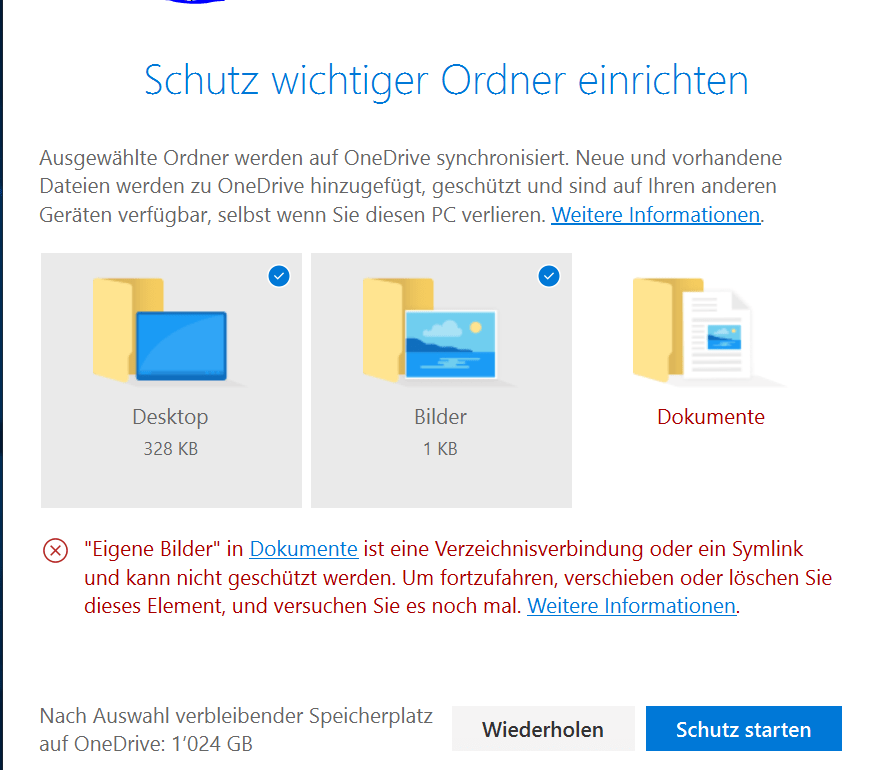
Microsoft OneDrive folder protection feature offers a robust way to safeguard sensitive files and folders within your OneDrive account. This feature provides various protection mechanisms, including password protection and granular permissions, making it an invaluable tool for enhanced data security. Understanding how to utilize this feature effectively is crucial for anyone managing files on OneDrive, and this article explores its capabilities from various perspectives.
This comprehensive guide delves into the intricacies of OneDrive folder protection, covering everything from basic setup to advanced security configurations. We’ll examine the underlying security principles, discuss user experience, and explore how folder protection integrates with other OneDrive features. The article also addresses troubleshooting common issues and provides best practices for optimal security.
Overview of OneDrive Folder Protection
OneDrive Folder Protection is a crucial feature designed to safeguard sensitive files and folders stored within the OneDrive cloud service. It offers multiple layers of security, ensuring that only authorized users can access and modify protected content. This robust approach is vital in today’s increasingly digital world, where data breaches and unauthorized access are serious concerns.The core function of this feature is to restrict access to specific folders, effectively creating a secure perimeter around sensitive information.
This protection extends beyond simple password safeguards, encompassing granular permission controls. This detailed control allows administrators to tailor access rights to specific users and groups, effectively mitigating the risks associated with accidental or malicious data leakage.
Microsoft OneDrive’s folder protection feature is a game-changer for keeping your files safe. It’s a great way to add an extra layer of security, especially if you’re concerned about unauthorized access. Speaking of security, did you know that the BBC is bringing back shortwave radio broadcasts in Russia? This move is a clever way to get around potential internet censorship, which is a testament to the importance of diverse communication channels.
This renewed focus on alternative communication methods makes OneDrive’s protection features even more crucial for safeguarding sensitive information.
Protection Mechanisms
Various security mechanisms are employed to bolster the protection of sensitive data within OneDrive folders. These mechanisms are layered to provide a multi-faceted approach to safeguarding information.
- Password Protection: This mechanism requires a unique password to access the protected folder. This simple yet effective approach is suitable for individual users who need to safeguard their personal documents or sensitive projects from unauthorized access. A strong password, combined with a complex password policy, can significantly deter unauthorized access attempts.
- Permissions: This advanced mechanism allows administrators to grant specific permissions to different users or groups. This granular control empowers administrators to tailor access rights, allowing certain users to read documents while prohibiting them from editing. Permissions can be further segmented based on specific actions (e.g., read-only access, write access, delete access), further enhancing the level of control and security.
Scenarios for Use
OneDrive Folder Protection is highly applicable in diverse situations where sensitive information needs to be secured.
- Financial Records: Protecting financial records, including bank statements and tax documents, is crucial to prevent unauthorized access and potential financial fraud.
- Confidential Project Documents: In collaborative work environments, securing project documents that contain confidential information is essential. Restricting access to specific teams or individuals ensures that only those authorized can access the sensitive data.
- Healthcare Records: In healthcare settings, protecting patient records is paramount. By implementing OneDrive Folder Protection, organizations can ensure that patient information remains confidential and accessible only to authorized personnel.
Contribution to Data Security
The OneDrive Folder Protection feature significantly contributes to overall data security by:
- Restricting Unauthorized Access: By implementing password protection and granular permission controls, unauthorized individuals are effectively prevented from accessing sensitive data. This is a critical aspect of safeguarding data confidentiality.
- Maintaining Data Integrity: Controlling who can modify the protected folders prevents accidental or malicious alterations to the data, ensuring its integrity and reliability. This is particularly important in scenarios where data accuracy is critical, such as financial records.
- Complying with Regulations: Many industries, such as healthcare and finance, have stringent regulations regarding data security and privacy. OneDrive Folder Protection can be a critical component in complying with these regulations, demonstrating a commitment to safeguarding sensitive information.
Enabling and Disabling the Feature
The procedure for enabling and disabling OneDrive Folder Protection is typically handled through the OneDrive settings interface. Specific steps may vary depending on the version of OneDrive being used and the user’s administrative privileges. Consult the OneDrive documentation for detailed instructions on enabling and disabling the feature.
Security Features and Functionality
OneDrive Folder Protection significantly enhances the security posture of sensitive data stored within the cloud. Understanding the underlying security principles and access control mechanisms is crucial for leveraging this feature effectively. This section delves into the security features and functionality of OneDrive Folder Protection, comparing it to other OneDrive security measures and highlighting the implications of unauthorized access.
Underlying Security Principles
Folder Protection in OneDrive leverages a combination of encryption and access control to safeguard sensitive information. Data encryption ensures that even if a compromised folder is accessed, the contents remain unreadable without the proper decryption key. This encryption process is transparent to the user, ensuring seamless file management while maintaining high security standards. The system’s core principle involves encrypting the entire folder, not just individual files, which protects the entire folder’s contents from unauthorized access.
This holistic approach ensures comprehensive security.
Access Control Mechanisms
The access control mechanisms in Folder Protection are crucial to limiting access to only authorized personnel. This involves defining explicit permissions, granting specific levels of access to different users or groups. Users can be assigned different roles, each with varying degrees of permission. These roles define what actions a user can perform within the protected folder, such as viewing, editing, or sharing.
Fine-grained control over access allows administrators to tailor security measures to the specific needs of their organization or team.
Comparison with Other OneDrive Security Measures
OneDrive offers a range of security features beyond Folder Protection. These include file versioning, data loss prevention policies, and multi-factor authentication. While Folder Protection focuses on securing specific folders, other measures address broader security concerns across the entire OneDrive account. A comprehensive security strategy combines these features to provide layered protection. For example, while file versioning protects against accidental deletion, Folder Protection actively prevents unauthorized modification.
I’ve been really digging OneDrive’s new folder protection features. It’s a lifesaver for keeping sensitive files secure. To keep your phone handy while you’re on the go, checking out the best Samsung Galaxy S22 car mounts is a great way to ensure you have a secure way to access your phone while driving, so you can keep those important files protected.
Ultimately, these features make OneDrive a solid choice for important documents.
This combination of tools creates a robust security framework.
Permission Levels and Their Impact
Different permission levels within Folder Protection dictate the level of access granted to users. These levels can range from “view only” to “full control.” “View only” permissions limit users to viewing folder contents without any editing capabilities. “Full control” permissions grant complete control over the folder, including the ability to modify files and share the folder. The appropriate permission level assignment is critical to controlling access and preventing unauthorized changes to protected files.
Implications of Unauthorized Access
Unauthorized access to protected folders can lead to severe consequences. This includes potential data breaches, intellectual property theft, or financial losses. Furthermore, unauthorized access could violate legal regulations or company policies. To mitigate these risks, organizations must carefully consider and implement stringent access controls. For example, a healthcare company dealing with patient data faces serious consequences if protected folders are accessed without authorization.
Implementing appropriate access controls is critical for protecting sensitive data and maintaining trust with clients.
User Experience and Usability
OneDrive Folder Protection’s success hinges on its user-friendliness. A smooth and intuitive experience is crucial for adoption, especially in a security context where users might be hesitant to use new features. The design should prioritize simplicity and clarity, guiding users through the process with minimal friction.The key is to make folder protection as seamless as possible, so users don’t perceive it as an added burden.
Clear visual cues, helpful prompts, and easy-to-understand language are essential for a positive user experience. This approach will foster confidence in the security features and encourage widespread adoption.
User Interface Flow for Enabling Folder Protection
The process for enabling folder protection should be straightforward and easily accessible. A clear path within the OneDrive interface, ideally with prominent icons or labels, is essential. A simple wizard or a series of dialog boxes should guide the user through the process, providing options for granular control. Users should be able to specify which folder or folders they wish to protect, and select the desired level of protection.For example, the flow could begin with a user navigating to the folder they wish to protect.
Then, they would click on a new icon or a menu item labeled “Protect Folder.” This action would open a dialog box with a wizard or a series of prompts. The user would be asked to confirm the selection and choose from a list of protection options, like specifying access permissions. Finally, the user would confirm the changes and the folder would be protected.
Comparison of Ease of Use with Other Security Tools
| Feature | OneDrive Folder Protection | Other Security Tools (e.g., FileVault, EFS) ||—|—|—|| Initial Setup | Intuitive wizard-style interface; clear instructions | Often complex, requiring technical knowledge || Granular Control | Allows specification of permissions for different users | Can be limited or challenging to manage || User Management | Seamless integration with OneDrive user management | Separate tools or procedures || Integration with Existing Tools | Integrates with OneDrive’s existing structure | May not integrate seamlessly with existing systems |This table illustrates the potential ease of use of OneDrive Folder Protection compared to other security tools.
OneDrive aims to offer a simplified experience, allowing users to control security settings without extensive technical expertise.
User Experience When Managing Permissions Within Protected Folders
Managing permissions within protected folders should be intuitive and accessible. A clear interface should display the current access levels for each user or group. Users should be able to easily add, remove, or modify permissions, and understand the implications of each action. The interface should provide a visual representation of who has access to the folder and what permissions they hold.For instance, the user interface should present a list of users and groups with their corresponding permissions (e.g., read, write, modify).
Users should be able to edit this list directly. A clear explanation of the different permission levels should be provided to avoid ambiguity.
User Feedback on the Effectiveness of the Feature
Collecting user feedback is critical to understand the effectiveness of the feature. Regular surveys, feedback forms, and analysis of user behavior within protected folders can provide valuable insights. Monitoring usage patterns and addressing reported issues will help identify areas for improvement. This ongoing feedback loop will ensure the feature remains user-friendly and meets evolving security needs.
Organization of User Roles and Access Levels Within a Protected Folder
Users can be assigned specific roles with predefined access levels. These roles might include ‘Owner’, ‘Collaborator’, and ‘Viewer’. The Owner has full control, while Collaborators can perform specific actions (e.g., editing documents), and Viewers can only access the folder’s contents. The specific roles and permissions can be customized according to the organization’s needs.The user interface should clearly display the roles and permissions assigned to each user, making it easy to understand who has access to what within the protected folder.
This approach ensures that the appropriate level of access is granted to each user.
Integration with Other OneDrive Features
OneDrive Folder Protection isn’t an isolated feature; it seamlessly integrates with other OneDrive functionalities to provide a comprehensive security solution. This integration enhances the overall user experience by streamlining the process of securing sensitive files while maintaining the ease of use and accessibility of other OneDrive tools. This interconnectedness ensures a unified approach to managing and protecting files within the OneDrive ecosystem.
Sharing Compatibility
The Folder Protection feature works harmoniously with OneDrive’s sharing capabilities. Users can protect folders that are shared with others, safeguarding the content from unauthorized access and modification, even when shared. This approach provides a layered security model, enabling granular control over sensitive information shared within an organization or with individuals. The protection mechanism applies even when the folder is shared with external users.
Syncing Workflow
The syncing process remains largely unaffected by Folder Protection. Protected folders synchronize with other devices and computers just as standard OneDrive folders do. This means users can continue to access and work on their files without significant disruption. The protection mechanisms are implemented in the background, ensuring that the files remain secure during the synchronization process.
Protection on Shared Folders
Protecting a shared folder requires a deliberate action from the owner. The owner initiates the protection process, and this action automatically extends the protection to all users with access to the folder. This ensures consistent security across all access points.
Operating System and Device Compatibility
OneDrive Folder Protection is designed for cross-platform compatibility, working seamlessly across various operating systems and devices. This means users can protect their folders on Windows, macOS, iOS, and Android devices without encountering compatibility issues. This universal approach ensures consistent security across all user environments.
Effects on Syncing
The impact of folder protection on syncing is minimal. The security measures are implemented in a way that does not significantly impede the syncing process. Users will notice only minor delays, if any, during the initial synchronization after enabling protection. The added security measures are implemented without introducing noticeable overhead to the synchronization process. The synchronization process remains relatively seamless.
Best Practices and Recommendations
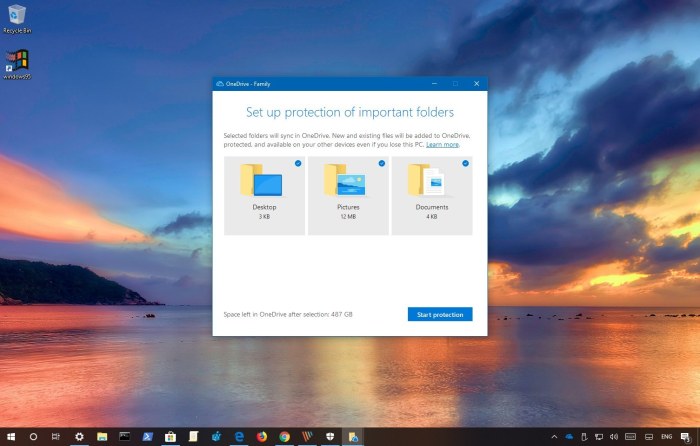
OneDrive Folder Protection offers a powerful layer of security, but its effectiveness hinges on proper configuration and management. This section details best practices to maximize the benefits of this feature and minimize potential risks. Understanding the nuances of permission management and potential pitfalls will ensure that your sensitive data remains secure.Effective implementation of OneDrive Folder Protection requires a proactive approach.
By following the recommendations Artikeld below, you can significantly enhance the security of your protected folders and ensure they remain inaccessible to unauthorized users.
Configuring Folder Protection Settings
Properly configuring folder protection settings is crucial for achieving the desired level of security. This involves carefully selecting the appropriate protection level and ensuring that the settings align with your specific security needs. Consider factors such as the sensitivity of the data, the frequency of access, and the potential for insider threats when determining the optimal configuration. For example, a folder containing financial data may require a higher level of protection than a folder with general project documents.
Managing Permissions Within Protected Folders
Managing permissions within protected folders is essential to control access to sensitive information. Implementing granular permissions ensures that only authorized users can access and modify the contents of the protected folder. A well-defined permission structure minimizes the risk of data breaches and unauthorized modifications. It’s also important to regularly review and update permissions to reflect changes in team structure or responsibilities.
For instance, if a team member leaves the organization, their access to the protected folder should be promptly revoked.
Common Mistakes When Using Folder Protection
Users often make errors that compromise the effectiveness of OneDrive Folder Protection. These mistakes range from overlooking critical settings to failing to regularly review access permissions. This section highlights common pitfalls to help users avoid them.
- Neglecting to set appropriate protection levels based on data sensitivity. This can leave sensitive information vulnerable to unauthorized access.
- Failing to review and update permissions regularly. Changes in personnel or project needs may necessitate adjustments to access controls, which can lead to security gaps.
- Overlooking the importance of strong passwords for access to the protected folder. Weak passwords can be easily cracked, exposing the folder’s contents to malicious actors.
- Not utilizing multi-factor authentication (MFA) for enhanced security. MFA adds an extra layer of security, making it significantly harder for attackers to gain unauthorized access.
Mitigating Security Risks
Understanding and mitigating potential security risks associated with folder protection is critical. This involves proactive measures to safeguard the protected folder and its contents. A comprehensive approach that incorporates both technical and administrative controls is necessary.
Microsoft OneDrive’s folder protection feature is a lifesaver for keeping important files safe. It’s great for sensitive documents, but sometimes you need a little extra security, like when you’re experimenting with fun face filters on Facebook Live, especially for Halloween. Check out the latest trends in facebook live face filters halloween to see how creative people are getting.
Ultimately, OneDrive’s protection is still a top choice for securing your digital treasures.
- Regularly updating OneDrive and the operating system to patch vulnerabilities. This proactive measure helps prevent exploitation of known weaknesses.
- Employing strong passwords for all accounts involved. A robust password policy helps prevent unauthorized access.
- Actively monitoring user activity within the protected folder for any suspicious behavior. Prompt detection and response to anomalies can help prevent security breaches.
- Conducting regular security audits of protected folders to identify potential vulnerabilities. This proactive measure ensures the ongoing effectiveness of the security controls.
Guidelines for Effective Use
Following these guidelines will maximize the effectiveness of OneDrive Folder Protection and safeguard your sensitive data.
- Define clear criteria for which folders require protection. This ensures that the feature is used judiciously and its benefits are maximized.
- Establish a comprehensive permission management policy to control access. This policy should be documented and communicated to all relevant stakeholders.
- Regularly review and update folder protection settings to reflect changes in data sensitivity or access needs. This proactive approach keeps the protection mechanism aligned with the organization’s security requirements.
- Educate users about best practices for utilizing folder protection. This includes providing training and awareness materials to help them avoid common mistakes.
Troubleshooting and Common Issues
OneDrive Folder Protection, while a valuable security feature, can sometimes present challenges. Understanding common issues and their causes is crucial for efficient troubleshooting. This section details typical problems users might encounter and provides step-by-step solutions.Troubleshooting OneDrive Folder Protection involves identifying the root cause of the problem and applying the appropriate solution. Knowing potential pitfalls will empower users to resolve issues quickly and maintain the integrity of their protected folders.
Common Folder Protection Issues
Folder protection issues often stem from misconfigurations, network connectivity problems, or software conflicts. Incorrect permissions, outdated software, or incompatible applications can lead to access restrictions or the inability to protect folders. A lack of understanding of the folder protection rules or unexpected file system changes can also cause difficulties.
Troubleshooting Steps, Microsoft onedrive folder protection feature
This section provides a structured approach to resolving common folder protection problems.
| Issue | Possible Cause | Troubleshooting Steps |
|---|---|---|
| Unable to protect a folder | Incorrect permissions, network issues, or conflicts with other applications. | Verify user permissions on the folder, check network connectivity, and ensure no other applications are interfering with the folder protection process. Restart OneDrive and the affected application. |
| Protected folder inaccessible | Incorrect folder path, corrupted file system, or OneDrive synchronization issues. | Double-check the folder path to ensure accuracy, verify OneDrive synchronization status, and repair OneDrive if necessary. Run file system checks on the affected drive if applicable. |
| Folder protection fails during synchronization | Temporary network interruptions, antivirus software blocking OneDrive operations, or insufficient storage space. | Check for network connectivity issues, temporarily disable antivirus software (if possible), and ensure sufficient free storage space on the device. Restart the computer and OneDrive. |
| Protected files cannot be accessed by others | Incorrect permission settings for the protected folder, or conflicting user permissions. | Verify the permission settings for the protected folder, and ensure appropriate access is granted to authorized users. Review the permissions set on the folder and its contents. |
Contacting OneDrive Support
If troubleshooting steps fail to resolve the issue, contacting OneDrive support is the next course of action. Document the problem thoroughly, including error messages, steps taken, and relevant system information. This detailed information aids support personnel in quickly identifying and resolving the problem.
Recovering Access to Protected Folders
In some cases, users may lose access to protected folders due to issues like accidental deletion or file corruption. While data recovery tools might help in some situations, the recovery process is often complex and depends on the specific issue. Always prioritize backing up important files to prevent data loss.
Technical Specifications: Microsoft Onedrive Folder Protection Feature
OneDrive Folder Protection leverages a robust set of technical specifications to ensure the security and integrity of protected folders. These specifications cover encryption, data storage, communication protocols, and hardware requirements. Understanding these technical details provides a deeper insight into the feature’s functionality and reliability.The encryption algorithms and data storage formats employed are designed to resist unauthorized access and data breaches, while communication protocols maintain secure data transmission.
This approach guarantees the confidentiality, integrity, and availability of the protected data.
Encryption Algorithms
The encryption algorithms employed by OneDrive Folder Protection are designed for robust security. Advanced encryption standards (AES) are used, typically AES-256, providing strong protection against unauthorized access. This ensures that only authorized users can access the data within the protected folders. The specific implementation details are proprietary to maintain security and are not publicly disclosed.
“AES-256 is a widely used and well-vetted encryption standard.”
Data Storage Format
OneDrive uses a proprietary data storage format specifically optimized for protected folders. This format ensures efficient storage and retrieval of encrypted data while maintaining compatibility with other OneDrive features. The format is designed to handle large amounts of data and ensure fast access times.
Security Protocols
Secure communication protocols, such as TLS/SSL, are employed for secure data transmission between the user’s device and OneDrive servers. These protocols encrypt the data in transit, preventing interception and ensuring the confidentiality of the data being transferred.
Hardware Requirements
The following table Artikels the minimum hardware requirements for utilizing OneDrive Folder Protection:
| Component | Requirement |
|---|---|
| Operating System | Windows 10 or later, macOS 10.15 or later, or supported mobile OS. |
| Processor | Intel Core i5-4590 or equivalent, or comparable ARM processor. |
| RAM | 8 GB RAM |
| Storage | Sufficient free space on the user’s device to store protected folders. |
| Network Connection | Stable internet connection for syncing and accessing protected folders. |
These hardware requirements are estimates and may vary depending on the specific usage and file sizes. Modern hardware should easily meet these requirements.
Future Enhancements and Developments
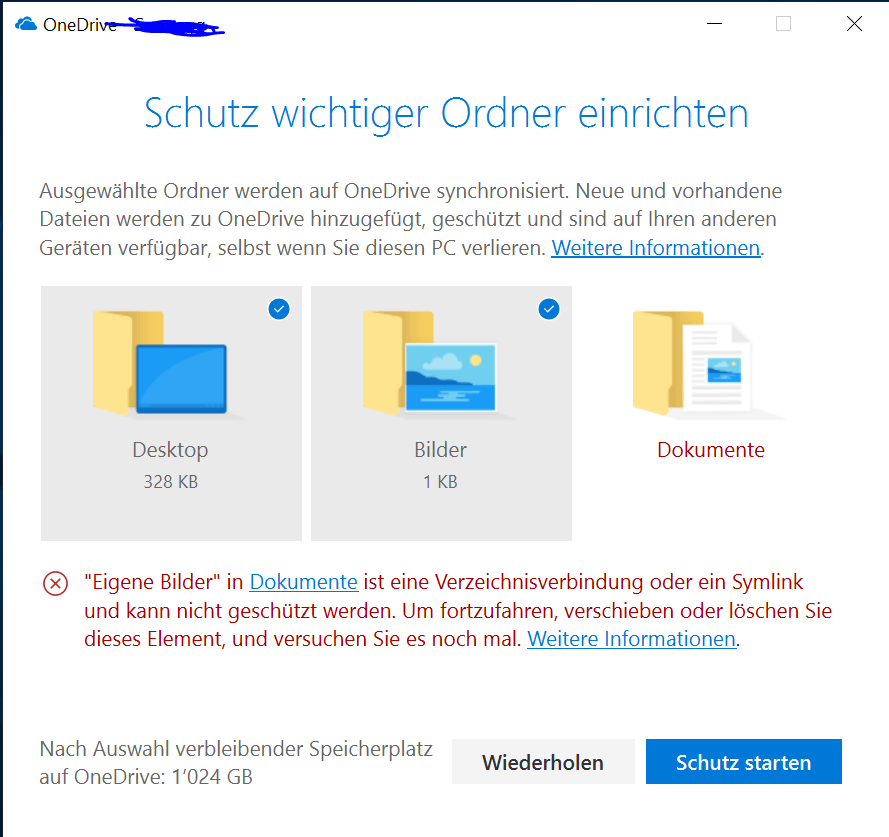
OneDrive’s folder protection feature is a valuable asset for securing sensitive information. As technology evolves, so too must security measures. Future enhancements should focus on proactive protection, enhanced user control, and seamless integration with other Microsoft services.The current implementation of OneDrive folder protection is a strong foundation. However, future development should explore ways to improve user experience, increase security robustness, and adapt to evolving threats.
This includes features for automatic updates to security protocols and user-friendly interfaces for adjusting security settings.
Potential New Features and Functionalities
OneDrive folder protection can benefit from proactive security measures, such as automatic threat detection and mitigation. Real-time threat analysis could flag potentially harmful files or folders, allowing for swift intervention. This approach could incorporate machine learning algorithms to identify anomalies and prevent unauthorized access or modification. The ability to apply different security levels to various folder types would also enhance flexibility.
For instance, a user could set a stricter level of protection for financial documents compared to personal photos.
Improvements to User Interface for Managing Folder Protection
A more intuitive interface for managing folder protection is crucial. A graphical representation of folder security settings, including permissions, access controls, and encryption levels, would improve user comprehension and allow for quick adjustments. Visual cues and clear instructions could guide users through complex security configurations. This approach would eliminate confusion and allow users to easily understand and apply various security settings.
Evolution of Security Features in OneDrive
The future of OneDrive folder protection likely involves advanced security features such as multi-factor authentication (MFA) and zero-trust principles. These additions would enhance the security posture of sensitive folders by requiring multiple verification methods to access them. Zero-trust principles, which assume no user or device is inherently trusted, would help limit the impact of a security breach by restricting access based on context and identity.
Examples of Enhanced Folder Protection to Meet Future Needs
One example of enhanced folder protection is the integration of AI-powered threat detection. This would allow OneDrive to identify and flag suspicious activities in real-time, enabling users to respond proactively. Another enhancement is the ability to set granular permissions on specific files within a protected folder. This would provide enhanced control over access to individual files, ensuring only authorized users can view or modify specific data elements.Furthermore, integration with external security systems like third-party antivirus solutions or vulnerability scanners can help to create a layered approach to security, providing a robust and comprehensive security posture for user data.
Closing Summary
In conclusion, Microsoft OneDrive’s folder protection feature is a powerful tool for bolstering data security within your OneDrive account. By understanding the different protection mechanisms, security features, and user experience aspects, you can effectively leverage this feature to safeguard your important files. This article has provided a detailed overview, allowing you to make informed decisions about how to best use this feature in your own workflow.
Further exploration of best practices and troubleshooting will ensure a seamless and secure OneDrive experience.