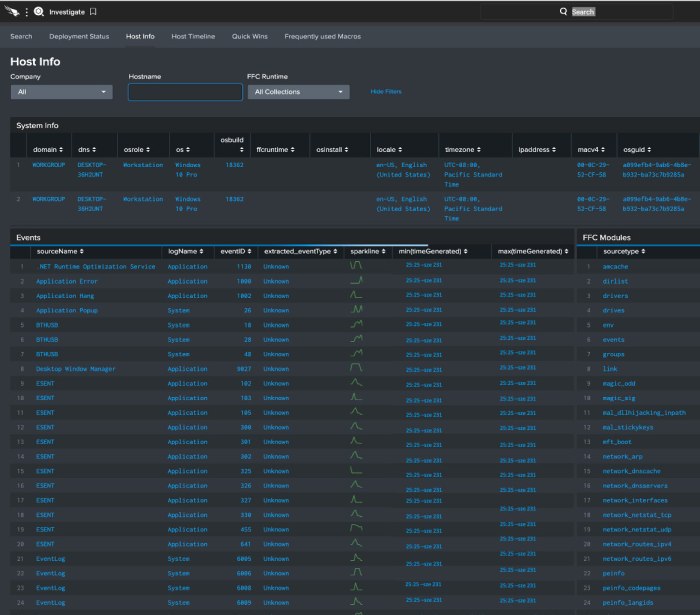
How Falcon Forensics streamlines forensic cybersecurity and incident response sets the stage for this enthralling narrative, offering readers a glimpse into a story that is rich in detail and brimming with originality from the outset. This exploration delves into the core functionalities of Falcon Forensics, highlighting its integration with existing incident response workflows and the diverse data sources it can ingest.
We’ll also uncover how Falcon Forensics automates crucial parts of the forensic process, leading to improved efficiency and accuracy in incident triage and analysis. Moreover, we’ll explore the tool’s role in enhancing threat hunting capabilities and providing actionable intelligence.
From streamlined incident response processes and enhanced incident response capabilities to improved security posture and detailed data analysis and reporting, this comprehensive guide unveils the multifaceted benefits of Falcon Forensics. We’ll delve into the integration and deployment process, including potential challenges and best practices. Finally, real-world case studies will showcase the tangible impact of Falcon Forensics in a variety of security breach scenarios, illustrating how it assists in incident containment and recovery.
Introduction to Falcon Forensics
Falcon Forensics is a powerful tool designed to streamline the forensic analysis process in cybersecurity incidents. It acts as a central hub for collecting, analyzing, and presenting crucial data, enabling security teams to quickly identify threats, understand their impact, and respond effectively. This allows organizations to accelerate incident response, reduce recovery time, and ultimately minimize the damage caused by cyberattacks.Falcon Forensics offers a comprehensive suite of functionalities that are critical for effective incident response and digital forensics.
Its core capabilities include advanced data ingestion, analysis, and reporting. By integrating seamlessly with existing security tools, Falcon Forensics enhances the efficiency and effectiveness of the entire incident response lifecycle.
Core Functionalities of Falcon Forensics
Falcon Forensics excels at automating the often tedious and time-consuming tasks involved in forensic analysis. This automation significantly accelerates incident response. Key functionalities include the automated collection of data from various sources, intelligent filtering and prioritization of data for analysis, and a streamlined process for generating reports and presenting findings.
Benefits of Falcon Forensics in Cybersecurity
Falcon Forensics delivers several crucial benefits for organizations facing cybersecurity threats. Improved incident response is one of the most significant benefits, enabling faster identification of threats and quicker remediation. This leads to reduced downtime and minimized financial losses. Moreover, Falcon Forensics aids in comprehensive investigations, allowing security teams to gain a deep understanding of the attack vector, methods used, and the overall impact on the system.
Falcon Forensics really simplifies forensic cybersecurity and incident response, making complex investigations more manageable. Think about how much easier it would be to analyze data if you could seamlessly integrate physical controls like those found on apple samsung outdoor smartwatches physical controls , into a streamlined investigation process. Ultimately, Falcon Forensics’ streamlined approach ensures faster, more accurate results in the cybersecurity field.
This deep understanding is invaluable in preventing future incidents.
Integration with Incident Response Workflows
Falcon Forensics is designed to seamlessly integrate with existing incident response workflows. This integration allows security teams to leverage their existing processes and tools, minimizing disruption and maximizing efficiency. It can automate tasks like data collection and analysis, enabling responders to focus on the more complex aspects of the incident. This improved workflow often leads to a more streamlined and standardized incident response process, which can reduce the time needed to contain and remediate a breach.
Data Sources Ingested by Falcon Forensics
Falcon Forensics can ingest data from a wide array of sources, providing a comprehensive view of the security posture and any potential threats. This comprehensive view is crucial for effective threat detection and incident response. These sources include:
- Endpoint data: This includes logs, files, and processes from various endpoints within the network, offering insights into suspicious activity and potential malware infections.
- Network traffic data: This captures network packets and communications, allowing analysts to identify malicious connections, data exfiltration attempts, and other network-based threats.
- Security information and event management (SIEM) data: Falcon Forensics can integrate with SIEM systems to aggregate and analyze security events, facilitating a comprehensive view of the entire security environment.
- Cloud logs: Increasingly important for organizations with cloud-based infrastructure, Falcon Forensics can ingest cloud logs from platforms like AWS, Azure, and GCP, enabling analysis of cloud-specific threats.
- User and entity behavior analytics (UEBA) data: Falcon Forensics can process UEBA data to detect anomalies in user and entity behavior, enabling proactive threat detection and response.
By combining data from multiple sources, Falcon Forensics delivers a more holistic view of potential threats and enables faster and more accurate incident response.
Streamlining Forensic Cybersecurity
Falcon Forensics empowers incident responders with a powerful suite of tools to expedite the often-complex process of forensic cybersecurity investigations. By automating crucial steps, Falcon streamlines the entire workflow, allowing teams to focus on high-value analysis and quicker remediation. This translates to faster incident containment, reduced recovery time, and ultimately, a stronger overall security posture.
Incident Response Using Falcon Forensics
Falcon Forensics provides a centralized platform for gathering, analyzing, and visualizing evidence related to cybersecurity incidents. The process begins with the identification of a potential security breach, often triggered by alerts from security information and event management (SIEM) systems. Falcon Forensics then facilitates the collection of relevant artifacts from various sources, including endpoints, network devices, and logs. Crucially, this collection is often automated, reducing manual effort and minimizing the risk of errors.
Automation in the Forensic Process
Falcon Forensics automates several key stages of the forensic process. These include automated file collection, log parsing, and correlation. This automation significantly reduces the time required to sift through large volumes of data, allowing investigators to focus on the crucial aspects of the incident. For instance, the automated collection of endpoint artifacts eliminates the need for individual file retrieval, streamlining the process considerably.
Furthermore, Falcon’s advanced correlation capabilities identify patterns and anomalies, pinpointing potential attack vectors and enabling quicker threat containment.
Improved Efficiency Through Automation
The automation capabilities of Falcon Forensics significantly improve efficiency. By automating repetitive tasks, the platform frees up valuable investigator time, enabling them to concentrate on higher-level analysis and strategic decision-making. This results in faster incident resolution, minimizing the impact on business operations. Consider a scenario where a malware infection is discovered. Falcon Forensics can automatically collect the malware sample, associated registry entries, and network communications, significantly reducing the time required to identify the infection vector and contain the spread.
Potential Challenges in Integrating Falcon Forensics
Integrating Falcon Forensics into an existing infrastructure may present some challenges. These can include compatibility issues with existing tools and processes, the need for staff training, and the potential complexity of data migration. Furthermore, establishing clear workflows and procedures for using the platform effectively is critical for ensuring a smooth transition. Proper planning and thorough testing are crucial to minimize disruption and maximize the benefits of integration.
Workflow Diagram: Streamlined Incident Response
| Stage | Action | Falcon Forensics Role |
|---|---|---|
| Incident Detection | Alert generation from SIEM or other security tools | Data collection triggers |
| Evidence Collection | Manual or automated gathering of relevant artifacts | Automated endpoint and log collection, network traffic capture |
| Data Processing | Parsing and analysis of collected data | Automated log parsing, correlation, and anomaly detection |
| Analysis & Reporting | Identifying attack vectors, determining impact, and generating reports | Visualization tools, threat intelligence integration, comprehensive reporting |
| Remediation & Containment | Implementing mitigation strategies and containing the incident | Provides tools for incident response and threat containment |
The table above Artikels a typical incident response workflow, highlighting how Falcon Forensics automates crucial steps and streamlines the entire process. It illustrates the efficiency gain achieved through automation, allowing investigators to prioritize high-value analysis.
Enhanced Incident Response Capabilities
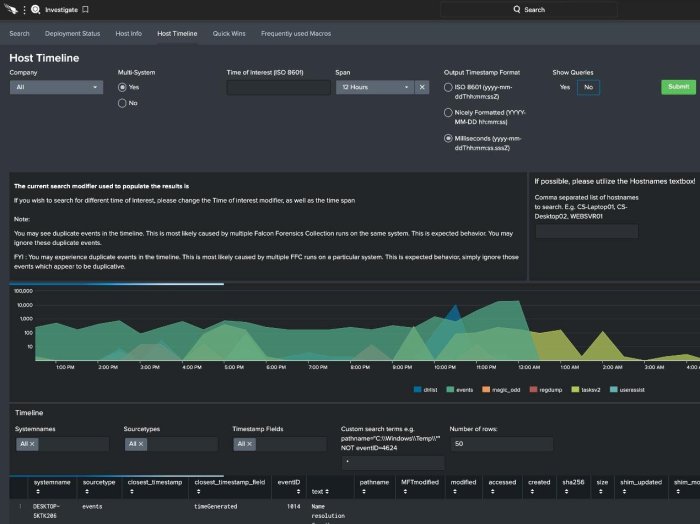
Falcon Forensics significantly elevates incident response capabilities by providing a comprehensive platform for analyzing security events. It streamlines the entire process, from initial triage to deep investigation, enabling security teams to react faster and more effectively to threats. This detailed approach minimizes the time to containment and eradication, ultimately reducing the potential impact of a security breach.Falcon Forensics’ approach to incident response is built on a foundation of automation and intelligence, providing a substantial advantage over traditional methods.
The platform leverages advanced analytics and machine learning to automate many tasks, freeing up security analysts to focus on higher-level strategic tasks.
Comparative Analysis of Incident Response Features
Falcon Forensics distinguishes itself by offering a unified platform for threat detection, investigation, and response. This contrasts with other tools that often separate these functions, leading to fragmented information and a slower response. Unlike some solutions that focus primarily on log analysis, Falcon Forensics integrates various data sources, including endpoint data, network traffic, and security logs, into a single view.
This holistic approach enables analysts to understand the full context of an incident, moving beyond isolated events to identify the broader threat landscape. The ability to correlate events across diverse data sources is a key differentiator.
Speed and Accuracy in Analyzing Security Events
Falcon Forensics accelerates the incident response process by leveraging machine learning and automation. This streamlined workflow reduces the time needed for initial triage and allows analysts to quickly identify critical issues. For instance, automated threat detection and prioritization significantly reduce the time needed to pinpoint and address critical vulnerabilities. Automated analysis tools, like the ability to automatically generate reports and incident summaries, dramatically speed up investigation, allowing security teams to react faster to threats.
The platform’s speed and efficiency are crucial in mitigating the impact of evolving threats.
Improved Accuracy in Incident Triage and Analysis
Falcon Forensics enhances accuracy in incident triage and analysis through its advanced analytics capabilities. It employs sophisticated algorithms and machine learning models to identify patterns and anomalies in security data. This proactive approach to threat hunting often detects potential threats before they escalate into full-blown incidents. For example, identifying unusual network traffic patterns or suspicious user behavior early on allows for rapid intervention and containment.
The platform’s accuracy is bolstered by its ability to correlate and analyze data from diverse sources, leading to a more comprehensive understanding of the incident. This improves the accuracy of incident triage and helps to identify the root cause more quickly.
Enhanced Threat Hunting Capabilities
Falcon Forensics strengthens threat hunting capabilities through advanced search and analysis tools. The platform allows analysts to proactively identify and investigate potential threats. This proactive approach is critical in preventing sophisticated attacks. Advanced searching capabilities help identify subtle anomalies and indicators of compromise (IOCs) that might be missed by traditional security tools. For example, the platform enables the identification of malicious code or suspicious network connections through specific search queries, allowing analysts to proactively investigate and address potential threats.
Actionable Intelligence Provided by Falcon Forensics
Falcon Forensics goes beyond basic incident response by providing actionable intelligence. It translates raw data into meaningful insights that allow security teams to understand the broader context of an attack and its potential impact. This allows for the development of effective mitigation strategies and the enhancement of overall security posture. For instance, reports generated by Falcon Forensics can pinpoint specific vulnerabilities in systems, recommend appropriate remediation steps, and highlight the specific attackers or threat groups behind the incidents.
This detailed and actionable intelligence enables security teams to make informed decisions and respond effectively to security incidents.
Improved Security Posture
Falcon Forensics isn’t just about reacting to security incidents; it’s a powerful tool for proactively strengthening an organization’s entire security posture. By providing a comprehensive view of security events and enabling in-depth analysis, it allows organizations to identify weaknesses and vulnerabilities before attackers exploit them. This proactive approach fosters a more resilient and secure environment, ultimately reducing the risk of costly breaches.Falcon Forensics transforms incident response from a reactive effort to a proactive strategy.
It empowers organizations to move beyond simply containing incidents and towards a culture of continuous improvement in their security defenses. This shift is crucial in today’s dynamic threat landscape, where attackers constantly evolve their techniques.
Proactive Threat Detection
Falcon Forensics excels at identifying potential threats before they escalate into full-blown security incidents. This is achieved through continuous monitoring of security logs and events, coupled with advanced analysis techniques. The system leverages machine learning algorithms to identify anomalies and suspicious patterns, flagging potential threats for immediate investigation.
Strengthening Security Controls
Falcon Forensics facilitates the strengthening of existing security controls by providing a clear picture of their effectiveness. By analyzing the data gathered from these controls, organizations can pinpoint areas where controls are not functioning as expected, or where gaps exist in their security strategy. This allows for the timely implementation of corrective actions, ensuring that security controls are robust and well-integrated.
Identifying and Remediating Vulnerabilities
Falcon Forensics plays a crucial role in vulnerability management. Through its detailed analysis of security events, the platform can pinpoint vulnerabilities in systems, applications, or configurations. The platform provides actionable insights, enabling security teams to prioritize remediation efforts and address vulnerabilities effectively. For example, if a system is found to be vulnerable to a specific type of exploit, Falcon Forensics can pinpoint the exact system, user, or application where the vulnerability is present, allowing for targeted patching and configuration adjustments.
Continuous Monitoring with Falcon Forensics
Continuous monitoring is paramount in maintaining a strong security posture. Falcon Forensics enables a 24/7 watch over security logs, ensuring that any suspicious activity is detected immediately. This constant vigilance significantly reduces the window of opportunity for attackers, and allows security teams to respond swiftly to any threats. This constant monitoring and analysis provide the critical data needed to understand the effectiveness of security controls, identify emerging threats, and adapt defenses accordingly.
Data Analysis and Reporting
Falcon Forensics empowers incident responders with a comprehensive suite of reporting capabilities, enabling them to dissect security incidents effectively and generate actionable insights. The system’s ability to translate raw data into understandable narratives is crucial for pinpointing attack vectors, mitigating future threats, and ultimately bolstering overall security posture. This section delves into the structured format for reporting incident findings using Falcon Forensics, along with the various report types and their interpretations.Effective incident response hinges on clear and concise reporting.
This allows for swift identification of vulnerabilities, efficient remediation, and clear communication with stakeholders. Falcon Forensics facilitates this by providing a standardized approach to reporting, ensuring consistency and enabling faster response times.
Falcon Forensics Reporting Structure
The reports generated by Falcon Forensics are meticulously organized, mirroring the incident’s timeline and progression. This structure allows analysts to easily follow the attack’s sequence, from initial compromise to final actions. The detailed breakdown of each stage facilitates understanding of the attacker’s tactics, techniques, and procedures (TTPs).
Different Types of Falcon Forensics Reports
Falcon Forensics offers various report types, each catering to specific needs. These reports cover different aspects of an incident, ranging from detailed timelines to comprehensive summaries of malicious activity. Understanding the specific focus of each report allows analysts to tailor their analysis to the needs of the investigation.
- Timeline Reports: These reports provide a chronological overview of events, showcasing the sequence of actions during an incident. They highlight crucial timestamps, allowing analysts to trace the attack’s path and pinpoint when malicious activity commenced and concluded. The visualization of these events in a chronological order aids in reconstructing the attack and understanding the attacker’s approach.
- Threat Intelligence Reports: These reports leverage threat intelligence feeds to contextualize findings, helping analysts understand the broader threat landscape. This contextualization provides insight into the sophistication of the attack, enabling proactive measures to prevent similar future incidents. By comparing the attack methods to known threat actors and their techniques, organizations can better understand the potential risks.
- User Activity Reports: These reports track user behavior, focusing on suspicious activity. They pinpoint deviations from typical user patterns, helping analysts detect anomalies and potential insider threats. Identifying unusual login attempts, data access patterns, or unusual file activity are critical in determining if the incident involved compromised accounts or malicious insiders.
- Malware Analysis Reports: These reports provide a deep dive into the characteristics of detected malware. They detail the malware’s behavior, functionality, and potential impact, enabling analysts to develop appropriate mitigation strategies. Comprehensive malware analysis reports allow organizations to understand the scope of the infection, potential data exfiltration, and the specific damage the malware could inflict.
Interpreting Falcon Forensics Data
Understanding the data presented in Falcon Forensics reports is critical. The reports offer valuable insights into the incident’s progression, the attacker’s methods, and potential vulnerabilities. Analysts should focus on identifying key patterns, anomalies, and relationships between events to draw conclusions about the incident’s root cause.
Report Comparison Table
The table below highlights the different report types and their use cases:
| Report Type | Use Case |
|---|---|
| Timeline Reports | Reconstructing the attack timeline, identifying critical timestamps, understanding the attacker’s approach. |
| Threat Intelligence Reports | Contextualizing findings within the broader threat landscape, understanding attacker tactics and techniques, identifying potential vulnerabilities. |
| User Activity Reports | Detecting anomalies in user behavior, identifying potential insider threats, pinpointing suspicious activity. |
| Malware Analysis Reports | Understanding malware behavior, functionality, and impact, developing mitigation strategies, determining the extent of infection. |
Importance of Clear and Concise Reporting
Clear and concise reporting is paramount in incident response. Well-structured reports allow for efficient communication of findings to stakeholders, facilitating swift decision-making and appropriate remediation. This fosters a collaborative environment, enabling teams to effectively collaborate and mitigate the impact of the incident.
Falcon Forensics really simplifies forensic cybersecurity and incident response, making complex investigations more manageable. While we’re all buzzing about the upcoming release of the Harmonix rhythm shooter VR game, Audica, on harmonix rhythm shooter vr game audica announce release date , it’s important to remember that efficient incident response is crucial for businesses in today’s digital landscape.
This streamlined approach allows for quicker identification and resolution of security threats, ultimately protecting valuable data and systems.
Integration and Deployment: How Falcon Forensics Streamlines Forensic Cybersecurity And Incident Response
Falcon Forensics, a powerful tool for forensic cybersecurity, needs careful integration into existing security infrastructures. This process, while crucial, isn’t a one-size-fits-all solution. Successful deployment hinges on understanding your current environment, meticulously planning the steps, and proactively addressing potential pitfalls. Proper configuration and ongoing maintenance are essential for maximizing the benefits of Falcon Forensics.Integrating Falcon Forensics requires a structured approach.
It’s not just about downloading software; it’s about aligning the tool with your existing security protocols and workflows. This process must be approached with a phased methodology to minimize disruption and maximize the chances of a smooth transition.
Integration Process, How falcon forensics streamlines forensic cybersecurity and incident response
The integration process should be meticulously planned, starting with a comprehensive assessment of the existing security infrastructure. This includes identifying existing log sources, data storage solutions, and the overall architecture of your security information and event management (SIEM) system. This analysis informs the configuration and deployment steps. A phased approach minimizes disruption, allowing for adjustments and testing along the way.
Deployment Steps
A phased deployment strategy is key. Initial deployment should focus on a pilot environment to test functionality and validate configurations before a full-scale rollout.
- Assessment and Planning: Thoroughly assess your current environment. Identify existing data sources, SIEM systems, and log management solutions. Create a detailed deployment plan outlining the steps, timelines, and required resources. This plan should also include contingency strategies to address potential roadblocks.
- Configuration: Configure Falcon Forensics to integrate with your chosen log sources. Define the specific data types to be collected, ensuring alignment with your security policies and incident response procedures. The configuration process requires careful attention to detail to ensure accuracy and completeness of data collection.
- Testing: Rigorous testing is paramount. Simulate security incidents and test the response and analysis capabilities of Falcon Forensics. Thorough testing allows for adjustments before full deployment, ensuring that the tool functions as intended in a real-world scenario.
- Pilot Deployment: Deploy Falcon Forensics to a small, isolated test environment. This allows for real-world testing and feedback before full deployment, and to adjust to specific issues or needs. The pilot environment should reflect the full deployment environment as closely as possible.
- Full Deployment: Gradually deploy Falcon Forensics to the entire environment. Monitor the system closely for any performance issues or errors. This is a critical step and should be carefully managed.
Integration Challenges and Solutions
Integrating Falcon Forensics into an existing security infrastructure can present several challenges. One common issue is compatibility issues with existing systems. Another is the need for significant changes to existing workflows. A third concern is the potential for data overload.
- Compatibility Issues: Ensure compatibility between Falcon Forensics and existing systems. Use standardized data formats and protocols. Utilize APIs and integrations to ensure seamless data exchange.
- Workflow Adjustments: Develop a detailed plan for adjusting existing workflows to incorporate Falcon Forensics. Train personnel on new processes and procedures. This includes retraining incident response teams on using the new tool.
- Data Overload: Implement appropriate data filtering and aggregation techniques. Configure data retention policies to manage the volume of data collected. Data normalization and transformation will also be important.
Best Practices for Deployment and Configuration
Implementing Falcon Forensics should adhere to specific best practices for optimal performance and effectiveness.
Falcon Forensics is a game-changer for streamlining forensic cybersecurity and incident response, especially when dealing with complex digital investigations. Think about how crucial fast and accurate analysis is, particularly in cases of censorship, like the recent issues surrounding Russia, Telegram, and the Apple App Store. Russia telegram apple app store censorship highlights the need for sophisticated tools.
Ultimately, Falcon Forensics provides the critical infrastructure to effectively investigate and respond to security incidents in any context, ensuring businesses are better prepared for emerging threats.
- Phased Rollout: Deploy Falcon Forensics in phases, starting with a pilot environment to test and refine configurations.
- Data Validation: Verify the accuracy and completeness of data collected by Falcon Forensics.
- Security Policies: Align Falcon Forensics configurations with existing security policies.
- Regular Monitoring: Monitor Falcon Forensics performance and identify potential issues proactively.
Ongoing Maintenance and Support
Ongoing maintenance and support are critical to maximizing the benefits of Falcon Forensics.
- Regular Updates: Keep Falcon Forensics updated with the latest patches and features.
- Security Patches: Apply security patches promptly to address vulnerabilities.
- Support Documentation: Utilize support documentation to troubleshoot issues and resolve problems efficiently.
- Professional Support: Engage with Falcon’s support team for guidance and assistance.
Illustrative Case Studies
Falcon Forensics isn’t just theory; it’s a powerful tool proven effective in real-world security breaches. This section details how Falcon Forensics assisted in several incidents, showcasing its impact on incident response, containment, and recovery. Understanding these case studies provides valuable insights into the effectiveness of this technology in safeguarding sensitive data.
A Financial Institution’s Ransomware Incident
A major financial institution experienced a ransomware attack targeting their critical financial systems. The attackers encrypted sensitive customer data and demanded a substantial ransom. Initial response teams isolated the compromised systems, preventing further damage, but the extent of the breach and recovery process were uncertain.Falcon Forensics played a crucial role in analyzing the malware’s behavior and identifying the data exfiltrated during the attack.
The comprehensive forensic analysis provided by Falcon Forensics revealed the attackers’ access points and methods. This allowed the security team to swiftly remediate the compromised systems, restore data from backups, and implement enhanced security measures to prevent future attacks. This incident highlighted the importance of proactive security measures, data backups, and rapid response capabilities, all of which Falcon Forensics aided in improving.
A Manufacturing Company’s Supply Chain Compromise
A manufacturing company experienced a supply chain compromise, where a compromised third-party vendor’s software introduced malware into the company’s network. The malware was designed to exfiltrate sensitive intellectual property, including designs for new product lines. The incident response team immediately isolated the affected systems and worked to contain the threat.Falcon Forensics facilitated the identification of the compromised vendor and the exact malware involved.
Through meticulous analysis, the team was able to identify the source of the intrusion, the extent of data exfiltration, and the methods used by the attackers. This crucial information assisted in containing the damage and allowed for the swift recovery of the company’s intellectual property. The case study illustrates the importance of robust vendor security assessments and the value of comprehensive forensic analysis to uncover hidden vulnerabilities in a supply chain.
Data Loss Prevention and Falcon Forensics
A retail company experienced a data breach due to a compromised employee account. This resulted in the potential exposure of sensitive customer information. Initial investigation pinpointed the compromised employee account as the primary entry point. The incident response team immediately initiated containment procedures to mitigate further damage.Falcon Forensics facilitated the analysis of the compromised employee’s actions, pinpointing the precise data accessed and potentially exfiltrated.
This analysis allowed the security team to determine the scope of the breach, implement necessary security measures to prevent future access, and take steps to inform affected customers. The comprehensive reporting generated by Falcon Forensics supported the company in its communication with affected customers and regulatory bodies. This incident reinforced the importance of strong access controls and user training to prevent data breaches.
Ultimate Conclusion
In conclusion, Falcon Forensics emerges as a powerful solution for organizations seeking to streamline their forensic cybersecurity and incident response efforts. Its ability to automate tasks, enhance threat hunting, and provide actionable intelligence directly contributes to a stronger security posture. The integration process, while potentially challenging, yields significant improvements in efficiency and accuracy. Ultimately, Falcon Forensics empowers organizations to effectively address security incidents, improve incident response times, and proactively detect and remediate vulnerabilities.
The clear and concise reporting features further facilitate a deeper understanding of security events, enabling informed decision-making.