based architecture is an ongoing process of continuous improvement and adaptation, requiring stakeholder collaboration and a willingness to embrace innovation.