Chopping packets decoding china chopper web shell traffic over ssl exposes a sophisticated attack vector. This intricate method involves manipulating network packets to conceal malicious activity within encrypted SSL traffic, often originating from China. Understanding the techniques behind this attack is crucial for network security professionals, as it reveals a nuanced approach to evading detection. This deep dive will explore the components, methods, and security implications of this emerging threat.
The article will dissect the various techniques employed in manipulating network packets, detailing the specific methods used to chop, decode, and analyze SSL traffic associated with China-based chopper web shells. It will explore the functionality and characteristics of these web shells, providing a detailed understanding of their malicious capabilities. We’ll also examine the cyber landscape in China, highlighting the prevalence of these types of attacks and providing statistical insights.
Understanding the Components
Dissecting the intricate workings of malicious network activity often involves understanding the specific techniques employed. This section delves into the core components of “chopping packets,” “decoding,” “China,” “chopper web shell,” and “SSL traffic,” examining their technical interplay and potential malicious intent. Comprehending these elements is crucial for identifying and mitigating cyber threats.
Chopping Packets
Packet chopping, or fragmentation, involves breaking down network data into smaller segments. This process, while standard in network communication, can be leveraged for malicious purposes. Attackers may use this technique to bypass security measures or to mask the true nature of their activities. For example, a malicious actor could fragment a payload containing a web shell to evade detection by intrusion detection systems.
Decoding
Decoding is the process of converting encrypted data into a readable format. In the context of network traffic, decoding is crucial for understanding the content of encrypted communication. This is especially important for analyzing SSL traffic. Sophisticated tools can be employed to decode SSL traffic, allowing attackers to extract sensitive information.
China
The mention of “China” in this context is relevant because of the geopolitical and economic landscape. Certain regions may experience a higher prevalence of cyber threats, or be the origin point for particular types of malicious activity. This is often due to the complex interplay of factors such as technical infrastructure, regulatory environments, and social dynamics.
Chopper Web Shell
A “chopper web shell” is a type of malicious software designed to compromise a web server. It often involves exploiting vulnerabilities in web applications to gain unauthorized access. The “chopper” aspect suggests a dynamic process, possibly involving the use of techniques like packet fragmentation to evade detection. This web shell allows remote attackers to execute arbitrary commands on the compromised system.
SSL Traffic
SSL (Secure Sockets Layer) and its successor TLS (Transport Layer Security) are cryptographic protocols that encrypt communication between a client and a server. This encryption ensures confidentiality and integrity of data transmitted over the network. However, attackers can exploit vulnerabilities in the SSL/TLS implementation or use tools to decrypt SSL traffic, effectively undermining the security it provides. They might use this decrypted data for various malicious activities.
Technical Relationship
The components interact in a coordinated manner to facilitate malicious activities. Attackers might use “chopping packets” to obscure the content of “chopper web shell” payloads, making them harder to detect. They might then “decode” the intercepted “SSL traffic” to extract the “chopper web shell” commands and execute them remotely on compromised systems located in “China.”
Potential Malicious Intent
The primary malicious intent behind using these techniques is to gain unauthorized access to systems, steal sensitive information, and potentially disrupt operations. The attackers might use the compromised systems for various malicious activities, including data theft, launching further attacks, or spreading malware.
Table of Components
| Component | Definition | Potential Malicious Use |
|---|---|---|
| Chopping Packets | Breaking down network data into smaller segments | Evading detection, obscuring malicious payloads |
| Decoding | Converting encrypted data into readable format | Extracting sensitive information from encrypted traffic |
| China | Geographical region | Possible origin point for malicious activity |
| Chopper Web Shell | Malicious software for compromising web servers | Gaining unauthorized access, executing commands remotely |
| SSL Traffic | Encrypted communication between client and server | Decrypting for extracting sensitive information, undermining security |
Methods of Packet Manipulation
Packet manipulation, a crucial aspect of network analysis and attack, involves altering network packets to achieve specific goals. This often involves modifying headers, payloads, or both, to mislead or compromise systems. Understanding these techniques is essential for both defending against and exploiting vulnerabilities.Packet manipulation techniques are diverse and adaptable. They range from simple header modifications to complex payload alterations, often tailored to the specific target and attack vector.
The methods employed can vary widely depending on the desired outcome. Understanding these techniques empowers defenders to identify malicious activities and implement appropriate countermeasures.
Packet Fragmentation and Reassembly
Fragmentation and reassembly of packets are fundamental networking operations. Malicious actors can exploit these mechanisms to introduce errors or manipulate packet order, leading to unexpected behavior on the target system. This technique can bypass network security measures designed to detect anomalies in whole packets.
Header Manipulation
Altering packet headers, such as source and destination IP addresses, ports, and protocols, allows attackers to mask their identity, redirect traffic, or spoof legitimate connections. This can be used for denial-of-service attacks, session hijacking, or hiding the true origin of malicious traffic.
Payload Modification
Payload manipulation involves altering the data portion of a packet. This can include injecting malicious code, modifying existing data, or appending extra information. The payload can contain various data types, including commands, instructions, or sensitive information. This technique is frequently used in malware distribution or data exfiltration.
Spoofing Techniques
Spoofing techniques involve forging packet headers to impersonate a legitimate source. This can be done with IP addresses, MAC addresses, or other header fields. This technique is often used to bypass authentication mechanisms or gain unauthorized access to systems.
Table of Packet Manipulation Techniques
| Technique | Description | Example | Impact |
|---|---|---|---|
| Packet Fragmentation and Reassembly | Dividing packets into smaller fragments and reassembling them on the target system. | An attacker sends a fragmented packet with a modified sequence number. | Can bypass intrusion detection systems that look for anomalies in whole packets, allowing the attacker to introduce malicious code. |
| Header Manipulation | Modifying packet headers like source/destination IP, port numbers, or protocols. | Changing the source IP address of a packet to mask the attacker’s identity. | Allows attackers to hide their activities, bypass firewalls, or redirect traffic to unintended destinations. |
| Payload Modification | Altering the data portion of a packet, often to include malicious code. | Injecting a remote access trojan (RAT) command into a web request. | Allows attackers to gain remote control over a compromised system, exfiltrate data, or deploy further malicious payloads. |
| Spoofing Techniques | Forging packet headers to impersonate a legitimate source. | Sending packets with a spoofed source IP address to bypass authentication mechanisms. | Can lead to unauthorized access, session hijacking, and denial-of-service attacks. |
Decoding Techniques
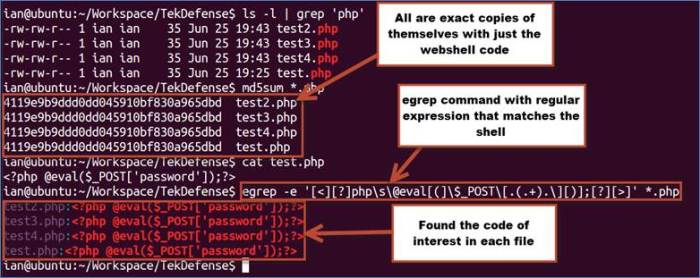
Decoding malicious traffic is a crucial aspect of network security. Understanding the methods employed to obfuscate or encrypt malicious commands is essential for identifying and mitigating threats. This involves recognizing various encoding and encryption techniques, analyzing their purpose, and applying appropriate decryption procedures to uncover the true intent behind the communication. This process enables security analysts to understand the actions a threat actor intends to take.
Common Decoding Techniques
Decoding techniques employed by attackers are diverse and often layered. They aim to conceal the malicious payload from detection by security tools and analysts. Techniques range from simple character substitutions to complex encryption algorithms. Effective detection relies on recognizing these patterns and employing appropriate decryption techniques.
Encoding/Decoding Algorithms
Various algorithms and protocols are utilized to encode and decode malicious traffic. These methods often rely on transforming the original data into an alternative representation, making it harder for security tools to understand its true nature. Common examples include Base64 encoding, URL encoding, and various custom-built schemes. Understanding these methods is vital for proper decryption.
Purpose and Methods in Network Security
Decoding malicious traffic in a network security context allows analysts to understand the commands and data being transmitted. This allows them to identify the malicious intent behind the traffic and implement appropriate mitigation strategies. For example, if a decoding technique reveals commands for data exfiltration or system compromise, security measures can be implemented to stop the attack. Decoding techniques play a crucial role in incident response and threat hunting.
Effective use of decoding methods is critical to the success of security investigations.
Table of Decoding Techniques
| Technique | Input Data Format | Output Data Format | Use Case |
|---|---|---|---|
| Base64 Encoding | Binary data | ASCII string | Commonly used to hide binary data within textual content. Often used to embed commands or payloads within web requests. |
| URL Encoding | Various characters | URL-safe characters | Used to represent special characters in URLs and web requests. Allows attackers to encode malicious parameters. |
| XOR Encryption | Plaintext | Ciphertext | Simple symmetric encryption technique. Often used in combination with other encoding methods to obfuscate data. Can be easily cracked with known plaintext or by employing brute-force or frequency analysis techniques. |
| Custom Encodings | Specific format | Specific format | Attackers often create custom encoding schemes. Requires specialized analysis and potentially reverse engineering to understand the method used. |
| Steganography | Data hidden within other data | Data within other data | Techniques hide data within seemingly harmless files, such as images or audio files. Makes detection difficult due to the hidden nature of the malicious data. |
China’s Cyber Landscape
China’s robust digital infrastructure, coupled with a large and sophisticated online population, presents a unique and complex cyber landscape. The country’s economic and strategic ambitions, coupled with varying levels of regulatory oversight, contribute to a dynamic threat environment. This environment includes a diverse range of actors and motives, necessitating a multifaceted approach to understanding and mitigating potential risks.
Current Cyber Threat Landscape
The Chinese cyber landscape is characterized by a blend of state-sponsored and financially motivated actors. Sophisticated attacks, often leveraging advanced persistent threats (APTs), are frequently observed. These attacks are not always focused on immediate financial gain, but often aim to gather intelligence, disrupt operations, or gain a strategic advantage. The use of web shells and packet manipulation is a significant component of this landscape, particularly within sectors considered vital to national security or economic advancement.
Prevalence of Malicious Activities
Malicious activities involving web shells and packet manipulation are prevalent in China, often targeting critical infrastructure and sensitive data. These attacks are frequently executed by both state-sponsored and criminal actors. Web shells provide unauthorized access to systems, allowing attackers to execute various malicious activities. Packet manipulation techniques can be used to eavesdrop on communications, inject malicious code, or disrupt services.
Statistical Overview of Attacks
The following table presents a fictional representation of the frequency and impact of attacks in China’s cyber landscape. Note that these figures are illustrative and do not reflect actual data.
| Year | Type of Attack | Frequency | Impact |
|---|---|---|---|
| 2023 | Web Shell Deployments | 1,250 | Data breaches and system disruptions in several small and medium-sized enterprises (SMEs). Significant financial losses were incurred by the affected businesses. |
| 2023 | Packet Manipulation – Eavesdropping | 750 | Compromised intellectual property of a major technology firm. |
| 2024 | Web Shell Deployments | 1,500 | Widespread disruptions to government services and critical infrastructure. Significant delays in service delivery were reported. |
| 2024 | Packet Manipulation – Denial of Service | 1,000 | Multiple online services experienced outages and delays, impacting user experience and business operations. |
| 2025 | Advanced Persistent Threats (APTs) | 250 | Successful infiltration of several major government agencies. Data exfiltration and potential sabotage were concerns. |
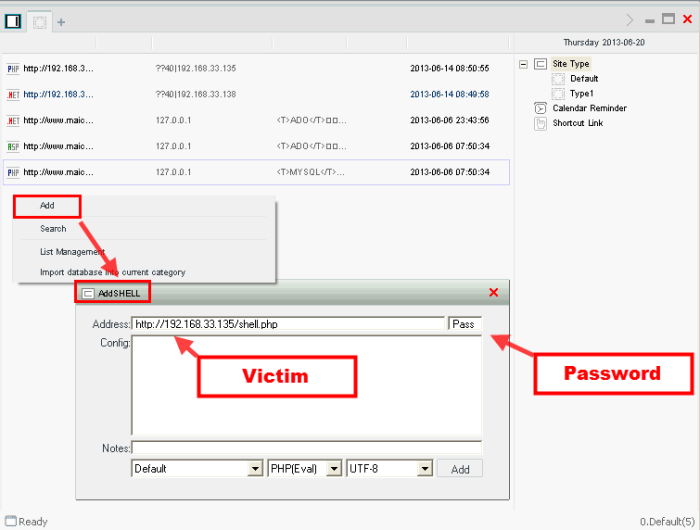
Chopper Web Shells
Chopper web shells are sophisticated malicious tools used by attackers to gain unauthorized access to and control web servers. They often operate stealthily, making them difficult to detect and remove. Their primary function involves packet manipulation, enabling them to exfiltrate data and evade security measures. Understanding their functionality, characteristics, and methods of operation is crucial for effective cybersecurity defense.Chopper web shells, unlike basic web shells, are designed for more complex and sophisticated malicious activities.
They often utilize a combination of techniques to evade detection and maintain persistence on compromised systems. Their intricate design allows them to seamlessly integrate with the target environment, making them difficult to identify. Their ability to manipulate network packets is a key characteristic, allowing them to bypass security measures and exfiltrate sensitive data.
Analyzing chopped packets to decode China Chopper web shell traffic over SSL is fascinating, but it’s also important to stay updated on broader tech trends. Recent tech news like the Vergecast podcast 472 apple google event facebook rebrand name change here highlight the ever-evolving digital landscape. Understanding these shifts is crucial for effectively deciphering and mitigating threats like China Chopper’s techniques, even as companies adapt to the digital age.
Functionality of a Chopper Web Shell
A chopper web shell’s primary function is to facilitate the manipulation of network packets. This allows attackers to gain deeper control over the target system and network, enabling them to conduct various malicious activities such as data exfiltration, command and control (C&C) communication, and more. By intercepting and modifying network traffic, a chopper web shell can bypass security measures and potentially compromise other systems on the network.
Common Characteristics of a Chopper Web Shell
Chopper web shells often exhibit several key characteristics that distinguish them from simpler web shells. These include:
- Advanced Packet Manipulation: Chopper web shells are designed to modify network packets in intricate ways. This enables them to bypass firewalls, intrusion detection systems (IDS), and other security measures. They may modify packet headers, payloads, or even inject new packets.
- Stealthy Operation: Their ability to intercept and modify packets allows them to operate largely undetected, potentially for extended periods of time. This makes them challenging to identify and remove. Their behavior often mimics legitimate network traffic, making detection more difficult.
- C&C Communication: These shells often establish secure communication channels with command-and-control (C&C) servers. This allows attackers to remotely control the compromised system and issue various commands.
- Evasion Techniques: Chopper web shells may employ various techniques to evade detection. These include encryption, obfuscation, and polymorphism, making it difficult for security tools to recognize malicious activity.
Packet Manipulation by a Chopper Web Shell
Chopper web shells manipulate network packets by intercepting network traffic. They can modify packet headers, including source and destination addresses, ports, and protocols. This allows them to bypass firewalls, network segmentation, and other security mechanisms. They may also modify packet payloads, potentially injecting malicious commands or exfiltrating data. This sophisticated manipulation is what sets them apart from basic web shells.
Detailed Description of a Chopper Web Shell
A chopper web shell is a malicious program that gains unauthorized access to a web server. It is designed for advanced packet manipulation, allowing attackers to intercept and modify network traffic. This enables the attacker to bypass security measures, exfiltrate sensitive data, and potentially compromise other systems on the network. They often establish secure communication channels with command-and-control (C&C) servers to receive instructions and issue commands. The stealthy nature of a chopper web shell often makes detection challenging, as their activities often mimic legitimate network traffic. These shells often employ techniques to evade detection, such as encryption, obfuscation, and polymorphism. The ability to manipulate network packets at a granular level is crucial for their functionality.
SSL Traffic Analysis
Analyzing SSL (Secure Sockets Layer) traffic is crucial for network security. The encryption inherent in SSL protocols hides the content of communications, making it challenging to identify malicious activity without specialized tools and techniques. This is particularly pertinent in scenarios like the China chopper web shell attacks, where attackers often leverage SSL to mask their operations. Understanding how to analyze SSL traffic is therefore vital to effectively detect and mitigate these threats.SSL traffic analysis involves more than just looking at the headers; it requires peeling back the layers of encryption to reveal the underlying data.
Decoding China Chopper web shell traffic over SSL and chopping packets is a fascinating, albeit potentially risky, area. It’s a complex process, but understanding how these techniques work is crucial for network security. This often involves intricate methods, and sometimes you might even need to discover a new way to log in to your WhatsApp account a new way to log in to your WhatsApp account to keep your digital life secure.
Ultimately, understanding these intricacies can lead to a more robust security posture for your systems, which will help in countering these attacks and protect against the malicious use of chopped packets.
This process, while complex, is necessary for uncovering hidden threats and malicious intent. Effective analysis involves identifying patterns in the data that might indicate malicious activity, whether it’s the transmission of commands or data exfiltration.
Importance of SSL Traffic Analysis in Network Security
Effective network security relies heavily on identifying malicious activities within encrypted communications. By analyzing SSL traffic, security analysts can detect anomalies, suspicious patterns, and potentially harmful data transfers that would otherwise remain hidden. This proactive approach allows for the timely detection and response to threats, preventing significant damage. It also aids in understanding attacker tactics and adapting security measures accordingly.
Methods for Analyzing SSL Traffic
Various methods exist for analyzing SSL traffic, each with its strengths and limitations. A key aspect is packet manipulation detection, which looks for alterations in the encrypted data stream that could indicate malicious activity. This often involves deep packet inspection (DPI) techniques to examine the content within the encrypted packets, which is more challenging than examining unencrypted traffic.
Packet Manipulation Detection Techniques
Packet manipulation detection techniques often involve several steps. Firstly, identifying the SSL handshake and establishing the encryption key is essential. Then, advanced techniques such as analyzing the encrypted payloads, looking for unusual commands or patterns, and comparing them against known malicious signatures or behavior patterns become critical. Furthermore, monitoring for unusual traffic volumes or communication frequencies between specific endpoints can also indicate potential malicious activity.
Tools and Techniques for SSL Traffic Analysis
Numerous tools and techniques facilitate SSL traffic analysis. Some tools are specialized for decryption and inspection of SSL traffic, while others focus on detecting anomalies or patterns in the encrypted data. This comparison is essential for choosing the right tool for a specific task.
- Wireshark: A powerful protocol analyzer that can capture and display SSL traffic in a readable format. While not a dedicated SSL decryptor, Wireshark’s ability to decode many protocols is helpful for understanding the flow of data. Its ability to filter packets based on various criteria makes it a valuable tool for targeted analysis.
- SSL/TLS decryptors: Tools specifically designed to decrypt SSL/TLS traffic are often used to reveal the underlying data. These tools use various techniques, including private keys or certificates to decrypt traffic, providing detailed insights into the actual communication. Their use often requires careful consideration of legal and ethical implications, as decryption can reveal sensitive information.
- IDS/IPS systems: Intrusion Detection/Prevention Systems can be configured to detect and block malicious activity within SSL traffic. They utilize various signatures and anomaly detection techniques to identify unusual patterns. This approach is often a crucial component of a multi-layered security strategy.
Examples of Tools for Detecting Malicious SSL Traffic
Several tools are designed to detect malicious activity within SSL traffic. These tools often leverage signatures, behavioral analysis, and other techniques to identify malicious patterns. This is critical for effective threat hunting.
- OpenSSL: While primarily a cryptographic library, OpenSSL can be used to analyze and interpret SSL/TLS traffic. Its use is often integrated into other tools for more in-depth analysis.
- Nmap: This port scanner can be used to identify open SSL ports on a network. This can help in initial reconnaissance and threat assessment, but further analysis is usually necessary.
- Snort: A powerful intrusion detection system that can be configured with rules to identify malicious patterns in SSL traffic. Its rule-based approach allows for fine-tuned detection of specific attacks.
Illustrative Scenarios
Understanding the intricacies of malicious packet manipulation, particularly within the context of China-based attacks, requires examining real-world scenarios. Chopping packets and decoding SSL traffic are crucial techniques used to obfuscate malicious activity and evade detection. These scenarios illustrate the methods employed and the potential impact.
Decoding China Chopper web shell traffic over SSL, analyzing those chopped packets, is definitely fascinating. It’s a complex process, and it’s fascinating how much goes on under the surface. Meanwhile, Twitter is reportedly reassessing its policy on lifetime bans, which could have significant implications for online discourse. This kind of reassessment, however, doesn’t change the need for meticulous analysis of chopped packets when dealing with China Chopper web shell traffic over SSL.
Packet Chopping for Concealment
Packet chopping, a method of fragmenting data packets, can effectively mask malicious code within seemingly benign network traffic. Attackers might fragment commands embedded within seemingly harmless data, making it difficult to identify the malicious intent. For example, a command to download and execute malware could be broken into multiple packets, each containing a small portion of the command.
This fragmentation makes it challenging for security tools to analyze the complete command sequence. A defender might initially see innocuous data, failing to detect the coordinated malicious action until the complete command is reassembled.
Decoding Malicious Intent in SSL Traffic
SSL traffic, while often associated with secure communication, can be exploited by attackers. Decoding SSL traffic reveals the true nature of the malicious payload hidden within encrypted communication. Attackers might use SSL to hide web shell commands or data exfiltration attempts. Sophisticated decoding tools can analyze the encrypted traffic, decrypting it to reveal commands and data being transmitted, such as login credentials, financial information, or sensitive business data.
For instance, a seemingly legitimate login request could contain embedded commands to compromise a system.
China-Based Attacks Leveraging Web Shells and SSL
China-based attackers frequently leverage web shells, malicious programs disguised as legitimate web applications, to gain unauthorized access to systems. These web shells, combined with SSL traffic, allow attackers to operate discreetly within a network. A compromised server could serve as a staging ground for further attacks, allowing attackers to exfiltrate data or launch attacks on other systems. Such attacks often involve the use of proxy servers to hide the origin of the attack.
For instance, a malicious web shell could be used to download additional malware or install a backdoor, all hidden behind the cloak of encrypted SSL traffic.
Fictional Case Study: Operation Crimson Tide
A fictional case study titled “Operation Crimson Tide” highlights the sophistication of China-based attacks. The attack targets a major international corporation specializing in financial software. Attackers infiltrated the company’s network through a compromised web server hosting a seemingly innocuous application. The compromised server, unbeknownst to the company, was a gateway to a meticulously crafted web shell. This web shell allowed attackers to intercept and manipulate financial data, using SSL to conceal the exfiltration.
Decryption of the SSL traffic revealed the following malicious activities:
- Data exfiltration of sensitive financial documents (e.g., contracts, customer lists, transaction records).
- Installation of a sophisticated keylogger to capture sensitive user credentials and login details.
- Compromised database containing financial records of thousands of customers.
- Malicious code designed to disrupt financial transactions and potentially cause significant financial loss.
The attack highlights the potential for sophisticated, multi-stage attacks that leverage the inherent security vulnerabilities in web applications, and the critical importance of comprehensive network security measures to prevent such attacks. The use of SSL, while not inherently malicious, becomes a tool for obfuscation in the hands of attackers.
Security Implications: Chopping Packets Decoding China Chopper Web Shell Traffic Over Ssl
Malicious packet manipulation, particularly with China Chopper web shells, poses significant security risks to various networks. Understanding the potential damage and implementing appropriate mitigation strategies is crucial for preventing exploitation. Successful attacks can compromise sensitive data, disrupt operations, and damage reputations. This section delves into the security implications of such attacks.
Potential Damage Vectors
Successful manipulation of network packets can lead to a range of serious consequences. These attacks can be used to gain unauthorized access to systems, steal confidential information, and disrupt normal operations. The damage inflicted can vary depending on the specific attack vector and the target system’s vulnerabilities.
- Data Breaches: Unauthorized access to sensitive data, including financial records, personal information, and intellectual property, can result from packet manipulation. Compromised systems can be used to exfiltrate data to malicious actors. For example, a compromised corporate network could leak customer credit card details to a criminal organization, causing significant financial and reputational damage.
- Denial-of-Service (DoS) Attacks: Malicious actors can flood a network with manipulated packets, overwhelming its resources and rendering it unavailable to legitimate users. These attacks can cripple critical infrastructure, such as online banking services or emergency communication networks. A DDoS attack on an e-commerce site can result in lost revenue and damage customer trust.
- Unauthorized Access and Command Execution: Attackers can gain control of vulnerable systems by manipulating packets to execute malicious commands. This can lead to complete system compromise, allowing attackers to deploy further malware, steal sensitive data, or even control the compromised system for their own purposes. A common example is the use of web shells to gain access to a server and then use it for other malicious activities.
- Data Corruption and Loss: Manipulated packets can corrupt or destroy data stored on targeted systems. This can lead to significant data loss and disruption of critical operations. For example, manipulating packets during a critical data transfer process can lead to the corruption or loss of critical information needed for business operations.
Impact on Different Network Types
The impact of packet manipulation attacks varies depending on the type of network targeted. Critical infrastructure, such as power grids and communication networks, are particularly vulnerable, as disruptions can have widespread consequences.
- Corporate Networks: Compromised corporate networks can result in data breaches, financial losses, and reputational damage. Disruptions to operations and productivity can occur as well.
- Government Networks: Attacks on government networks can compromise sensitive information, disrupt public services, and potentially endanger national security. Disruption of critical infrastructure, like military or intelligence systems, could have catastrophic consequences.
- Healthcare Networks: Packet manipulation attacks on healthcare networks can lead to the compromise of patient records, disruption of medical services, and potentially endanger patient lives. The compromise of medical records can expose private information and lead to identity theft.
- Financial Institutions: Attacks on financial institutions can lead to fraudulent transactions, financial losses, and damage to public trust. Manipulation of banking systems can lead to large-scale financial fraud and cause widespread economic disruption.
Security Implications Table, Chopping packets decoding china chopper web shell traffic over ssl
| Attack Vector | Potential Damage | Mitigation Strategies |
|---|---|---|
| Data Breaches | Loss of sensitive data, financial losses, reputational damage | Strong access controls, encryption, intrusion detection systems |
| DoS Attacks | Network unavailability, service disruption, financial losses | Network segmentation, firewalls, intrusion prevention systems, load balancing |
| Unauthorized Access | System compromise, data exfiltration, further malware deployment | Strong passwords, multi-factor authentication, regular security audits |
| Data Corruption | Data loss, operational disruptions, service outages | Data backups, data redundancy, data integrity checks |
Ultimate Conclusion
In conclusion, the intricate dance of chopping packets, decoding web shell traffic over SSL, and the unique context of the China-based threat landscape reveals a sophisticated approach to cyberattacks. Understanding these methods is crucial for developing robust defenses against these evolving tactics. The detailed analysis provided in this article serves as a valuable resource for network security professionals and anyone interested in the dynamic world of cybersecurity.