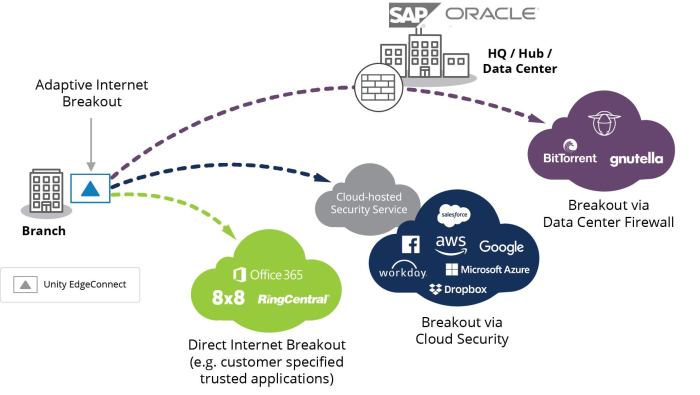
SD deployment service for enhanced plus for Prisma Access Enterprise is a powerful solution for modern enterprise security. It provides a streamlined way to deploy and manage Prisma Access, enhancing its capabilities for complex environments. This service simplifies the integration process and provides a clear path to leveraging Prisma Access’s advanced features. This guide delves into the key aspects of this service, from deployment strategies to operational management, helping you understand its full potential within your organization.
The service offers a robust architecture, incorporating various components that work seamlessly together. This ensures a secure and efficient deployment process. Furthermore, it offers a comparison with other deployment methods, highlighting the advantages of using this specific approach for Prisma Access Enterprise. The guide also explores the typical use cases, demonstrating how the service can meet the needs of diverse enterprise environments.
Introduction to SD Deployment Service

The SD Deployment Service is a crucial component for efficiently deploying and managing Prisma Access Enterprise within complex enterprise environments. It streamlines the process of configuring and integrating security domains, ensuring a secure and controlled access model. This service automates many manual tasks, allowing security teams to focus on higher-level strategic initiatives.This service offers a centralized platform for configuring and deploying Prisma Access Enterprise, facilitating consistent and controlled access policies across diverse applications and resources.
It simplifies the complex process of establishing secure connections and micro-segmentation for cloud applications.
SD deployment services for enhanced plus Prisma Access Enterprise are crucial for streamlined workflows. Learning about the latest smart home tech, like in a recent Michele Turner interview discussing Matter and Google Nest integration matter google nest smart home michele turner interview , can actually help optimize your deployment strategies. These services need to be adaptable and secure, just like the smart home ecosystem itself.
Core Functionalities of SD Deployment Service, Sd deployment service for enhanced plus for prisma access enterprise
The SD Deployment Service facilitates the automation of tasks critical for securing enterprise applications. Key functionalities include automated configuration of security policies, seamless integration with existing infrastructure, and continuous monitoring of deployed environments. It also supports the creation of custom security profiles tailored to specific application requirements.
Benefits of Leveraging SD Deployment Service
Utilizing the SD Deployment Service for Prisma Access Enterprise offers significant advantages. These include accelerated deployment times, reduced operational overhead, and enhanced security posture. The automated provisioning and configuration processes minimize manual effort, minimizing the potential for human error and reducing the risk of configuration drift.
Service Architecture Overview
The SD Deployment Service’s architecture is designed for scalability and reliability. A central management console allows for centralized control over deployments. This console interacts with various components, including a policy engine for defining access rules and a deployment engine for automated provisioning. The service further integrates with Prisma Access Enterprise’s existing infrastructure, ensuring seamless integration and minimal disruption to existing operations.
A critical component is the monitoring engine, which continuously tracks and reports on the deployed environment’s health and security posture. This architecture enables the service to handle diverse and complex deployments across various cloud platforms.
Comparison with Other Deployment Methods
Traditional manual deployment methods for Prisma Access Enterprise are often time-consuming and error-prone. These methods frequently involve intricate configuration steps and require significant expertise. In contrast, the SD Deployment Service significantly reduces the complexity and risk associated with deployments. It automates these processes, improving efficiency and reliability. The service’s automation capabilities and centralized management approach make it significantly more efficient than manual deployment methods.
The result is a more secure and streamlined approach to deploying Prisma Access Enterprise.
Typical Use Cases in Enterprise Environments
The SD Deployment Service is applicable to various enterprise use cases, including application deployments, cloud migration, and secure access to cloud resources. A common use case is the secure deployment of applications running in a hybrid cloud environment. This allows organizations to control access to their applications while adhering to strict security policies. Another example includes deploying Prisma Access Enterprise across multiple data centers or regions.
This centralized approach to deployment simplifies management and ensures consistency across all locations.
Enhanced Prisma Access Enterprise Features
Prisma Access Enterprise offers a robust platform for secure access management, and its enhanced features are crucial for streamlining and bolstering secure deployments of software. These enhancements directly impact the efficiency and security of the SD Deployment Service, providing a more comprehensive and reliable solution for organizations seeking to implement secure remote access.The enhanced features of Prisma Access Enterprise provide a significant improvement in the functionality of the SD Deployment Service, allowing for more granular control and improved security postures.
This streamlined approach reduces complexity and enhances the overall user experience.
Enhanced Security Controls for SD Deployment
Prisma Access Enterprise’s advanced security controls are paramount for the SD Deployment Service. These controls extend beyond basic authentication, offering a layered approach to security. This includes granular access policies, multi-factor authentication (MFA) integrations, and advanced threat detection. Such enhancements minimize vulnerabilities and ensure compliance with industry standards.
Improved Scalability and Performance for Enterprise Needs
Prisma Access Enterprise’s architecture is designed for scalability, enabling seamless handling of increased user traffic and deployments. This robust infrastructure is vital for SD Deployment Service, as it can handle the demands of large organizations with numerous users and applications. The improved performance contributes to a more responsive and reliable user experience, preventing delays or service disruptions.
Integration with Existing Infrastructure
Prisma Access Enterprise’s ability to integrate with existing infrastructure is a significant advantage for SD Deployment Service. This seamless integration reduces the complexities and disruptions associated with migrating to a new access management system. Organizations can leverage their existing systems and workflows without significant modifications, ensuring a smooth transition.
Comparison with Other Access Management Solutions
Prisma Access Enterprise, when integrated with the SD Deployment Service, offers a comprehensive solution. It stands apart from other solutions by providing advanced security controls, enhanced scalability, and a robust integration framework. A direct comparison with competitor solutions reveals a stronger emphasis on security and performance, resulting in a superior user experience. This is especially true when evaluating solutions focused on enterprise-grade security requirements.
Addressing Enterprise Security Concerns with SD Deployment Service
The SD Deployment Service, coupled with Prisma Access Enterprise, effectively addresses several critical enterprise security concerns. These include:
- Reduced Attack Surface: Prisma Access Enterprise enables granular access control, limiting potential entry points for malicious actors. By restricting access to only authorized users and applications, the deployment service significantly reduces the overall attack surface.
- Enhanced Compliance: Prisma Access Enterprise’s integration with various compliance frameworks ensures adherence to industry standards and regulations. This simplifies compliance efforts for organizations utilizing the SD Deployment Service.
- Improved Visibility and Control: Prisma Access Enterprise provides detailed monitoring and reporting capabilities, giving administrators visibility into user activity and potential security threats. This improved visibility allows for proactive threat management and facilitates better control of access to sensitive data and applications.
Deployment Strategies and Procedures
Deploying a secure and reliable SD Deployment Service for Prisma Access Enterprise requires careful planning and execution. This process involves understanding the prerequisites, choosing the appropriate deployment strategy, and addressing potential challenges. This guide provides a structured approach to successfully implement the service, focusing on best practices for security and efficiency.
Prerequisites and Dependencies
Successful deployment hinges on several key prerequisites. These ensure a smooth transition and avoid unexpected roadblocks. A thorough understanding of the necessary components and their interdependencies is critical. This includes network configurations, system requirements for the Prisma Access Enterprise platform, and the availability of appropriate personnel with the necessary technical expertise. A comprehensive checklist outlining these prerequisites will significantly reduce potential deployment issues.
- Network Connectivity: A stable and reliable network connection is paramount for seamless communication between the SD Deployment Service components and the Prisma Access Enterprise environment. This involves verifying sufficient bandwidth, firewall configurations, and DNS resolution.
- System Requirements: The Prisma Access Enterprise platform and the SD Deployment Service components must meet specific system requirements for optimal performance. This includes checking hardware specifications, operating system compatibility, and available storage space.
- Personnel Expertise: A team with sufficient knowledge of network security, cloud computing, and Prisma Access Enterprise is crucial for the successful deployment and ongoing maintenance of the SD Deployment Service. Training and documentation are vital for empowering the team.
Deployment Strategies
Different deployment strategies cater to various needs and environments. Choosing the right strategy depends on factors like infrastructure availability, security requirements, and scalability needs.
- Cloud-Based Deployment: Cloud-based deployments offer scalability and flexibility. The SD Deployment Service can be deployed on cloud platforms like AWS, Azure, or Google Cloud. This approach allows for quick provisioning and scaling resources as needed. A key consideration is the choice of cloud provider and its specific security policies.
- On-Premise Deployment: On-premise deployments offer greater control over the infrastructure. The SD Deployment Service is installed and managed on dedicated hardware within the organization’s data center. This option might be more suitable for organizations with strict security regulations or specific compliance requirements. The on-premise deployment requires significant upfront investment in hardware and infrastructure maintenance.
Deployment Procedures
A step-by-step procedure streamlines the deployment process. This ensures consistency and reduces errors. Each step should be carefully documented and reviewed before proceeding. Following a detailed checklist ensures the deployment is efficient and secure.
- Planning and Assessment: Thoroughly assess the current network infrastructure, security policies, and Prisma Access Enterprise configuration. This includes identifying potential risks and creating a detailed deployment plan.
- Infrastructure Setup: Establish the necessary infrastructure for the SD Deployment Service. This involves configuring networks, servers, and other required components.
- Deployment Configuration: Configure the SD Deployment Service according to the Prisma Access Enterprise environment. This includes setting up authentication, authorization, and other security parameters.
- Testing and Validation: Conduct rigorous testing to ensure the SD Deployment Service functions as expected. This includes validating connectivity, performance, and security measures.
- Monitoring and Maintenance: Establish monitoring and maintenance procedures for the SD Deployment Service to ensure ongoing reliability and security.
Common Deployment Challenges and Solutions
Deployments often encounter challenges. Addressing these issues proactively is essential for success. A well-defined troubleshooting strategy can mitigate the impact of these problems.
- Network Connectivity Issues: Verify network configurations, firewall rules, and DNS resolution to resolve connectivity problems. Utilize network diagnostic tools for deeper analysis.
- Security Concerns: Implement robust security measures throughout the deployment process. Use strong passwords, multi-factor authentication, and encryption techniques. Regular security audits are crucial for maintaining the security posture.
- Performance Bottlenecks: Optimize the deployment configuration and resource allocation to address performance issues. Monitor system resource usage and adjust configurations as needed.
Best Practices for Securing the Deployment Process
Implementing best practices enhances security and reduces risks during deployment. Following these practices will safeguard the SD Deployment Service and the Prisma Access Enterprise environment.
- Security Audits: Conduct regular security audits to identify and address potential vulnerabilities in the deployment process.
- Access Control: Implement strict access control policies to limit access to sensitive data and configurations.
- Regular Updates: Maintain the Prisma Access Enterprise and SD Deployment Service components with the latest security updates to mitigate known vulnerabilities.
Security and Compliance Considerations
Deploying a secure SD Deployment Service for Prisma Access Enterprise requires meticulous attention to security and compliance. A robust security posture is paramount to safeguarding sensitive data and maintaining regulatory compliance. This section delves into the critical security aspects, relevant compliance requirements, best practices for implementation and maintenance, a comprehensive security audit checklist, and potential security risks and mitigation strategies.
Critical Security Aspects
Implementing a secure SD Deployment Service involves various crucial security aspects. These include strong authentication mechanisms, role-based access controls, regular security audits, and vulnerability management. Secure configuration of the SD Deployment Service is critical, and it should comply with industry best practices and internal security policies.
Compliance Requirements
The deployment of the SD Deployment Service must align with relevant industry and regulatory compliance standards. This necessitates adherence to data protection regulations like GDPR, HIPAA, or CCPA, depending on the nature of the data being handled. Additionally, any relevant industry-specific regulations or internal security policies must be meticulously followed.
Security Best Practices
Implementing and maintaining a secure SD Deployment Service requires adhering to specific best practices. These include utilizing strong passwords, enforcing multi-factor authentication, regularly updating software and firmware, and implementing robust intrusion detection and prevention systems. Continuous monitoring and logging of system activities are vital to detect and respond to potential threats effectively.
Security Audit Checklist for SD Deployment Service
A comprehensive security audit checklist is essential to ensure the deployment meets security standards. This checklist should cover various aspects, including network security, access controls, data encryption, and compliance with relevant regulations. A thorough checklist should address configuration settings, user access privileges, and potential vulnerabilities.
- Network Security: Verify firewall rules, network segmentation, and intrusion detection/prevention systems are correctly configured and functioning as expected. Ensure that all network devices are patched and updated to the latest security releases.
- Access Controls: Review and validate user roles and privileges, confirming they align with the principle of least privilege. Assess the effectiveness of multi-factor authentication mechanisms.
- Data Encryption: Confirm data encryption is implemented at rest and in transit. Verify encryption keys are managed securely. Test the recovery procedures for encrypted data.
- Compliance: Confirm adherence to all relevant regulations (e.g., GDPR, HIPAA) through detailed documentation and audits.
- Vulnerability Management: Regularly scan the system for known vulnerabilities. Address identified vulnerabilities promptly and thoroughly.
- Incident Response: Establish a comprehensive incident response plan. Regularly test and update the plan to ensure its effectiveness.
Potential Security Risks and Mitigation Strategies
Deploying the SD Deployment Service introduces potential security risks. These include unauthorized access, data breaches, and denial-of-service attacks. Mitigation strategies involve implementing robust security controls, regularly updating software and systems, and training personnel on security best practices.
- Unauthorized Access: Employ strong authentication methods, access controls, and encryption to mitigate the risk of unauthorized access. Monitor user activity and promptly address any suspicious patterns.
- Data Breaches: Implement data loss prevention (DLP) tools, encryption, and access controls. Establish a data breach response plan. Regularly back up sensitive data to protect against data loss or corruption.
- Denial-of-Service (DoS) Attacks: Implement DDoS mitigation solutions. Utilize rate limiting and other techniques to protect against DoS attacks. Monitor network traffic and implement appropriate response mechanisms.
Integration with Existing Infrastructure: Sd Deployment Service For Enhanced Plus For Prisma Access Enterprise
Seamless integration with your existing infrastructure is crucial for a successful SD Deployment Service implementation. This ensures minimal disruption to your current operations while maximizing the benefits of the enhanced Prisma Access Enterprise features. A well-planned integration strategy minimizes downtime and ensures a smooth transition.Effective integration involves understanding the points of contact between the new service and your existing systems.
SD deployment services for enhanced Prisma Access Enterprise are crucial for smooth operations, but a great home office setup can also significantly impact productivity. Think about how your remote work setup, like the perfect writer’s desk or a gamer-friendly setup using Logitech and Asus equipment from remote work desk home set up writer gamer logitech asus , can affect your overall efficiency.
Ultimately, a well-optimized SD deployment service is key to keeping everything running smoothly in a remote or hybrid work environment.
This includes identifying critical systems like identity providers, databases, and application servers, and mapping their interactions with the SD Deployment Service. Careful planning and execution of these integrations are vital for a successful deployment.
Integration Points
Understanding the various touchpoints between the SD Deployment Service and your existing infrastructure is paramount for a smooth implementation. This allows for a proactive approach to potential issues and ensures the new service works harmoniously with your current systems. This mapping process is a critical step in the deployment process.
| System | Integration Point | Description |
|---|---|---|
| Identity Provider (e.g., Okta, Azure AD) | Authentication and Authorization | The SD Deployment Service leverages the existing identity provider for user authentication and authorization. This ensures secure access to the protected resources. |
| Databases | Data Access | The SD Deployment Service may need to access data stored in your existing databases. Appropriate access controls and secure protocols are essential. |
| Application Servers | Application Integration | The SD Deployment Service may need to interact with your existing application servers. Proper API integrations and communication protocols are needed. |
| Network Infrastructure | Traffic Routing | Integration with your network infrastructure ensures proper routing of traffic to and from the SD Deployment Service. This involves configuration of firewalls and network devices. |
Integration Process
The process of integrating with various systems involves several key steps. These steps ensure a smooth transition and minimize disruptions.
- Assessment: Thoroughly analyze your existing infrastructure to identify all relevant systems and their configurations. This includes understanding the existing security protocols and access controls.
- Planning: Develop a detailed integration plan outlining the steps, timelines, and resources required. This plan should address potential challenges and mitigation strategies.
- Configuration: Configure the SD Deployment Service to interact with your existing systems. This may involve setting up API keys, configuring network access, or establishing user roles and permissions.
- Testing: Conduct thorough testing to validate the integration and ensure the service operates as expected. This involves simulating real-world scenarios and verifying functionality across various systems.
- Deployment: Deploy the SD Deployment Service in a controlled manner, gradually rolling out the changes to minimize disruption to ongoing operations.
Common Integrations and Benefits
Several common integrations can streamline your processes and enhance security.
- Integration with Identity Providers: Using existing identity providers for authentication and authorization simplifies the onboarding process and reduces the need for separate user management systems. This ensures secure access to protected resources.
- Database Integrations: Integrating with your existing databases allows the SD Deployment Service to leverage existing data for various operations. This ensures data consistency and avoids duplication.
- Application Integrations: Integrating with existing applications allows seamless communication and data flow between the SD Deployment Service and your existing infrastructure. This improves efficiency and avoids manual data entry.
Challenges and Mitigation Strategies
Integration projects can face various challenges. Proactive planning and mitigation strategies can address these issues.
- Compatibility Issues: Differences in protocols or formats between the SD Deployment Service and existing systems can cause compatibility problems. Using standardized protocols and formats can mitigate these issues.
- Data Migration Challenges: Migrating data from existing systems to the SD Deployment Service can be complex. Careful planning and data mapping can help address these issues.
- Security Concerns: Ensuring secure access to data and resources during integration is crucial. Employing robust security measures and implementing strong access controls is vital.
Impact on Existing Workflows
Integrating the SD Deployment Service may impact existing workflows. These impacts should be anticipated and addressed proactively.
- Process Adjustments: Users may need to adjust their workflows to utilize the new service. Providing clear documentation and training materials can help facilitate these adjustments.
- Efficiency Gains: The new service may streamline some processes, resulting in increased efficiency and reduced manual effort.
Operational Management and Monitoring
Successfully deploying Prisma Access Enterprise requires meticulous operational management and monitoring. This phase ensures the service’s continued stability, performance, and security. Effective monitoring enables proactive issue resolution and optimized resource utilization. Robust procedures and tools are crucial for maintaining a high level of service quality.
Monitoring Procedures
Monitoring the SD Deployment Service for Prisma Access Enterprise demands a comprehensive strategy. This involves tracking key metrics, identifying potential issues early, and establishing proactive responses. Regular monitoring and reporting are essential to maintaining the service’s reliability.
- Real-time Monitoring Tools: Employing dedicated monitoring tools is essential for real-time visibility into the service’s performance. These tools track key metrics such as connection latency, user login rates, and API response times. Real-time monitoring provides immediate alerts for anomalies, enabling swift intervention and preventing service disruptions.
- Scheduled Reporting: Generate reports on a regular basis (e.g., daily, weekly, monthly) to track performance trends. This allows for analysis of long-term patterns and proactive adjustments to the service. Reports should detail metrics like user activity, access patterns, and security events.
- Alerting System: Configure a robust alerting system that triggers notifications for critical events, such as excessive latency, high error rates, or security breaches. The system should provide specific details about the issue, its impact, and its location within the deployment, facilitating swift troubleshooting.
Dashboard Design
A well-designed dashboard is crucial for effective monitoring. It should present key metrics in a clear and concise format, facilitating rapid identification of potential problems. Visualizations are key to understanding trends and anomalies.
- Key Metrics Display: The dashboard should prominently display critical metrics such as connection success rates, error rates, latency, and resource utilization. This ensures quick identification of performance bottlenecks or security issues.
- Visualization Tools: Utilize interactive charts and graphs to display data trends and patterns. This helps identify anomalies and potential issues before they escalate into major problems. For example, a graph illustrating user login times over a period can highlight unusual spikes or drops in performance.
- Filtering and Drill-Down Capabilities: Provide filtering options to focus on specific segments of the deployment (e.g., particular applications, user groups, or geographical locations). This allows for targeted analysis and identification of issues within specific areas of the service.
Proactive Issue Resolution
A proactive approach to issue resolution involves implementing preventative measures and utilizing automation. This reduces the impact of potential disruptions and ensures continuous service availability.
So, I’ve been diving deep into SD deployment services for Enhanced Plus Prisma Access Enterprise lately, and it’s been a wild ride. While I’m still figuring out the best way to optimize this for my team, I stumbled upon some really interesting new trailers, like Fifty Shades Darker, Tupac biopics, and Disney releases, here. It’s definitely a distraction, but ultimately, I need to get back to the core of the SD deployment service for Prisma Access Enterprise and how to make it work seamlessly for us.
- Automated Remediation Scripts: Develop and implement automated scripts to address common issues automatically. This streamlines the troubleshooting process and minimizes manual intervention. For example, scripts can automatically scale resources or adjust configurations based on detected anomalies.
- Predictive Modeling: Implement predictive models to anticipate potential issues based on historical data and trends. This enables proactive measures to be taken before problems arise. For example, if user login attempts suddenly spike, a predictive model can flag the event and suggest adjustments to capacity to avoid a service disruption.
- Regular Security Audits: Schedule routine security audits to identify and address potential vulnerabilities in the system. This helps to prevent security breaches and maintain the integrity of the deployment. Regular security audits, using tools like vulnerability scanners, are crucial to identifying and addressing potential security issues before they are exploited.
Troubleshooting Guide
A comprehensive troubleshooting guide is essential for addressing operational problems. This guide should cover common issues, their causes, and solutions. It acts as a valuable resource for both administrators and support teams.
- Common Operational Problems: Document common issues like connection timeouts, high error rates, and performance degradation. The guide should also detail the causes of these issues (e.g., network problems, insufficient resources, or configuration errors).
- Step-by-Step Solutions: Provide detailed step-by-step procedures for resolving each problem. This should include instructions on how to diagnose the issue, collect relevant logs, and implement the appropriate solution.
- Example Scenarios: Include example scenarios to illustrate the application of troubleshooting procedures. This makes the guide more practical and user-friendly.
Performance Optimization
Optimizing the operational performance of the deployment requires continuous monitoring and adjustments. Strategies to improve performance and ensure scalability should be part of the ongoing maintenance process.
- Resource Optimization: Regularly review and adjust resource allocation based on demand and performance metrics. This ensures that the system has the necessary resources to handle expected loads without compromising performance.
- Code Optimization: Review and optimize any custom code or scripts that are part of the deployment. This helps to improve performance and reduce resource consumption. Efficient code reduces latency and increases overall system responsiveness.
- Load Balancing Techniques: Implement load balancing strategies to distribute traffic evenly across the deployment. This prevents any single point of failure and ensures that the system can handle peak loads without significant performance degradation.
Cost Analysis and ROI
Deploying a secure access service like SD Deployment Service for Prisma Access Enterprise requires careful consideration of both initial and ongoing costs. Understanding the potential return on investment (ROI) is crucial for justifying the investment and ensuring the service aligns with business objectives. A thorough cost analysis, comparing different deployment options, and methods for measuring ROI are key elements for a successful implementation.A comprehensive cost analysis considers direct and indirect costs associated with the SD Deployment Service.
Direct costs include software licenses, hardware upgrades (if needed), and professional services for deployment and configuration. Indirect costs encompass training personnel, potential downtime during deployment, and ongoing maintenance and support. Evaluating these costs against the anticipated benefits is essential for achieving a positive ROI.
Deployment Option Cost Comparison
Different deployment options influence the total cost. A cloud-based deployment often has lower upfront costs but potentially higher ongoing costs due to cloud service charges. A hybrid approach, combining cloud and on-premises infrastructure, can provide a balance but may involve more complex management. On-premises deployments, while potentially having higher upfront costs, may offer greater control and security, and lower ongoing cloud service fees.
Analyzing the total cost of ownership (TCO) for each option is critical.
- Cloud-based deployment often has lower initial capital expenditures, but ongoing costs include cloud service charges, potentially exceeding on-premises solutions if not managed efficiently. For example, an organization might spend less on servers but more on cloud compute, storage, and networking services. This highlights the need for careful planning and cost optimization strategies for cloud deployments.
- Hybrid deployments balance the benefits of cloud and on-premises solutions, offering flexibility and control. This can lead to more complex management but may provide cost savings in certain scenarios. However, the cost of managing two different environments should be carefully considered. For instance, a company might leverage cloud services for non-critical applications while maintaining sensitive data on-premises.
- On-premises deployments usually involve higher upfront capital expenditures for hardware and software licenses. However, ongoing costs are often lower, depending on the infrastructure maintenance and support contracts. A traditional bank, for example, might choose on-premises solutions for the security and control they provide, even if the upfront investment is larger.
Measuring ROI
Quantifying the ROI of the SD Deployment Service is vital for demonstrating its value. The ROI can be calculated by comparing the total costs of the service with the benefits realized. Quantifiable benefits include reduced security breaches, improved operational efficiency, and increased user productivity.
- Reduced security breaches can be measured by calculating the cost of past breaches and estimating the reduction in future breaches through the SD Deployment Service. For example, a company could use data from similar organizations to project cost savings from a reduced breach rate.
- Improved operational efficiency can be measured by tracking metrics such as reduced support tickets, faster response times, and improved user adoption. Data from previous systems can help compare operational efficiency gains.
- Increased user productivity can be measured by tracking metrics such as reduced downtime, improved access times, and higher user satisfaction. Using productivity benchmarks from similar companies is one way to quantify this gain.
Factors Affecting Cost and ROI
Several factors influence the cost and ROI of deploying the SD Deployment Service. These factors include the scale of the deployment, the complexity of the existing infrastructure, the security and compliance requirements, and the level of support and maintenance needed.
- Scale of deployment directly affects the cost of licenses, hardware, and personnel. A large-scale deployment requires more resources and expertise, leading to increased costs.
- Complexity of existing infrastructure influences the deployment complexity and potential integration challenges. A complex infrastructure may require more time and resources for deployment, increasing costs.
- Security and compliance requirements can add significant costs through specialized security tools, personnel training, and compliance audits.
- Level of support and maintenance required impacts ongoing costs, including personnel time and contracted support services.
Wrap-Up

In conclusion, SD deployment service for enhanced plus for Prisma Access Enterprise provides a comprehensive solution for securing and managing access in modern enterprises. By understanding its deployment strategies, security considerations, and integration with existing infrastructure, organizations can effectively leverage its capabilities to enhance their security posture. The service offers a clear path to maximizing the benefits of Prisma Access Enterprise while addressing specific security concerns.
This comprehensive guide provides a practical roadmap for implementing this solution within your organization.